<div>
<div>
<div>
<img alt="The Role of Threat Intelligence Providers in TIBER-EU tests" src="https://quointelligence.eu/wp-content/uploads/2020/09/TIBER-Blog-Header.png" title="TIBER Blog Header" />
</div><div>
<div><h2><strong>Part II of II: Testing the Cyber Resilience of Financial Institutions with TIBER-EU</strong></h2>
This post is the second in a series of two blog posts, in which we explain the TIBER-EU framework, how the test is carried out, and how financial entities can benefit from it.
In the first part of this series, we explained what TIBER-EU exercises are and how financial institutions can benefit from them. In this blog post, we will outline the structure of these intelligence-led tests and, especially the role of the threat intelligence provider.
Structure of TIBER Tests
The Threat Intelligence Based Ethical Red Teaming, commonly known as TIBER-EU, is an “intelligence-led red team test of entities’ critical live production systems” that tests and improves the cyber resilience of financial institutions by carrying out a controlled cyberattack based on real-life threat scenarios. TIBER tests are designed for entities which are part of the core financial infrastructure at the national or European level. However, any sized organization can conduct the test and benefit from its outcome.
“I would very much like to see at least the largest financial institutions in Germany conducting a TIBER test in the near future.”
– Jörg Kukies, State Secretary at the Federal Ministry of Finance
The structure of TIBER tests is defined by the European Central Bank (ECB) and adapted by the relevant authorities in each member state. Each national jurisdiction adapts the framework to suit the specification of the respective financial sector. In Germany, for example, the central bank Deutsche Bundesbank oversees TIBER-DE tests.
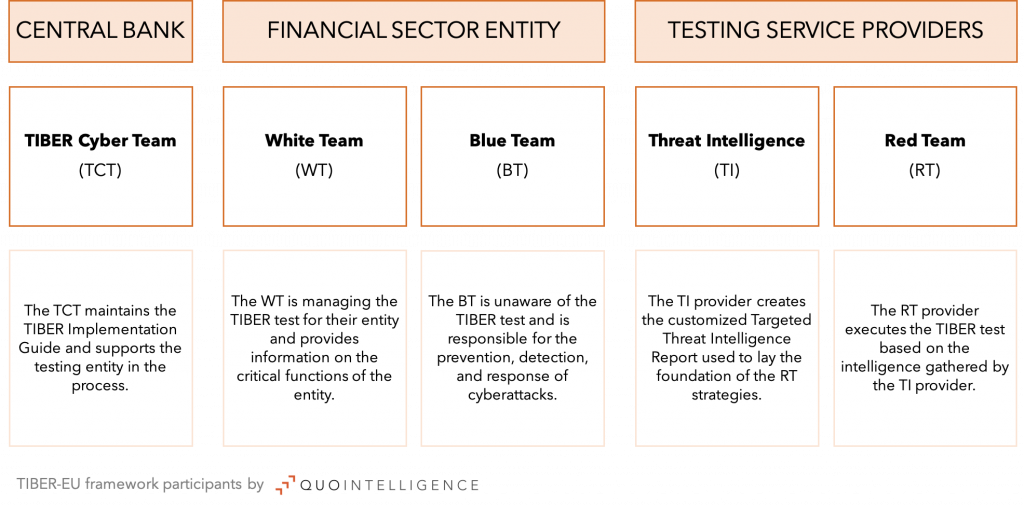
TIBER-EU framework includes the following participants:
- TIBER Cyber Team (TCT): In Germany, the TCT is provided by Bundesbank. The TCT maintains the national and European TIBER Implementation Guide, facilitates TIBER tests, supports the testing entity, and is the contact point for all enquires.
- White Team (WT): The WT is a dedicated team within the testing entity which is aware of the test and provides information on the critical functions of the entity. It cooperates closely with the TCT and external providers.
- Blue Team (BT): The team in the testing entity which is responsible for the prevention, detection, and response of cyberattacks. They are not made aware of the test, as their capabilities are being tested by TIBER.
- Threat Intelligence (TI) Provider: The TI provider creates the customized Targeted Threat Intelligence Report for the testing entity which lays the foundation for the Red Team to work out their attack scenarios. The TI and RT providers cooperate closely throughout the exercise.
- Red Team (RT) Provider: The RT provider finally executes the TIBER test based on the intelligence gathered by the TI provider.
TIBER tests consist of one optional and three mandatory phases:
Optional – Generic threat landscape phase:
This phase involves a generic assessment on the national financial threat landscape. It includes an overview of market participants and identifies relevant threat actors and their Tactics, Techniques, and Procedures (TTPs).
The Generic Threat Landscape can be used as basis for the later development of the Targeted Threat Intelligence Report. If possible, the Generic Threat Landscape will be validated and reviewed by national intelligence agencies and updated on an ongoing basis to reflect any changes in the threat landscape.
As QuoIntelligence is a European company, we have extensive knowledge of the cyber threat landscape of the financial sector in Europe.
