Author: S2W TALON
Last Modified : June 30, 2022.
 Photo by DeepMind on Unsplash
Photo by DeepMind on UnsplashExecutive Summary
- As LockBit ransomware group has been updated twice without rebranding for a long time and continues to strengthen their brand reputation with their recently announced update to 3.0.
- As a result, the copycat groups that imitate LockBit ransomware’s logo or the chat site was discovered, and they are operating under the names of “SolidBit” and “CryptOn”, respectively.
- SolidBit is a variant of Yashma ransomware, and it is believed that the SolidBit ransomware group is currently working with the original developer of the Yashma ransomware.
- It has not been confirmed whether CryptOn is running a ransomware campaign yet, but the leak site they are operating is very similar to that of operated by the other groups.
- Neither group has confirmed any connection with LockBit ransomware, and it seems that they are trying to exploit the reputation of LockBit ransomware group.
1. SolidBit
Recently, the analysis of the ransomware named SolidBit has been disclosed by several analysts. We analyzed the ransomware sample and found that it was a variant of the Yashma ransomware (aka. Chaos ransomware). The builder software that can generate Yashma ransomware had already been leaked on underground forums and Telegram channel, so it is currently available to anyone who has access. However, SolidBit has some differences from the ransomware generated by the original builder, and we presume that the developer probably modified some features in the builder and rebranded it as SolidBit.
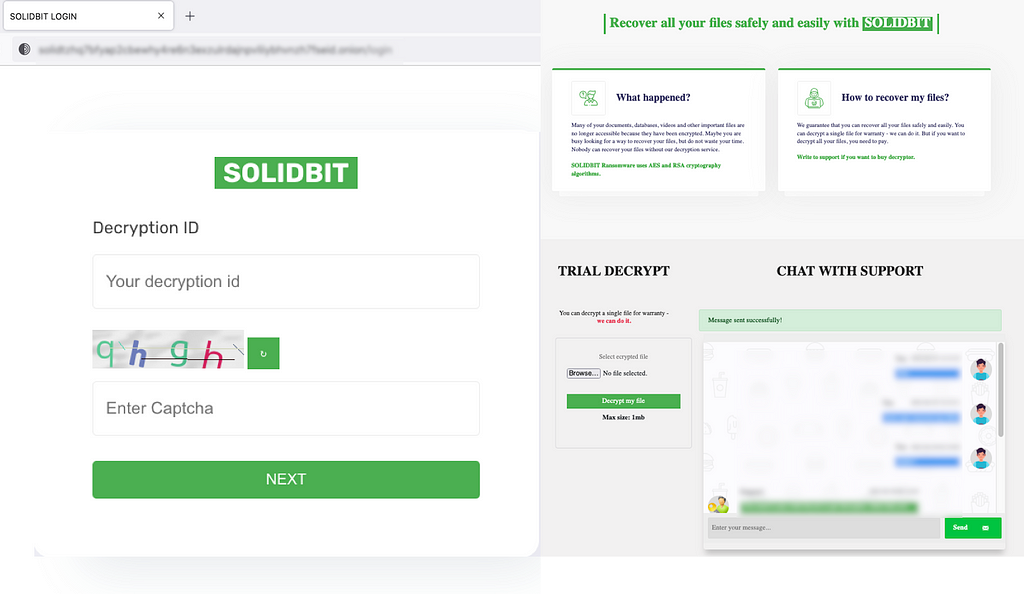 Figure 1. SolidBit ransomware login and chat site
Figure 1. SolidBit ransomware login and chat site- Leak site
As Chaos and Yashma ransomware builder software supports setting custom ransom notes, the ransomware strain doesn’t support an official chat site, but SolidBit now officially supports a chat site. However, both the login and chat site looks very identical to LockBit’s chat site, with the exception of the main theme changed from red to green.
