Uncovering APT29 tool: Trojan PolyGlot Duke — (analysis)
This blog is about analysis of Trojan packed in APT29 PolyGlot Duke.

It’s the follow-up blog on my previous blog on PolyGlot Duke in which i had unpacked the packed PolyGlot Duke. Here is the link to that blog.
Uncovering APT29 tool: Trojan PolyGlot Duke — (unpacking)
Static and Dynamic Analysis
Static Analysis (Basic)
File Information

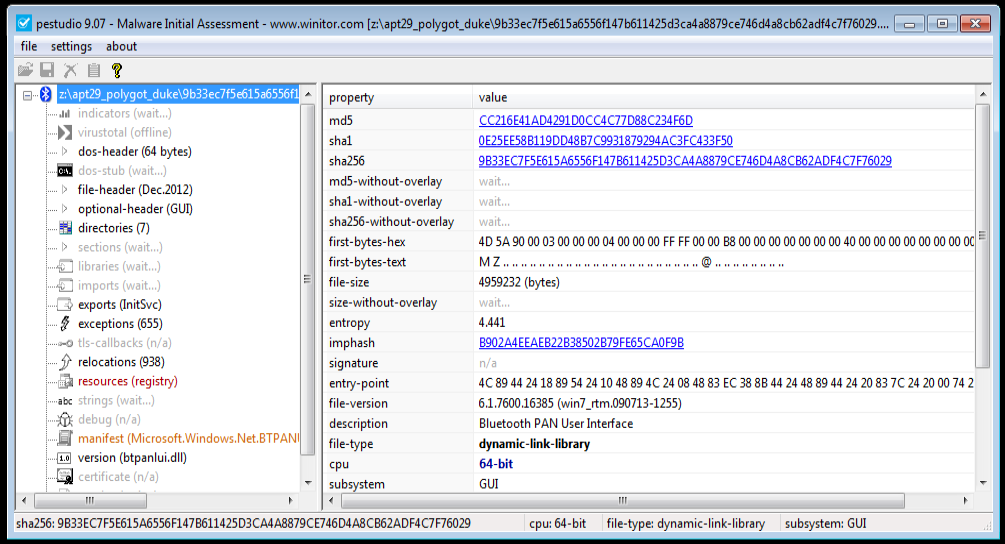 PE Studio view in right unpacked file of Trojan whereas in left is the packed file of PolyGlot Duke of APT29.
PE Studio view in right unpacked file of Trojan whereas in left is the packed file of PolyGlot Duke of APT29.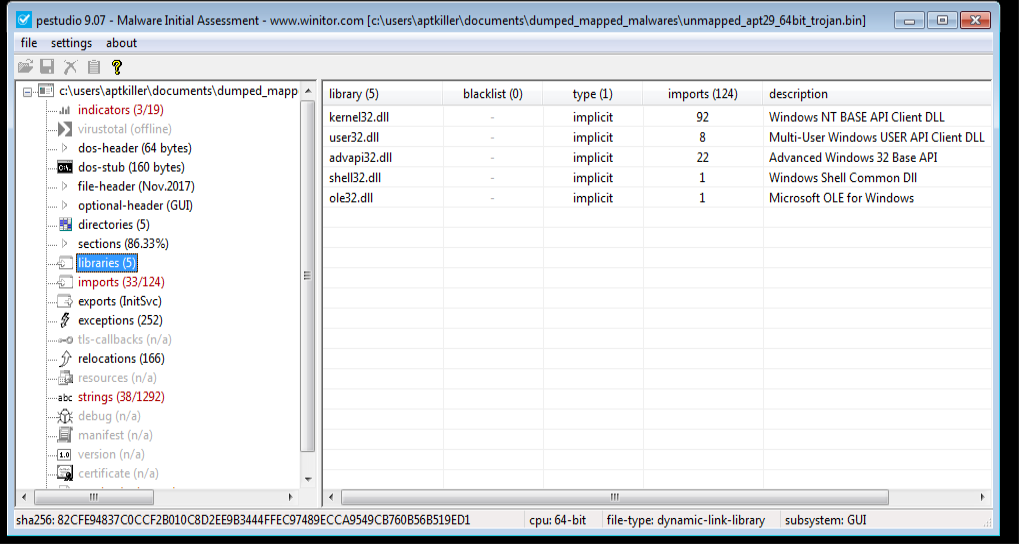
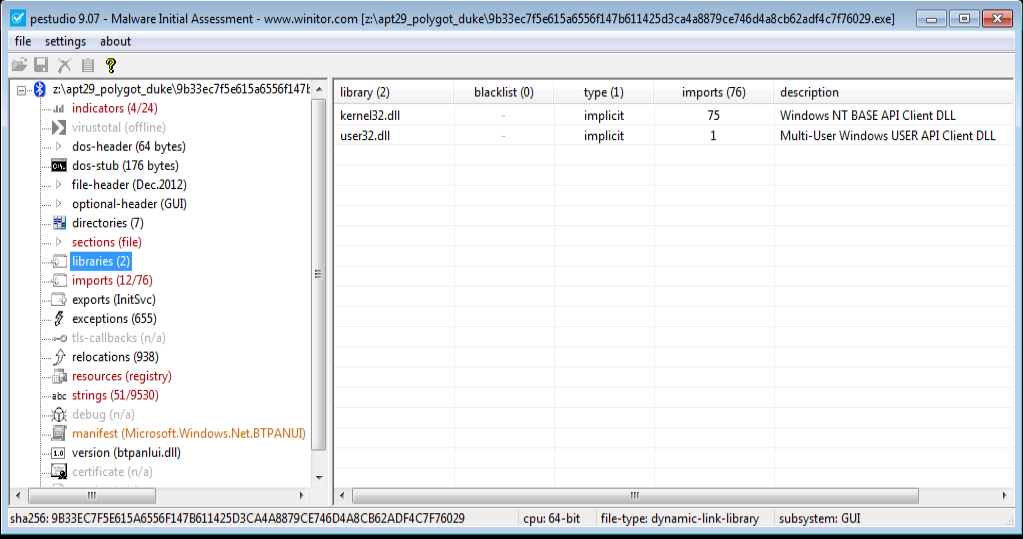 PE Studio view in right unpacked file library of Trojan whereas in left is the packed file library of PolyGlot Duke of APT29.
PE Studio view in right unpacked file library of Trojan whereas in left is the packed file library of PolyGlot Duke of APT29.
 IDA View in right unpacked file of Trojan whereas in left is the packed file of PolyGlot Duke of APT29.
IDA View in right unpacked file of Trojan whereas in left is the packed file of PolyGlot Duke of APT29.Static Analysis ( Advanced)
Starting off from exports of Trojan.
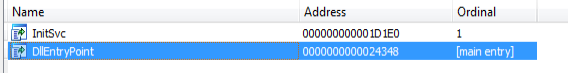 Exports made from trojan.
Exports made from trojan.Since their are two exports in trojan. Main export is DllEntryPoint.
DllEntryPoint function:
In this main entry module of trojan what’s happening is that two functions are happening.
One is “anti_VM_Analysis” and other is “call_Main_of_payload_writer”. Mainly what’s happens in “anti_VM_Analysis” is used for anti VM and Anti Analysis techniques whereas the “call_Main_of_payload_writer” is a module used for the writer that writes payload in memory.
