The thread follows the needle
With contribution from Denise Dasom Kim, Jungyeon Lim, Yeonghyeon Jeong | S2W LAB Talon

SoW (Story of the Week) publishes a report summarizing ransomware’s activity on the Darkweb. The report includes summary of victimized firms, Top 5 targeted countries and industrial sectors, status of dark web forum posts by ransomware operators, etc.
Executive Summary
- [Statistics] The number of companies infected by ransomware is 28 in one week which is 50.9% lower compared to previous week, and United States is still positioned at the highest which amounts to 32.1% among all victims infected by ransomware.
- [Dark Web] Petya Ransomware builder released on the dark web
- [Dark Web] eCh0raix ransomware damage continues to target QNAP NAS device
- [Cryptocurrency] We tracked eCh0raix bitcoin address paid by victims and found some clustered addresses
- [New] New Ransomware discovered: Darkjon, and AvosLocker
1. Weekly Status
A. Status of the infected firms (06/28~07/05)
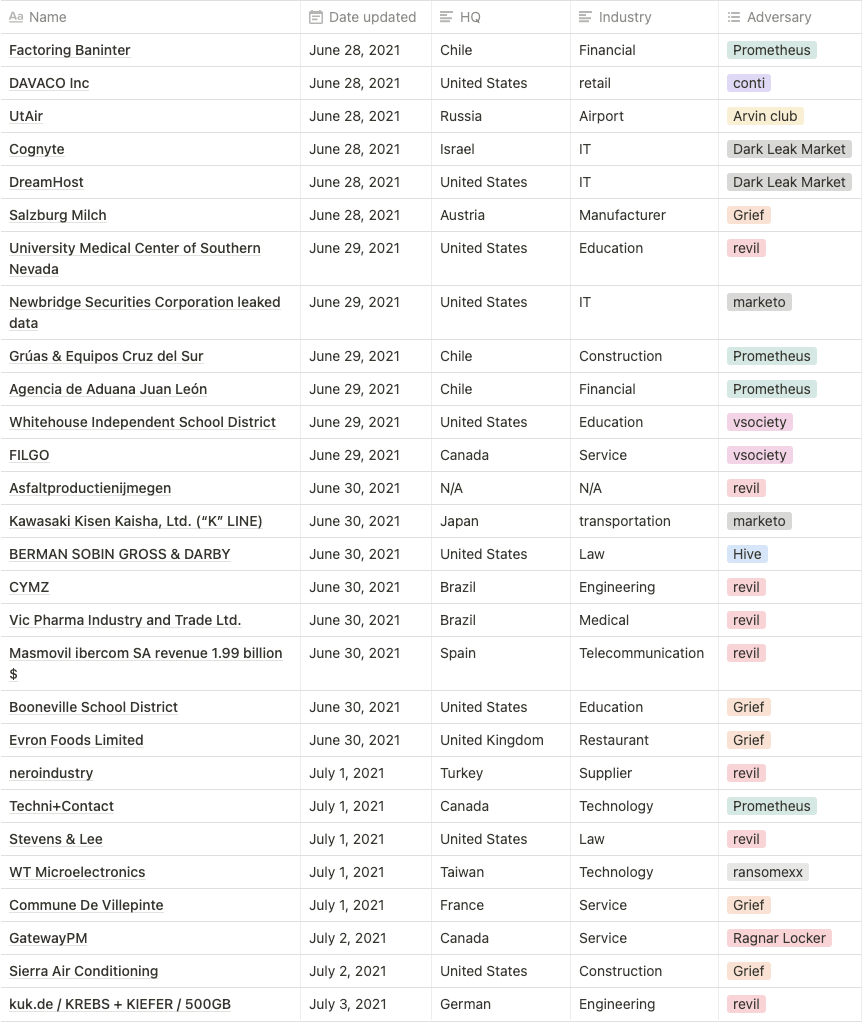