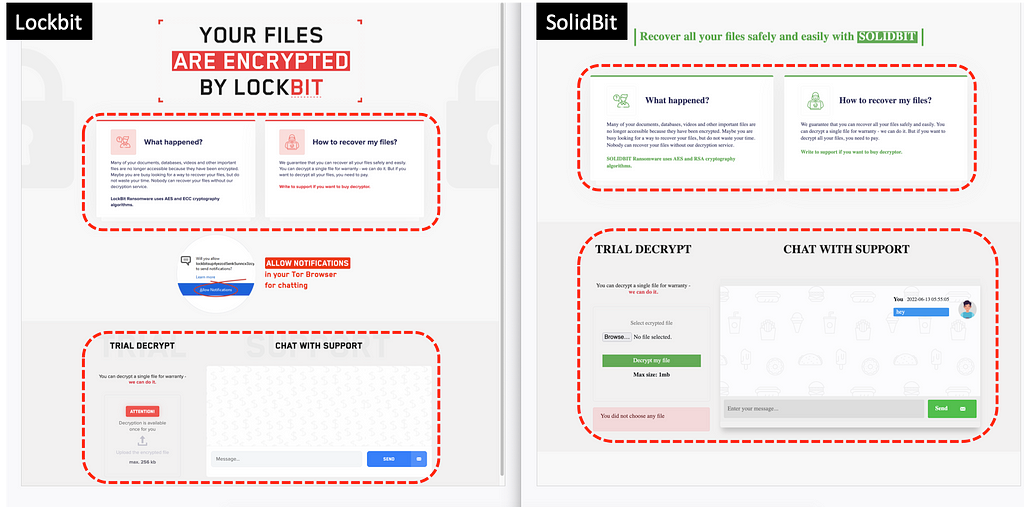 Figure 2. LockBit ransomware chat site (Left) / SolidBit ransomware chat site (Right)
Figure 2. LockBit ransomware chat site (Left) / SolidBit ransomware chat site (Right)- Ransomware
SolidBit ransomware was subsequently developed than the Yashma, with numerous features removed. In the former version, features such as checking the country of the infected device and whether to execute specific behavior through flags were included, but SolidBit performs only the given behavior without an additional branch. This suggests that the developer of the Yashma ransomware has modified SolidBit’s to customize it for a specific campaign, and with the addition of its own ransom note and chat site support this claim.
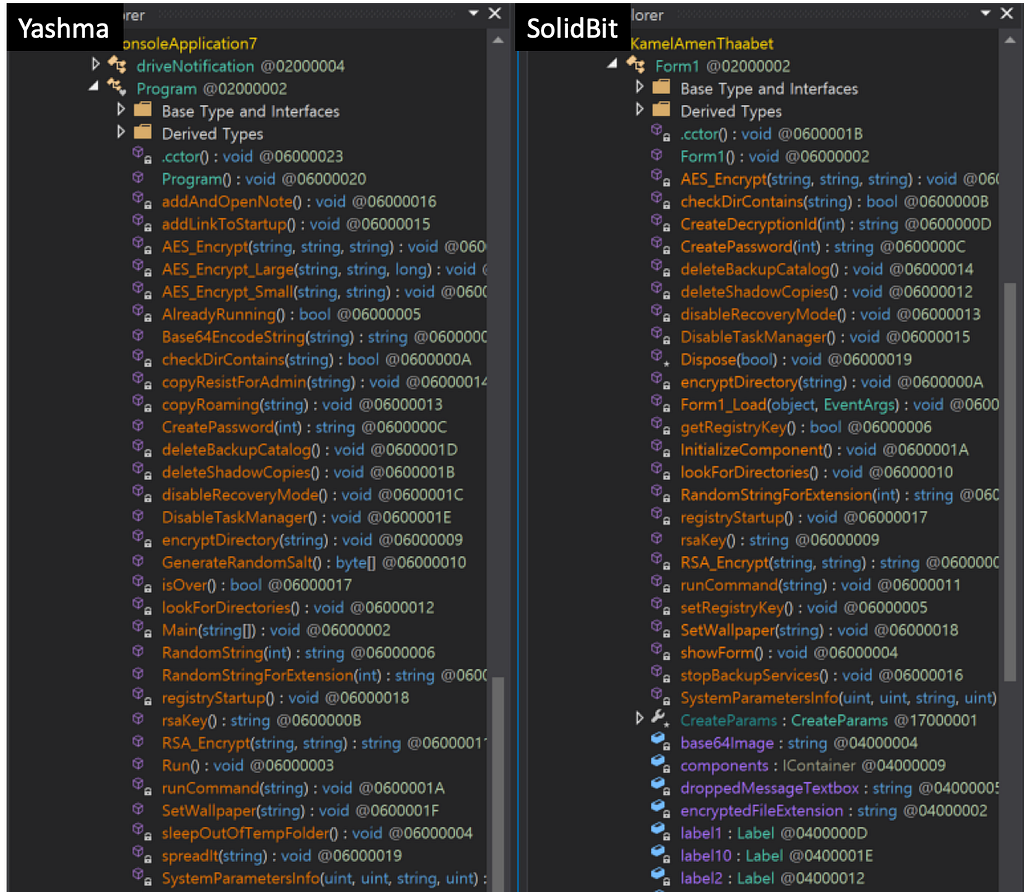 Figure 3. Yashma ransomware functions (Left) / SolidBit ransomware functions (Right)
