Analysis of latest malware strain from APT37

Introduction:- My purpose of writing of this blog is to produce intel on recent malware campaigning done by the sick pathetic APT37 (run by dictator NK government & is a NK RGB Military Intelligence state-sponsored espionage APT group often known as Lazarus) on South Korea online newspaper for implanting surveillance and for conducting espionage which is main motive of this particular APT group. In these 2 blog I will be performing my analysis around this malware by statically & dynamically analyzing for making the task easier for infosec community in understanding the capabilities of this malware so that community can work accordingly in detecting this particular malware strain easily. This is the 1st part of analysis in which i only be performing Static Analysis.
Analysis
Basic Analysis:- On gathering information on this sample of Bluelight malware by throwing it into the PE Studio it can concluded that file is malicious and it’s 32-bit binary.
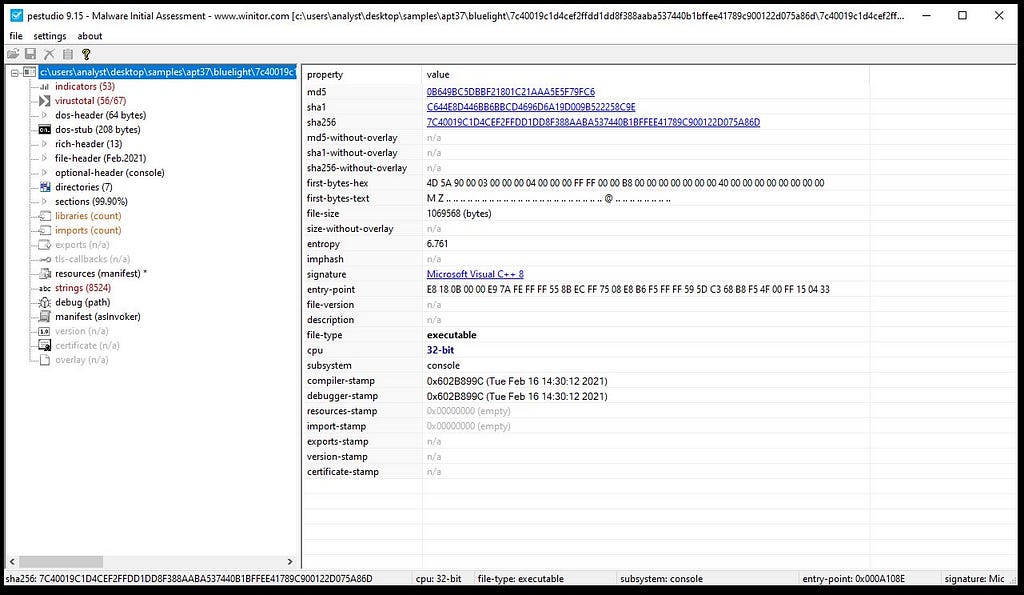 On dragging the Bluelight malware in the PE Studio for gathering information.
On dragging the Bluelight malware in the PE Studio for gathering information.On dropping this sample in the online 32-bit binary unpacking sandbox Unpac.me it shown that file is not in packed state. So, there is not need to unpack the binary.
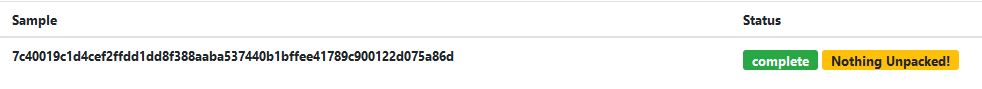 On dropping the Bluelight malware in Unpac.me.
On dropping the Bluelight malware in Unpac.me.Advanced Analysis:- For starting off advance static analysis, we need to throw the sample in the IDA. For starting of our analysis first thing that we need to look for is the export table. As there is only one function which is “start”.
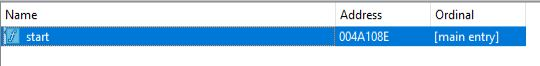 Export table of Bluelight malware.
Export table of Bluelight malware.start function:
In the start function, there are two functional calls are being made which are:
::- bof_mitigation()
::- main_fun_caller()
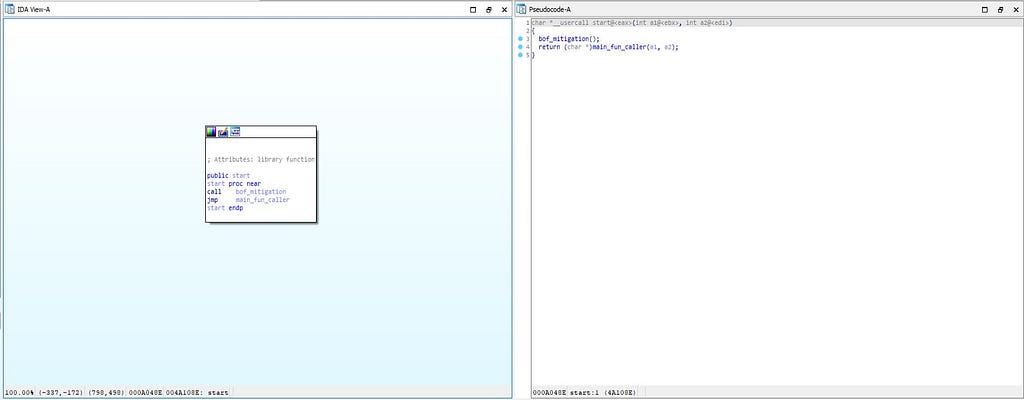 Call graph & reversed code of start() function.
