Hunting Down Big Game Hunters
With contribution from Denise Dasom Kim, Jungyeon Lim, Yeonghyeon Jeong | S2W LAB Talon
 Image from unsplash
Image from unsplashSoW (Story of the Week) publishes a report summarizing ransomware’s activity on the Darkweb. The report includes summary of victimized firms, Top 5 targeted countries and industrial sectors, status of dark web forum posts by ransomware operators, etc.
Executive Summary
- [Statistics] The number of companies infected by ransomware decreased by 46 in one week (-53% compared to previous week), due to the sudden shut down of Avaddon ransomware operator’s activity (22 companies that were infected by Avaddon ransomware last week)
- [Dark Web] According to AdvIntel, there was an initial access seller of JBS (a company infected by REvil) Citrix Access information, and we found similar information in relation to JBS citrix-related information on bot market.
- [Dark Web] Avaddon Dark Web uploaded 120 victims for 10 months, and on June 11th, the operation was shut down with the release of the decryption key.
- [Current Affairs] G7 (Group of 7) warns Russia to suspend all ransomware-related activities within its borders. Russian President Putin responded that he is prepared to extradite cyber criminals attacking US critical infrastructure.
1. Weekly Status
A. Status of the victimized firms (06/07~06/13)
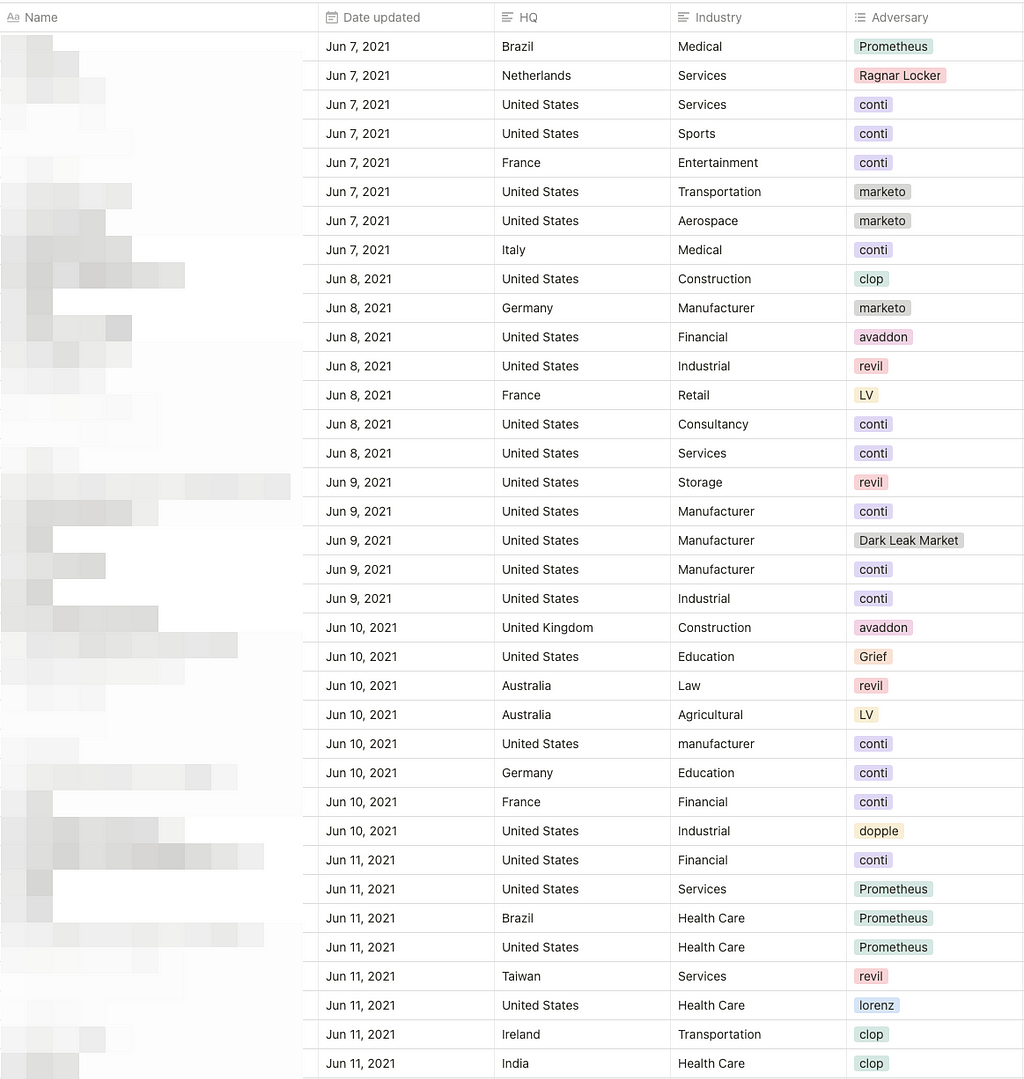
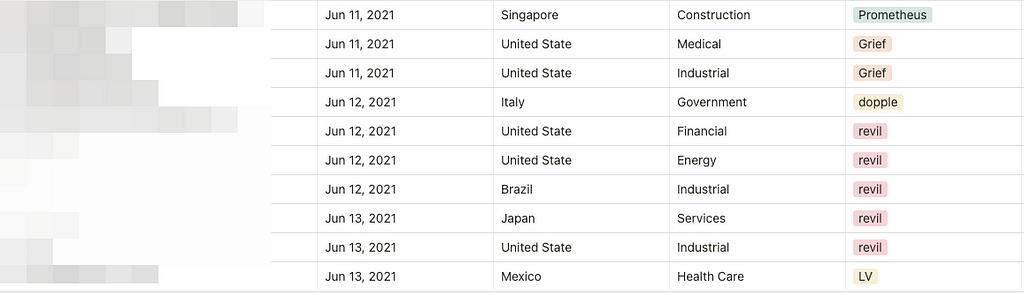
- For a week, a total of 46 victimized firms were mentioned. The number of victims decreased by 53% compared to the previous week.