Figure 3. Yashma ransomware functions (Left) / SolidBit ransomware functions (Right)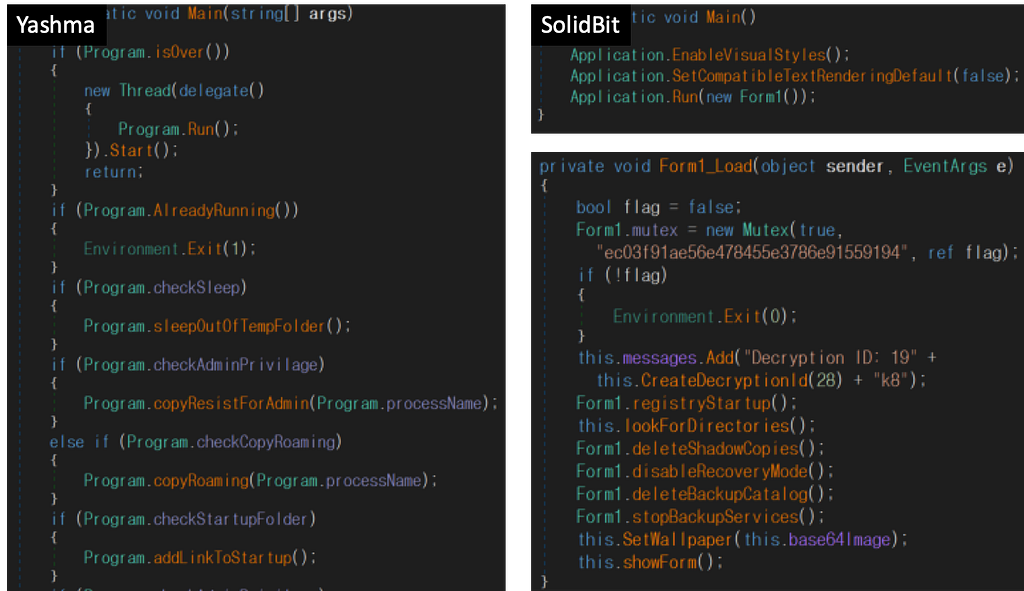 Figure 4. Yashma ransomware Main function (Left) / SolidBit ransomware Main function (Right)
Figure 4. Yashma ransomware Main function (Left) / SolidBit ransomware Main function (Right)There are two additional features added than that of prior. One is generating a decryption id which is used to join the chat site and the other one is changing the icon of the encrypted file. When a victim tries to open an encrypted file, SolidBit is executed again and the only ransom note is displayed as the encrypting process has already been executed. This feature is already implemented by other ransomware groups, but it was first used on the Yashma-Chaos ransomware strains by copying the open-source code from Stack Overflow.