- For a week, a total of 28 infected firms were mentioned which is 50.9% lower compared to the previous week.
- 11 threat groups’ activities were detected
B. TOP 5 targeted countries
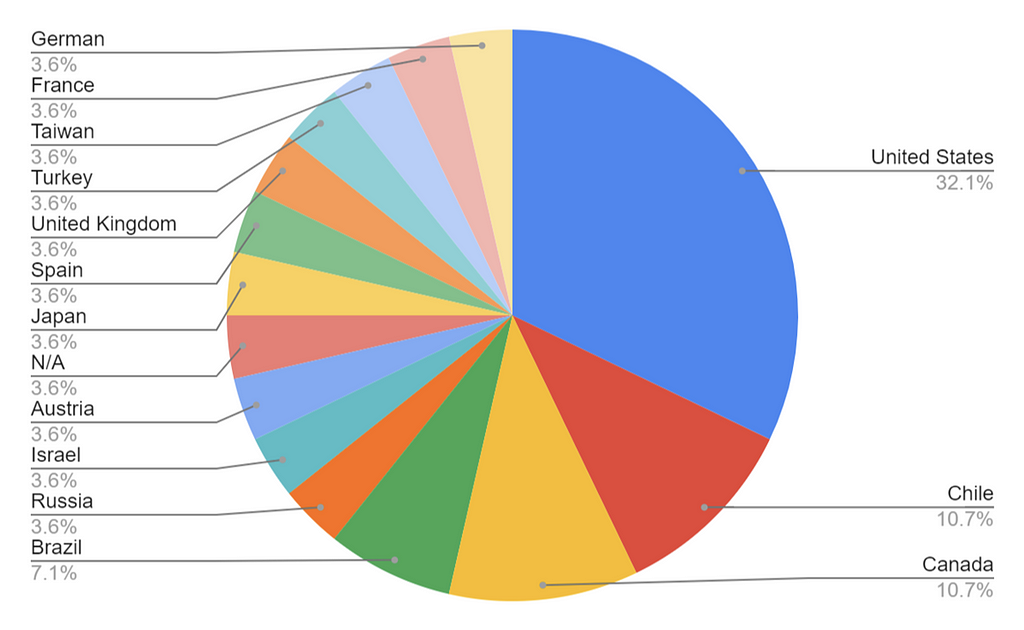
- United States — 32.1%
- Canada & Chile — 10.7%
- Brazil — 7.1%
- Others — 3.6%
C. TOP 5 targeted industrial sectors
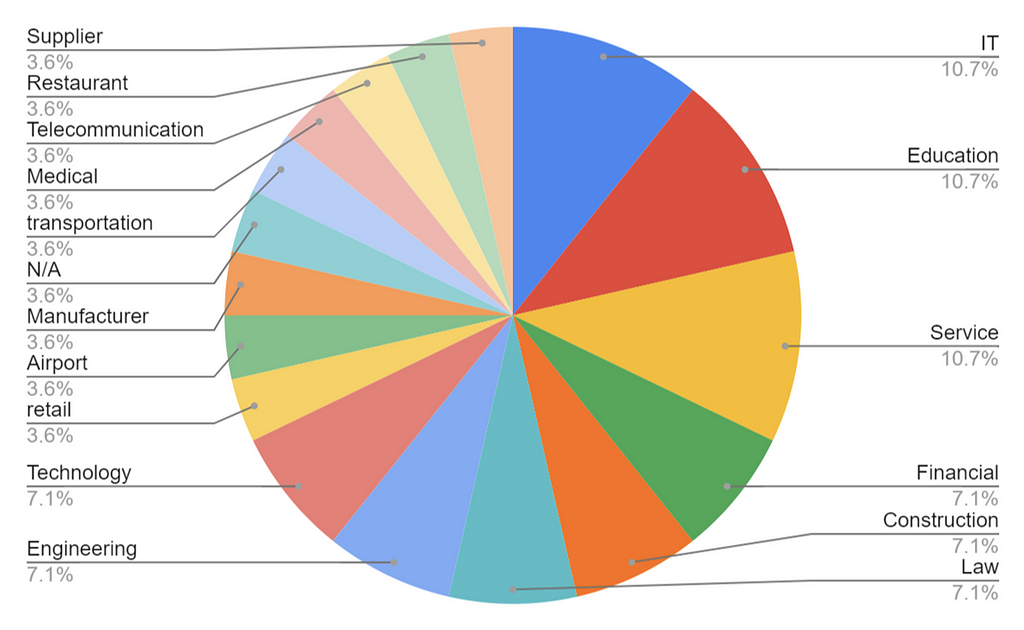
- Service & Education & IT — 10.7%
- Financial & Law & Engineering & Technology & Construction — 7.1%
- Others — 3.6%
D. Current status of data leak site operated by ransomware groups
- We keep monitoring the status of data leak sites operated by ransomware groups and approximately 28 sites operate stably while 5 sites are unstable.
- “Latest Updated” is based on the date the victim company information was updated.
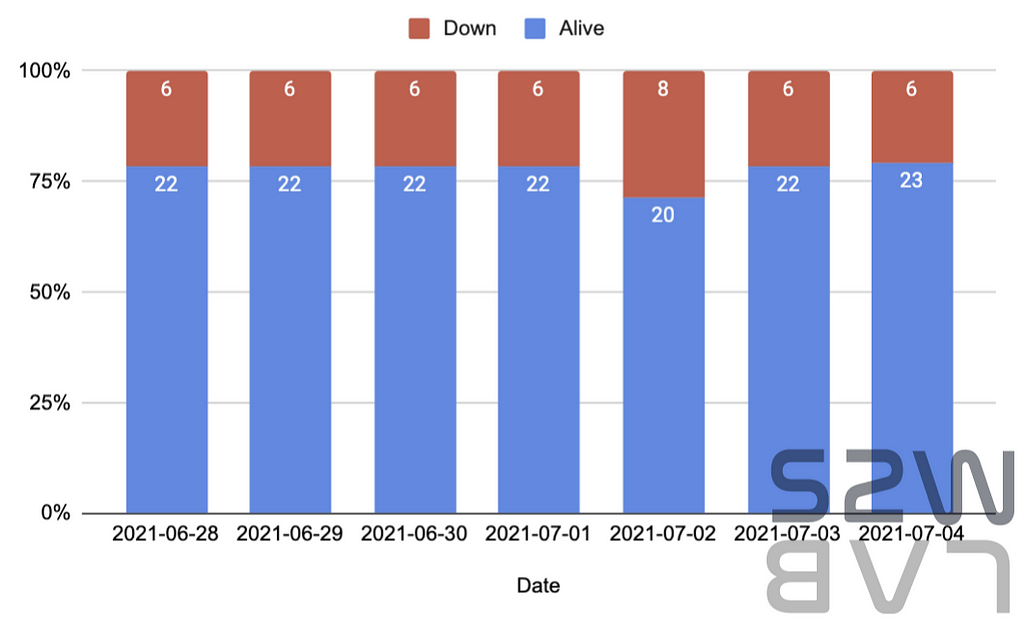
Current status of monitoring data leak site operated by ransomware
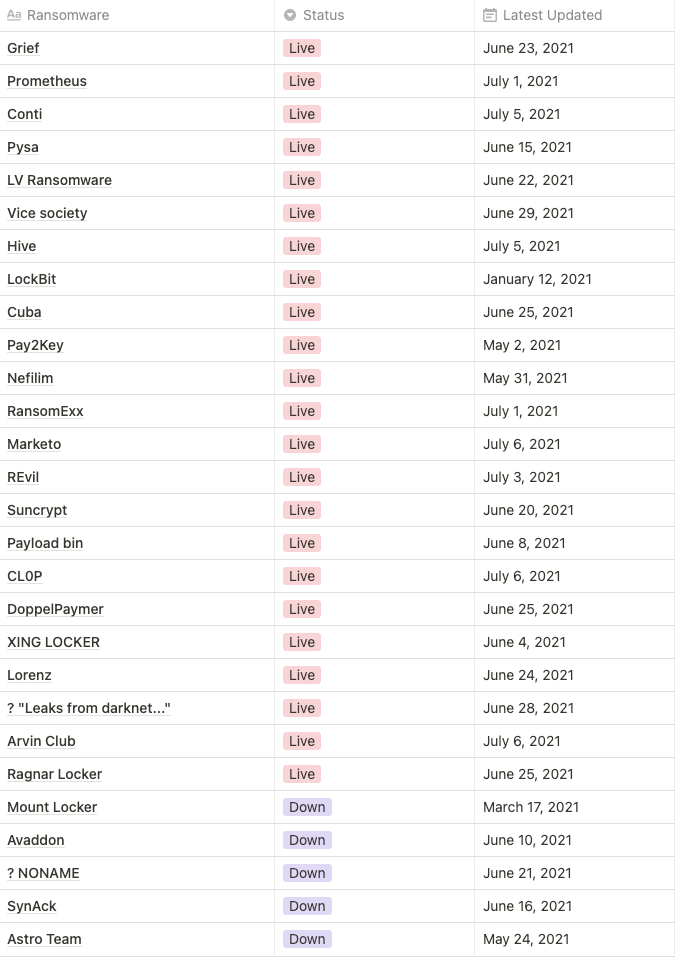
- Among the currently monitored ransomware leak sites, an average of 22 sites are stable and show steady activity.