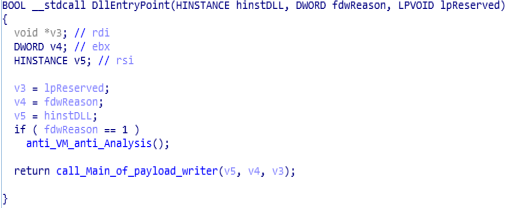
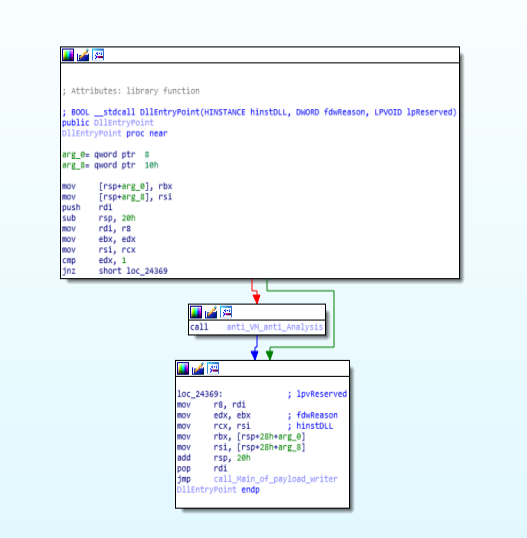 Code and Call Graph of “DllEntryPoint” function.
Code and Call Graph of “DllEntryPoint” function.anti_VM_anti_Analysis function:
This module checks and followed for the anti VM and anti analysis.
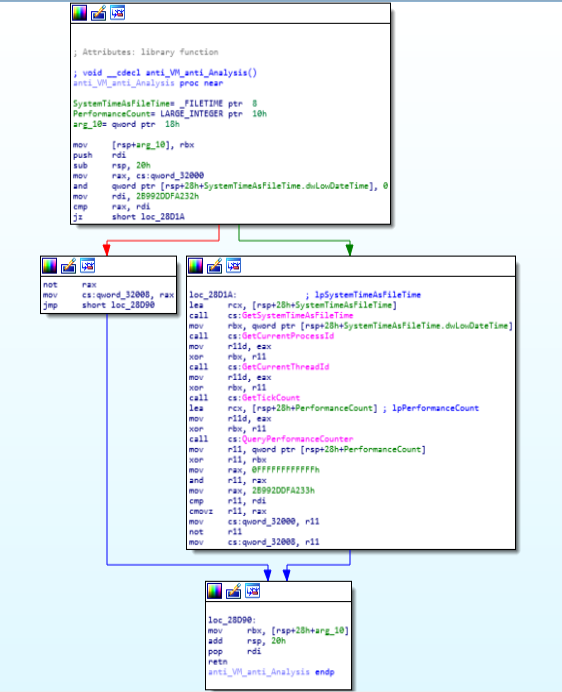
 Call Graph and Code of “anti_VM_anti_Analysis” function.
Call Graph and Code of “anti_VM_anti_Analysis” function.call_Main_of_payload_writer function:
This module calls the “Main_payload_writer” function which writes the payload in the memory and it’s is called twice in this module in conditional if statement and in the end returned as variable “v8” to the entry function.
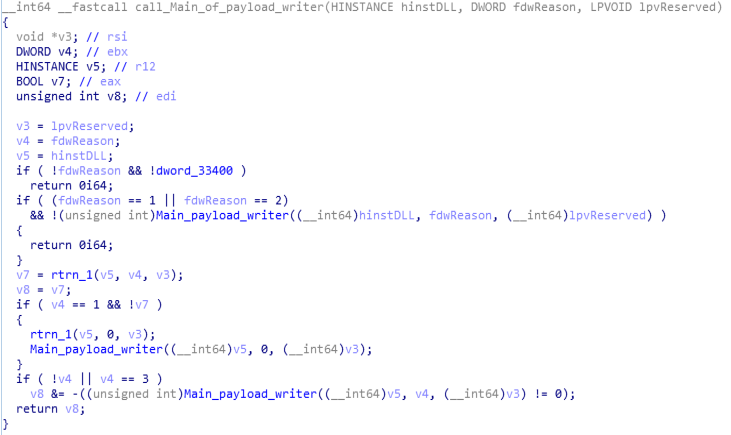 Call Graph and Code of “call_Main_of_payload_writer” function.
Call Graph and Code of “call_Main_of_payload_writer” function.Main_payload_writer function:
This modules writes payload to the memory.