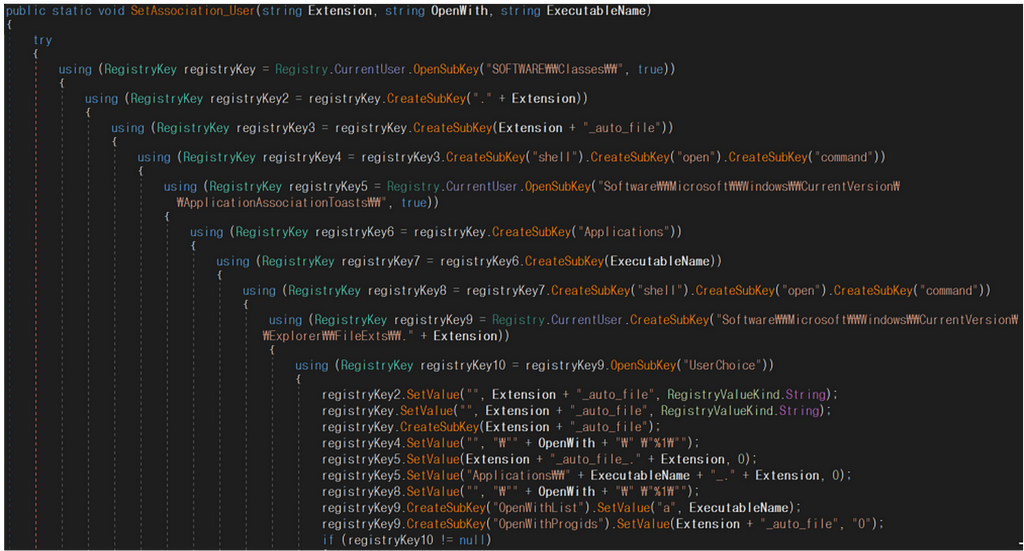 Figure 5. Added icon linking feature on SolidBit ransomware
Figure 5. Added icon linking feature on SolidBit ransomwareEncrypted files have their icon changed, as shown below. If a victim opens the file, the ransom note is displayed.
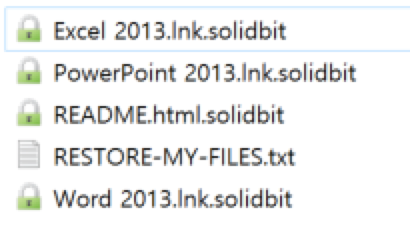 Figure 6. Encrypted file’s extension and icon
Figure 6. Encrypted file’s extension and icon- Ransom note
Yashma ransomware only creates a ransom note with a “.txt” extension, but SolidBit also creates ransom notes for both text file and windows form. When SolidBit is executed, a window in the form of a ransom note is displayed while encrypting files in the background.
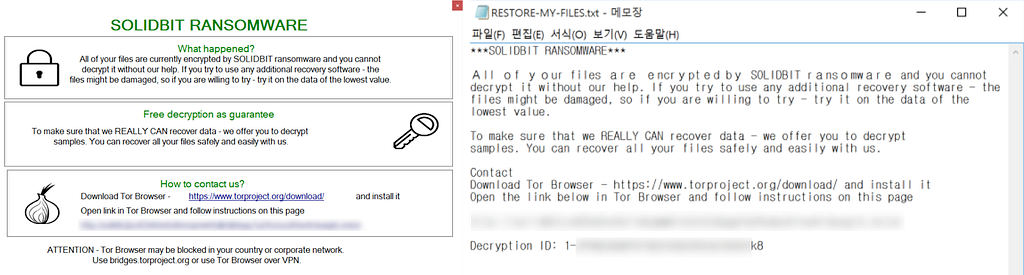 Figure 7. Ransom note after SolidBit ransomware infection
Figure 7. Ransom note after SolidBit ransomware infection- Recruitment
On June 29, 2022, SolidBit ransomware group posted a job advertisement for affiliates on an underground forum to start its full-fledged activities. They mentioned that they would take only 20% of the profits, are looking for pentesters who will infiltrate the company and then spread the SolidBit ransomware, and ask them to contact via Tox.
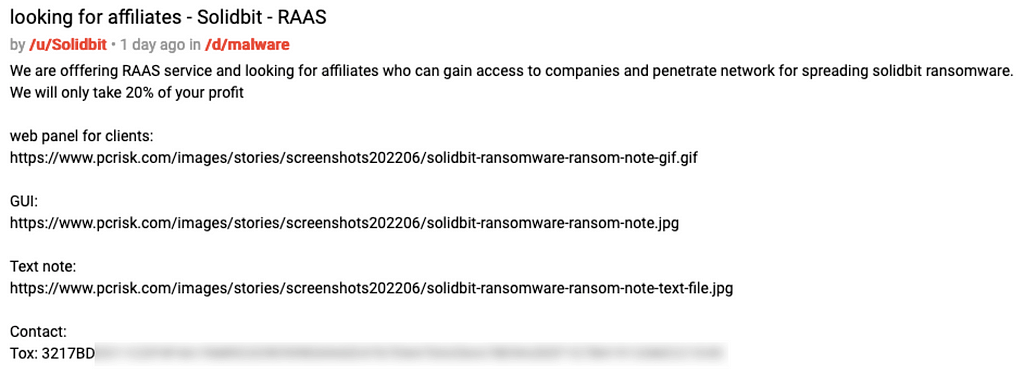 Figure 8. SolidBit ransomware group‘s job advertisement
Figure 8. SolidBit ransomware group‘s job advertisement2. CryptOn
The CryptOn leak site was first identified on April 13, 2022. Currently, there are 9 victim companies on the site, but two other companies were uploaded before the site was normally operated. From April to mid-June, stolen data for 3 companies was published, and as activities began in earnest, 8 new companies were additionally updated on June 28–29. The two companies that were first uploaded have now been deleted.
