Introduction :- Tonight in this blog, we’ll looking at the unpacking of sample from Russian Foreign Intelligence Unit “APT29” aka “Cozy Bear” / “The Dukes”.
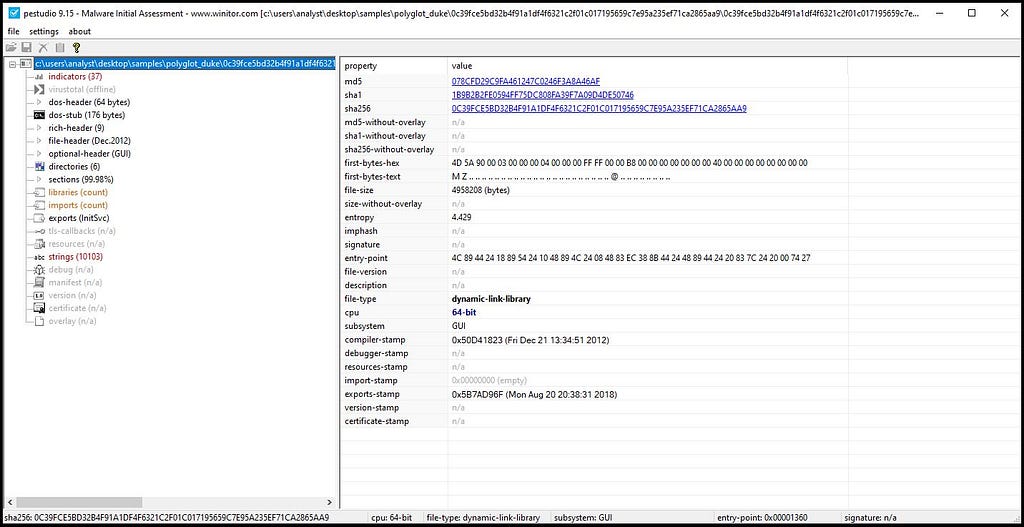
Before starting off with debugger for the dynamic unpacking of “Polyglot Duke” trojan we had to look the sample in the information gathering tool PE Studio for portable executable ( PE) files.
Dropping Polyglot Duke in PE Studio shows that information.Dropping the polyglot file in PE Studio most valuable is that file is a malicious 64-bit file. So, it decides that we’ll be unpacking 64-bit malicious file.
Setting Up for Unpacking :-
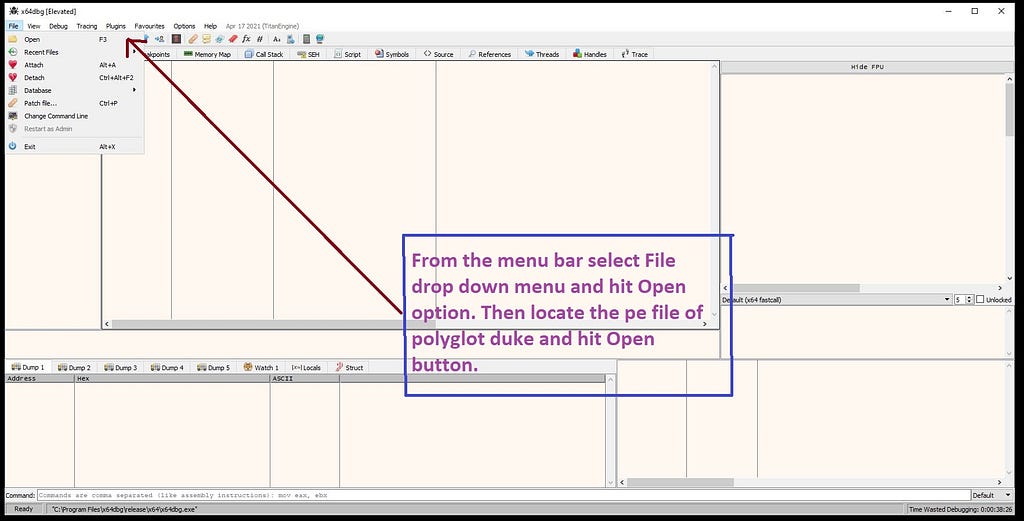
Without wasting time seeing the information on sample in PE Studio , let’s drop the file in x64-dbg which is great tool for unpacking & debugging malware for exploring it’s internals dynamically.
