Corporate Data Matters
Co-Author: Denise Dasom Kim, Jungyeon Lim, YH Jeong @ Talon
 Image from unsplash
Image from unsplashSoW (Story of the Week) publishes a report summarizing ransomware’s activity on the Darkweb. The report includes summary of victimized firms, Top 5 targeted countries and industrial sectors, status of dark web forum posts by ransomware operators, etc.
Executive Summary
- Compared to SoW 5 months ago (W1 Jan), the number of victimized firms increased by about 2.6 times, and the ransomware threat groups increased by 1.6 times, requiring attention to ransomware attacks.
- The United States was mostly positioned at top in terms of the rate of victim infection, but as the number of active ransomware threat groups increased, the percentage of victimized firms’ country locations also varied.
- Users who worked as affiliate partners with Darkside (as a pentester) claiming to the admin of XSS forum as Darkside did not pay their portion properly, which accepted and permanently suspended the Darkside account.
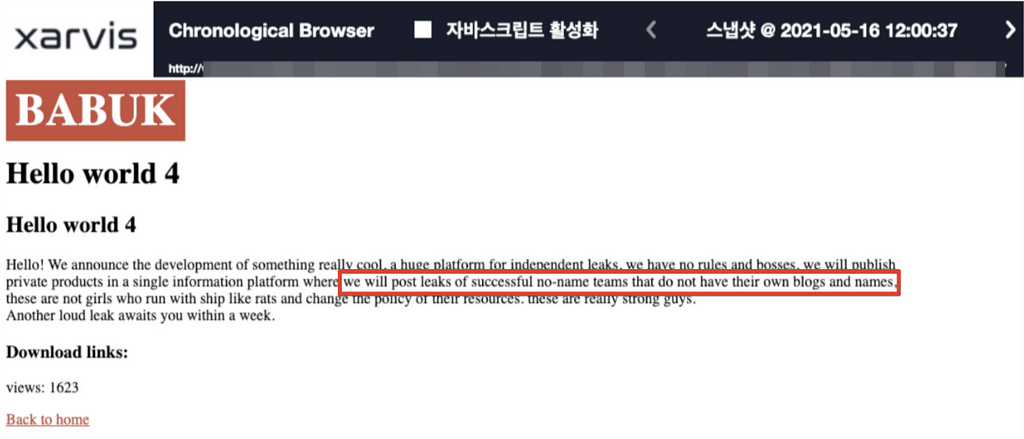
- Babuk ransomware rebranded as Payload Bin and their first victim was CD PROJEKT.
- The CD PROJEKT’s source code leak is an incident found to be related to HelloKitty ransomware as Babuk ransomware announced last week planning to integrate a platform by gathering ransomware partners who did not operate their own data leak site.
1. Weekly Status
A. Status of the victimized firms (5/24 ~ 5/30)
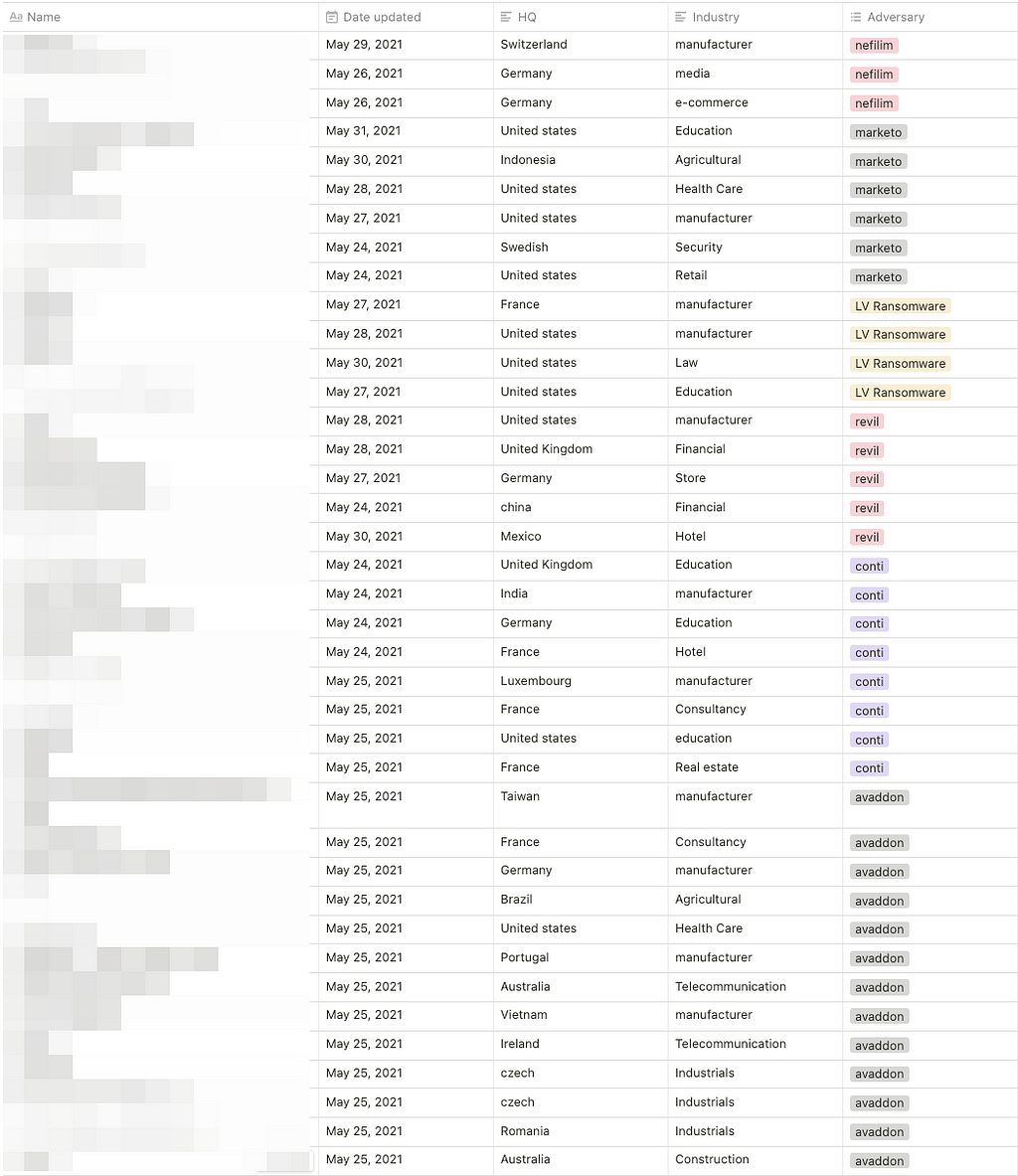
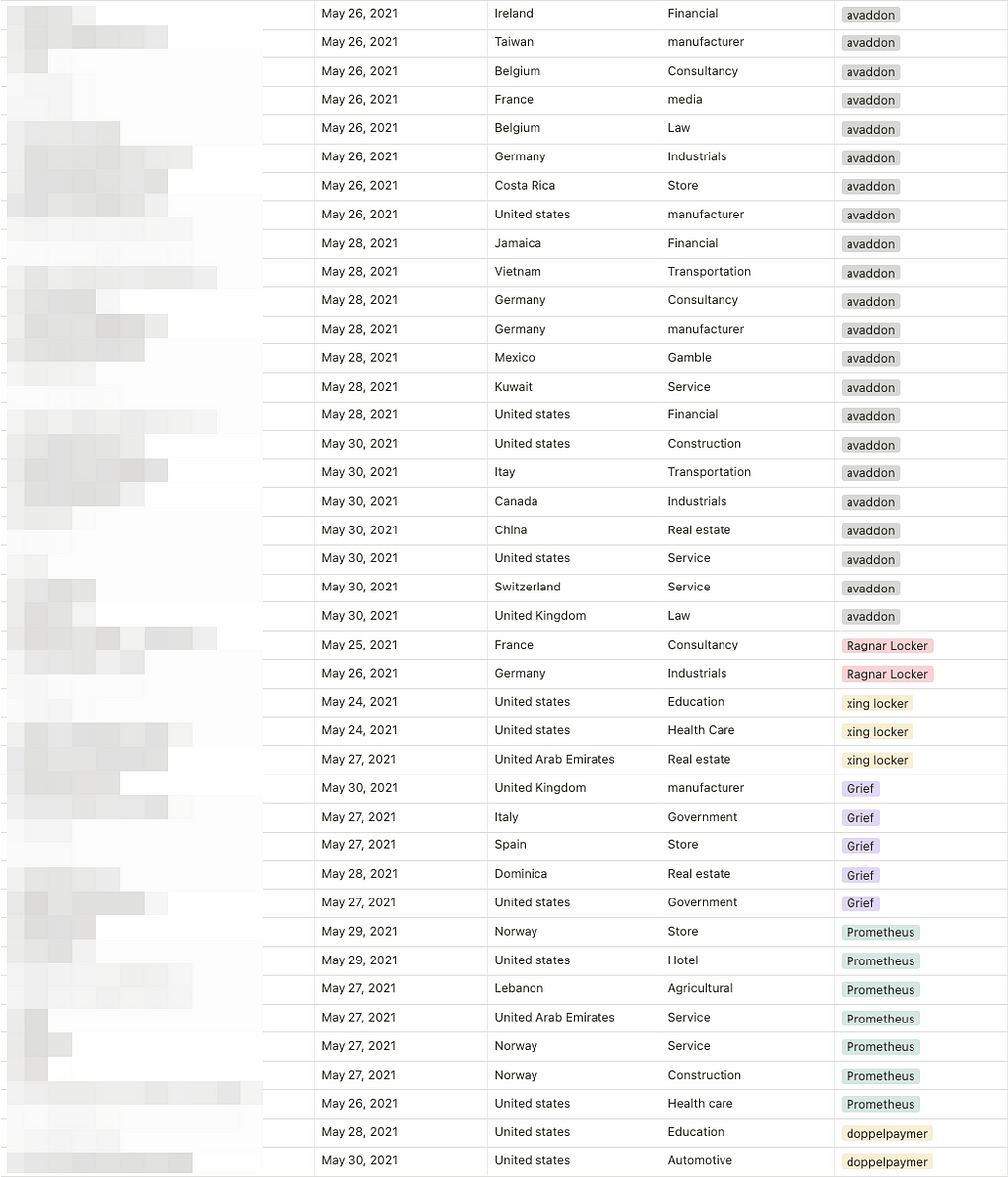
- For a week, a total of 80 victimized firms were mentioned and a change in the state of the data leaked from the victims in the ransomware site was detected.
- 11 threat groups’ activities were detected.