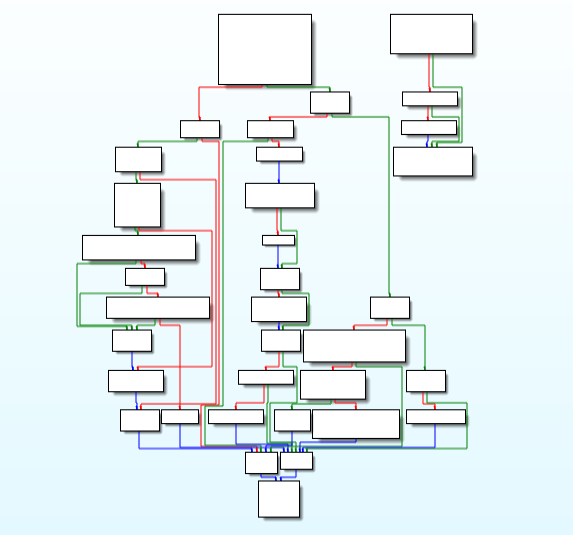 Code and Call Graph of “Main_payload_writer” function.
Code and Call Graph of “Main_payload_writer” function.goto_callr_decrypt_ops_and_heavy_cache_loader_heap_ops function:
In this module, call to module “callr_decrypt_ops_and_heavy_cache_loader_heap_ops” is being done in which decryption of payload is being done and cache memory is being filled with heavy buffer and some heap operations like HeatCreate() and Heap Free() is being done.
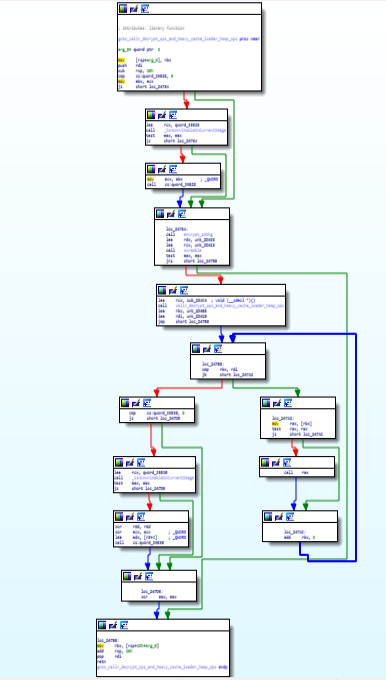
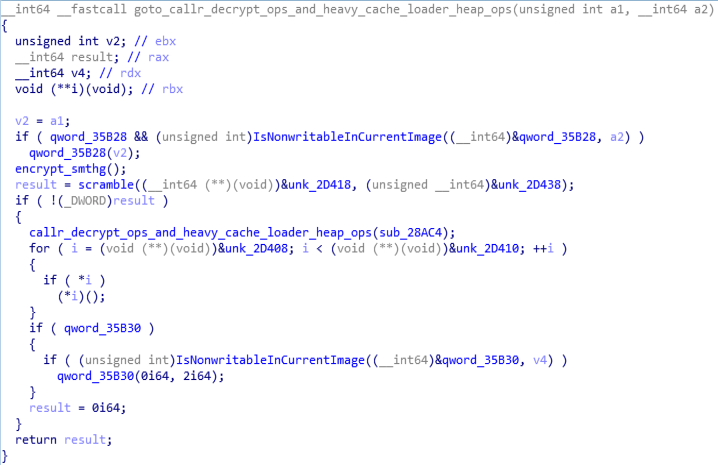 Call Graph and Code of “goto_callr_decrypt_ops_and_heavy_cache_loader_heap_ops” function.
Call Graph and Code of “goto_callr_decrypt_ops_and_heavy_cache_loader_heap_ops” function.callr_decrypt_ops_and_heavy_cache_loader_heap_ops function:
This is the follow-up module called in above mentioned function which calls “decrypt_ops_and_heavy_cache_loader_heap_ops” function.
