Any business sector is liable to suffer a cyberattack. But perhaps the most cautious in this respect is the industrial sector. A vulnerability in an industrial system can lead to serious economic losses, along with a loss of information, as well as damage to customers, providers, users and even to the company’s reputation.
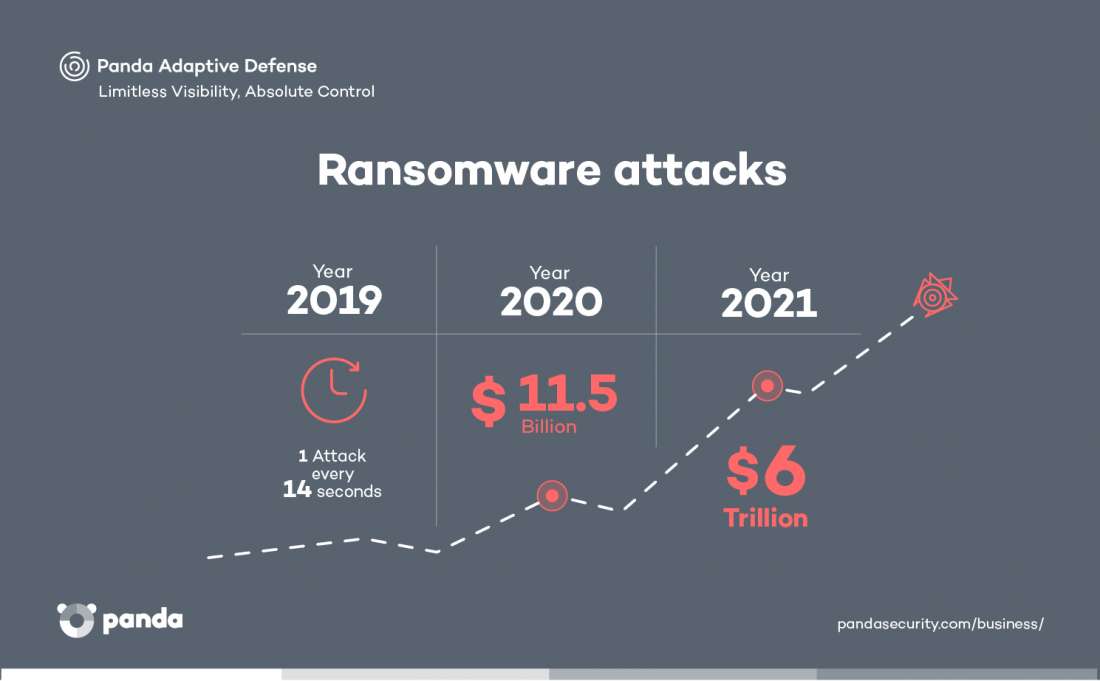
And the fact is that critical infrastructure is the kind of infrastructure that suffers most from this cybercriminal activity. According to a Cybersecurity Ventures report, a ransomware attack will be carried out on a company every 14 seconds in 2019. And that doesn’t take into account cyberattacks on individual people, which will be the vast majority of cases.
The report also takes a look at the economic costs of these vulnerabilities: ransomware attacks will costs companies as much as $11.5 billion. And by 2021, all kinds of attacks on corporate cybersecurity could cost as much as $6 trillion. In any case, the increase in damages of this kind is to be expected; all companies in every kind of industry are undertaking a digital transformation, which means that it is only logical that the number of vulnerabilities grows while this digitalization is taking place.
228 vulnerability warnings in Spain
The danger is clear; in Spain, the Incibe-CERT (Spanish national CERT) underlines this fact. Every year, it registers the vulnerability warnings in Spanish companies and organizations. And its latest report shows a clear trend: incidents are on the up. According to Incibe, in 2018, there were no fewer than 228 vulnerability warnings in the critical infrastructure of industrial control systems (ICS) in Spain. This figure represents a 14% increase compared to the 199 warnings throughout 2017.
Attacks on infrastructure of this kind, which include everything from the most traditional desktop tools to the most cutting edge Internet of Things (IoT) devices, also have their preferences. As the report shows, the most frequent vulnerabilities are those related to obtaining confidential or sensitive data from companies. It also highlights the use of algorithms to steal passwords for computers and user accounts, and hence, access company information.
The worst thing is perhaps, upon analyzing the most affected computers, we discover that the most vulnerable are those that are multipurpose, used in a vast number of different industries. This, of course, means that very few sectors (if any) are safe. When carrying out an attack, there is no doubt that cybercriminals make use of the most common paths and devices.
And these aren’t small scale cyberattacks either: 45% of them have a high level of severity, while 33% were critical. That is to say, regardless of whether or not the attacks were successful, the intentions behind them were seriously worrying for these companies’ corporate cybersecurity.
2019 won’t be any better
On the other hand, just as in 2018 warnings increased compared to 2017, this year, the landscape doesn’t look any more positive. Incibe believes that the number of vulnerability warnings will continue to grow, especially if we consider the fact that sectors such as energy and healthcare will undergo more cyberattacks of this kind.
However, it is worth remembering that the the increase in the number of warnings can’t simply be put down to an increase in cybercriminal activity; the fact that companies often reinforce their own cybersecurity control systems could also have a hand in it.
How to avoid vulnerabilities in critical infrastructure
In any event, companies must take steps to properly protect their cybersecurity.
1.- Passwords. The use of brute force to try to crack passwords is on the up. This means that it is a very good idea to reinforce verification systems for devices. Although we’ve already discussed the fact that two-factor authentication isn’t foolproof, it will certainly make things more difficult for cybercriminals.
2.- Encryption. The goal of most of these cyberattacks is to gain access to sensitive or confidential information. As such, organizations need to ensure that they’re using appropriate encryption on this data so that, even if someone does manage to get their hands on it, decrypting it will be that much more complex.
3.- Control of processes. The best was to know if there is suspicious activity afoot in an IT system is to monitor what is going on at all times. Solutions such as Panda Adaptive Defense monitor all processes in real time, detect unusual activity and thus stop any threats before they can happen.
4.- Isolation. The Incibe warns that a significant proportion of vulnerabilities occur in infrastructures that cybercriminals can access remotely. It is therefore essential that the most sensitive processes and systems be properly isolated and, wherever possible, on networks with no Internet connection.
It is not possible for a company to be completely sure that it will never experience an attack that will threaten its cybersecurity. However, what it can do is to take appropriate measures to reduce the likelihood and to reduce the fallout from such an attack as much as possible. If we also bear in mind the impact that a cyberattack can have on a country’s critical infrastructure, any improvement in cybersecurity strategy is most welcome.
The post Vulnerabilities in critical infrastructure increased 14% in 2018 appeared first on Panda Security Mediacenter.
Article Link: https://www.pandasecurity.com/mediacenter/news/vulnerabilities-critical-infrastructures/