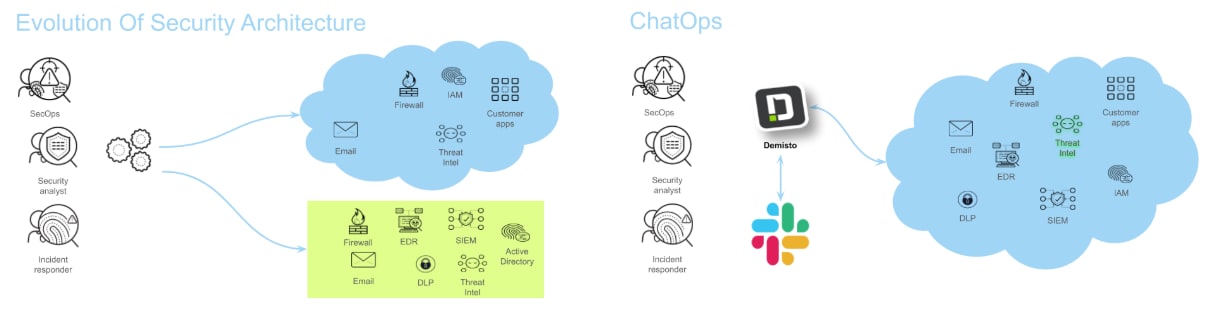
Scaling assets and applications in the cloud creates a degree of complexity that often leads to misconfigurations and vulnerabilities. With this increased complexity, other process issues begin to surface, such the need for a collaborative space to share threat intelligence information and lessons learned, or an audit trail of actions taken during the investigation.
Automations are often created by both team members and product vendors to alleviate some of these issues. I’ve worked with exceptional analysts and engineers who have successful processes and techniques powered by custom-built scripts and applications to make their lives easier. For instance, a security analyst may create Python scripts to format and transform data to more easily comprehensible information. However, custom tools are often difficult to leverage at scale due to limited compute and/or inability to access and launch cloud functions. Additionally, custom tools often lack a friendly user interface.
By taking these automations and combining them with modern chat interfaces and existing tools, we can combat these issues. For example, creating a Slack bot can assist by inviting users to a collaborative space and sharing relevant information about an alert or incident.
In this post, I’ll explore how to scale automation efforts with a focus on threat intelligence, leveraging Cortex XSOAR to ingest alerts from security controls and to automate reports for analysts. Additionally, I’ll show how Slack can be used as a collaborative space that automatically invites team members and provides alert context.
XSOAR to ingest alerts from security controls and to automate reports for analysts. Additionally, I’ll show how Slack can be used as a collaborative space that automatically invites team members and provides alert context.
Automated Bots
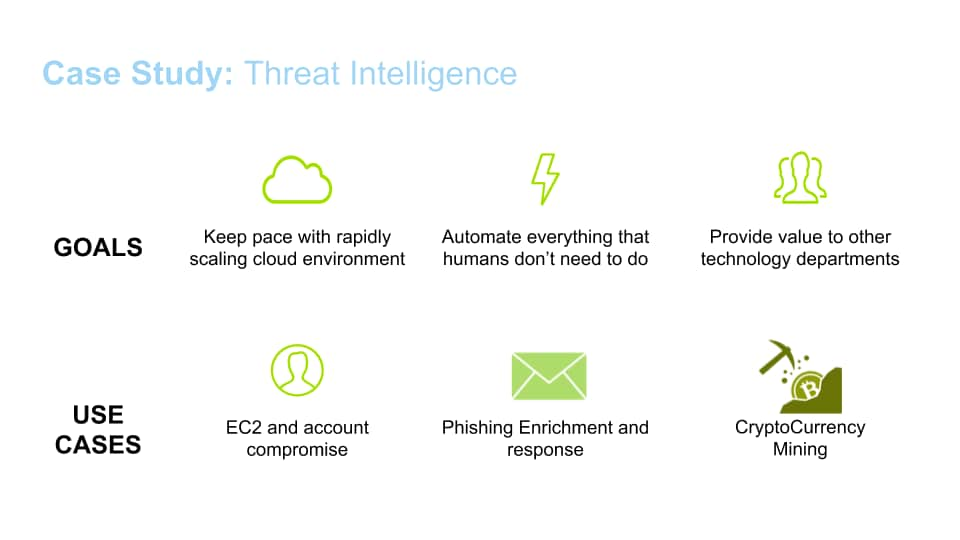
The image below describes common goals and use cases where an automated bot can assist. Each of these use cases requires different contextual information for responding to the event types. For example, email headers, email subject and email body are artifacts that can expose threats to users. Additionally, analysts often leverage threat intelligence data sources to determine if the threat has been previously identified.
