As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
The most prevalent threats highlighted in this roundup are:
-
Doc.Malware.Donoff-6759556-0
Malware
Donoff is a malicious Microsoft Office document that leverages the Windows Command shell to launch PowerShell and download and execute an executable.
-
Doc.Malware.00536d-6758981-0
Malware
Doc.Malware.00536d is the denomination of a set of malicious documents that leverage VBA and PowerShell to install malware on the system. These documents usually convince the user to enable macros that, if executed, will download and install additional malware on the system.
-
Xls.Dropper.Donoff-6758223-0
Dropper
Donoff is a payload delivery Office document that leverages the Windows Command shell to launch PowerShell to download and execute an executable.
-
Win.Trojan.Emotet-6758832-0
Trojan
Emotet is a banking trojan that has remained relevant due to its continual evolution to better avoid detection. It is commonly spread via malicious emails, and saw a resurgence recently during Black Friday.
-
Doc.Malware.Valyria-6757519-0
Malware
Valyria is a malicious Microsoft Word document family that is used to distribute other malware. This campaign is currently spreading Emotet.
-
Win.Virus.Triusor-6757540-0
Virus
Triusor is a highly polymorphic malware family. All the binaries are packed and obfuscated to hinder the static analysis. The malware contains code that complicates the dynamic analysis. Once it is executed, the samples perform code injection.
Threats
Doc.Malware.Donoff-6759556-0
Indicators of Compromise
Registry Keys
- N/A
- N/A
- N/A
- 3ek6[.]top
- pvy1[.]top
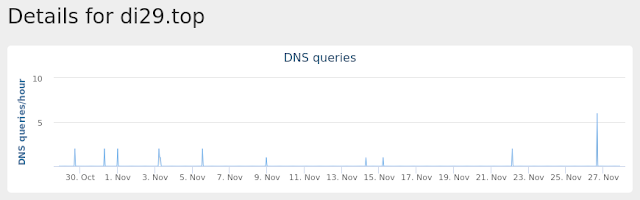
- di29[.]top
- 68d4[.]top
- %LocalAppData%\Temp\sDweD.exe
- %LocalAppData%\Temp\22dughsl.5qd.ps1
- %LocalAppData%\Temp\4s5lt2th.dfc.psm1
- %LocalAppData%\Temp\4e5cllpa.loj.psm1
- %LocalAppData%\Temp\zbaj2qbd.fvr.ps1
- 043a80eab9723a815096c7338c14105011f90c8fe1fe86a02c7c763726cfaa2a