2. Posts related to Ransomware threat actors @Dark Web
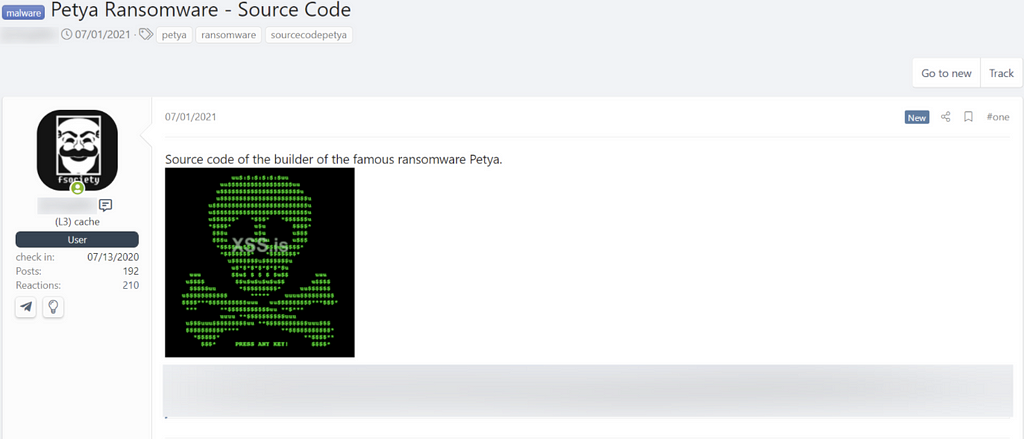
A. Petya ransomware builder released on the dark web
- 2021.07.01 The famous Petya ransomware (emerged and notorious in 2016) builder was shared on Russian hacking forum XSS.
- It was shared in the form of source code, and user can compile it.
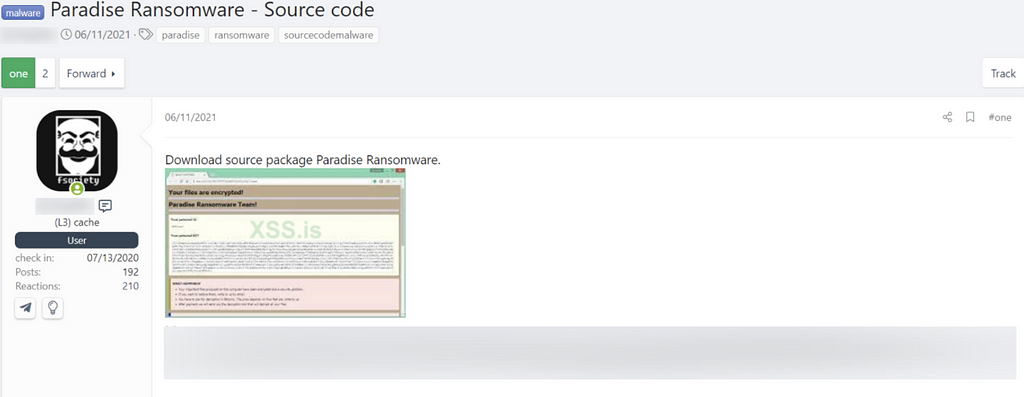
- The uploaded user has a history of sharing the Paradise ransomware source code in the past.
B. eCh0raix ransomware targeting QNAP NAS device
The eCh0raix ransomware is known to have appeared in 2019, and it has been reported steadily on the BleepingComputer forum.
https://www.bleepingcomputer.com/news/security/ongoing-ech0raix-ransomware-campaign-targets-qnap-nas-devices/
This ransomware is known to attack QNAP NAS devices, and the attack still continues and resulting many victims as of today.
B-1. The information of victims consistently published on community
The below is the affected device from eCh0raix ransomware.
- QNAP TS-219P II
- QNAP TS-228
- QNAP TS-228A
- QNAP TS-231
- QNAP TS-251
- QNAP TS-253A
- QNAP TS-451
- QNAP TS-459 Pro II
- QNAP TS 251
- QNAP TS 253B
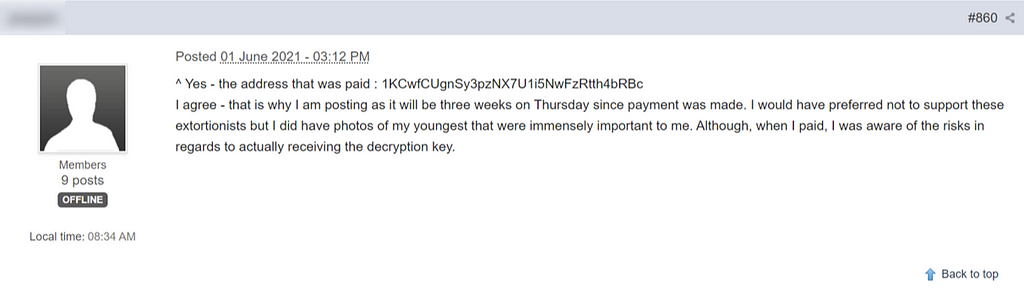
On June 1st, Specific user mentioned he paid BTC to the attacker related to eCh0raix.
https://www.bleepingcomputer.com/forums/t/617854/ech0raix-ransomware-qnapcryptsynology-nas-encrypt-support-topic/?p=5200448
- Victims are found to be individuals as well as enterprises.