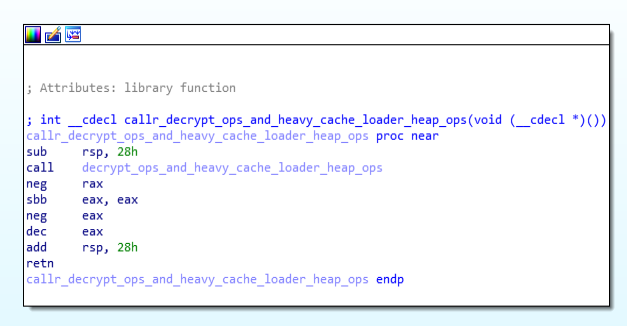
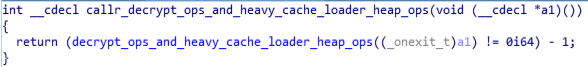 Call Graph and Code of callr_decrypt_ops_and_heavy_cache_loader_heap_ops function.
Call Graph and Code of callr_decrypt_ops_and_heavy_cache_loader_heap_ops function.decrypt_ops_and_heavy_cache_loader_heap_ops function:
In this module, the decryption operation using DecodePointer() for decoding Ptr and as we goes further in this module the encrypting of pointer is being used.
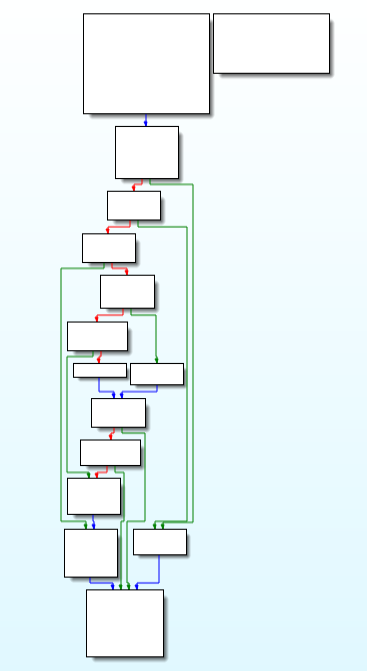
 Call Graph and Code of “decrypt_ops_and_heavy_cache_loader_heap_ops” function.
Call Graph and Code of “decrypt_ops_and_heavy_cache_loader_heap_ops” function.Moving on to the next export “InitSvc” which i had renamed as “thread_create_ops”.
thread_create_ops function:
In this module, mainly what happen is that Thread is being created after the Cryptographic operations and file,access operation and heap free operation.
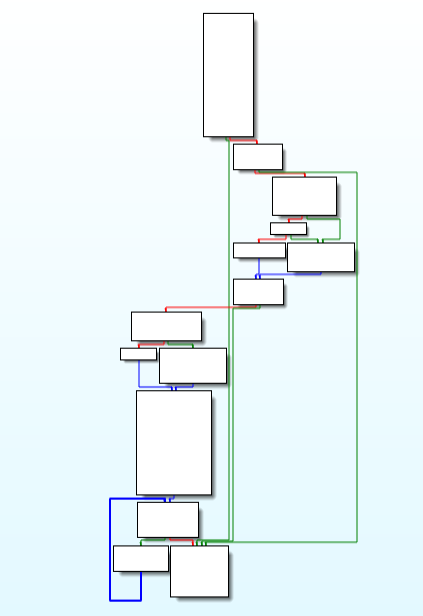
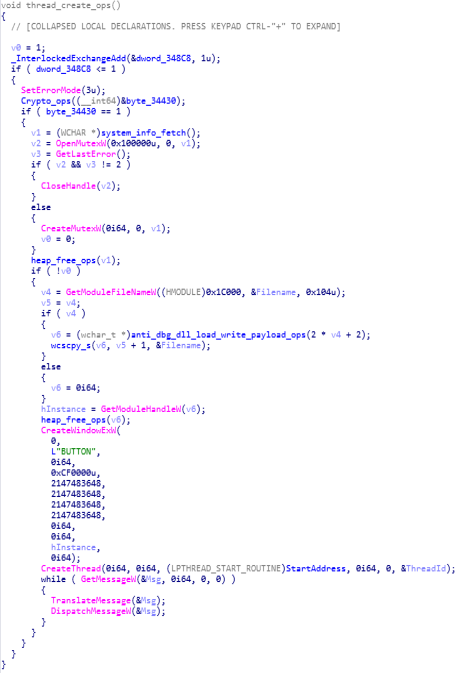 Call Graph and Code of “thread_create_ops” function.