- 06aa7214d492067f4f6a8aa0a910b5b32aee7734e0525a471bb2ca111ee6f3d0
- 09d47ec5acae65e60e8316435d57e75b8a0153458f4471c8ff3510ee2a809558
- 0a12a0000a78dfa623f71b0274df5b54f14dea7ddfe0799ad09cd76db2340441
- 0a137fefbe8edc0652e9eb4c6a9694a199d758241c5d2e5da98351771372d8f0
- 0b2a44c3b90bfc7c26605321c75fdc9703d67f71849cf106ef1e9fbd3160c533
- 0bdaed255c30cbce8a62153de694ffb80ede08f38ffd48706e415d457a21cbc1
- 0e12bab4d0a4c65141c6d16cc8401efda84373a667dfdca21f56b61466ef9e7d
- 0fe0f094572df903940dd8394c4c5c307705bb4146c794e77793f74a1e873327
- 121c49ab3eccc4472a13766f874b489b025ef1d5d9e1f8243085cb07290177c6
- 1459d9df5d2117263b051339baa35d5c28f54f5db6261135ea3d55c90e0985f7
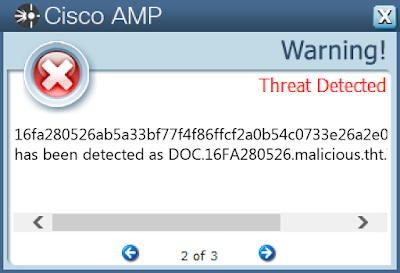
- 16fa280526ab5a33bf77f4f86ffcf2a0b54c0733e26a2e070e724981927d1ad8
- 1792e52f31de940e6d233967b62bd6712deae048fc110ba38cea000314781c16
- 19badf1bbaa2ba68db14bf76e88b11a29492fb8d0cf180b83736a55d23a402be
- 1b409f2f2146c2318580c73d5eaeafbdd79e39d4d4f3e5862323b3b6f4a6c916
- 1cb58e56ae9f1a563e4789ee947f3941b90c5221f68ea0506da345fb63805826
- 1f312a61244c970d254c24055b714138835b839f1da36b9ee1cfc1acf636fbf1
- 24d62b3de48bf8b55b79fafcd17bf4a2cb8489a86358b26aa361193ad355dee4
- 25fbacf14f3ea9918aa054f040c6cc73edb9450a34e2fe739b131d9c155e3e3d
- 2696e57e2daac38a37ca382f979f1e4c61b20f516dd18ba33290fd00ef3eec7e
- 29de1616d80266c566605928b266a43dc9e1cb7c1a1ed9c95e32d54efd4f6696
- 2af5928b3dfeaeff2556b7fbf27ef564c0a67457ef2ec6ac41dcfdb214b84856
- 2caaf8bad60e3e663993727b5ff26d685fb511892f90939d04e5f92765154687
- 2eab620737103e94f0dcd33163071e8c0bd1cdaaf42c1d2e254d3e5e71851b24
- 33d98771535a91ad332f2e59969b9f51a2bf811dbe886208e139e456cd124631
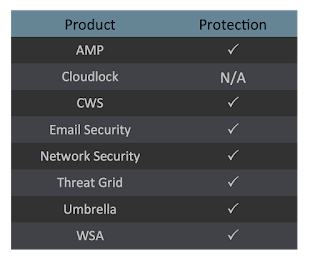
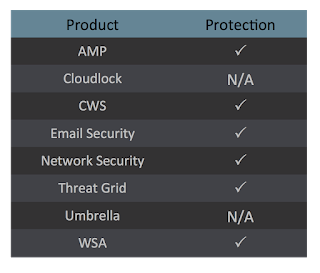
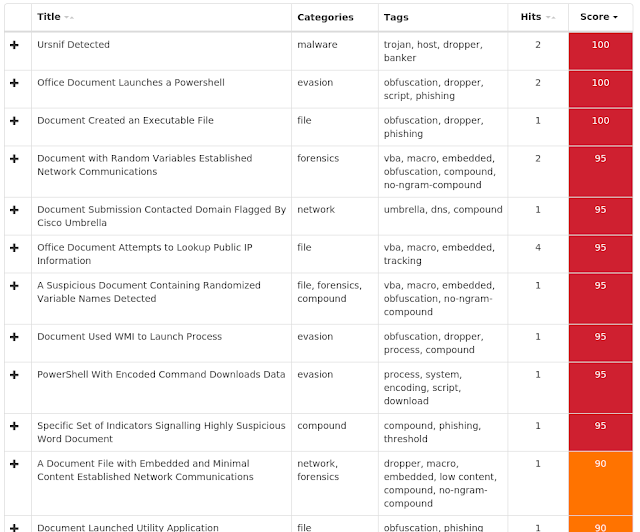
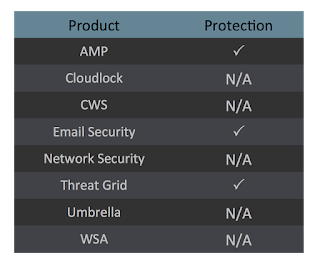
Coverage
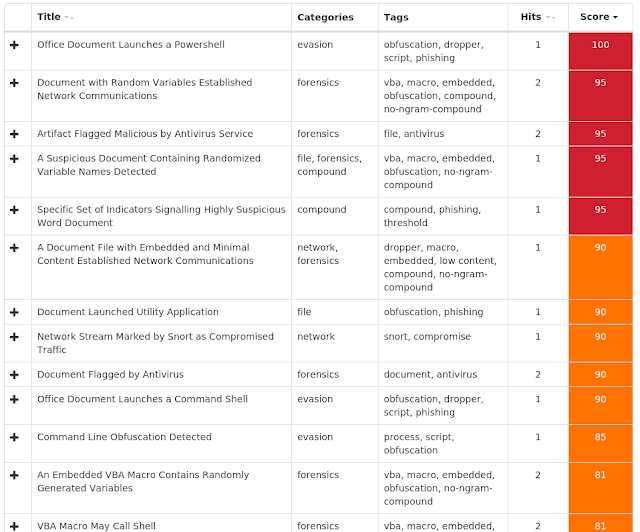
Screenshots of Detection
AMPThreatGrid
Umbrella
Malware