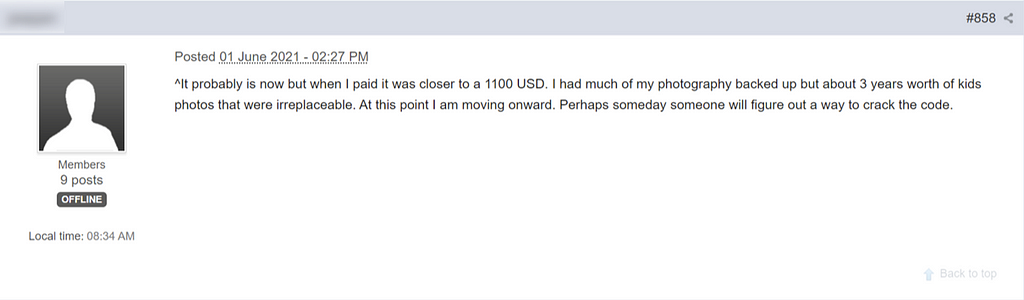
https://www.bleepingcomputer.com/forums/t/617854/ech0raix-ransomware-qnapcryptsynology-nas-encrypt-support-topic/?p=5200441
B-2. Tracking the bitcoin address of eCh0raix Ransomware
- The analysis of bitcoin addresses paid by victims
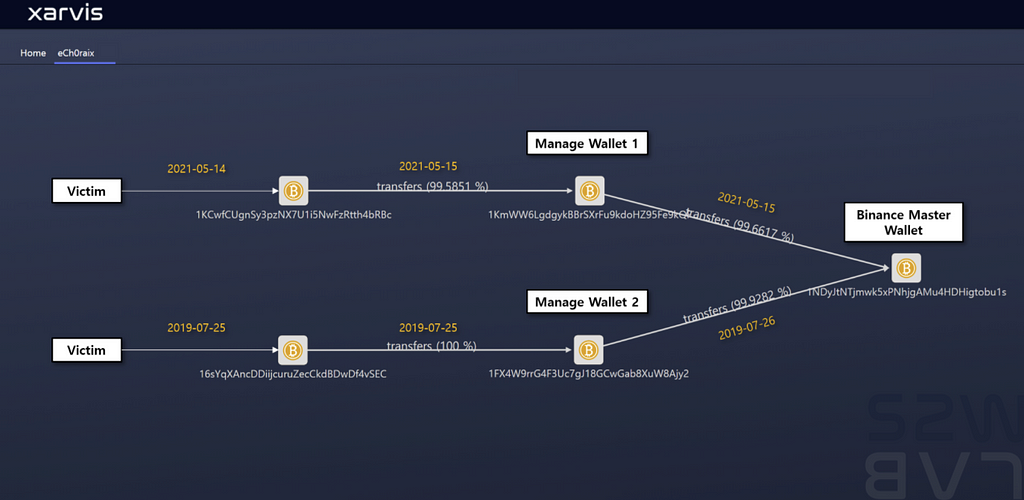
- It can be seen that eCh0raix is clustering bitcoin received from victims to one specific address for money management.
- Manage Wallet 1 : 1KmWW6LgdgykBBrSXrFu9kdoHZ95Fe9kQF
- Manage Wallet 2 : 1FX4W9rrG4F3Uc7gJ18GCwGab8XuW8Ajy2
- Afterwards, the collected bitcoins are transferred to the Binance Master wallet.
- Binance Master wallet : 1NDyJtNTjmwk5xPNhjgAMu4HDHigtobu1s
- It is an address that Binance manages for buying/selling and has a very large number of deposit/withdrawal transactions and holdings.
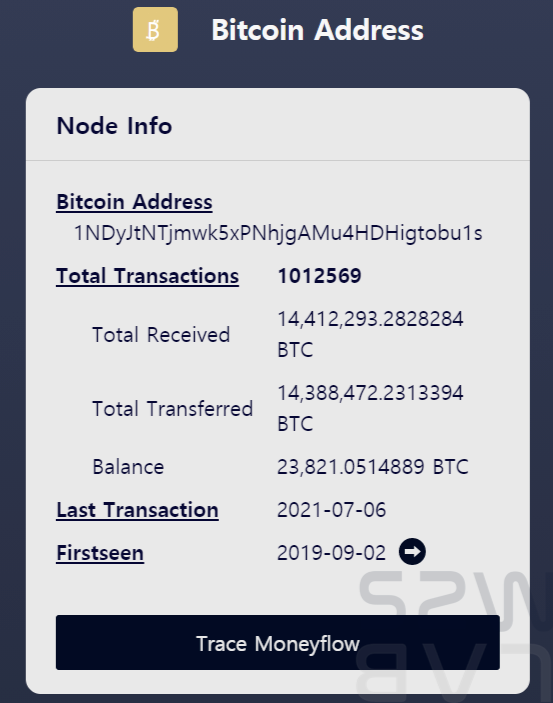
- Since 99.6% of the amount excluding the fee is transferred to the Binance Master wallet, the address also appears to be a wallet owned by eCh0raix created from Binance.

- After 2020.06, only Manage Wallet 1 is used as the Bitcoin address for money management
- It seems that the Leak Site address used in 2019 was changed in 2020, and the wallet address that mainly manages Bitcoin funds has also been changed
- 2020 ~ Now : veq****.onion
- 2019 : sg3****.onion
B-3. The detail analysis of the transaction
- We have back tracked bitcoins paid by victims, and we found several addresses transferred to a specific address.