Fig 2: Use cases where a Cloud Threat Intel Bot can assistThreat intelligence data is contextual information that may provide details about the who, what, when and where of an attack. Using this data could assist with making informed decisions when answering security questions and responding to events.
Threat intelligence doesn’t guarantee success when responding to these events, but it can serve as a great data source for analysts and engineers. There are also information sharing groups called Information Sharing and Analysis Centers (ISACs) that your organization may be eligible to join. These groups can serve as a great source when retrieving context about an attack or event seen by companies in the same industry.
Today, leveraging threat intelligence and coupling it with alert data comes with challenges. More specifically, few case-management platforms support storing data gathered from alerts and threat intelligence. This creates challenges pivoting from data point to data point and coupling it with alerts from our data sources. By documenting analyst tradecraft, playbooks can be created that facilitate the delivery of threat intelligence to analysts. Delivering this information in a common workspace such as Slack enables organizations to enrich data on demand while displaying a log of analyst actions and chats.
Creating a Threat Intelligence Bot
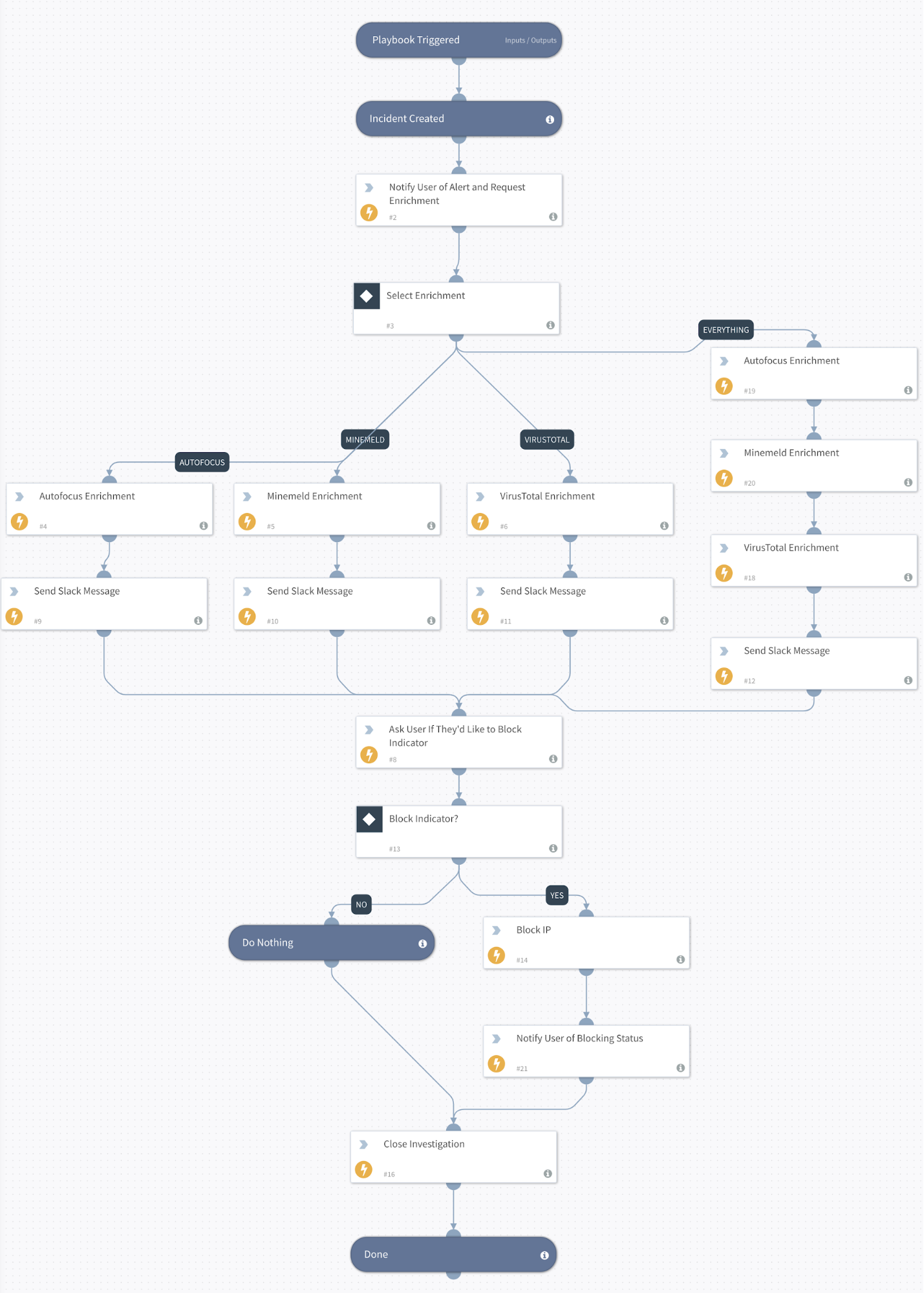
Fig 3: How a Cortex XSOAR playbook powers bot logicFor the following examples, Cortex XSOAR will be leveraged to ingest alerts from cloud applications and threat intelligence sources and orchestrate bot logic via a playbook.