Doc.Malware.00536d-6758981-0
Indicators of Compromise
Registry Keys
- N/A
- _!SHMSFTHISTORY!_
- N/A
- cysioniven[.]com
- %LocalAppData%\Temp\ebeqjwi0.znf.ps1
- %LocalAppData%\Temp\xnakv4n3.jj0.psm1
- %LocalAppData%\Temp\glq130qw.p3e.psm1
- %LocalAppData%\Temp\haoyv1sm.xuc.ps1
- %AppData%\900194a4.exe
- 0ef9bfca2a912149f417a562853084d460565bdea22574d5f16d148905162d07
- 1de14e103775d466cfe9222ba3305e254dc9e8c1efb4454343ab7ef1368cc91a
- 70e0962256b2f98bf5ee698be7805dff03789cecdcac79519d3a0b0f327beef7
- d53aded580b952005cec23cf6e4a79de8775f5fab4ad8d1e715556499d3bd1cf
- dd2b0957848a603fde2abb678f3cd9fd6a271b427c04b16708f13f10be691ab6
- e470428e5c12292e0e6723c22c9b1deefa94ec8d182179118474239db192002d
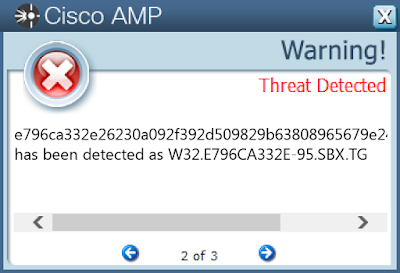
- e796ca332e26230a092f392d509829b63808965679e245d5914a3a9fbaeeb04f
- ecbb1cacd8390963a669b92cdd6a78f3e3dfffa93e794dde7426d4ef2780fab4
- f371a9934b7e07b03d3b8982fa3573b456504bf8a9ad5fc6c86801c8f40aa7cb
- fd4098a016d0a192efaf640c7376ea29272313eaed35d386305a0c87bd092a70
Coverage
Screenshots of Detection
AMPThreatGrid
Malware
Xls.Dropper.Donoff-6758223-0
Indicators of Compromise
Registry Keys
- N/A
- N/A
- N/A
- momdopre[.]top
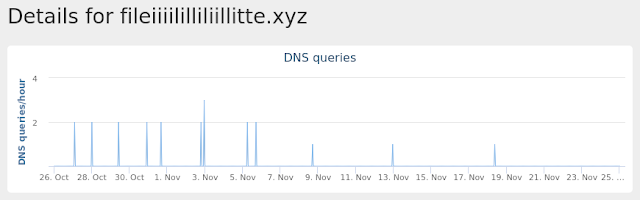
- fileiiiililliliillitte[.]xyz
- %SystemDrive%\Documents and Settings\Administrator\My Documents\rnohht`t.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\upd22ef67fa.bat
- %LocalAppData%\Temp\0w4zsktj.rxt.psm1
- %LocalAppData%\Temp\vnug35u0.1pd.ps1
- %LocalAppData%\Temp\cmnt0etf.0lt.psm1
- %LocalAppData%\Temp\l21izk2f.bel.ps1
- 0033f2a32856a043d34d491b0b79a3b1d25fbc084447ae801b94a6f4c8c67eec
- 0587d2fd8a94400a1a8f87a59111b4ec53c69ab7e4a50e6a4c7dd6eb7590e0b3
- 21df4279e0c9f6df6fb9ac8462e89ec9d2c777a3309dc9b8cf891a5232178800
- 405e08a4ab0c60f3ddc24dc4f4998bb654fbfae556163c9b70a2545cb79c4414
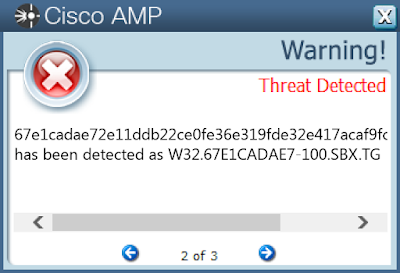
- 67e1cadae72e11ddb22ce0fe36e319fde32e417acaf9fcbe9ea1b0bd1852fded