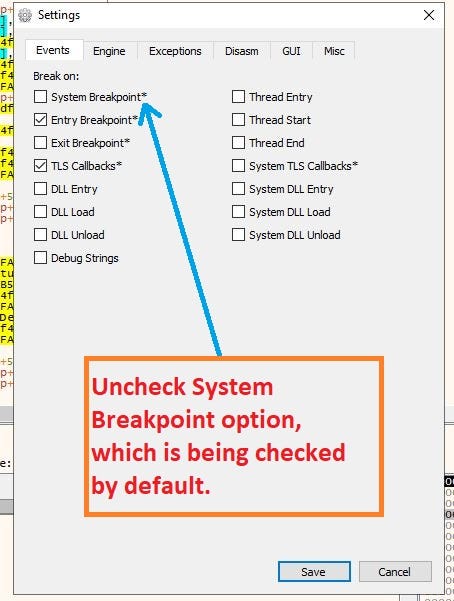
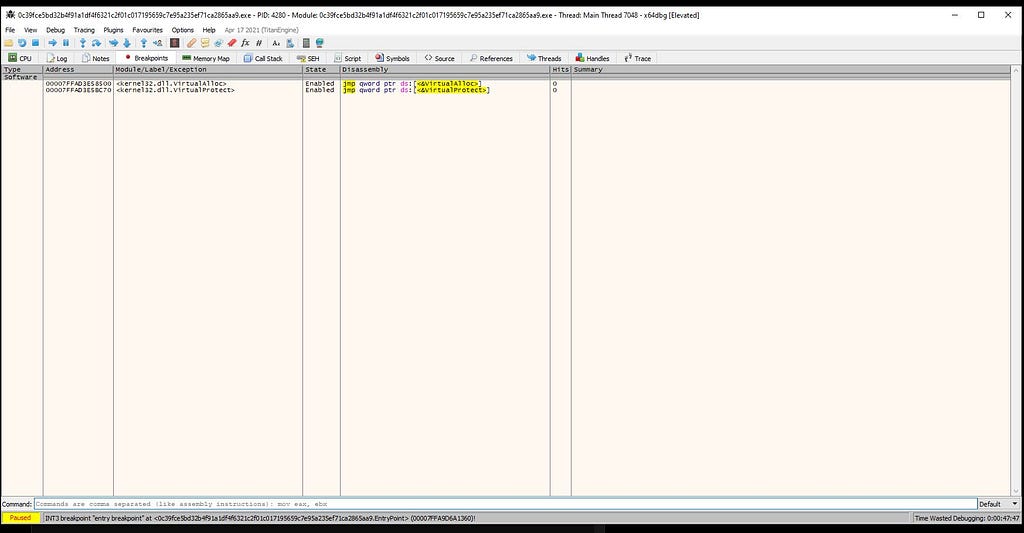
Before we open file in x64-dbg firstly uncheck the “System Breakpoint” option by going to the “Preferences” option of “Options” drop-down tab from menu bar in x64-dbg.