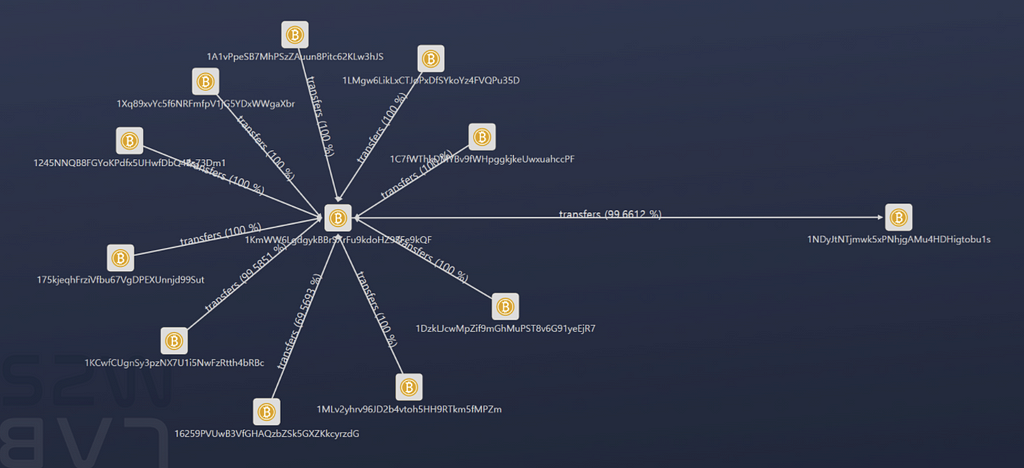
- By inserting the bitcoin addresses into the eCh0raix negotiation page URL, we could check the negotiation pages of other victims who paid the amount.
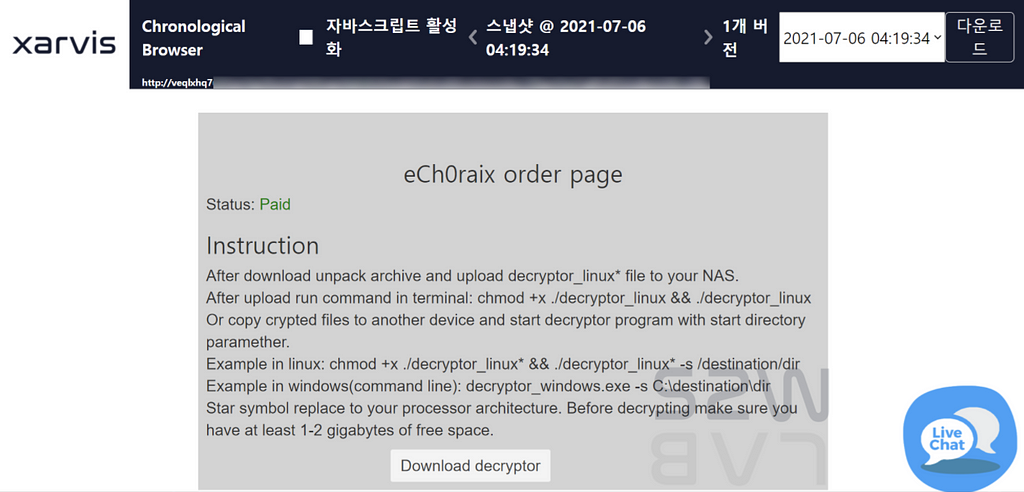
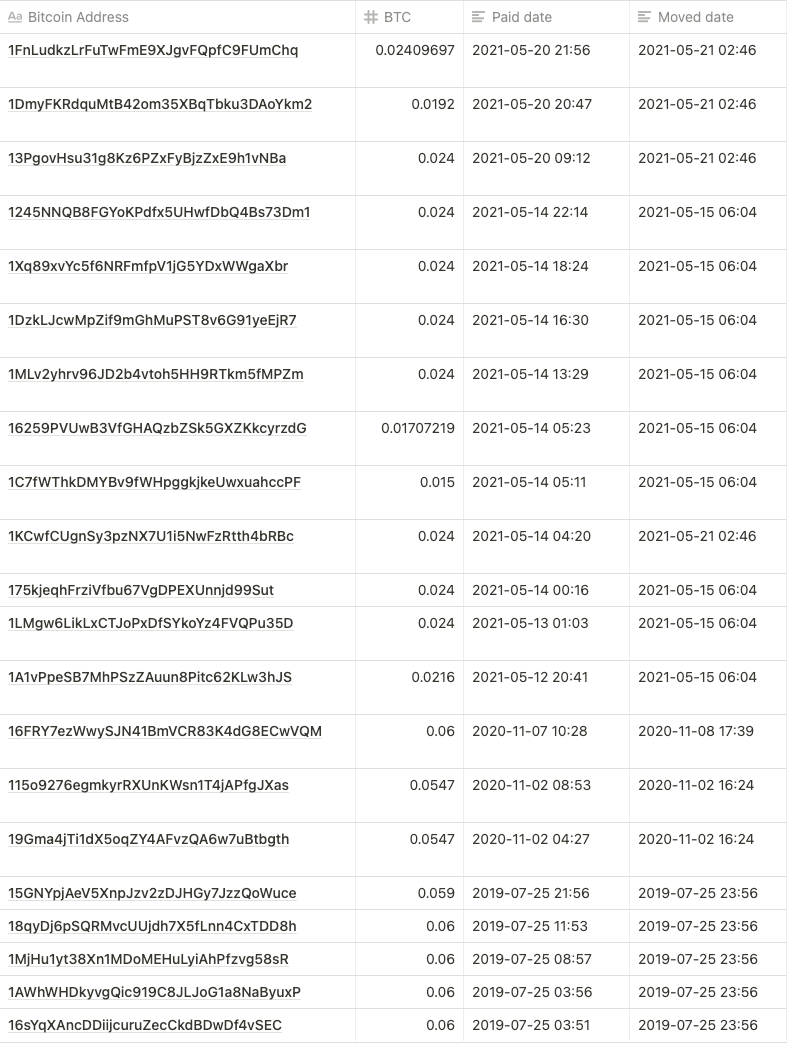
So we repeated the process and found addresses as below
- 175kjeqhFrziVfbu67VgDPEXUnnjd99Sut
- 1245NNQB8FGYoKPdfx5UHwfDbQ4Bs73Dm1
- 1Xq89xvYc5f6NRFmfpV1jG5YDxWWgaXbr
- 1C7fWThkDMYBv9fWHpggkjkeUwxuahccPF
- 1DzkLJcwMpZif9mGhMuPST8v6G91yeEjR7
- 1LMgw6LikLxCTJoPxDfSYkoYz4FVQPu35D
- 1MLv2yhrv96JD2b4vtoh5HH9RTkm5fMPZm
- 1A1vPpeSB7MhPSzZAuun8Pitc62KLw3hJS
- 16259PVUwB3VfGHAQzbZSk5GXZKkcyrzdG
- 15GNYpjAeV5XnpJzv2zDJHGy7JzzQoWuce
- 18qyDj6pSQRMvcUUjdh7X5fLnn4CxTDD8h
- 1MjHu1yt38Xn1MDoMEHuLyiAhPfzvg58sR
- 1AWhWHDkyvgQic919C8JLJoG1a8NaByuxP
The list of Bitcoin address that paid bitcoin among eCh0raix ransomware victims
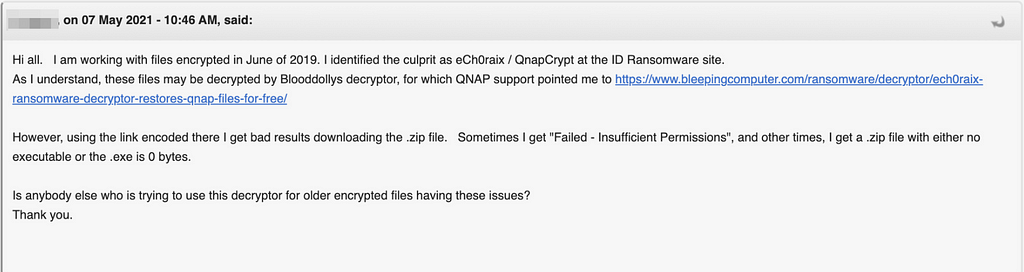
B-4. The detail analysis of eCh0raix Decryptor
We have seen several posts that eCh0raix ransomware decryptor doesn’t work properly even though victims paid the ransom money. So we have analyzed the detail analysis of eCh0raix decryptor as below.