- This is due to the sudden shut down of Avaddon ransomware operation (Posted 22 victims last week).
- 12 threat groups’ activities were detected
B. TOP 5 targeted countries
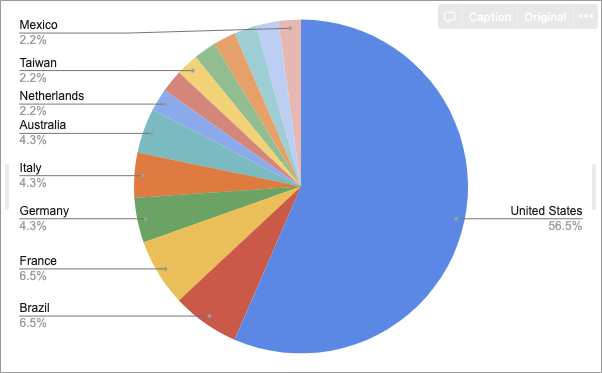
- United States — 56.5%
- Brazil & France — 6.5%
- Germany & Italy & Australia — 4.3%
- Netherlands & Taiwan & Mexico — 2.1%
C. TOP 5 targeted industrial sectors
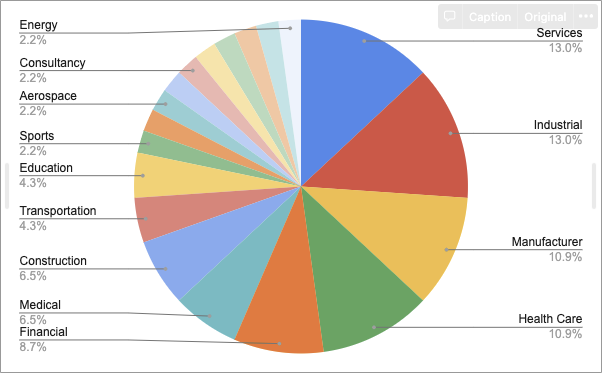
- Services & Industrial — 13.0%
- Manufacturer & Health Care — 10.9%
- Financial — 8.7%
- Medical & Construction — 6.5%
- Transportation & Education — 4.3%
2. Posts related to Ransomware threat actors @Dark Web
A. Recent findings about REvil and JBS
- AdvIntel tweeted that they discovered an initial access seller of JBS Citrix Access on the Exploit forum.
- Additionally, S2W LAB also found that JBS Citrix information was sold in the Bot Market on March 15, 2020 (Vidar) and June 11, 2021 (RedLine).

