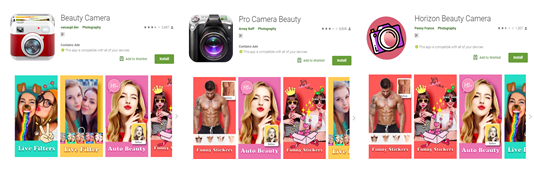
We discovered several beauty camera apps (detected as AndroidOS_BadCamera.HRX) on Google Play that are capable of accessing remote ad configuration servers that can be used for malicious purposes. Some of these have already been downloaded millions of times, which is unsurprising given the popularity of these kinds of apps. A large number of the download counts originated from Asia — particularly in India.
Figure 1. Screenshots of the malicious beauty camera apps on Google Play
Technical Analysis
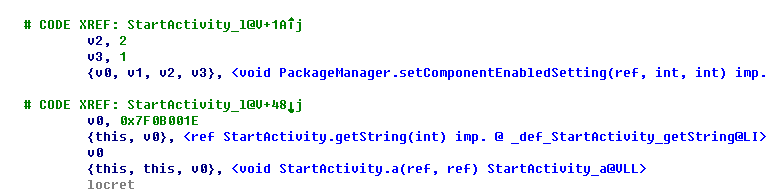
A user downloading one of these apps will not immediately suspect that there is anything amiss, until they decide to delete the app. Take, for example, the package com.beauty.camera.project.cloud, which will create a shortcut after being launched. However, it will hide its icon from the application list, making it more difficult for users to uninstall the app since they will be unable to drag and delete it. Furthermore, the camera apps use packers to prevent them from being analyzed.
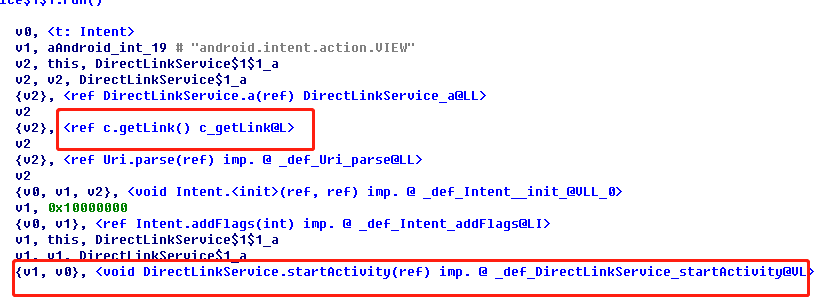
Figure 2. Code snippet to show how the malicious app hides itself from the application list
The app will push several full screen ads when users unlock their devices, including malicious ads (such as fraudulent content and pornography) that will pop up via the user’s browser. During our analysis, we found a paid online pornography player (detected as AndroidOS_PornPlayer.UHRXA) that was downloaded when clicking the pop up. Take note, however, that nothing will play, even after the user pays and executes the player.
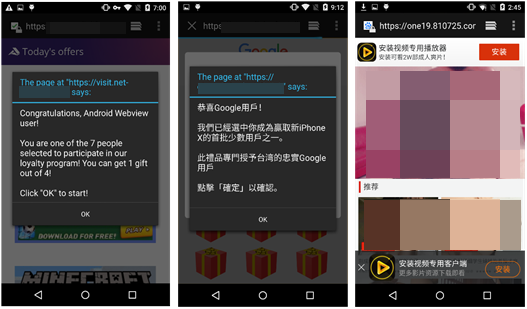
None of these apps give any indication that they are the ones behind the ads, thus users might find it difficult to determine where they’re coming from. Some of these apps redirect to phishing websites that ask the user for personal information, such as addresses and phone numbers. For example, in the figure below, clicking the “OK” button in the middle screenshot will redirect the user to a new page, which will give the user three tries to win a prize. The third try will always allow the user to win, after which a form will appear asking the user for detailed information.
Figure 3. Screenshots of the pop-up ads. The Chinese text in the middle screenshot is an announcement that the user has won an iPhone X. Clicking OK on the pop ups will bring up a phishing website
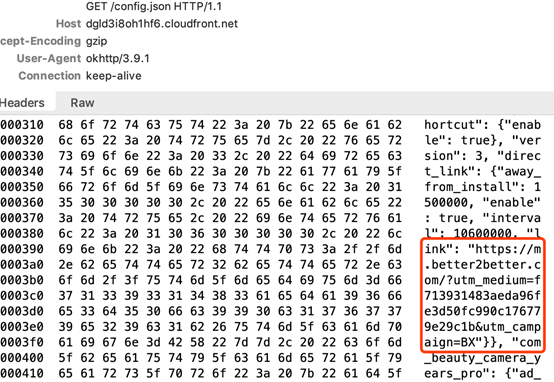
The app will download an ad configuration from the following remote servers and external URLs, which will analyze the target device to determine the advertisement’s behavior:
- hxxps://d3pukqxlxhielm.cloudfront.net/congfig[.]json
- hxxps://dgld3i8oh1hf6.cloudfront.net/congfig[.]json
The background service is then scheduled to parse the configuration and call the device browser.