Call Graph and Code of “thread_create_ops” function.Crypto_ops function:
This module carried out , anti debugging , dll loading and writing payload operations along with the call to the “goto_callr_of_decrypt_key_after_importing_key”.
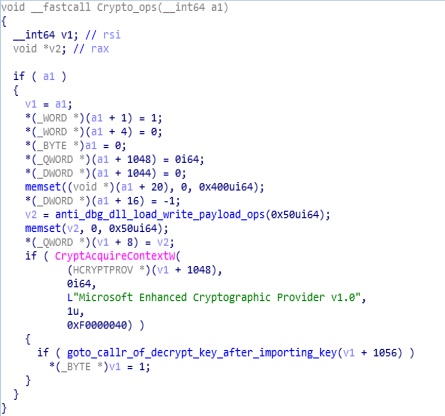
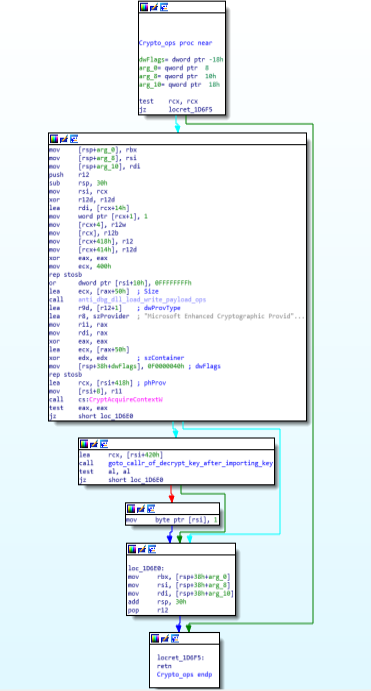 Code & Call Graph of “Crypto_ops” function.
Code & Call Graph of “Crypto_ops” function.anti_dbg_dll_load_write_payload_ops function:
In this function, anti debugging technique is being used ,along with the heap allocation, thread operations and dll initialisation.
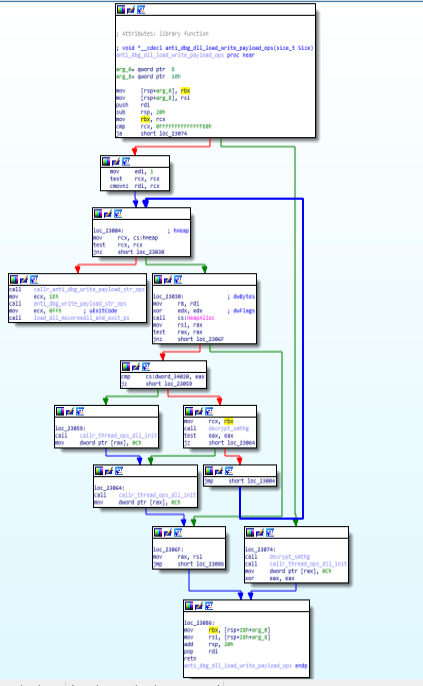
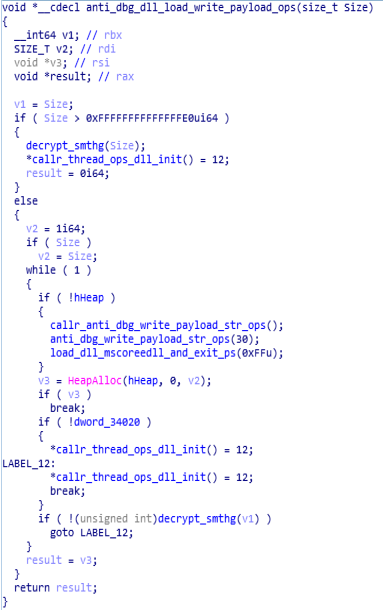 Call Graph and code of “anti_dbg_dll_load_write_payload_ops” function.
