While it is normal to see a positive trend in terms of number of artifacts analyzed by our engines, a stark increase might in some cases be the telltale sign of a shift in the threat landscape. Just recently, our threat intelligence telemetry alerted us of an anomalous surge of Agent Tesla binaries detected in the wild. While the threat is quite well-known, the number of different samples (100% increase in just 3 months) prompted us to further investigate the underlying cause.
In this threat report, we outline the extent of the surge, and detail which customer verticals appear to be more impacted. We also illustrate how easy it is to custom-build new samples evading traditional signature-based defenses, and how this ease-of-use translated to a plethora of variants, all including the very same noxious info-stealer functionality. In the last section, we release a YARA rule tailored to reliably detect the payload regardless of the module enabled, and discuss the efficacy of VT retro-hunting.
The Surge
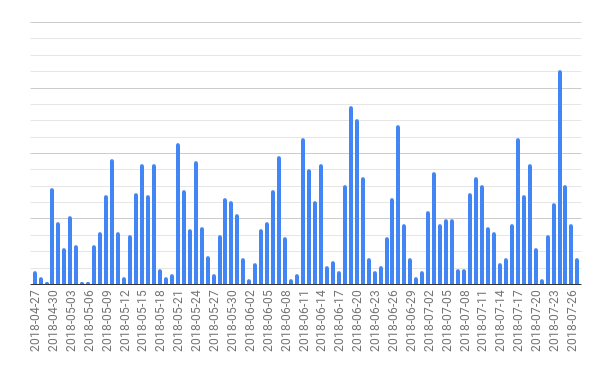
Figure 1: The increasing number of Agent Tesla samples detected by our telemetry.
Agent Tesla is a well-known monitoring software written in .Net. Acting as a fully-functional information stealer, it is capable of extracting credentials from different browsers, mail, and FTP clients. It logs keys and clipboards data, captures screen and video, and performs form-grabbing (Instagram, Twitter, Gmail, Facebook, etc.) attacks. It is quite clear how a surge of detections, as shown in Figure 1, might be a worrying sign: info-stealers are able to quickly impact a company’s operations and revenue, and thus shall not be underestimated.
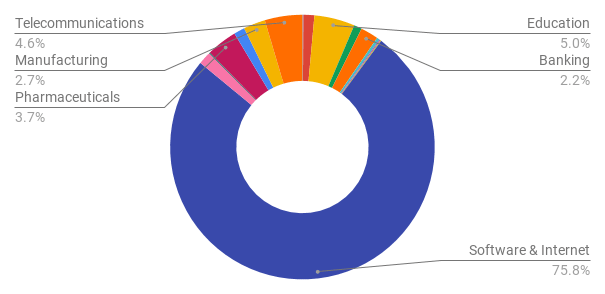
Figure 2: Customer verticals most affected by the wave of Agent Tesla.
Figure 2 shows the detections pivoted by the affected verticals. The lion’s share goes to the “Software and Internet” vertical, potentially indicating how businesses that are less compartmentalized and therefore more susceptible to attacks using continually updated code hashes might be more exposed to (or a more likely target of) off-the-shelf info-stealers featuring plentiful variants.
The productization of this piece of malware is so advanced that prospective customers can purchase it online by choosing one of the available options: bronze, silver, gold, or platinum. The last two allow the buyer to additionally pack the binary with a FUD packer, and ship it via document exploit (or VBA downloader) for its further execution on the target machine. Agent Tesla also runs its own discord channel, 24/7 support, and regularly publishes updates. Both aspects mean that there is a dedicated team standing behind this regrettably successful product.
To Each His Own (Agent Tesla) Flavour
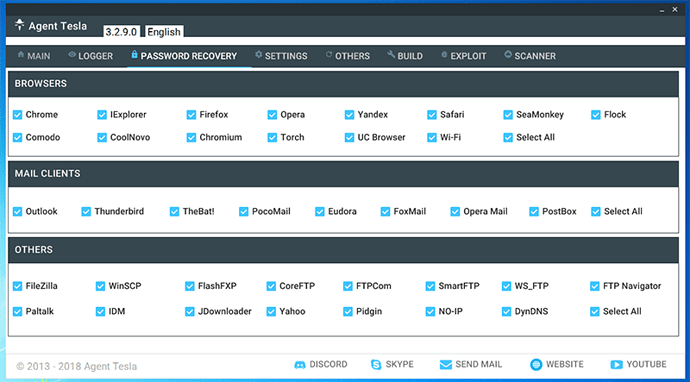
Crafting your own Agent Tesla into an executable or malicious document is an incredibly straightforward process: the user just needs to access the provided builder. Its control panel is user-friendly and explains at length every single option. In just a couple of clicks it is possible to select what information is to be targeted, and how the stolen data shall be exfiltrated. See Figure 3 to see all the info stealer modules available.
Figure 3: Info-stealer modules available in Agent Tesla. Or in other words, how to be spoilt for choice.
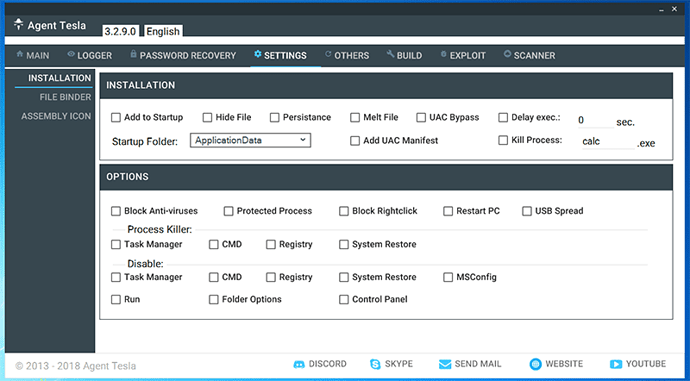
Agent Tesla provides functionalities to assure its persistence, and increase the likelihood of staying under the radar. It is possible to auto-start the malware after reboot, disable some Windows utilities (including “Task Manager”), delay its execution, bypass known anti-analysis tools, and more (see Figure 4 for the whole list).