- Analyze eCh0raix ransomware after acquiring decryptor
- Built with go 1.13
- Uses AES-256-CFB for encryption algorithm
- Attempts to decrypt files with .encrypt extension while recursively traversing the entire path
- Large files are divided into several blocks, then encrypted.
- After decoding 10485760 bytes (10MB), check whether the delimiter ‘eCh0raix’ exists in the decrypted data, and proceed with the decryption by writing the rest of the data to a new file.
Detailed analysis
- Cycle through the entire path and execute the decryption function
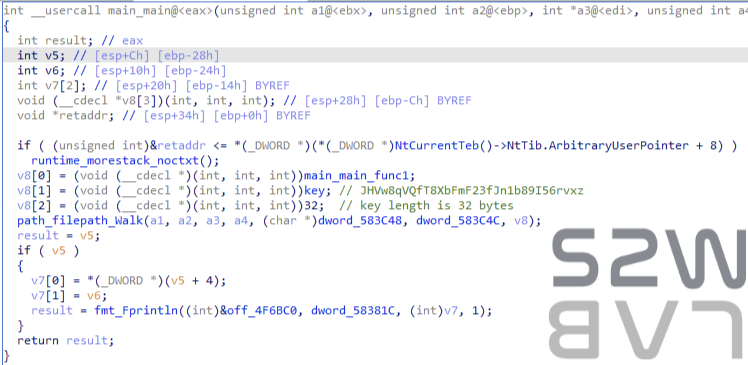
- Implementation using the built-in function Walk in Go's filepath package
- Cycles through the entire path and calls main_main_func1 whenever a file is found in the path. After checking the extension within the function, decryption is attempted if it is .encrypt.
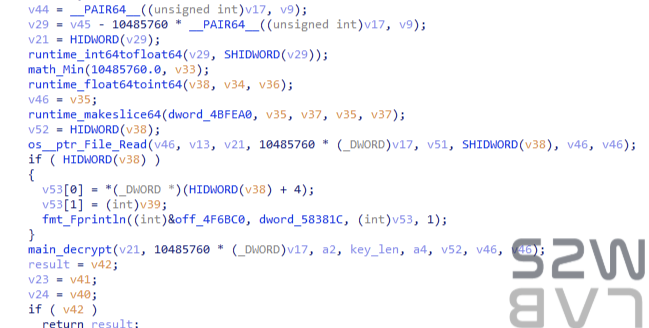
2. File size inspection and block decryption
- Check the file size and skip if it is 0 bytes.
- Start decryption by reading 10485760 bytes, if the size is not 0.
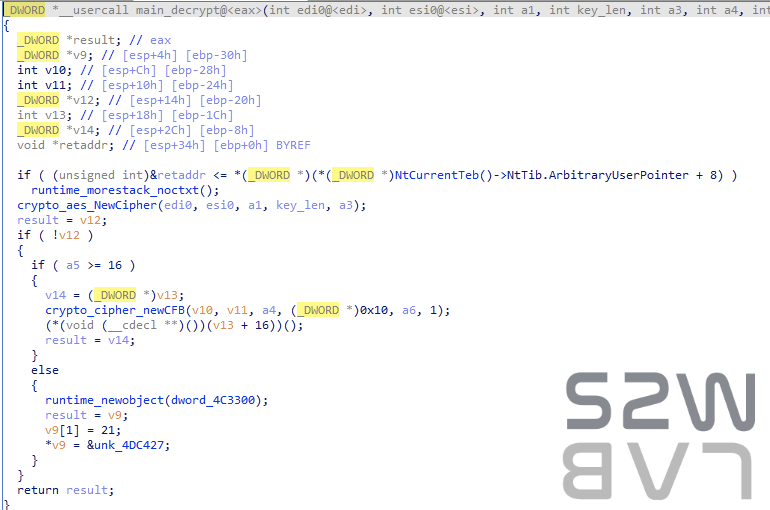
- Decrypted with AES-256-CFB
- Use the key set as an argument in main_main
- key: JHVw8qVQfT8XbFmF23fJn1b89I56rvxz
- length: 32
- If the eCh0raix delimiter exists, it is recorded in the file after removing delimiter using genSplit. If there is no delimiter, the entire data is recorded. Repeat this process until the end of the file.

- After decryption, delete the encrypted file and finish.
