Vulnerable Software and Overview
VestCert is a certification program used while accessing websites, and is a non-ActiveX module developed by the Korean company, Yettiesoft. This program is registered as a Startup Program and will be relaunched by Yettiesoft’s service (Gozi) even if it is terminated. It remains constantly active as a process once it is installed, so it can be exposed to vulnerability attacks. Thus, it needs to be updated to the latest version.
Description of the Vulnerability
This vulnerability was first discovered and reported by AhnLab and the remote code execution vulnerability (RCE) can occur on vulnerable versions of VestCert.
Patch Target and Versions
VestCert versions 2.3.6 – 2.5.29
Vulnerability Exploitation Log (Lazarus)
AhnLab’s ASD (AhnLab Smart Defense) infrastructure confirmed the exploitation of this vulnerability. The threat actor exploited this vulnerability to download and execute their malware.
 Figure 1. Vulnerability log from ASD
Figure 1. Vulnerability log from ASDThis malware (winsync.dll) has similar features and appearance as the SCSKAppLink.dll file which was covered in a past post.
Additionally, both files were compiled by exploiting the open-source plugin, NotePad++, and the code routine for string decryption was also the same.
 Figure 2. Same file info as SCSKAppLink.dll
Figure 2. Same file info as SCSKAppLink.dll Figure 3. Same code pattern as before
Figure 3. Same code pattern as beforeSolution
Users must check their program version by following the steps below and update their program to the latest version.
– Service operator: Replace with the latest version through Yettiesoft
– Service user: If a vulnerable version of VestCert is installed, uninstall and install the latest version
 Figure 4. Terminating and uninstalling VestCert
Figure 4. Terminating and uninstalling VestCert[1] Process Termination
– Must terminate ① Goji → ② VestCert in this order specifically from the Process tab of Task Manager
[2] Uninstall Installed Program
– Check the VestCert version in [Control Panel]-[Programs]-[Programs and Applications] and click “Uninstall”
[3] Reinstall Program
– Reinstall the resolved version of the program by accessing the financial website* you have been using
* Financial websites have different vulnerability patch schedules, so confirmation is required
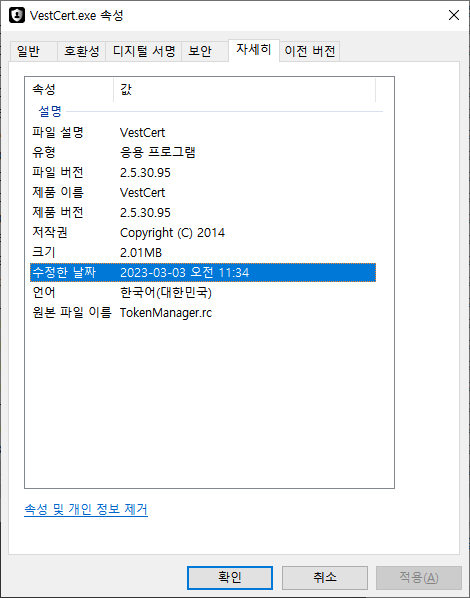 Figure 5. Latest VestCert version (2.5.30 ~)
Figure 5. Latest VestCert version (2.5.30 ~)Detection
Trojan/Win.LazarLoader.C5378117 (2023.02.08.03)
Execution/MDP.Powershell.M1185
IOC
MD5
– 0a840090b5eac30db985f0c46f46a602
[References]
- https://knvd.krcert.or.kr/detailSecNo.do?IDX=5881
- https://atip.ahnlab.com/ti/contents/asec-notes?i=11d64889-76f5-40a5-86d3-8319e1bef763
- https://www.yettiesoft.com/html/support/0502_faq.html
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
The post Warning for Certification Solution (VestCert) Vulnerability and Update Recommendation appeared first on ASEC BLOG.
Article Link: Warning for Certification Solution (VestCert) Vulnerability and Update Recommendation - ASEC BLOG