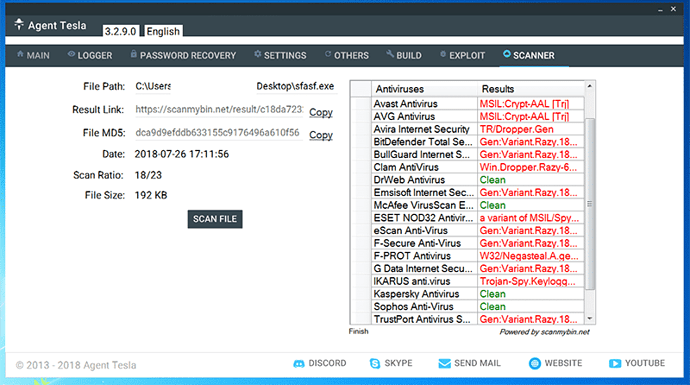
Standard tricks might not be enough if the binary is meant to stay under the radar against common AV solutions. This is why Agent Tesla even embeds a crypter and scanner (see Figure 5) based on scanmybin.net. These are all necessary steps to tentatively grant to the resulting artefact FUD (Fully UnDetectable) status without uploading the data to VirusTotal, which would ultimately share the sample with subscribing AV vendors.
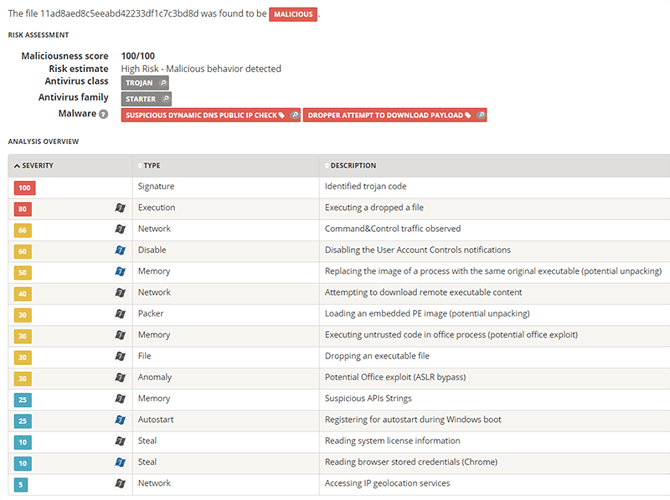
As we mentioned, the actual delivery takes many forms, including EXE, XLS, DOC, DOCX, VBS, and highly-obfuscated RTF files. In some cases, our Global Threat Intelligence Network managed to isolate a number of samples relying on vulnerabilities exploiting the Equation Editor executable (see here for more information on this vulnerability class). Figure 6 shows one of such samples, and details all the steps of the infection chain.
Figure 6: Example of a delivery (sha1: 521bac9e6e95ef975f224a862a5ace54920d8a1c)) via the Equation Editor exploit.
Different Modules, Identical Core
Because of the packer/crypter and the high number of potential modules, static analysis might not be able to generalize well enough to reliably detect all Agent Tesla variants.
This is why relying on data and code introspection and extracting memory dumps dynamically are both necessary building blocks to classify Agent Tesla at scale. In particular, the ability to unpack executables and statically analyze the output addresses both coverage and completeness concerns. This is exactly our approach: while we actively maintain a repository of YARA rules, we execute the static analyzer for every single step of the dynamic analysis. By adopting this approach we can craft rules that are both extremely precise (because they are profiling only code specific to the threat in question) and complete (the rules are guaranteed to be run on all the code whether it is executed or not).
Attached below, you can find one of the YARA rules we considered for this specific threat. As you can see the rule targets the password and key salt from the main decryption function, a precise indicator to trigger detection.
private rule IsPE
{
condition:
uint16(0) == 0x5A4D and
uint32(uint32(0x3C)) == 0x00004550
}
rule Agent_Tesla : Agent_Tesla
{
strings:
$pass = “amp4Z0wpKzJ5Cg0GDT5sJD0sMw0IDAsaGQ1Afik6NwXr6rrSEQE=” fullword ascii wide nocase
$salt = “aGQ1Afik6NampDT5sJEQE4Z0wpsMw0IDAD06rrSswXrKzJ5Cg0G=” fullword ascii wide nocase
condition:
IsPE and all of them
}
Note that relying on YARA rules aimed at the payload might lead to suboptimal results when using the retro-hunting utility of VT (the rule above yields to approx 353 different matches). Besides the fact that very few engines attempt to statically unpack the input binary, matching a rule against the final payload requires all layers of encryption/packing to be completely removed, a non-trivial feat if dynamic analysis is not employed.
Conclusions
In this blog post, we analyzed a recent surge of Agent Tesla samples. While the threat is a known one, the ease of use due to its advanced productization led to a stark increase of new variants. We also share a YARA rule to reliably detect this threat when matched against the implant’s innermost payload.
The post Tales From the Field: The Surge of Agent Tesla appeared first on Lastline.
Article Link: https://www.lastline.com/labsblog/surge-of-agent-tesla-threat-report/