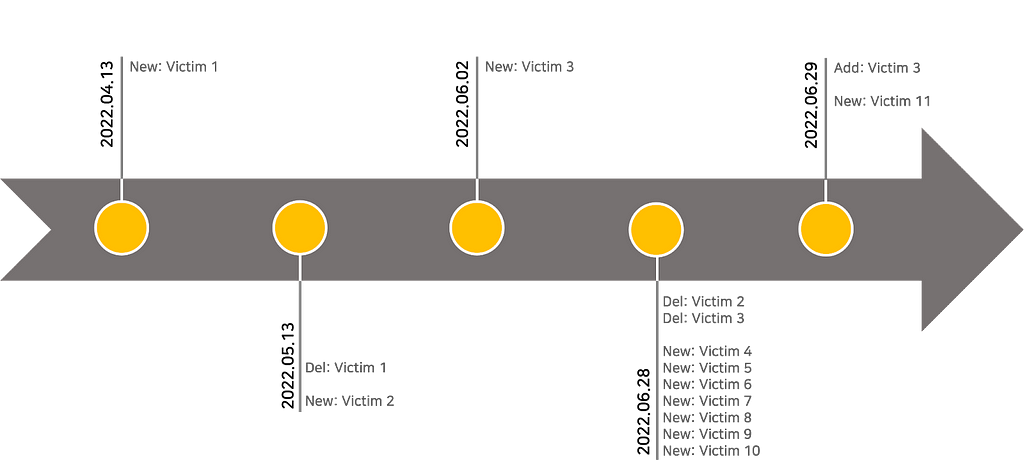 Figure 9. Timeline of victims uploaded to CryptOn
Figure 9. Timeline of victims uploaded to CryptOnThe LockBit Ransomware 2.0 logo was inserted at the top of the site to disguise itself as LockBit Ransomware group. However, it has not been confirmed whether they are actually using ransomware, and there is no more connection with LockBit ransomware group. In addition, as the victims mentioned on their site and the victims uploaded to LockBit’s leak site dosen’t match at all, it is speculated that CryptOn is a copycat exploiting LockBit’s reputation.
An example of exploiting the reputation of such large ransomware groups is when Prometheus ransomware group inserted the phrase “GROUP OF REVIL” into their logo.
 Figure 10. Logo of Prometheus ransomware group, a former REvil copycat
Figure 10. Logo of Prometheus ransomware group, a former REvil copycat- Leak site
On the main page of the leak site, there is an All tab to check a list of all compromised companies, a Publish tab to check a list of companies whose data has been published, and an Unpublish tab to check the list of companies whose data have not been published. It is believed that the site is not yet fully implemented in that within the Publish tab 8 of 9 companies doesn’t shown any form of downloadable data.