1. Preparation phase:
During this phase, the testing entity will establish the teams responsible for conducting the tests and define the scope of the test. The scope will be submitted to the financial institution’s board of directors for approval and for validation by the respective regulatory authorities. Both, the board’s approval, and regulatory validation are mandatory under the TIBER-EU guidelines. Finally, the Threat Intelligence and Red Team providers are procured for the TIBER-EU exercise.
2. Testing phase:
The testing phase includes activity by the TI and RT provider. First, the TI provider will create the Targeted Threat Intelligence Report, which the RT provider will use to create and carry out attack scenarios against the entity.
3. Closure phase:
After the RT provider commences its scenarios, it drafts the Red Team Test Report. In this report, it outlines its approach, as well as any observations and findings from the test and provides advice on improvements. After these findings are taken to the board, a Remediation Plan will be created by the testing entity in close consultation with supervising authorities.

Overall, a TIBER test can take between 10 – 12 months, depending on each entity’s specifications. Throughout the test, frequent communication between all participants is highly recommended to ensure the test runs smoothly.
The role of the Threat Intelligence Provider
As a distinguished European cyber threat intelligence provider, QuoIntelligence has been procured to act as the TI provider in previous TIBER tests. The TI provider plays a crucial part in TIBER tests, which are by definition intelligence-led. The TI provider produces the Targeted Threat Intelligence Report based on real-life attack scenarios, which forms the foundation of the Red Team exercises.
The Targeted Threat Intelligence Report is structured based on guidelines provided by the ECB. The report is customized for the specific entity and includes at a minimum the following areas:
Target identification:
At the beginning of the testing phase, the testing entity provides the TI provider with a list of its critical functions. The participants of the test agree on the scope, i.e. which functions can be targeted during the tests and which are out of scope. The TI provider uses the information provided by the entity and engages in additional intelligence gathering and analysis to create a detailed report on the entity’s attack surface, for example potential vulnerabilities that could be abused by cyber actors. This could include leaked credentials of employees or vulnerabilities in exposed systems.
Thanks to the technologies and processes QuoIntelligence uses to provide our Digital Risk Protection (DRP) service, our analysts can easily retrieve the entity’s digital footprint and highlight notable findings which could be exploited by the Red Team.
Threat identification:
The TI provider also analyses the overall threat landscape for the testing entity, by identifying relevant threat actors based on the likelihood they would target the testing entity. Detailed profiles on these selected threat actors, including in-depth examination of their TTPs mapped on the MITRE ATT&CK framework, malware kits used, and vulnerabilities commonly exploited are created.
To fulfil this objective, QuoIntelligence tracks 100+ threat actors, including analysis on their motivation and intent. In addition, we track more than 100 malware kits, many with complete MITRE ATT&ACK technique descriptions. We also developed a methodology to rank the relevance of each threat actor to the testing entity, based on their business exposure.
The TI provider provides their findings in the Targeted Threat Intelligence Report, which includes information gathered and analyzed during the target and threat identification phases. The Targeted Threat Intelligence Report will be reviewed by all participants and potentially amended based on the feedback received. The RT provider will use the final version of this report as base to create their attack scenarios.
In conclusion
The main objective of TIBER is to test and improve the protection, detection, and response capabilities of financial entities against sophisticated cyber threats. TIBER enables organizations to enhance their cyber and operational resilience by increasing their awareness of their strengths and weaknesses before real-life threat actors exploit them.
TIBER exercises are intelligence-led and based on real-life attack scenarios, requiring customized Targeted Threat Intelligence Reports for each testing entity. The involved intelligence provider works closely with the testing entity, as well as with the Red Team provider, to understand the actual threat surface of the testing entity to enable these real-life attack scenarios. QuoIntelligence provides the expertise and experience to support any entity in conducting their own TIBER tests.
Find out more on TIBER-EU exercises and how QuoIntelligence can support you!
<div><h2>Join our Newsletter!</h2><div><p>Subscribe to our newsletter <strong>with your business email</strong> to receive intelligence summaries, analytic product updates, and more!</p>
<div>
<div></div>
<div>
<h2>Thanks! You will soon receive a confirmation email!</h2>
</div>
<div>
<p>
First Name
</p>
<p>
Last Name
</p>
<p>
Email
</p>
<p>
<a href="https://quointelligence.eu" rel="noreferrer" target="_blank">
Subscribe
</a>
</p>
</div>
</div>
</div><ul>
<li><a href="https://twitter.com/QuoIntelligence" rel="noreferrer" target="_blank" title="Follow on Twitter">Follow</a><a href="https://twitter.com/QuoIntelligence" rel="noreferrer" target="_blank" title="Twitter">Follow</a></li><li><a href="https://www.linkedin.com/company/quointelligence/" rel="noreferrer" target="_blank" title="Follow on LinkedIn">Follow</a><a href="https://www.linkedin.com/company/quointelligence/" rel="noreferrer" target="_blank" title="LinkedIn">Follow</a></li>
</ul>
</div>
</div>
</div>
The post The Role of Threat Intelligence Providers in TIBER-EU tests appeared first on QuoIntelligence.
Article Link: The Role of Threat Intelligence Providers in TIBER-EU tests