As alerts are generated and threat context is provided, opportunities begin to emerge for rapid response and remediation. The delivery of alert data and threat intelligence context is facilitated by the Cortex XSOAR playbook and sent to a collaborative workspace or war room, such as Slack. An organization could also use other chat services such as Microsoft Teams or Discord.
As an example, phishing campaigns send mass emails to as many users as possible. This threat may be reported by several users or applications. As duplicate or related events are seen by Cortex XSOAR, our threat intelligence bot can provide correlated event information and the option to block malicious indicators on demand. For more sensitive events such as malware outbreaks, analysts may want to enrich threat data with specific threat intelligence sources to avoid tipping the attacker that an investigation is ongoing. The playbook then controls our threat intelligence bot logic and selectively enriches threat data based on an analyst response.
Another common threat that cloud applications are exposed to is cryptocurrency mining. When this threat emerges, response strategies need to be implemented immediately. This often includes blocking malicious IP addresses and reprovisioning cloud applications. To avoid analyst burnout and error, simple tasks can be performed via our threat intelligence bot. For example, the playbook in figure 3 contains an optional path for blocking IP addresses at the firewall.
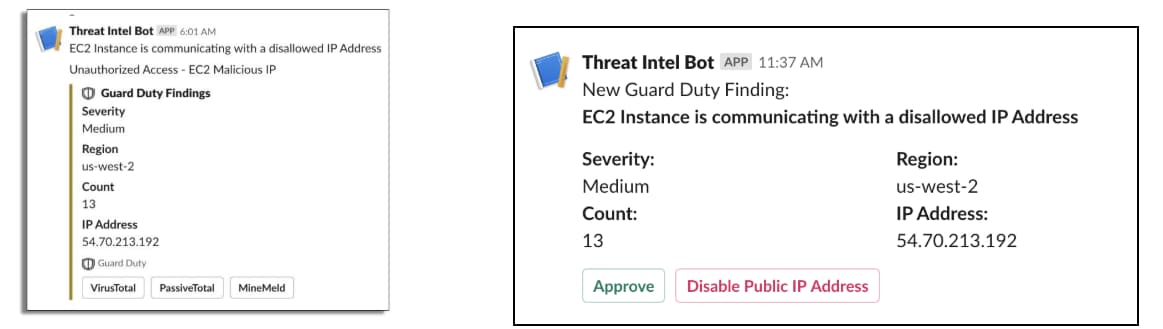
Fig 4: Threat intel provided by a botDepending on the context of the alert and threat intelligence supplied, specific analysts and engineers are required to collaboratively respond to events. As mentioned, automation often assists with this investigation phase. Additional logic can be implemented in our playbook to invite users on demand and restrict access to a Slack channel when sensitive information is contained within an investigation.
When to Use a Threat Intelligence Bot
In summary, as organizations migrate and onboard services and applications to the cloud, managing and responding to alerts can become increasingly difficult. Automation can assist with responding and mitigating security events generated from applications and users. Leveraging chat services such as Slack can assist with creating an interface for automation tools that were previously difficult to interact with, while providing an audit trail of events that transpire during an investigation. Pairing automation and Cortex XSOAR can enable organizations to create an interactive war room that assists analysts during each phase of their investigation.
Go more in-depth on threat intelligence bots – check out Ron’s on-demand session, “Creating Threat Intel Bots in the Cloud,” from our recent Cloud Native Security Summit.
The post The Art of Automation: Creating Threat Intelligence Bots in the Cloud appeared first on Palo Alto Networks Blog.
Article Link: http://feedproxy.google.com/~r/PaloAltoNetworks/~3/yomOwVCeAyI/