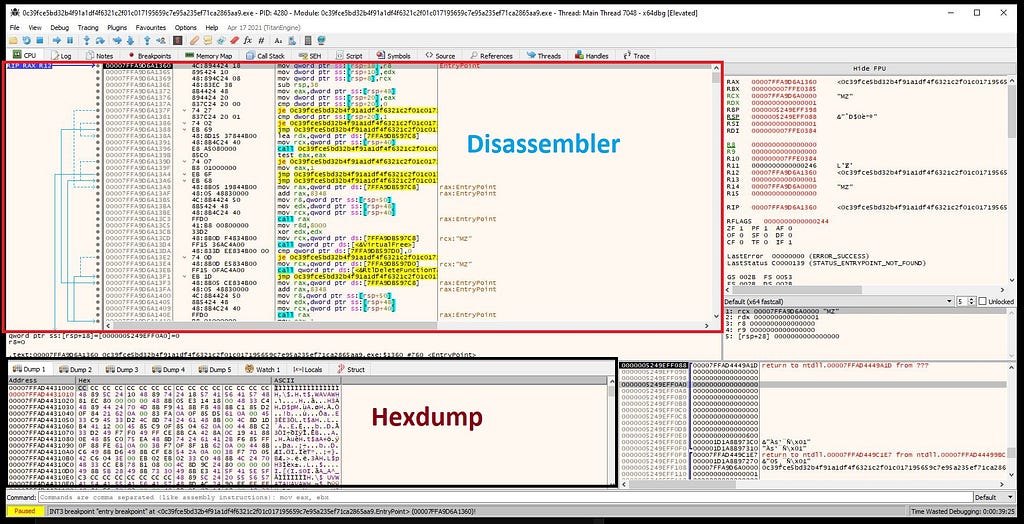
Goto Options -> Preferences and Uncheck “System Breakpoint”.x64-dbg in action before executable is being loaded.After we load the executable in x64-dbg it’ll look something like this.
x64-dbg in action after executable is being loaded.For unpacking the malicious payload from executable we have to set few breakpoints from command palette present down at the bottom in x64-dbg.
command palette in x64-dbg.For this particular sample we’ll be setting two breakpoints which are :-
- VirtualAlloc
- VirtualProtect
Note:- for setting breakpoint in x64-dbg we have to use command “bp” followed by the “breakpoint name”. Eg:- bp VirtualAlloc.
Unpacking :-
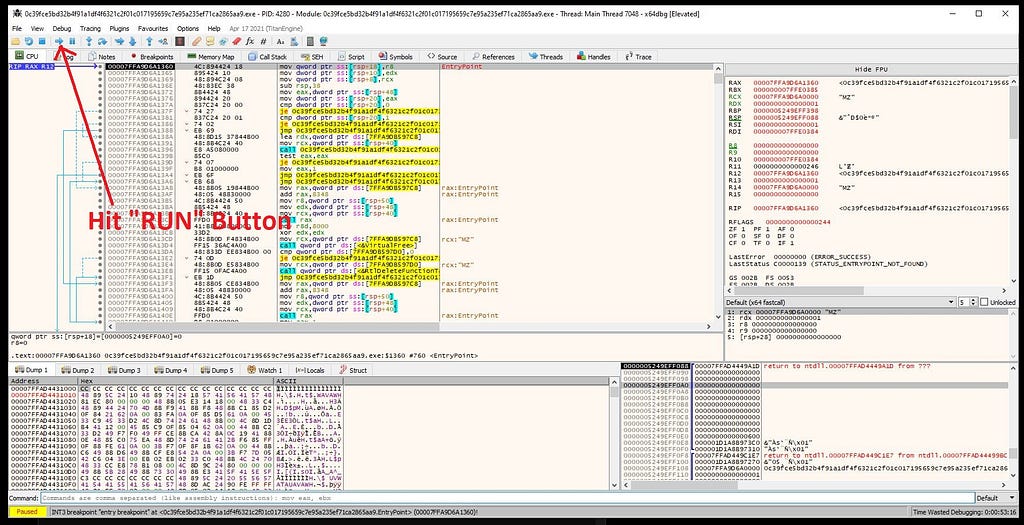
Now just hit run button present just above the disassembler window in x64-dbg.
As soon as after hitting run button , dbg stops at the breakpoint “VirtualAlloc”.