Call Graph and code of “anti_dbg_dll_load_write_payload_ops” function.goto_callr_of_decrypt_key_after_importing_key function:
This particular module is being used for calling module that goes into calling another function that goes into decryption of key after import of key.
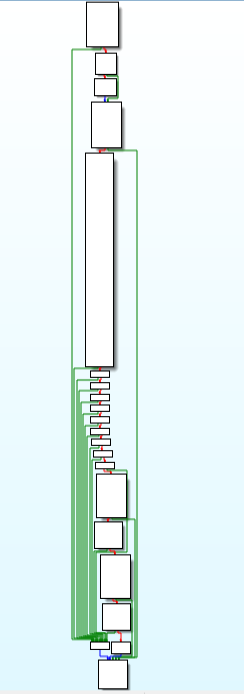
 Call Graph & Code of “goto_callr_of_decrypt_key_after_importing_key” function.
Call Graph & Code of “goto_callr_of_decrypt_key_after_importing_key” function.callr_of_decrypt_key_after_importing_key function:
This function calls the function “decrypt_key_after_importing_key” and does some heap ops , anti debugging and dll loading and write payload in the memory.
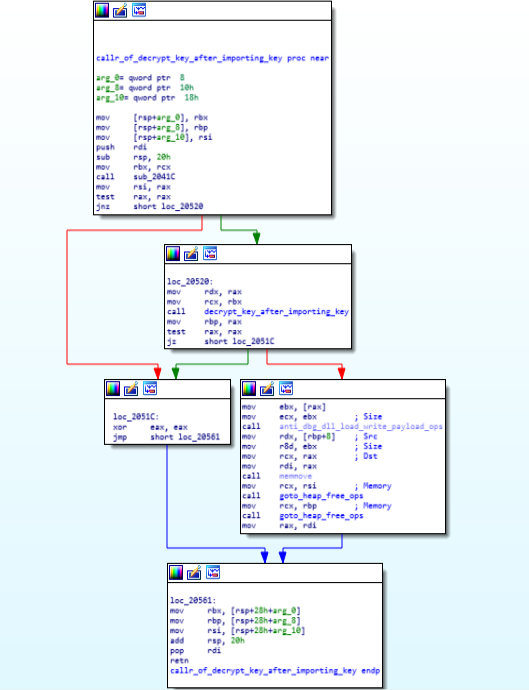
 Call Graph & Code of “callr_of_decrypt_key_after_importing_key function.
Call Graph & Code of “callr_of_decrypt_key_after_importing_key function.decrypt_key_after_importing_key function:
This particular module is being used for Importing key using “CreateImportKey” and then after that key is being Decrypted using CryptDecrypt() function and then some heap operations is being done and at the end Key is being destroyed using “CryptDestroyKey()”.
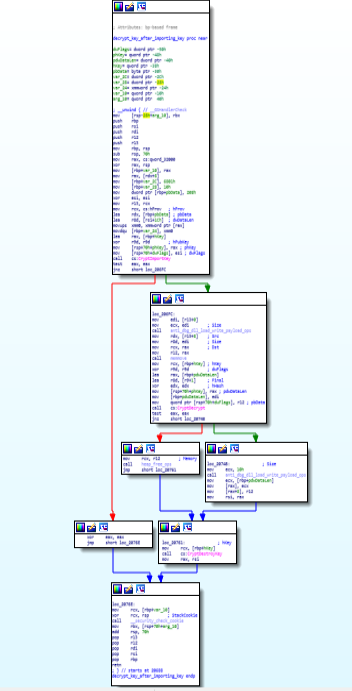
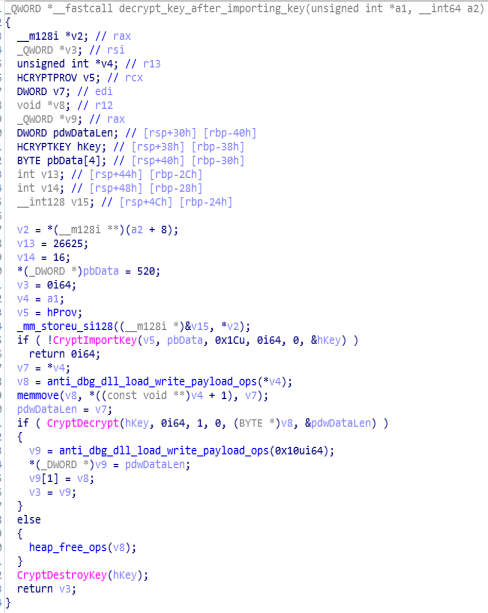 Call Graph & Code of “decrypt_key_after_importing_key function.