- Compared to previous statistics 5 months ago, the number of victims increased by about 2.6 times, and the ransomware threat groups increased by 1.6 times that needs to raise awareness about ransomware attacks.
https://medium.com/s2wlab/story-of-the-week-ransomware-on-the-darkweb-w1-jan-739c62424f2a
B. TOP 5 targeted countries
The United States was mostly positioned at top in terms of the rate of victim infection, but as the number of active ransomware threat groups increased, the percentage of victimized firms’ country locations also varied.
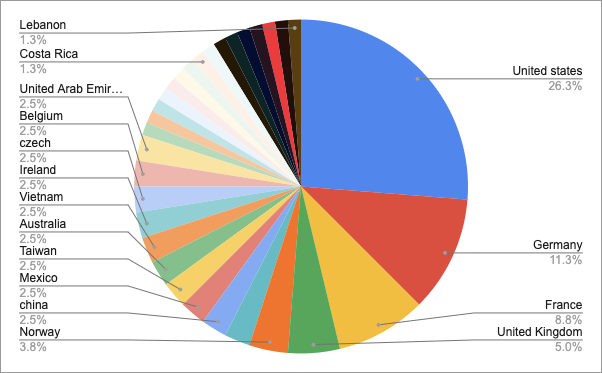
- United States — 26.3%
- Germany — 11.3%
- France — 8.8%
- United Kingdom — 5.0%
- Norway — 3.8%
C. TOP 5 targeted industrial sectors
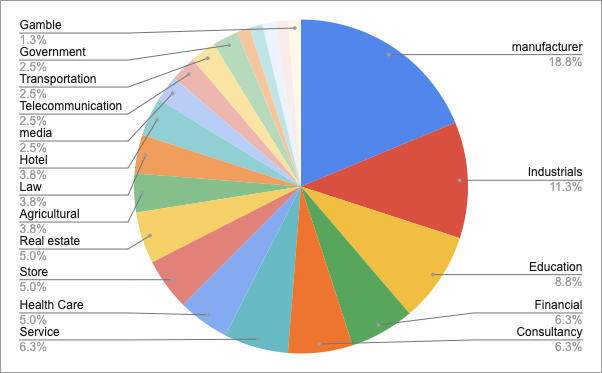
- Manufacturer — 18.8%
- industrial — 11.3%
- Education — 8.8%
- Financial & Consultancy & Service — 6.3%
- Health Care & Store & Real estate — 5.0%