- 6816c39d57cf2008ddd7ff252d97b9eb372c9c70ae9ac1834aee5beb0c24208c
- 792436cb281c6704ea7f53f7532e7abdfa1370ecf071cb07fdf690f8f6469013
- 7c78d19e0f8fe4420346cf0d0033071bcb5bba18015fab8d3e40dc57a5565c7b
- 88ceeeed4a5d23e5c26c74300d2f1cc89376c09057ac848032b45e2777d15b3d
- 99b43c4080202b48a2a729ed28dac8e3b98cd837494b2e419d71e7693b0652b8
- 9a9d1c1b43c93982eaf304c3c7ecb361bede0ea811c23cddb8b13a39328f0c3c
- 9e8fb999bba4c93ae100c02ede01475ddbc2b7db624930574ed76ec5813dd451
- bffbd9caa578af5caa98fcb20e0e5e4f55154e9e2ca256364c1f70538c04c5b9
- d59e75ccdee3f0419fd247372697275fa45f391af8319a4cf1f56df411885805
- dcbdf1859c62728c680ed7267f65b3a425aaed5c79b0f7404ef2e6541150d573
- e723f535550c7c4398bbb29f16e76e7a59b8e314b0d0d602c96cda07da56cc17
- ee5fb50a88b4b4a97bf82258cefc53e5de1bd416ddbdbee363dd9dc269ad867d
- f60827889d806f6864b2af5e5c08c467c1f41b176ae47b51bb3918f5cafa68a9
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
Malware
Win.Trojan.Emotet-6758832-0
Indicators of Compromise
Registry Keys
- N/A
- N/A
- 67[.]216[.]131[.]134
- 88[.]235[.]54[.]71
- 24[.]190[.]11[.]79
- 192[.]208[.]165[.]34
- 98[.]6[.]145[.]178
- 207[.]244[.]67[.]214
- N/A
- %WinDir%\SysWOW64\4WPGc4HlcDQ.exe
- 3567201c7de66370aa8eb0bd6242b0ce6edf3d4326c2255828470407a2a124b3
- 3f2fa56542583680c7feeda31a5e16b85f11d74b710e6cb699ffcf15b6ca753a
- 40ef85a4108702a3af09f9047b66585ffa2c73458cf9177a6ca67b4d8f388050
- 529a8f391dd994779340aa59118b703256321bb421db138ee0b7db4265599b12
- 5f30eab9dbf08a80292bc5184b6ff8e0ef075806b3d1eb8f5b5c525ec3efc4e9
- 78ccba1d9e5d32658ce4cd4b2f8a8be65c6aa6a4f4eec2016777afb3a50ac843
- 7d42a037f8c824724e3525e40f09ae6b3f0eaca4278e4f0b95bb5ca50f008f7b
- 864b1ce8feeed53db144afae131da20601bdf2951e198827177d40a233c490bd
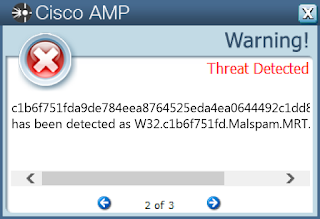
- c1b6f751fda9de784eea8764525eda4ea0644492c1dd8f1da9fc34e5b26b95b6
- c2ffeb181bc57e65011cb68ed33de62ef2ae79b12f320fa8362b096fe9f26430
- d60149eb78e3df622e24afec34b06c7c4c1d26a401ec326ea5eaaa74df873e3b