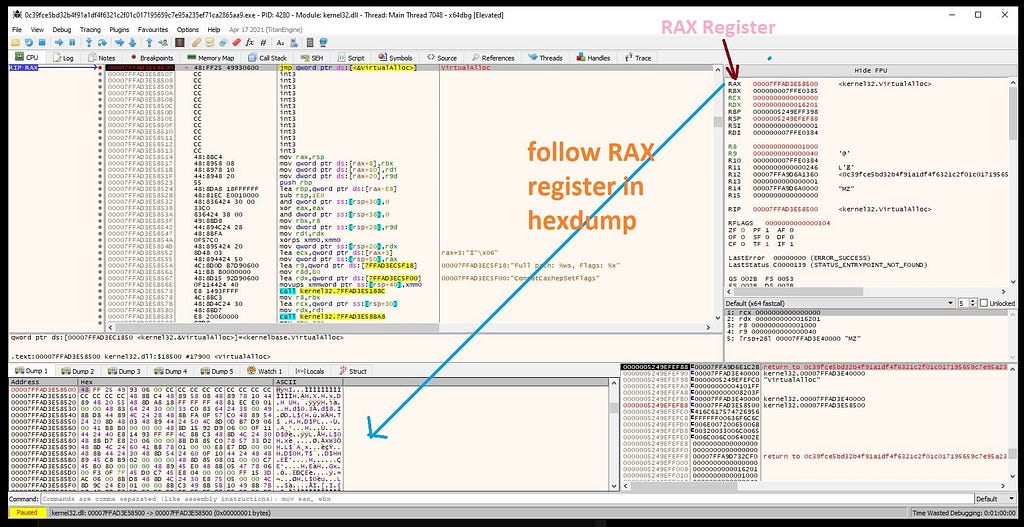
dbg stops at breakpoint VirtualAlloc.Now following up RAX register in hexdump and hitting return just after that we get this outcome.
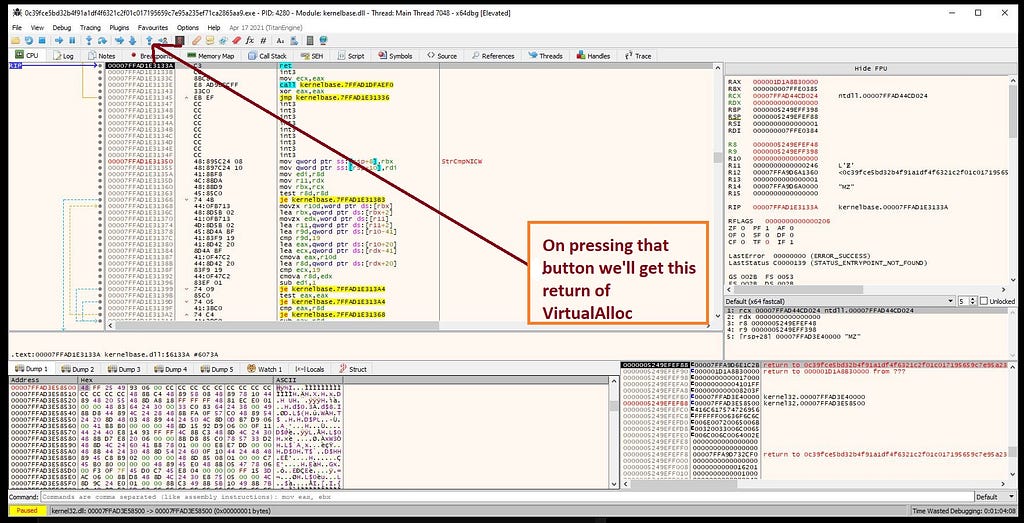
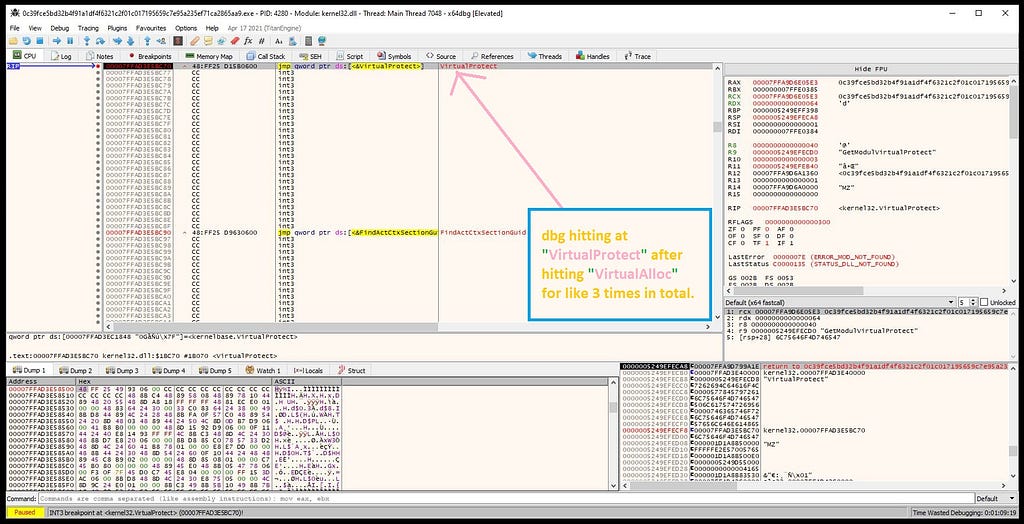
following up RAX register in hexdump shows that.On pressing return we’ll goto VirtualAlloc return.On repeating this step for another two times dbg will stops at our second setup‘ed breakpoint “VirtualProtect”.