https://twitter.com/y_advintel/status/1402751254242201600?s=21
- Citrix[.]jbs.com.br information sold on the Bot Market
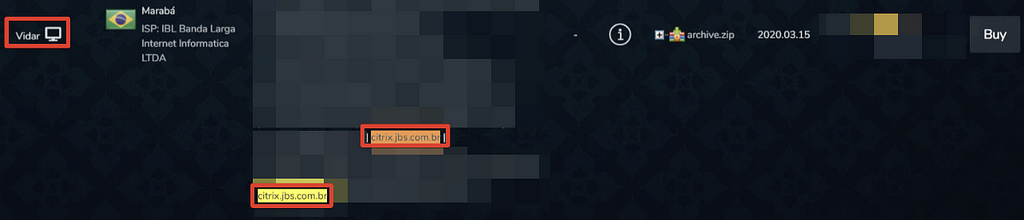 2020.03.15 — Vidar Stealer
2020.03.15 — Vidar Stealer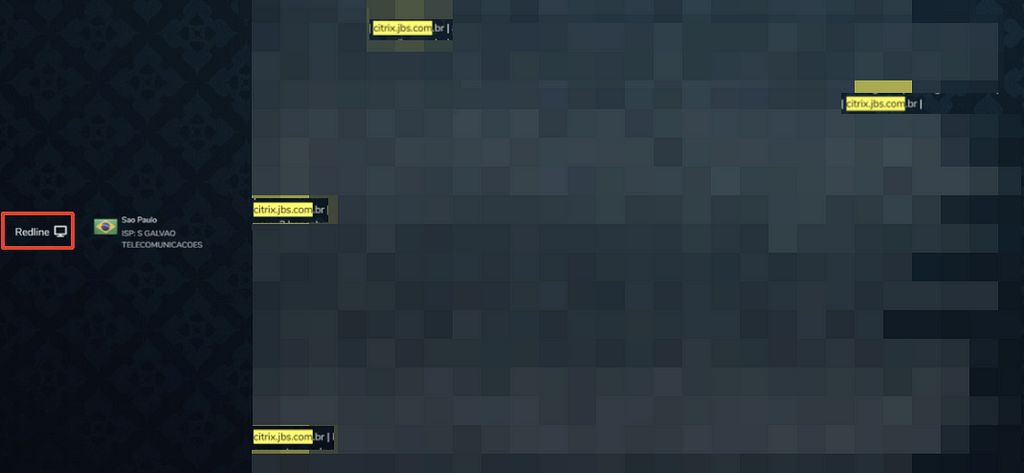 2021.06.11 — Red Line
2021.06.11 — Red LineB. REvil intertwined with political issue
- REvil uploaded a post titled “Big data breach from invenergy” on their data leakage site.

- Then, the titled “Big data breach from invenergy” was soon changed to “Obama’s friend is a dirty pervert” and added a picture of Obama to draw public attention. In the past, he uploaded a post titled “For the press #2 and Trump” and intentionally posted provocative and political content, and it did spread over globally via press.

C. G7 warns Russia against ransomware activities and Russia prepared to extradite cyber criminals
- The US recently announced that they are investigating ransomware at a level equivalent to terrorism, and it was announced again in G7 asking Russia to hunt down ransomware activity operating within its borders.
G7 leaders ask Russia to hunt down ransomware gangs within its borders
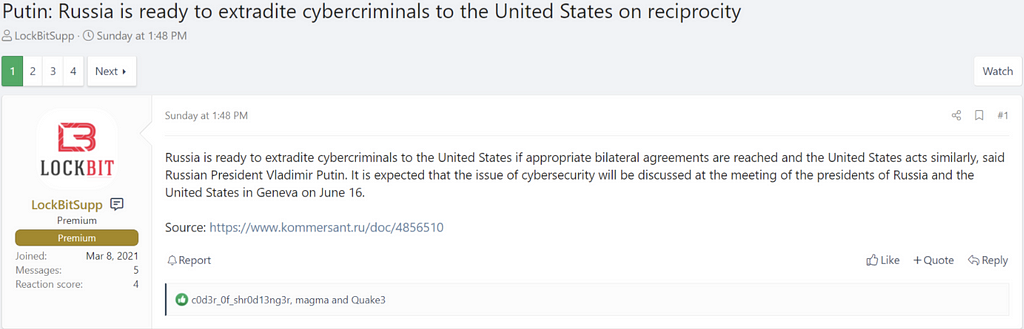
- Russia responded by saying that they are prepared to extradite cyber criminals to the U.S on a reciprocal basis.
Putin says Russia prepared to extradite cyber criminals to US on reciprocal basis
- LockBit has posted concerns about related content, but REvil is still active in this situation.
D. The doom of Avaddon ransomware
Decryptor Download Link: https://www.emsisoft.com/ransomware-decryption-tools/avaddon
- An anonymous password-protected ZIP file and password-containing information were received from the FBI, and the ZIP file contained three files:
 Source: https://www.bleepingcomputer.com/news/security/avaddon-ransomware-shuts-down-and-releases-decryption-keys/
Source: https://www.bleepingcomputer.com/news/security/avaddon-ransomware-shuts-down-and-releases-decryption-keys/- The decryption tool delivered by Emsisoft and bleeping worked successfully as it decrypted files that are previously encrypted by Avaddon.
- Currently, the data leak site operated by Avaddon ransomware on Tor is not accessible.