2. Posts related to Ransomware threat actors @Dark Web
A. Darkside permanently banned from XSS forum
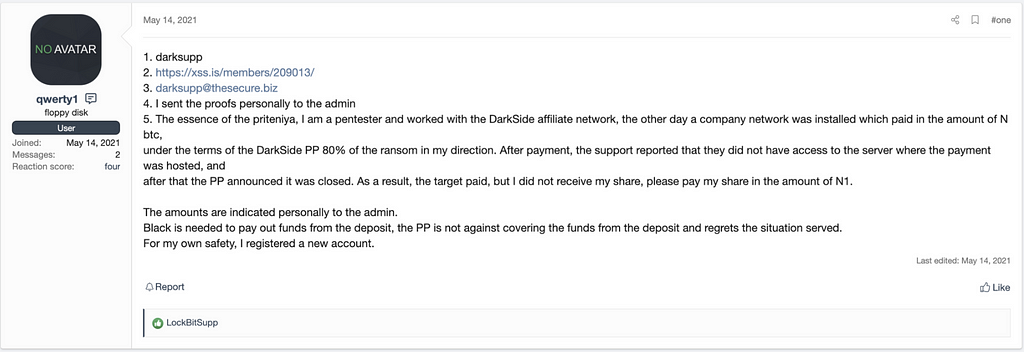
On May 14th, the user (qwety1) of the XSS Forum claimed to the admin that the user did not receive any amount working as a pentester participating with the affiliate program of DarkSide Ransomware.
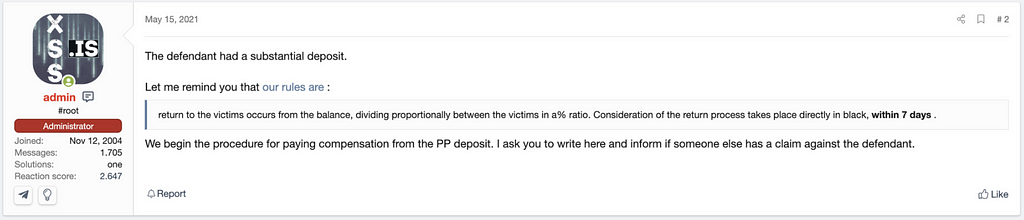
The administrator of the XSS Forum mentioned they begin the procedure for paying compensation with the rule of XSS Forum as below.
return to the victims occurs from the balance, dividing proportionally between the victims in a% ratio. Consideration of the return process takes place directly in black, within 7 days .
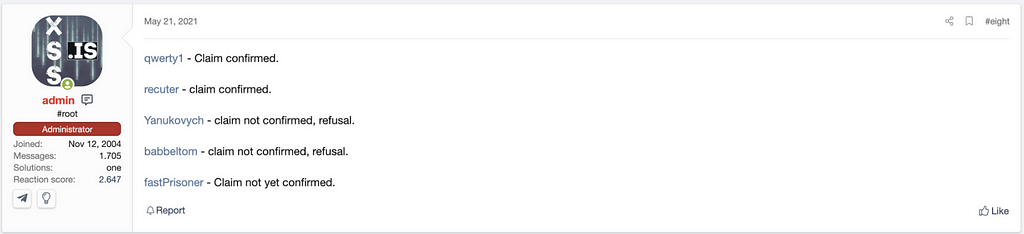
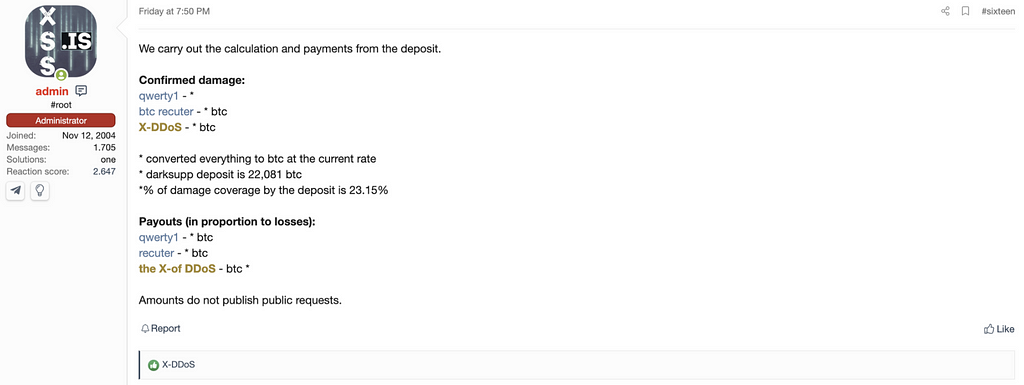
The administrator of the XSS Forum mentioned they begin the procedure for paying compensation with the rule of XSS Forum as below.