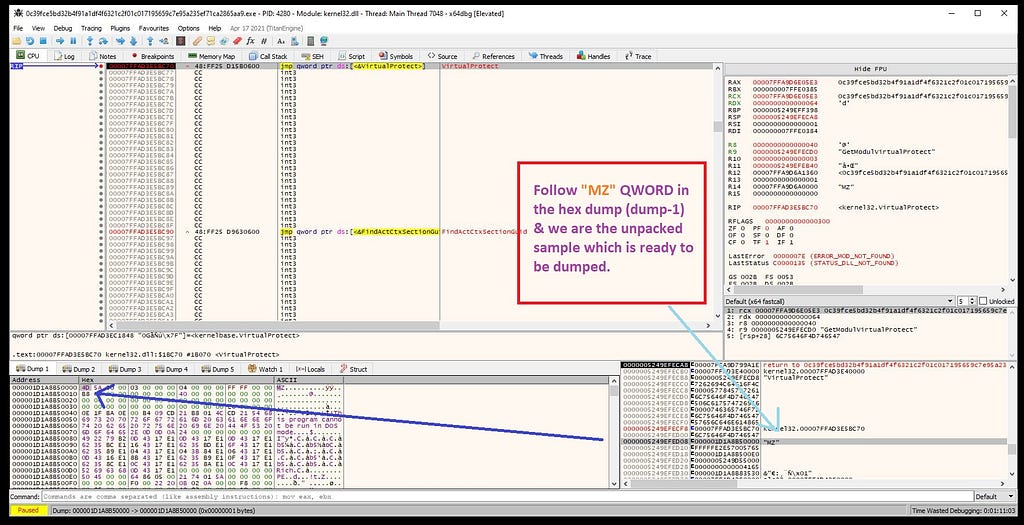
dbg hits at the VirtualProtect breakpoint on further debugging.Now we can see that “MZ” header in the window side to the hexdump. So, what we need to do is that follow the “MZ” in the hexdump (dump-1).
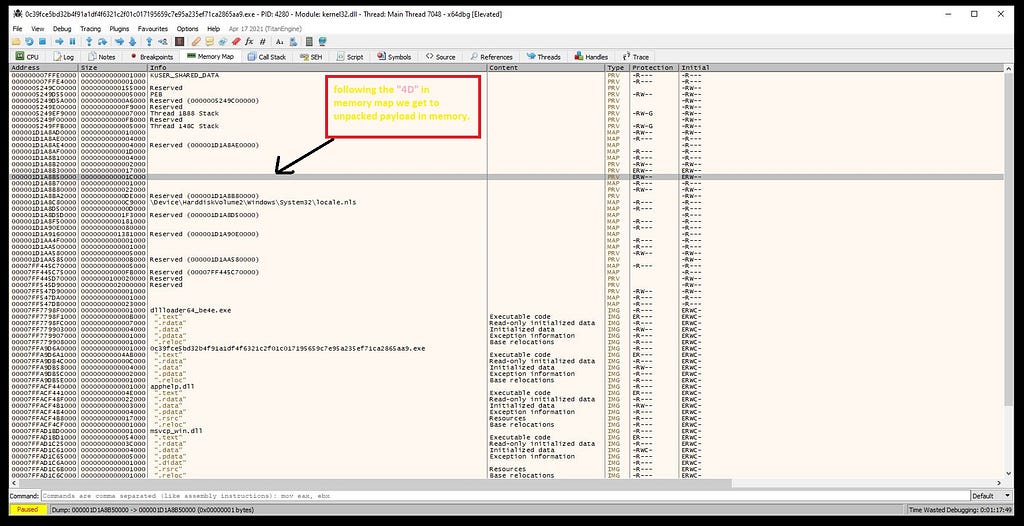
following MZ header in the hexdump(dump-1).Now following the hexdump “4D” in memory map we can dump the memory of final unpacked payload.