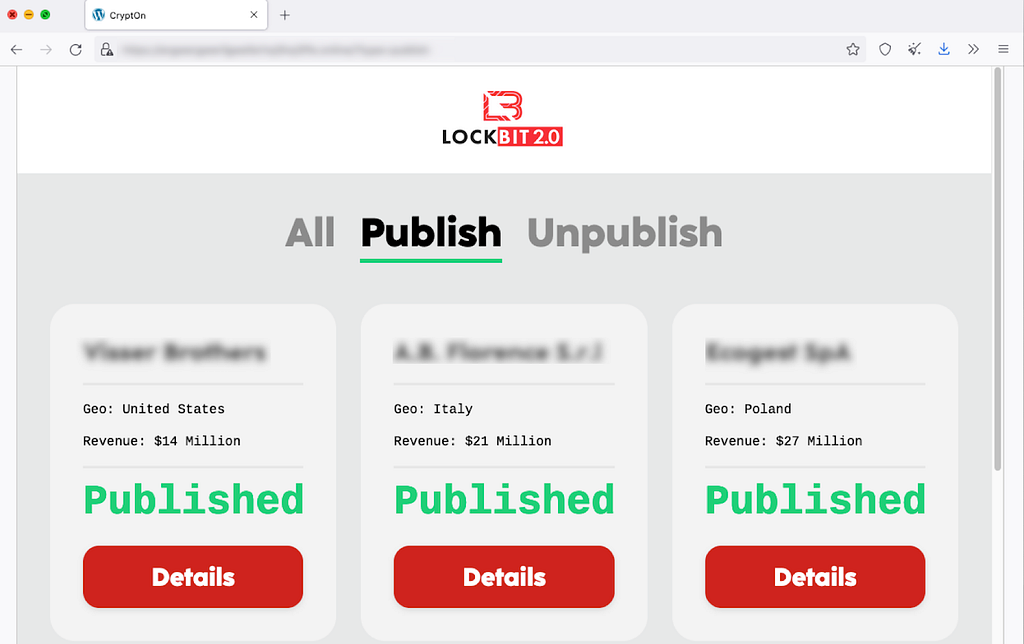 Figure 11. The main page of CryptOn leak site
Figure 11. The main page of CryptOn leak siteOn the page that appears when you click the Details button, you can see the Files tab and the Clients Contact tab where you can download the leaked data. Simple text data such as combolist can be displayed on the site, but other files or large files such as documents and emails are uploaded to MEGA storage.
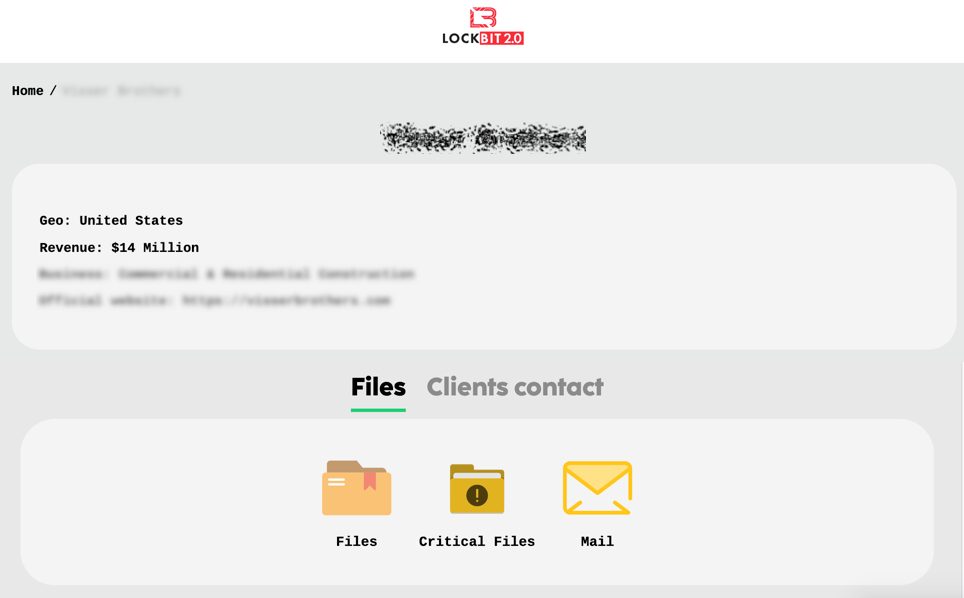 Figure 12. Categories of leaked data
Figure 12. Categories of leaked data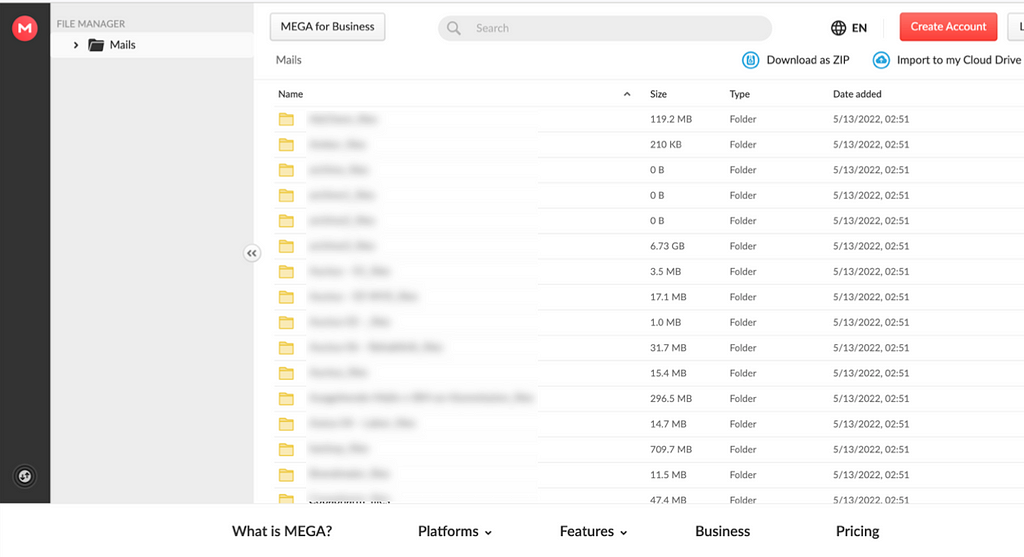 Figure 13. Victim‘s stolen data uploaded to MEGA
