I was showing a colleague how to use my patched SpiderMonkey to analyze obfuscated JavaScript, when I realized I had not yet released my latest version.
SpiderMonkey is an opensource JavaScript interpreter. I modified it to help with malware analysis. For example, my version will dump the argument of the eval function, and I’ve implemented document.write and window.navigate (dumping arguments too).
This latest version was developed a couple of years ago (that’s why it’s still based on SpiderMonkey 1.7) to dump arguments to stdout. Previous versions of my patched SpiderMonkey dump arguments to files, in this latest version, you can choose were to dump the arguments. A method was added to object document: document.output(arg). This output method takes one argument: a string. The following values may be used as argument:
- ‘a’ ASCII/HEX dump
- ‘x’ HEX dump
- ‘d’ raw dump
- ‘A’ pure ASCII/HEX dump
- ‘x’ pure HEX dump
- ‘d’ pure raw dump
- ‘f’ file dump
The ZIP file you can download contains source code and executables for Windows, Linux and OSX. There are 2 versions: js-ascii.exe and js-file.exe. Both are identical, except for their default output behavior. js-file.exe will output arguments by default to files (and thus behave like previous versions of SpiderMonkey) and js-ascii.exe will output arguments by default as ASCII/HEX dump to the console.
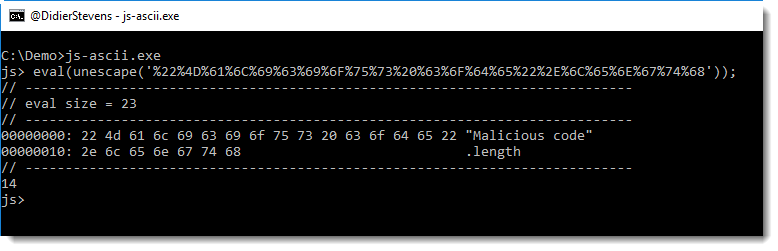
I prefer to use js-ascii.exe now, and I’ve renamed it to js.exe (like previous versions).
The ASCII/HEX dump allows me to see exactly, at the byte-level, what is passed as argument to eval.
js-1.7.0-mod-c.zip (https)
MD5: B14B522E81366D6AAF3B7EB235B62707
SHA256: 2CCB2F57DF706A8EE689C54B18A0EA7BB052EF08BA233F1319119825DB32927B
Article Link: https://blog.didierstevens.com/2018/04/19/update-patched-spidermonkey/