
Today, the Messaging, Malware and Mobile Anti-Abuse Working Group (M3AAWG) gave the JD Falk Award to the Business Email Compromise (BEC) List.
The BEC List comprises cybersecurity firms, researchers and internet infrastructure companies that help deal with cybercriminal activities and schemes. The JD Falk Award is given to individuals or groups whose meritorious work has helped protect online users and organizations.
We commend the organizations, along with the threat and security researchers and analysts who were an instrumental part of the BEC List. Trend Micro is proud to be part of it as one of the first members at its inception in 2015. Our extensive research on BEC — from keyloggers such as Predator Pain, Limitless, and Hawkeye to the various email and social engineering tricks used in BEC — is a reflection of our commitment to making the world safe for the exchange of digital information.
Why tackle BEC?
Online scams are a recurring pain point for users and enterprises. BEC fraud in particular has accounted for over $12.5 billion in global losses since 2013, according to the FBI. Its operators use malware — many of which are bought in underground marketplaces — social engineering, or a combination of both to access and hijack systems or trick victims into wiring money into an account the cybercriminal controls. Our further research into BEC also revealed a steady increase in BEC-related attempts.
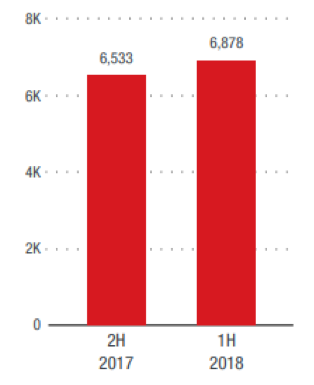
Figure 1: Half-year comparison of recorded BEC attempts
Note: Data refers to the number of BEC attempts seen, which does not indicate whether the attacks were successful. BEC samples consist mainly of CEO fraud (attackers posing as CEO/executive).
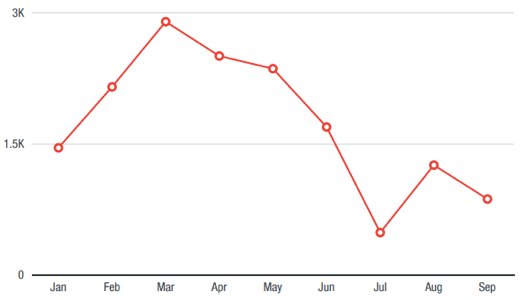
Figure 2: Malware samples used in BEC attacks from January 2017 to September 2017 based on VirusTotal samples
The number of perpetrators and the scope of their crime require a combined effort between individuals and organizations across the cybersecurity community to help thwart threats like BEC.
Previous recipients of the JD Falk Award were involved in various takedowns that required significant coordination and knowledge sharing such as the Avalanche takedown in December 2016 and DNS Changer Working Group in November 2011.
We are honored to be recognized by the M3AAWG with this award. Our efforts to stop cybercriminals from successful BEC attacks – and all cybercrime – will continue.
The post The BEC List: Helping Thwart Business Email Compromise through Collaboration appeared first on .
Article Link: https://blog.trendmicro.com/the-bec-list-helping-thwart-business-email-compromise-through-collaboration/