- Avaddon ransomware threat actors shared a key to decrypt a total of 2,934 encrypted files.
- Avaddon operated the dark web leaked site for 10 months (Aug. 2020 ~ Jun. 2021), infecting 120 companies while negotiating with 47 companies then finally shut down.

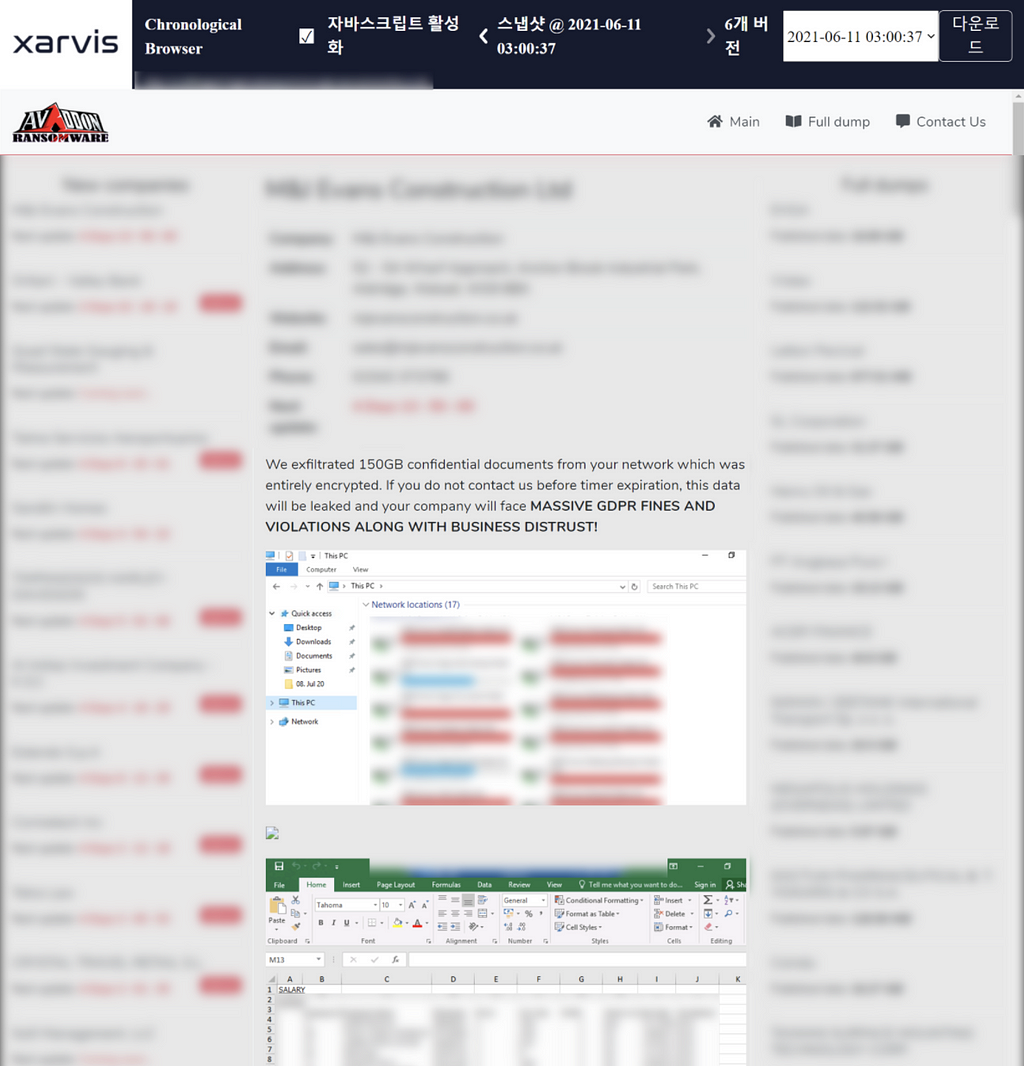
- Last activity of Avaddon leak site
Conclusion
- Although Avaddon’s activities have been suspended, it is unknown whether the group has been arrested or has just disappeared.
- It has been reported that the REvil ransomware that infected JBS was sold on Citrix accounts on the dark web. It is necessary to be careful about information such as citrix, vpn, etc. being sold in the bot market.

- Homepage: https://www.s2wlab.com
- Facebook: https://www.facebook.com/S2WLAB/
- Twitter: https://twitter.com/s2wlab
W3 Jun | EN | Story of the week: Ransomware on the Darkweb was originally published in S2W LAB BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: W3 Jun | EN | Story of the week: Ransomware on the Darkweb | by Hyunmin Suh | S2W BLOG | Medium