Figure 4 and 5. Network traffic and code snippet showing how the unwanted ads pop up by browser
Another set of malicious camera apps
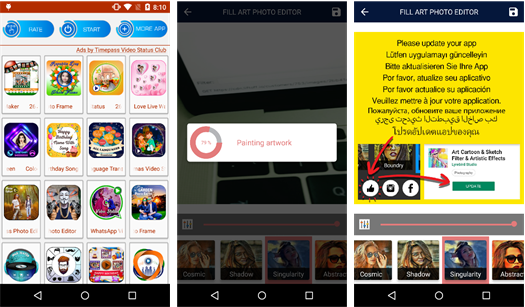
Further investigation led to another batch of photo filter-related apps that share similar behavior on Google Play. These apps seemingly allows users to “beautify” their pictures by uploading them to the designated server. However, instead of getting a final result with the edited photo, the user gets a picture with a fake update prompt in nine different languages. The authors can collect the photos uploaded in the app, and possibly use them for malicious purposes — for example as fake profile pics in social media.
Figure 6: The Fill ART Photo Editor (middle: the “editing process”, right: the fake update)
The remote server used by these apps is encoded with BASE64 twice in the code. In addition, several of these apps can also hide themselves via the same hidden technique mentioned above.
Google has already taken down these apps at the time of writing.
Figure 7: Malicious Camera Filter Apps downloaded from Google Play
Recommendations
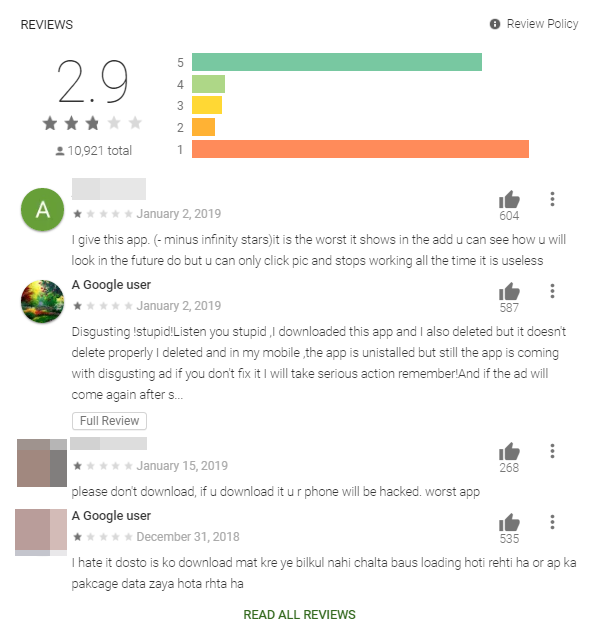
Given that many of these malicious apps take great pains to look as legitimate as possible, users should always investigate the legitimacy of an app. One good method of doing this is by checking reviews from other users. If the reviews mention any kind of suspicious behavior, then it might be a good idea to refrain from downloading the app.
Figure 6. Reviews from one of the apps. Most of the scores are either 5-star or 1-star, in a “U” shaped curve, which might indicate that the legitimate reviewers are giving it a low rating, while the fake ones are giving it as high a rating as possible
Indicators of Compromise (IoCs)
| Package | Label | Installs |
| com.beauty.camera.years.pro | Pro Camera Beauty | 1,000,000+ |
| com.cartoon.art.photo.ygy.camera | Cartoon Art Photo | 1,000,000+ |
| com.lyrebirdstudio.emoji_camera | Emoji Camera | 1,000,000+ |
| art.eff.filter.photo.editor | Artistic effect Filter | 500,000+ |
| art.filter.editor.imge | Art Editor | 100,000+ |
| com.beauty.camera.project.cloud | Beauty Camera | 100,000+ |
| com.selfie.camerapro.pro | Selfie Camera Pro | 100,000+ |
| com.camera.beauty.kwok.horizon | Horizon Beauty Camera | 100,000+ |
| com.camera.ygysuper.photograph | Super Camera | 100,000+ |
| com.effects.art.photo.for.self | Art Effects for Photo | 100,000+ |
| com.solidblack.awesome.cartoon.art.pics.photo.editor | Awesome Cartoon Art | 100,000+ |
| com.photoeditor.artfilterphoto | Art Filter Photo | 50,000+ |
| com.photocorner.artfilter.arteffect.prizma | Art Filter Photo Effcts | 10,000+ |
| com.picfix.cartoonphotoeffects | Cartoon Effect | 10,000+ |
| com.picsartitude.arteffect | Art Effect | 10,000+ |
| com.csmart.photoframelab | Photo Editor | 5,000+ |
| com.wallpapers.nuclear.hd.hd3d.best.live.nuclear | Wallpapers HD | 5,000+ |
| com.perfectmakeup.magicartfilter.photoeditor.selfiecamera | Magic Art Filter Photo Editor | 5,000+ |
| appworld.fillartphotoeditor.technology | Fill Art Photo Editor | 1,000+ |
| com.artflipphotoediting | ArtFlipPhotoEditing | 1,000+ |
| com.artphoto.artfilter.artpiczone | Art Filter | 1,000+ |
| com.photoeditor.cartoonphoto | Cartoon Art Photo | 1,000+ |
| com.photoeditor.prismaeffects | Prizma Photo Effect | 1,000+ |
| com.cmds.artphotofiltereffect | Cartoon Art Photo Filter | 100+ |
| com.latestnewappzone.photoartfiltereditor | Art Filter Photo Editor | 100+ |
| com.livewallpaperstudio.pixture | Pixture | 100+ |
| app.pixelworlds.arteffect | Art Effect | 50+ |
| timepassvideostatus.photoarteffect.cartoonpainteffect | Photo Art Effect | 10+ |
| com.techbuzz.cartoonfilter | Cartoon Photo Filter | 5+ |
The post Various Google Play “Beauty Camera” Apps Sends Users Pornographic Content, Redirects Them to Phishing Websites and Collects Their Pictures appeared first on .
Article Link: http://feeds.trendmicro.com/~r/Anti-MalwareBlog/~3/2_zDTFGDZHw/