Figure 13. Victim‘s stolen data uploaded to MEGA- IP used by BlackGuard Stealer in the past
CryptOn leak site have been registered on March 14, 2022.
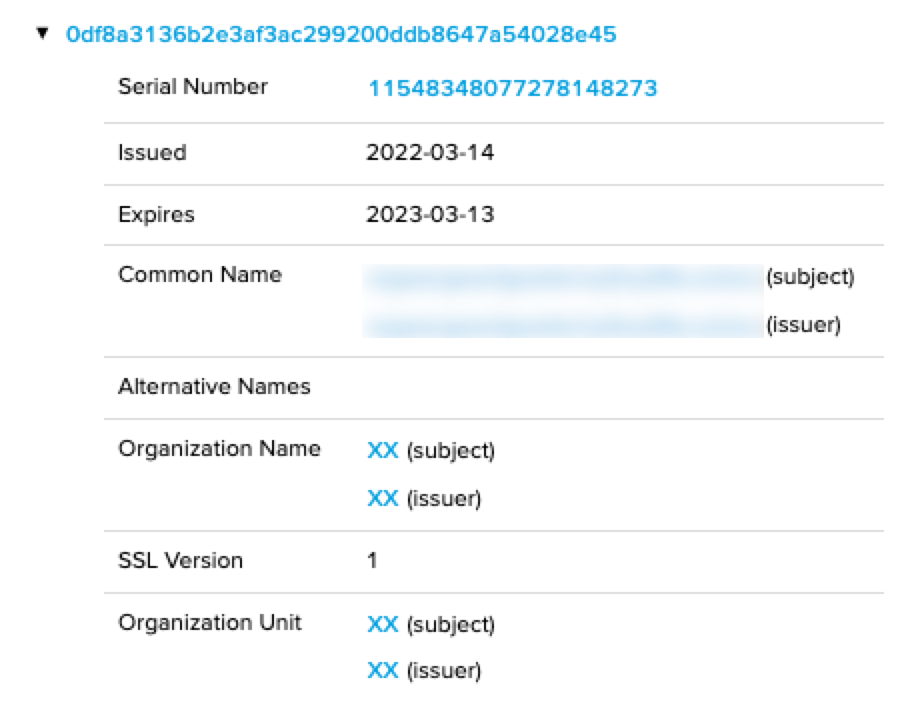 Figure 14. Date the CryptOn leak site was registered
Figure 14. Date the CryptOn leak site was registeredWhen queried for the site, it shows Cloudflare’s IP, but the hosted IP has been confirmed as the IP band of Scalaxy BV located in the Netherlands, and this ISP is widely used among cybercriminals. This IP was used as the admin panel for BlackGuard stealers from February 2 to March 6, 2022. Currently, it is only used as a CryptOn Leak site.