- e06807d11e7fba844ffe986638234633bfb93ccea283187b9019e0268b7876f4
- f5e1c6d6d9bd26a6d0ae3b8657030dd40138e0371b824013821f48302e3f67f3
- fe7d3a850371b6effe47525e39efbf705c4136e78b35f78228b1f986d30ceced
Coverage
Screenshots of Detection
AMPThreatGrid
Doc.Malware.Valyria-6757519-0
Indicators of Compromise
Registry Keys
- N/A
- N/A
- N/A
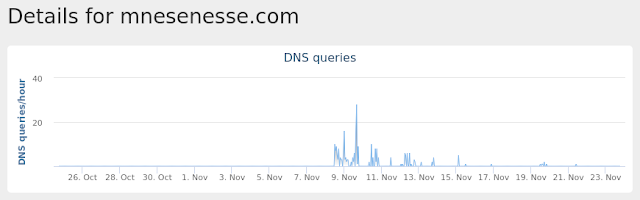
- mnesenesse[.]com
- ostrolista[.]com
- %LocalAppData%\Temp\qrldddmq.hyb.psm1
- %LocalAppData%\Temp\swfrthjc.vr1.ps1
- 0734985f67598ec0a0caf9ca31edd54bc93c5072ab0facc09f3d5164c8930afe
- 0ed8f1b95565876de24b49ab281f37d05d68130edc574ddd66300c5d5c9ad468
- 10aab8954d92baa70b29b5d9c13e0bc5f60d21bb34a00c45e963251516441aff
- 13707ac10ce41e2ec1547148c17a6186ff06009cd79789e01b879e96a5765f8a
- 15edcb2fc3b4d2fc1700f8e6837cd5c4759fb3791787c9cd9d0e16f129e0b234
- 173ee1fdd02789e581caa6858422f4afcf3cebcf4791e4e52c8ffda11ef726e4
- 1e1c3a6252578c94258f738d40ca36547631be604ad645e2c33a56cd26eab04b
- 2aa5876411a940b91e5091fffc10774063e93d9007bc5b75703747f1ff6737d9
- 35b3927d155688d396614850d95358c1d5b19e1d3487598788ffa1b881ecd156
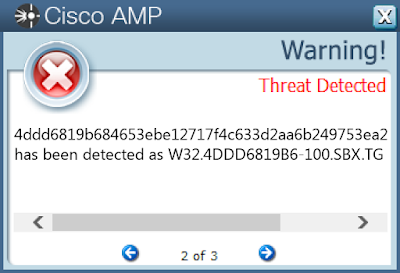
- 4ddd6819b684653ebe12717f4c633d2aa6b249753ea2e9af9e886cd5abf599b0
- 500fe0e5847b6677fa8b91073d3c0fca1d80fef35cafd57b95634abab8973d42
- 52577b1c77ef1a8e21c3681d4610bf47fec5fbae0f751f3396dc349d23186de8
- 52fb2178d177421a16086155829b67154ddfc589ddc71a99b14f922741586479
- 54485288c4cc0956a765a7a0165b8c70066314baa98dfdfc088db0f82d611bee
- 5ac2183dc29d6cea617b06c5787019409662898e259f6b1c0c7465c69054bb26
- 608c215893b99203b2d355253d42b14fe0bae98b22a891cfa2950c79d8b4dfe1
- 61da1d5f5a0e508f1b79fee2a8ed00b37970f5c967cdfbf4a7933163752d777a
- 6b1ebcc59ca46e52be7f0b896898ef19577946da900f31145e1ae9d0451cf08f
- 6e005fab674754f7a84fa80b873d02d8c321cfdfa7dbb7661d9d03fbd5c943d0
- 6f9b7938e71ce992206f8a8c065159e36dfb26a5c146844a14c8689c68b46985
- 7665239ea5a4928f88cc39051fde78ad6ef2660a248bb57550fc3adb69d414bc