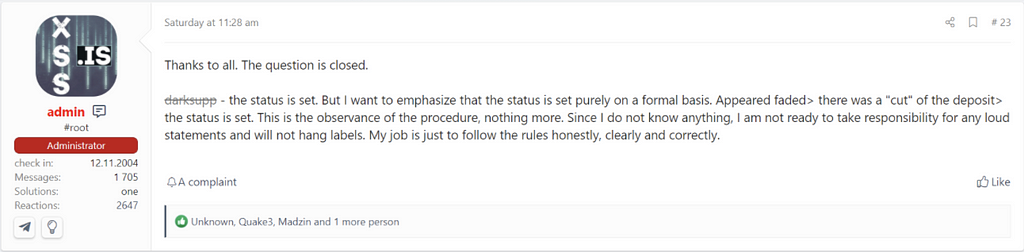
XSS.IS admin
Thanks to all. The question is closed.
darksupp(Darkside ransomware's Operator) - the status is set. But I want to emphasize that the status is set purely on a formal basis.
Appeared faded> there was a "cut" of the deposit> the status is set. This is the observance of the procedure, nothing more.
Since I do not know anything, I am not ready to take responsibility for any loud statements and will not hang labels.
My job is just to follow the rules honestly, clearly and correctly.
As a consequence, Darkside is banned by administrator violating the forum policy as a scammer.
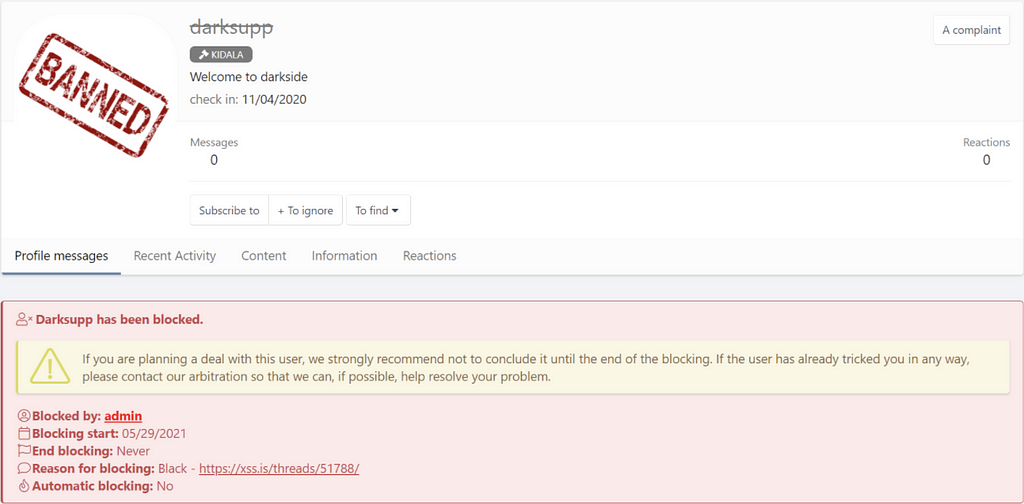
B. Babuk ransomware rebranded as Payload[.]bin
https://medium.com/s2wlab/w4-may-kr-story-of-the-week-ransomware-on-the-darkweb-2ba061070812
Last week, we covered a post where the Babuk ransomware launch an integrated platform gathering partners who don’t have a data leak site, and operate them instead. On May 31, the Babuk ransomware rebranded as Payload Bin and re-organised the homepage.