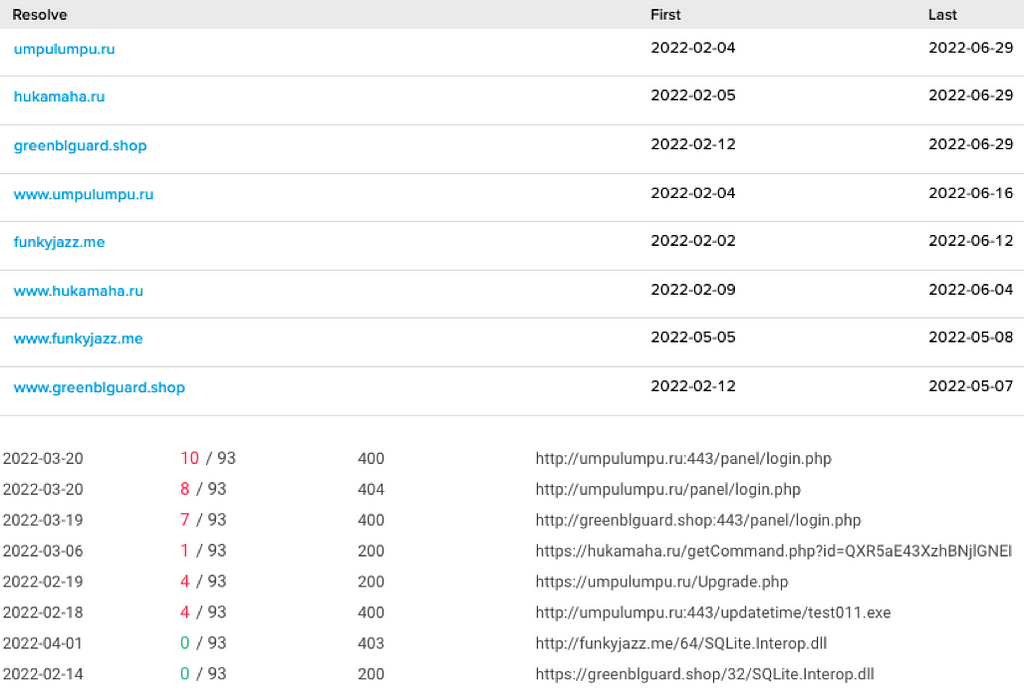 Figure 15. The server hosting CryptOn leak site was used as the admin panel for BlackGuard in the past
Figure 15. The server hosting CryptOn leak site was used as the admin panel for BlackGuard in the pastAs it is very common to reuse IP among cybercriminals, it is difficult to conclude that they are the same criminal just because they use the same IP. However, given that the attacker behind the CryptOn leak site has not yet been clearly identified, and the IP has been used for a completely different intention within a short period, continuous monitoring of the attack campaign related to the IP is required.
Conclusion
- It is estimated that the SolidBit ransomware group is cooperating with the developer of Yashma ransomware.
- The group operating CryptOn leak site is using the server used by the BlackGuard stealer in the past, but no connection with the BlackGuard stealer has been found so far.
- Both SolidBit and Crypton groups are copycats that copy and use some elements of the LockBit ransomware group, but it is necessary to monitor for changes in the ransomware and leak sites to track their activity.
Appendix. A. IoC
SolidBit
- 0f73ddb9dba894298b468d162f7dd49ae6f49cdc71184b98339d5b1e3eccbb02
- 63c9e7ec3a191e9ffbfc388a3cf7375693b609f4fd223b3fbcc9d7d21759b1bc
- bc30903638dbe661a8afd6a8f078e68c834e9c3ed706d0ad1b49457e154c4039
- eeb0a884d4eabc4f8811ecaa3e37acc8156c52b60a89537c5498df4c0e0c21f7
- 93f6f8e188d36ab7bf04e92d9673c3bcc4af2b56baa0fe98f30d3b05af6378a7

Homepage: https://s2w.inc
Facebook: https://www.facebook.com/S2WLAB
Twitter: https://twitter.com/S2W_Official
Two Copycats of LockBit Ransomware: SolidBit and CryptOn was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: Two Copycats of LockBit Ransomware: SolidBit and CryptOn | by S2W | S2W BLOG | Medium