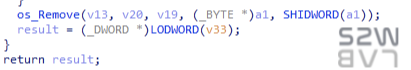
- Possible cause of decryption failure
- Attacker’s key setting mistake (possibly created a decryption program with the wrong person’s key)
- Incorrect extension setting (in this sample, only the .encrypt extension is recognized and decrypted)
- Block processing error for large files (possibly wrong separator or different block size from encryption program)
See QNAP advisory regarding eCh0raix ransomware
https://www.qnap.com/en/security-advisory/qsa-21-18
C. Darkjon
New Ransomware Darkjon
- The attacker requests the victim to pay $50 worth of BTC.
- BTC Address: 1AefQmfitXAuQDm1BSNpTN6mygpePd3MT6
- There isn’t any transaction yet (checked July 8th 2021)
Checked the information of Victims
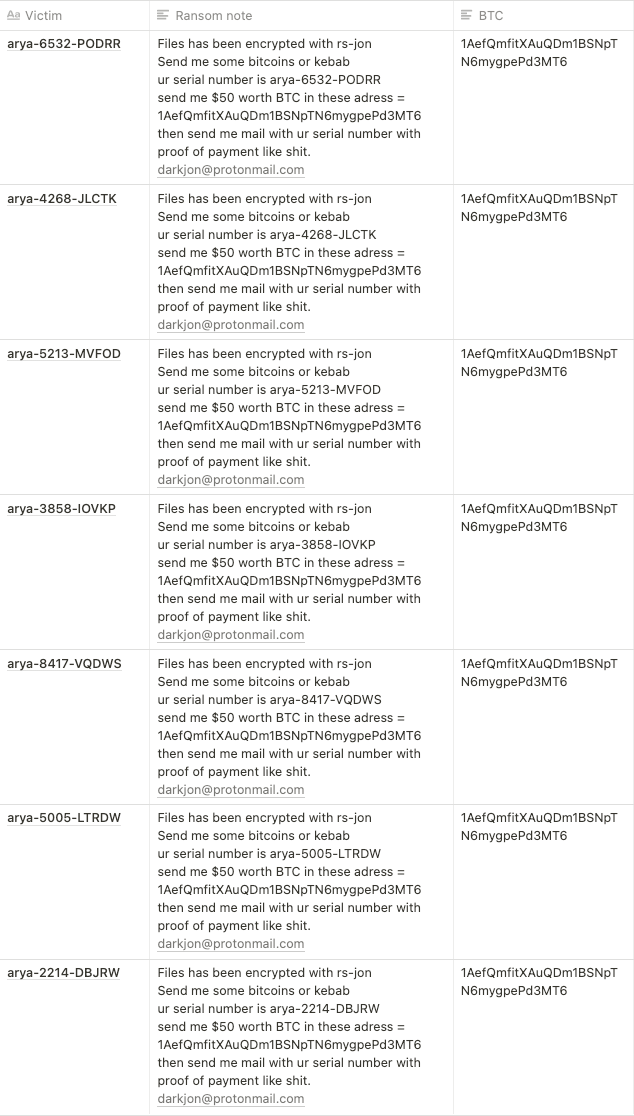
- No further analysis was performed as there isn’t any transaction made.
D. AvosLocker
D-1. New Ransomware AvosLocker
- The operator of AvosLocker published the advertisement included with the description of the function and the feature about AvosLocker on the forum of Surface Web.
- According to AvosLocker, they will host their services on Tor.