Call Graph & Code of “decrypt_key_after_importing_key function.StartAddress function:
This is the function which stores the malware configuration files as it contains calls to the function that does have hashes of files which you will find in the “some_kind_of_config” and it also have one another function similar to that.
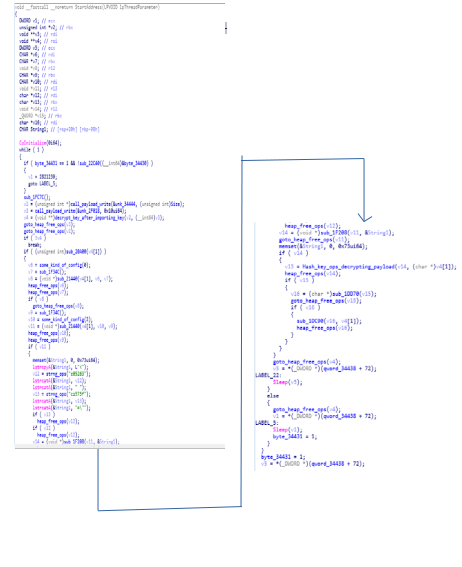 Call Graph & Code of “ StartAddress function.
Call Graph & Code of “ StartAddress function.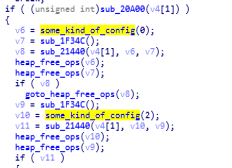 some_kind_of_config function.
some_kind_of_config function.Hash_key_ops_decrypting_payload function:
This is that function that i had shared on twitter yesterday with you guys.
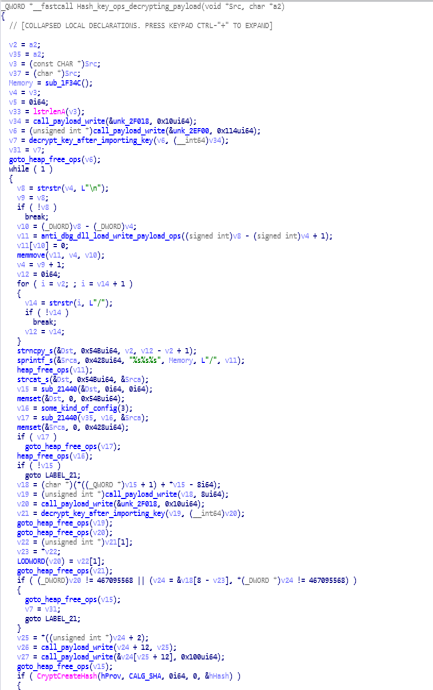
 Code of “Hash_key_ops_decrypting_payload” function.
Code of “Hash_key_ops_decrypting_payload” function.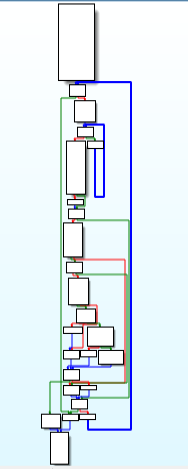 Call Graph of “Hash_key_ops_decrypting_payload” function.
Call Graph of “Hash_key_ops_decrypting_payload” function.Details of that Algo. used is in tweet mentioned here.
Dynamic Analysis ( Joe Sandbox)
Analysis Report unmapped_executable_of_polyglot_duke.bin
Samples from Report ( Intezer Analyze )
Note: YARA Signature from Me will be available.