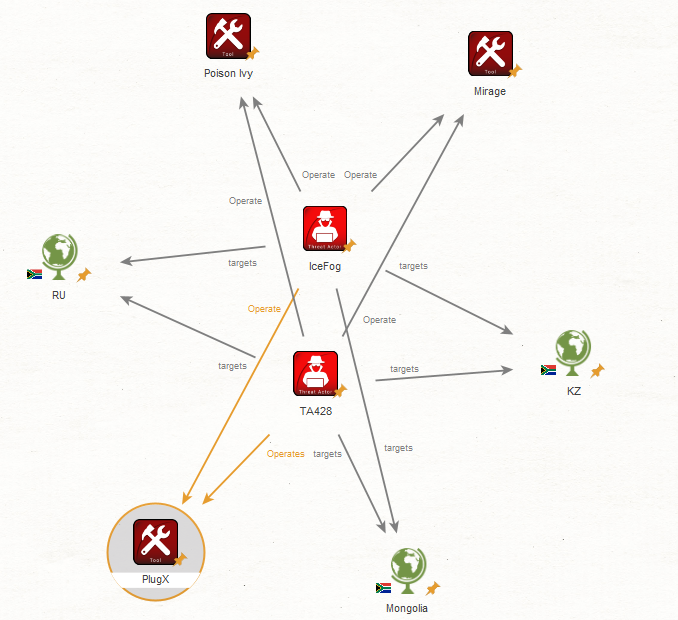
TA428 behind Operation Lagtime: the following of IceFog ?
In Chinese APT, Russia was the playground of IceFog with other country like Kazaghstan, Tadjikistan or Mongolia.
Into the Fog — The Return of ICEFOG APT — Speaker Deck
Now many report of APT, many campaigns target those countries by TA428 with many TTPs similare:
- DNS dynamic
- Sideloading
- Using same encryption
- Mirage, PlugX, Poison Ivy
Dr web has pusblished two reports very similare Study of targeted attacks on Russian research institutes (drweb.com) and Study of the APT attacks on state institutions in Kazakhstan and Kyrgyzstan (drweb.com) Theses actors used the same malware during those campaigns and the geographical aera is Russia and Central Asia.
With high confidence, it’s the same actor behind those campaign. And we have a link with Icefog: nicodonald[.]accesscam[.]o r g
This domain has used in the campaign 2019 Skyline.
if the operator behind Chinoxy/Cotx is TA428, this backdoor has used in campaign against Vietnam. Or Icefog has started in Vietnam too and Kirzighstan: New version of chinoxy backdoor using COVID19 alerts document lure | by Sebdraven | Medium
The sample has found against Mongolia developped in .NET has the similare functionnalities than TManger of TA428
So very a good confidence, TA428 has the following of IceFog in for operations against Russia, Central and South Est Asia.
Article Link: TA428 behind Operation Lagtime: the following of IceFog ? | by Sebdraven | Jun, 2021 | Medium