With seismic events already linked to the men’s World Cup, many wonder what other kinds of activities we may see. Cybersecurity discussions of the World Cup have largely focused on the criminal activity that tends to accompany major global events. In a recent survey, 72% of security professionals expect some sort of attack on this year’s tournament. The anticipated activities range from World Cup-related phishing schemes to device infiltration and surveillance. Many of these malicious activities were present during the men’s World Cup in Brazil four years ago.
In general, major political events, such as summits and sporting events, are generally prime targets for nefarious digital activity. This year’s Olympic Destroyer attack during the Winter Olympics is perhaps the most recent example. Given that the men’s World Cup is held in Russia, it is easy to assume Russia itself will not be a target. However, that may be a short-sighted assumption. Increasingly, anti-government groups in authoritarian states target various government-related institutions and events with distributed denial of service attacks (DDoS) or various forms of ‘cyber vandalism’ such as website defacement that may disrupt business activities. Taking a look at this broader trend provides insight into what kind of anti-government cyber activity may occur surrounding the men’s World Cup over the next month.
Anti-Government Protests & Digital Attacks
Numerous authoritarian governments - such as China, Iran, and Russia - are well-known for the level of sophistication of their state-affiliated cyber groups. What is less discussed is the rise of anti-government hacktivists within these and contiguous states. Anti-government groups employ various kinds of cyber attacks to achieve a variety of objectives. Their motivations range from protesting specific government policies or actions to spotlighting various kinds of corruption or illicit government activity. Of course, in some situations the government itself is not the target, but rather the activities of foreign governments operating within a country are targeted.
In the case of the men’s World Cup, while the Russian government may not be inclined to target the event itself, both anti-government groups or regional groups fending off Russian interference may very well want to wreak havoc throughout the month-long event. In fact, protests occurred in Brazil in 2014 over the high costs of the World Cup, and coincided with a string of anti-governments DDoS and spearphishing attacks. Let’s take a look at a few recent examples of this kind of activity.
-
Venezuela: In 2014, South American anons led an effort targeting government websites following the domestic uprising and protests sparked by increased government censorship and repression. The cyber attacks included both website defacement and DDOS attacks. This quickly turned into a widespread campaign dubbed OpVenezuela. More recently, the Binary Guardians claim to have hacked 40% of government sites in April 2017, again during a time of heightened tensions.
-
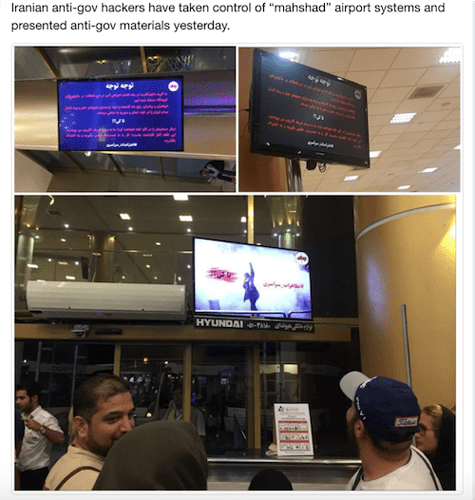
Iran: In May, an anti-government group hacked the airport system at an Iranian international airport in protest of military activities in the region. The group took control of the airport monitors and replaced it with anti-government content and a call to protests. They also took control of the email account of a civil aviation head to spread the news. Earlier this month, a group again disrupted an international airport, this time in Tabriz, by turning the monitors off. This is all occurring during a time of heightened censorship in Iran, including the recent extension of the ban on Telegram.
A Twitter Post from May 24, 2018
-
Ukraine: The Ukraine Cyber Alliance aims to counter Russian interference in Ukraine. The network of four groups - CyberHunta, Falcons Flame, Trinity, and RUH8 - targets the Kremlin, and aims to expose Russian interference abroad. Another group, InformNapalm, similarly targets Russia, and was created in response to the annexation of Crimea. The groups have compromised the Duma’s website, leaked emails, and published names of Russian military members, demonstrating a range of behavior all aimed at undermining the Kremlin. In some cases, both the Ukrainian government and other countries have condemned their behavior.
-
Lithuania: The broad impact of Russian trolls continues to garner much attention. To counter their activity, many Lithuanians have taken steps to disrupt the Russian propaganda with evidence-based campaigns. Known as the Elves, the group coordinates social media activity to counter the Russia disinformation. NATO has since made a video highlighting the anti-propaganda activity.
Digital Activism & the World Cup
Recently, a Ukrainian artist created a series of alternative World Cup posters to highlight Russian criminal activity and human rights violations. These spread quickly on the internet, and not surprisingly were a hit in Ukraine, but attacked in Russia. This kind of activity, however, may have copycats over the next month as the tournament progresses. With the recent Russian ban on Telegram disrupting major online activity and costing billions, the domestic environment is ripe for the kind of online protest behavior as we’ve seen elsewhere across the globe. This does not rule out the potential for a major attack of course - remember NotPetya also hit Russia as a self-imposed wound. However, when looking at motivations and resources required for various kinds of attacks, the greater likelihood are these kinds of anti-government cyber vandalism attacks with explicit messages and protests. While geopolitical tensions may seep into this global sporting event, most certainly we’ll see a series of epic goals, and epic dives, that will dominate online forums for remainder of the tournament.
Article Link: https://www.endgame.com/blog/technical-blog/growing-reach-anti-government-hacktivism-world-cup-next