from here we gonna dump unpacked memory of final payload after following it from hexdump “4D”.Getting the final payload :-
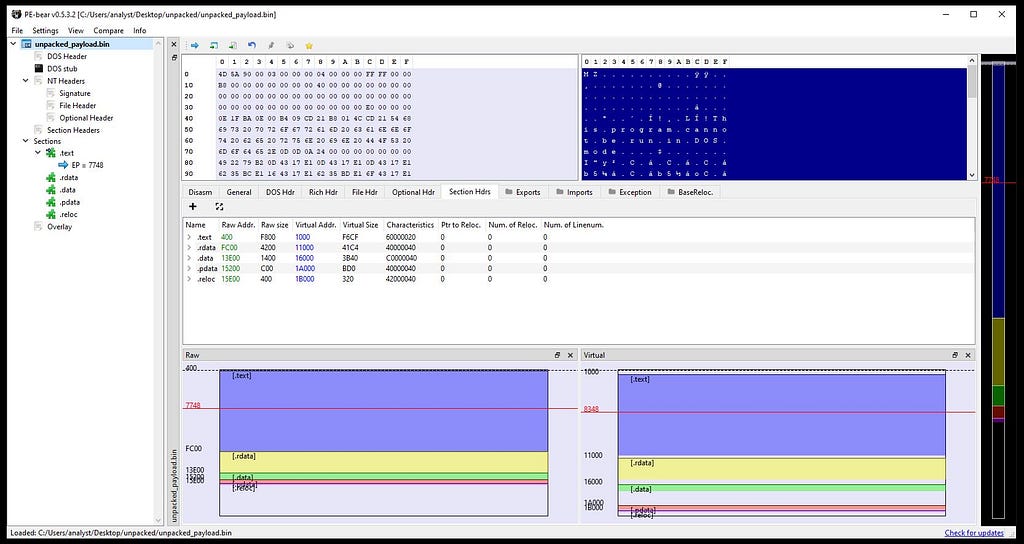
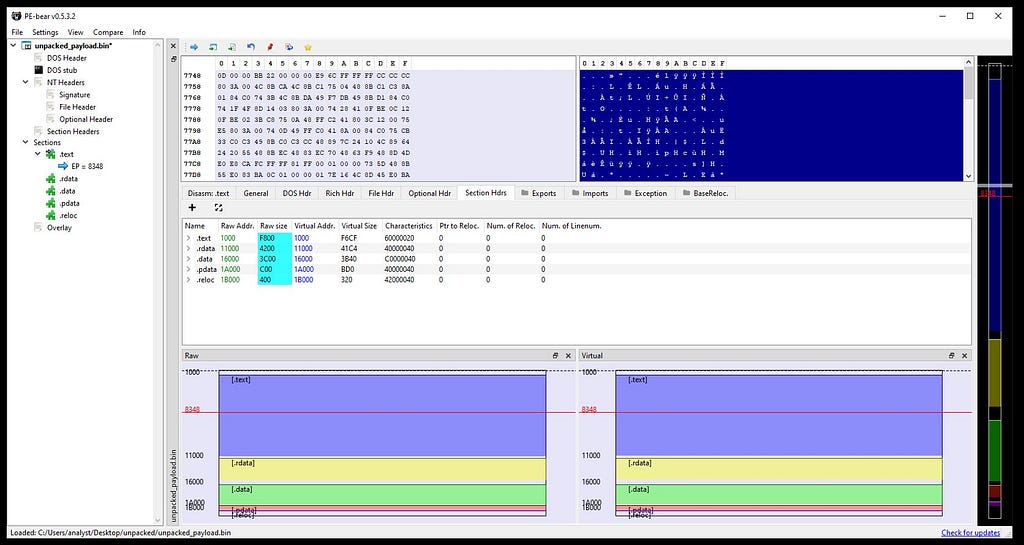
After dumping the memory of final payload we have to just fix the raw/virtual address/size just by making the similar values in raw size with the virtual size and likewise for the raw/virtual addresses values in PE Bear.
