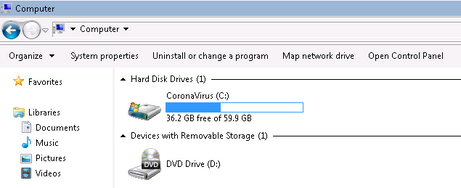
“CoronaVirus” Ransomware has been found distributed via a phishing website. The malicious website will distribute a trojan downloader which then leads to downloading additional malicious payloads: the Kpot InfoStealer and Coronavirus Ransomware.
“CoronaVirus” Ransomware will perform the deletion of volume shadow copies and overwrite the Master Boot Record (MBR) of the hard disk. It will also drop ransom notes named “CoronaVirus.txt” to the victim as shown in Figure 2.
Figure 1: Malware distribution
Figure 2: Screenshot of the ransom note
Details
- Upon execution it will delete itself, then create a copy of itself to the %TEMP% directory with a randomly generated filename.
- It will rename system C drive to “CoronaVirus”
- It will modify the following registry key to display ransom note on screen during reboot and startup:
-
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager “BootExecute” autocheck autochk * {%TEMP%\”RansomNote”}
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run {%TEMP%\CoronaVirus.txt}
- It will perform the deletion of volume shadow copies with the following command:
- “C:\Windows\system32\VSSADMIN.EXE” Delete Shadows /All /Quiet
- “C:\Windows\system32\wbadmin.exe” delete backup -keepVersions:0 -quiet
- “C:\Windows\system32\wbadmin.exe” delete systemstatebackup -keepVersions:0 -quiet
Behavioral Summary
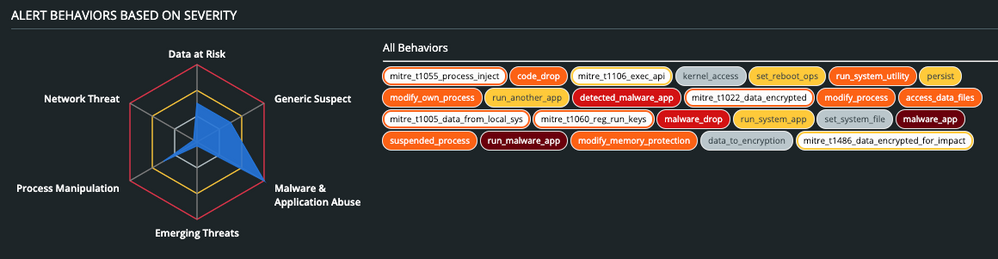
The following is a screenshot of Cloud Enterprise EDR (CB ThreatHunter) process chart by “CoronaVirus” Ransomware.
In addition, VMware Carbon Black Cloud Endpoint Standard (CB Defense) will display the malware’s overall triggered TTPs.
Customer Protection
CoronaVirus Ransomware is blocked and detected by existing policies within VMware Carbon Black products. To learn more about further ransomware behavior, detection and protection capabilities within the Carbon Black suite of products against CoronaVirus ransomware, you may refer to the following blog post:
MITRE ATT&CK TIDs
| TID | Tactics | Technique |
|---|---|---|
| T1143 | Defense Evasion | Hidden Window |
| T1083 | Discovery | File and Directory Discovery |
| T1060 | Persistence | Registry Run Keys / Startup Folder |
| T1112 | Defense Evasion | Modify Registry |
| T1497 | Defense Evasion,Discovery | Virtualization/Sandbox Evasion |
| T1006 | Defense Evasion | File System Logical Offsets |
| T1067 | Persistence | Bootkit |
| T1490 | Impact | Inhibit System Recovery |
Indicators of Compromise (IOCs)
| Indicator | Type | Context |
|---|---|---|
| 5987a6e42c3412086b7c9067dc25f1aaa659b2b123581899e9df92cb7907a3ed | SHA256 | Trojan Downloader |
| 3299f07bc0711b3587fe8a1c6bf3ee6bcbc14cb775f64b28a61d72ebcb8968d3 | SHA256 | CoronaVirus Ransomware |
| a08db3b44c713a96fe07e0bfc440ca9cf2e3d152a5d13a70d6102c15004c4240 | SHA256 | Kpot InfoStealer |
| cb2b4cd74c7b57a12bd822a168e4e608 | MD5 | Trojan Downloader |
| ec517204fbcf7a980d137b116afa946d | MD5 | CoronaVirus Ransomware |
| 99785ae0679d6d3e27de83af403c23b0 | MD5 | Kpot InfoStealer |
| wisecleaner[.]best | URL | Phishing website |
| trynda[.]xyz | URL | Trojan Downloader website |
The post Threat Analysis Unit (TAU) Threat Intelligence Notification: CoronaVirus Ransomware appeared first on VMware Carbon Black.
Article Link: https://www.carbonblack.com/2020/03/31/threat-analysis-unit-tau-threat-intelligence-notification-coronavirus-ransomware/