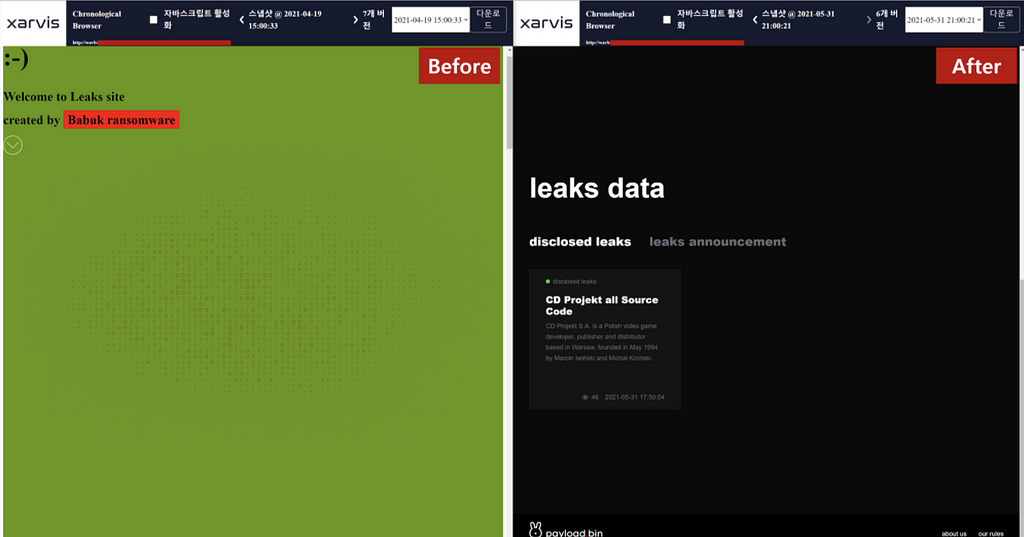
All leaks data previously disclosed by the Babuk ransomware disappeared with renewal but CD Projekt’s source code data. The CD PROJEKT’s source code leak is an incident found to be related to HelloKitty ransomware on Feb 9.
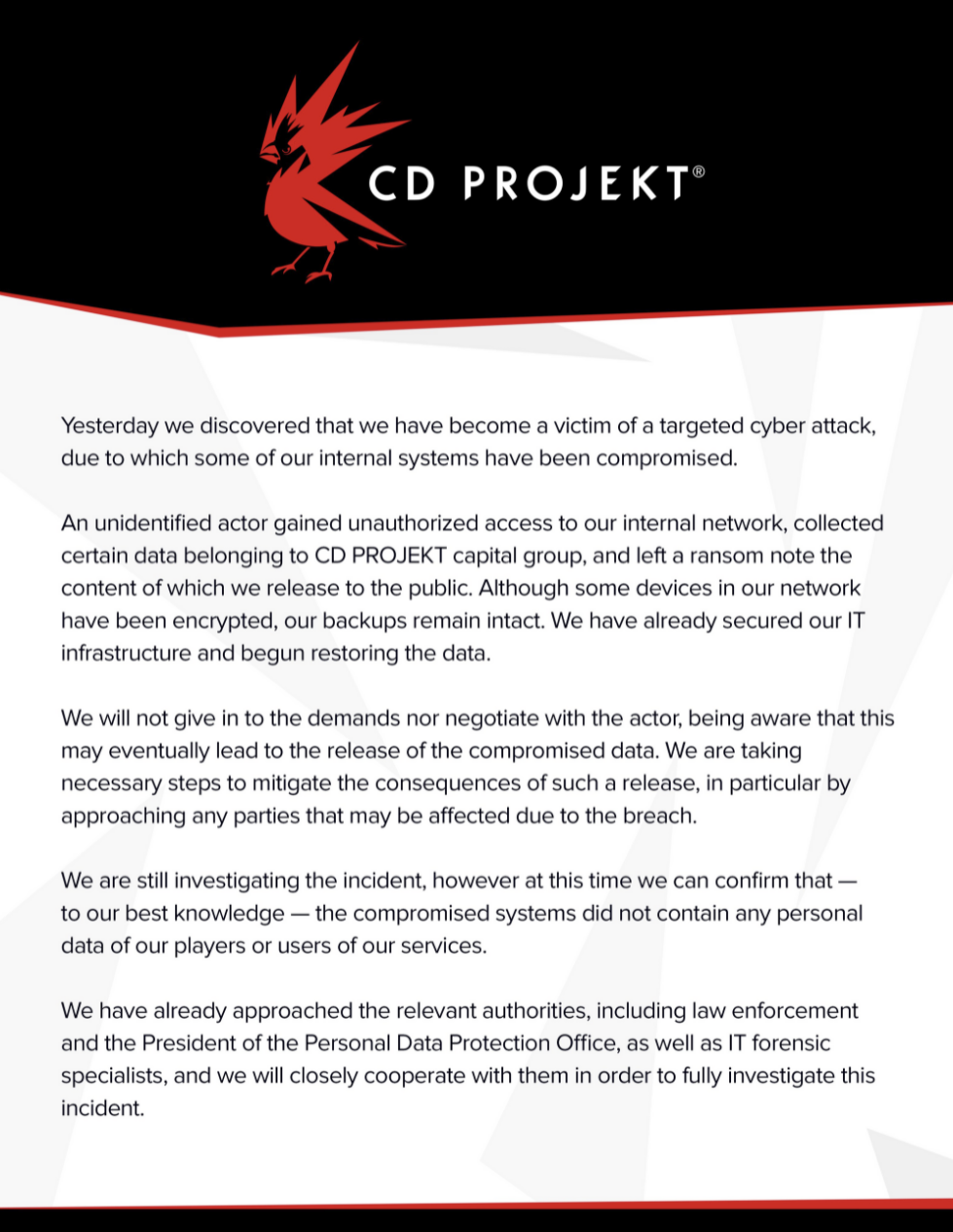 CD Projekt가 공지한 랜섬웨어 피해 내용