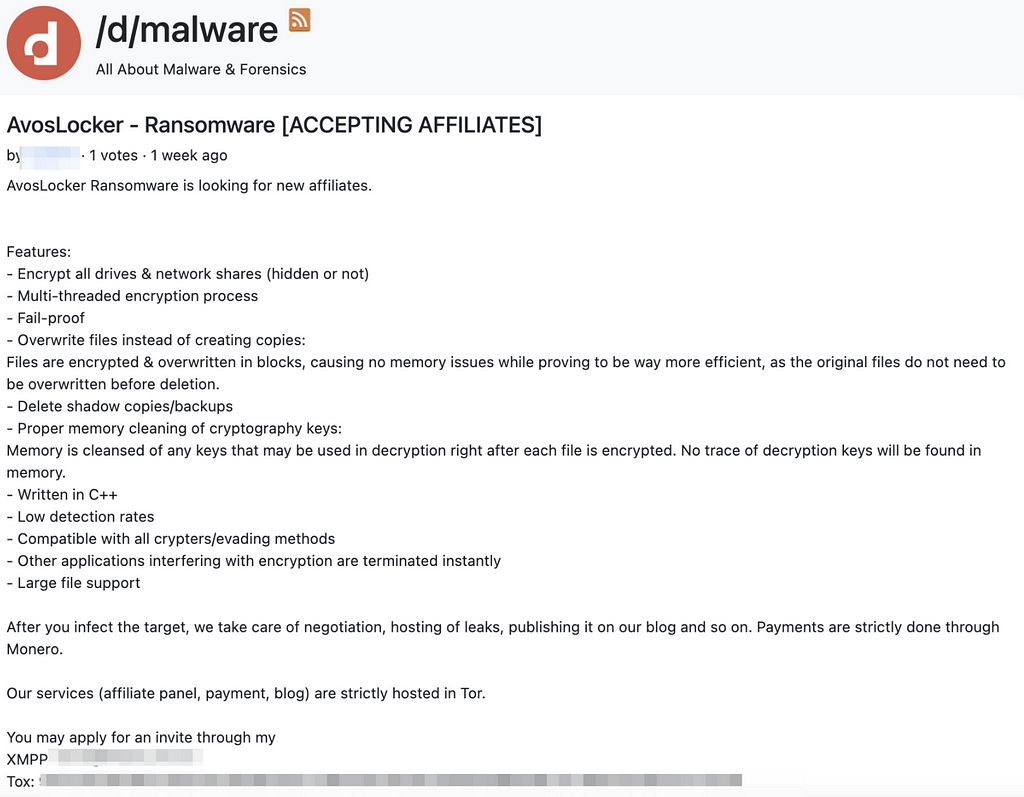
D-2. The current status of victims related to AvosLocker
- Anonymous victim was reported the detail with Ransom note that AvosLocker attack to victim
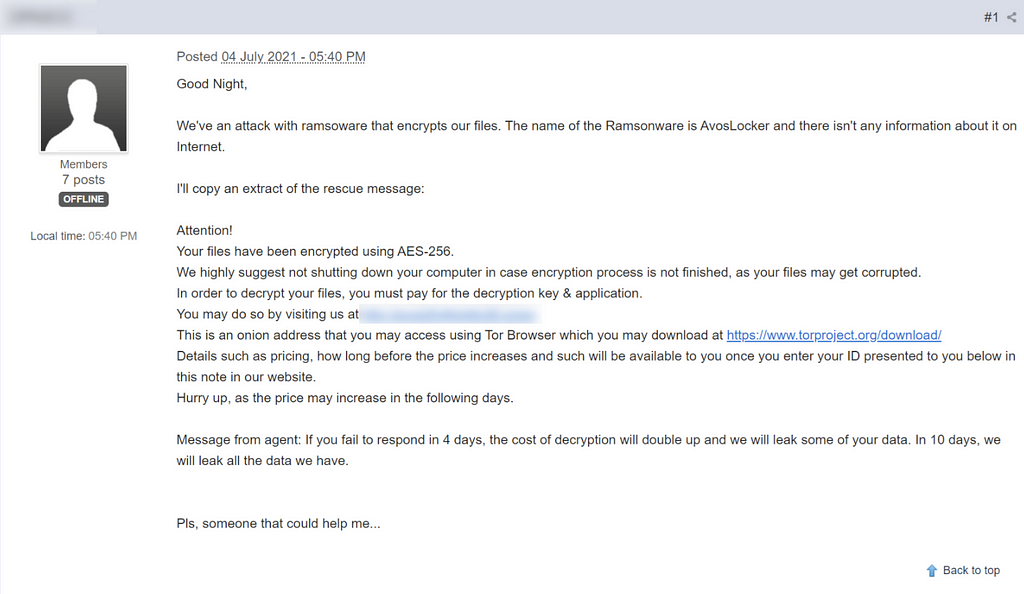
https://www.bleepingcomputer.com/forums/t/754311/ramsomware-attack-avoslocker/?p=5219874
D-3. Contact 사이트 및 지불 페이지 정보
- The payment page can be accessed using victim’s ID.
- The attacker requests the victim to pay 913.24 XMR (Monero) as below.
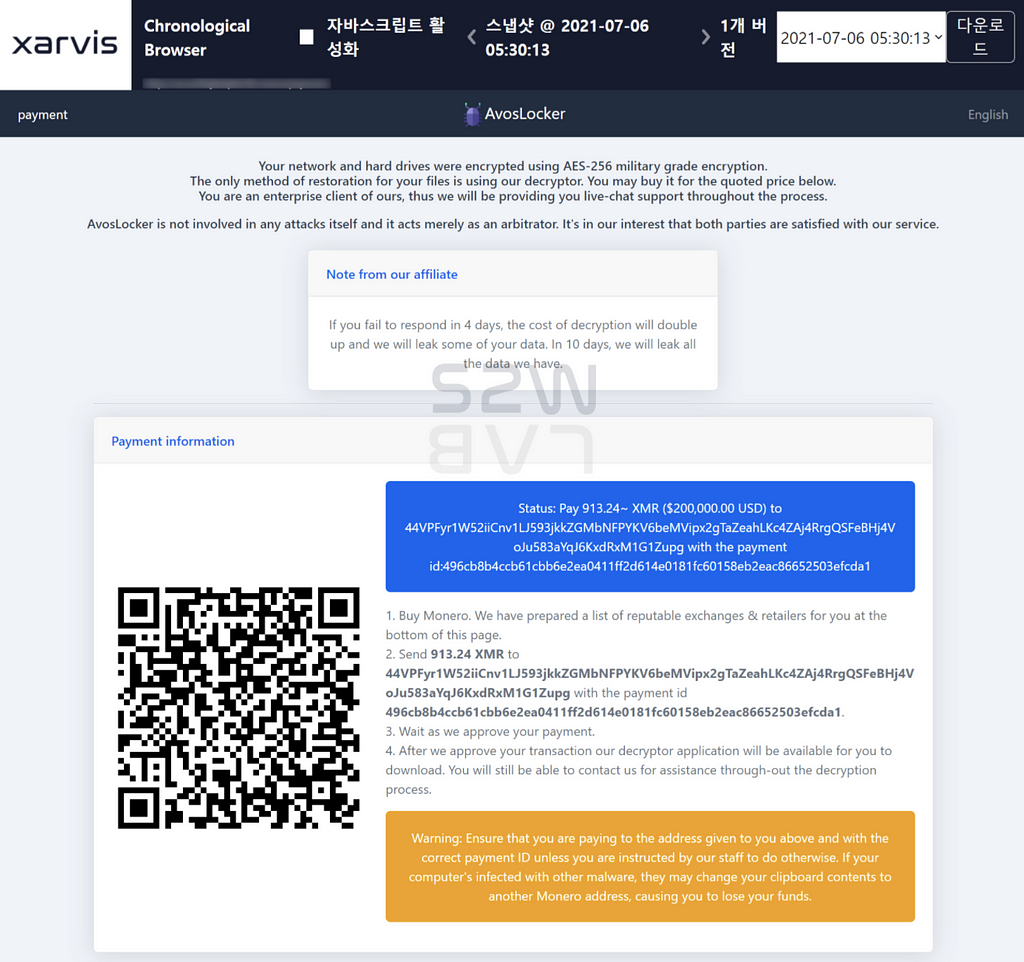
Conclusion
- The cryptocurrency addresses mentioned in eCh0raix, Darkjon, and AvosLocker require active monitoring to prevent damage and track attackers.
- With appearance of Petya ransomware builder, be aware of Petya and its mutant ransomware.

- Homepage: https://www.s2wlab.com
- Facebook: https://www.facebook.com/S2WLAB/
- Twitter: https://twitter.com/s2wlab
W2 July | EN | Story of the week: Ransomware on the Darkweb was originally published in S2W LAB BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: W2 July | EN | Story of the week: Ransomware on the Darkweb | by Hyunmin Suh | S2W BLOG | Medium