Before fixing the raw/virtual size/address in PE Bear.After fixing it looks something like this.
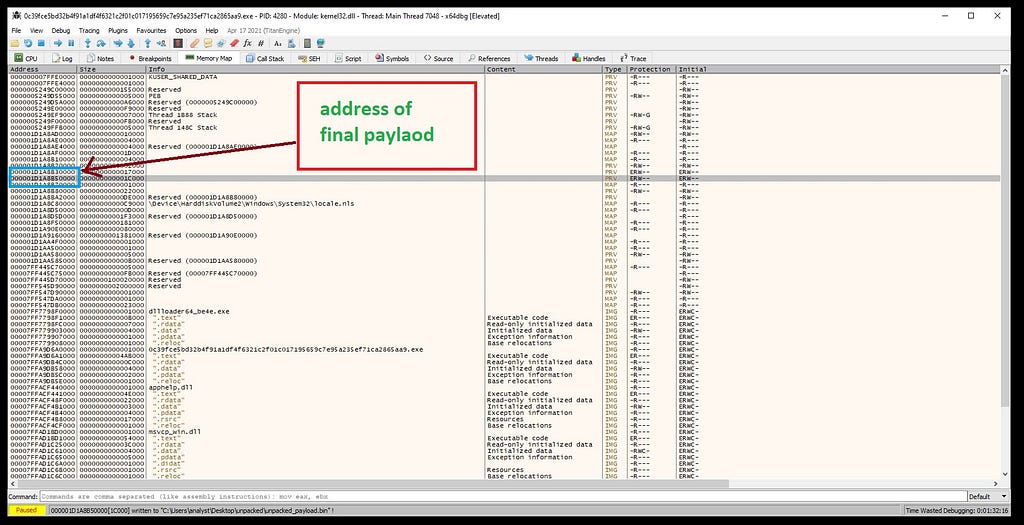
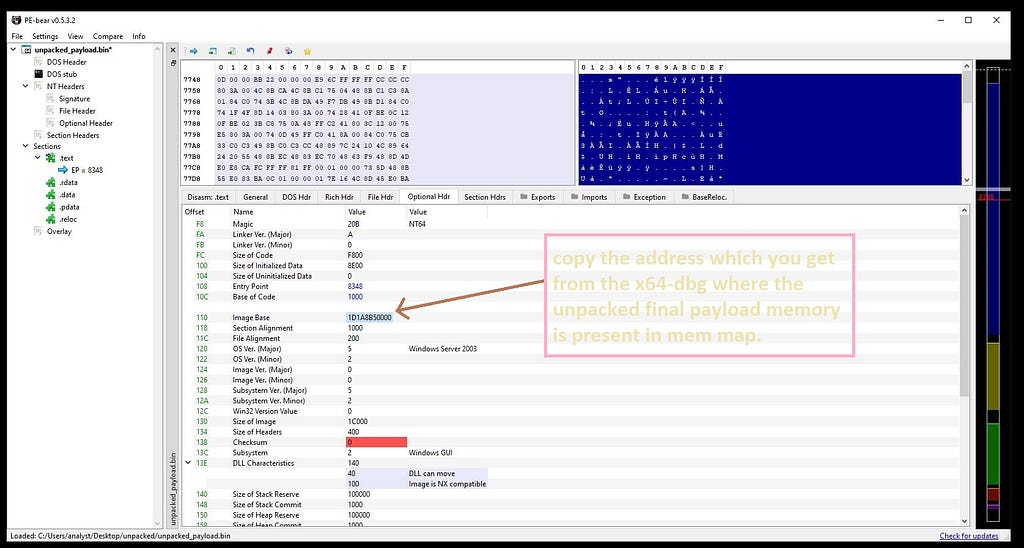
After fixing raw/virtual sizes and addresses respectively.For the get the exact un-mapped memory we need to pass the same address in the “Image base” which we are getting from the memory map of the x64–dbg where the final unpacked payload memory of “Polyglot Duke” is being present.