CD Projekt가 공지한 랜섬웨어 피해 내용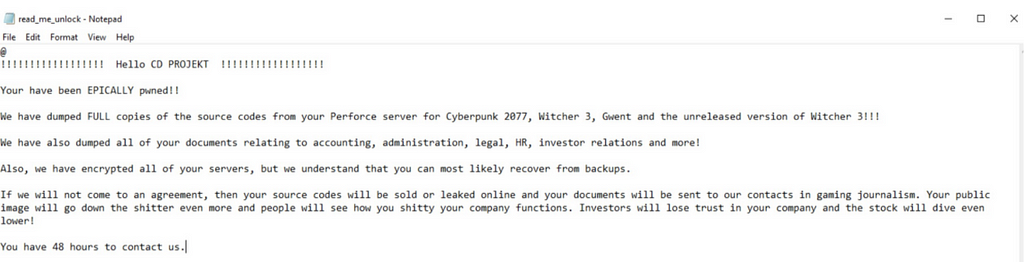 CD Projekt가 트위터를 통해 공개한 랜섬노트
CD Projekt가 트위터를 통해 공개한 랜섬노트https://twitter.com/CDPROJEKTRED/status/1359048125403590660/photo/1
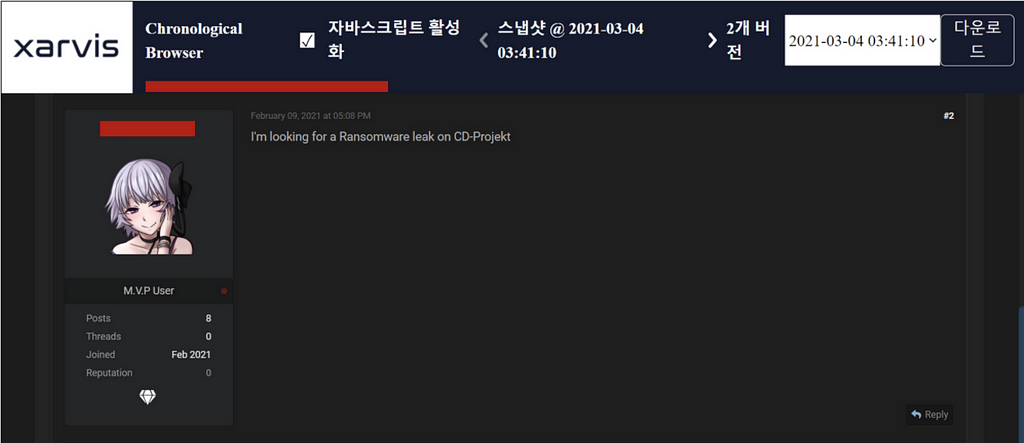
After the announcement, there was a user looking for the leaked data regarding CD Projekt’s incident.