- 782071bd82d2a75149d55cf3a036add1a82349c42a77cecf17f5c74c3d535c04
- 8aeddfcdce551eede421e527a4f1183b6378ca7bfbea07e0f4810d8c60357cec
- 8eb3b092f7105734380156ddf60db8ab71d23270c55f7d9e98499bb11399b47a
- 8fb33dc484fcfc5440e175cce2fe3efe3b70cfd1e61f8dbce5a846e7271a8469
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
Malware
Win.Virus.Triusor-6757540-0
Indicators of Compromise
Registry Keys
- N/A
- N/A
- N/A
- N/A
- %WinDir%\Microsoft.NET\Framework\v1.1.4322\RegAsm.exe
- %WinDir%\Microsoft.NET\Framework\v1.1.4322\ilasm.exe
- %WinDir%\Microsoft.NET\Framework\v1.1.4322\jsc.exe
- %WinDir%\Microsoft.NET\Framework\v1.1.4322\ngen.exe
- %WinDir%\Microsoft.NET\Framework\v1.1.4322\vbc.exe
- 0bc3007209f850ac764646065dcc8fdd85c46425dc98d72631e51045ba36069c
- 14bc92fb1cb50fc6ffd2f34b701e57603fb99b96130c7e5b77187c2c3684a4db
- 249ac287cada8bab59c445a286a8edb645f58035681c788687979c17d7eb766f
- 3822de7241c17afa298071ab05ea0552456c7b9e78f2655b3471554f972520cf
- 3adbbb8794d8244bbc905ad9b7d54046e494374f1856447fd174869911f8ebd2
- 68d400f36ef0ac8869499a0185fc52a7d22add5a137fcdd9d73b7e47d8514049
- 6a897eacea0f1a6773d19c6b1dbd101db860e3f8df547d97392c98a6aef0cce5
- 6b34a29fcdf2ad7a74859ba38c3a622971c1bbdb6a1268d5c766fac441b9970d
- 8cee25864d734f6624754ba68d47d0d6573ce6d4ca55c2cf3025a1435bf84685
- 8f4bd4d1d9d337cfd8ffd0afe80213ae90063d274aad64b04aa8558b837218e6
- 9df2784ba1fd594ab90357d799b26e0fa3abca65a5744ce3d62993d74b0f7e0f
- 9e76c9877cb6820ff88937ee158cd59cbe16b9eb26526f0f1ec39d09601dca05
- a3168cb7b3fd30eed135ba086e9e96984f56fd52317d185f3e988176440a5a25
- db6317729cabcb31a4be51a3cc281bffc5dd38a8164861c4d7fe7a0be386f892
- dc8c46a57c38955f4b6356d29662beeb0f88eeca50a94191df8892efab3bfc2e
- ec0b82ac2d4ca03a4c20ebeaa2fe5a0fc33f4e2270f8bf08063400c06a005f59
Coverage
Screenshots of Detection
AMPThreatGrid
Article Link: http://feedproxy.google.com/~r/feedburner/Talos/~3/671plxFAmfc/threat-roundup-1123-1130.html