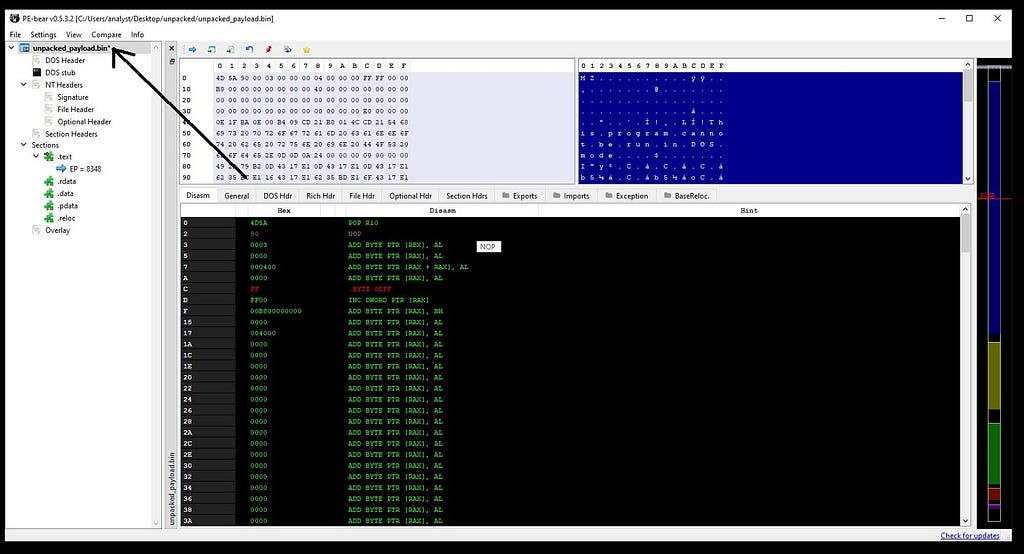
Address of final unpacked payload from x64-dbg.Copying the address in the Image Base.Now saving the executable after fixing.
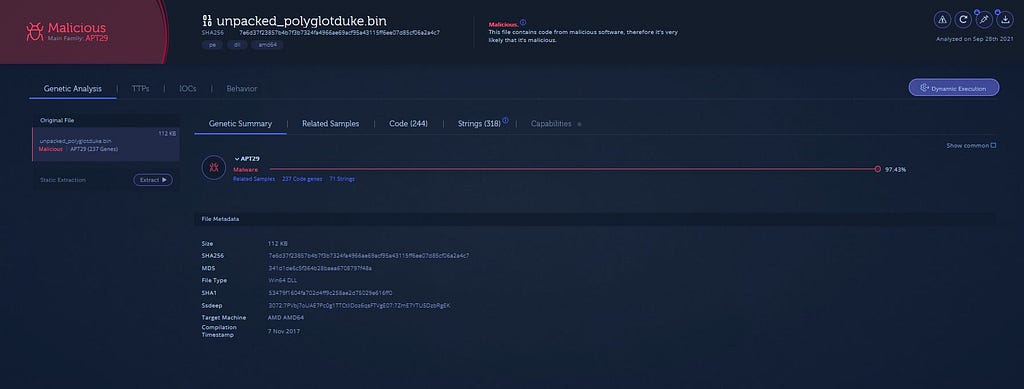
Hop towards the unpacked_payload and save as executable.<==: Confirming payload in Analyze Intezer :==>
Analyze Intezer Online Sandbox confirms that payload is from APT29.Hope you liked it. You can follow me here on Twitter.
Thanks for reading & giving your precious time for my research blog.
Article Link: Unpacking APT29's Polyglot Duke. Unpacking of sample from Russian… | by 0xthreatintel | Sep, 2021 | Medium