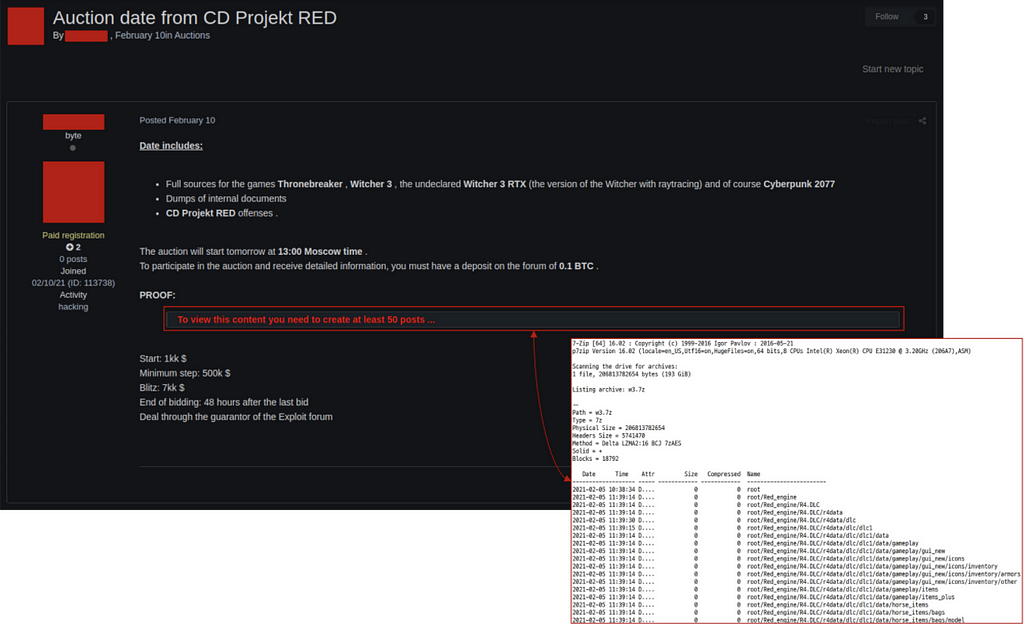
However, there wasn’t any free sharing page on DDW, rather a seller appeared trying to sell the source code of CD Projekt on DDW as a form of auction.
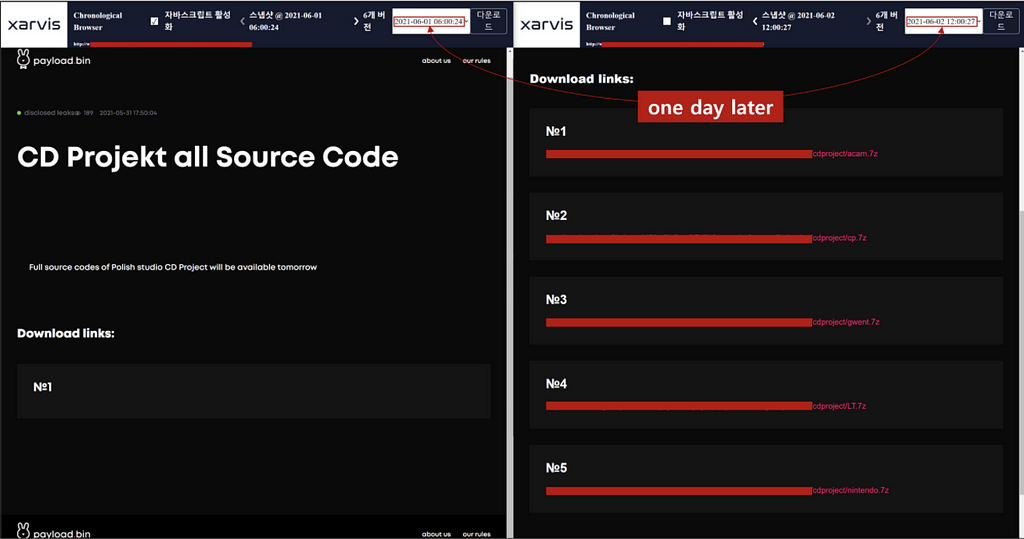
As Babuk announced, the data appears to be CD Projekt’s data which was stolen by HelloKitty ransomware regarding previous incident, and they seem to be partnered with Babuk ransomware now rebranded as Payload Bin.
Conclusion
- The number of victims mentioned on data leak site operated by ransomware is rapidly increasing compared to 5 months ago, so it needs to be vigilant
- Babuk ransomware rebranded as Payload Bin, appears to strengthen its strategy of threatening victims by focusing on exfiltrating the data by partnering with the previously active ransomware groups who did not have their own data leak page.

- Homepage: https://www.s2wlab.com
- Facebook https://www.facebook.com/S2WLAB/
- Twitter https://twitter.com/s2wlab
- Facebook https://www.facebook.com/S2WLAB/
- Twitter https://twitter.com/s2wlab
W1 Jun | EN | Story of the week: Ransomware on the Darkweb was originally published in S2W LAB BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: W1 Jun | EN | Story of the week: Ransomware on the Darkweb | by Hyunmin Suh | S2W BLOG | Medium