Call graph & reversed code of start() function.bof_mitigation function:
This function is being used for buffer overflow mitigation during the execution “Bluelight” malware.
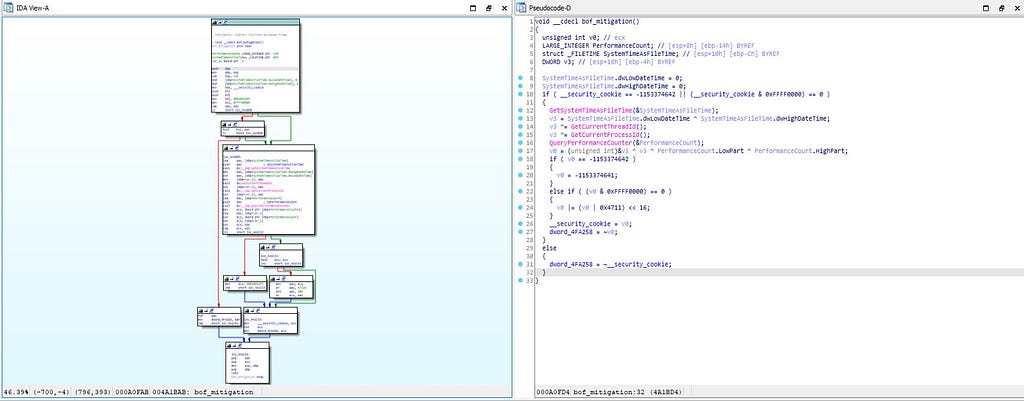 Call graph & reversed code of bof_mitigation() function.
Call graph & reversed code of bof_mitigation() function.main_fun_caller function:
Work of this function is calling main function which carries out all the operations for malware besides that calls to several other functions is being made in this module of “Bluelight” malware.
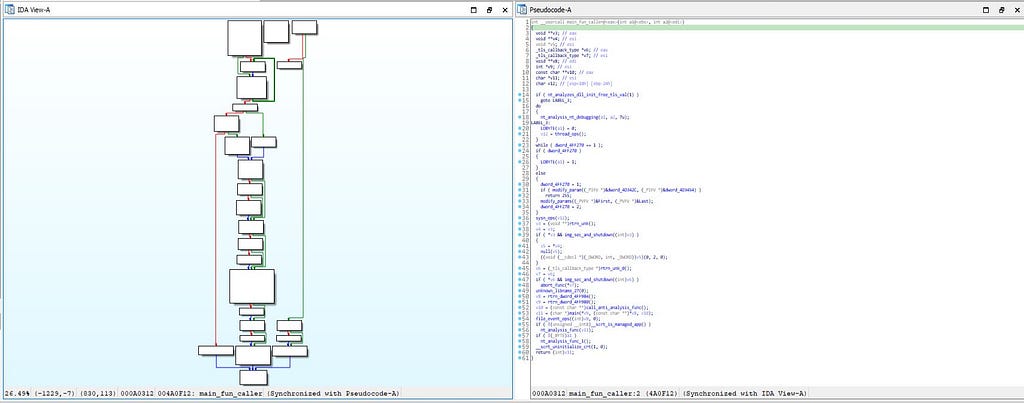 Call graph & reversed code of main_fun_caller() function
Call graph & reversed code of main_fun_caller() functionAs we can see some of the function in this main module is being developed by APT37 malware developers for slowing up the forensics analyst work by making use of obfuscation and anti debugging and anti analysis functions as mentioned above but they failed in fooling us as usual, we caught them tight.
Other than main func. following functions are being called in this module:
nt_analyzes_dll_init_free_tls_val(), nt_analysis_nt_debugging(), thread_ops(), modify_param(), sysn_ops(), img_sec_and_shutdown(), abort_func(), call_anti_analysis_func(), file_event_ops().
nt_analyzes_dll_init_free_tls_val function:
In this module, nt_analysis_processor_chcks() function is being developed by malware authors to look for the feature of the system on which “bluelight” malware is being running & for that purpose it make use of “IsProcessorFeaturePresent()” function present in this module.
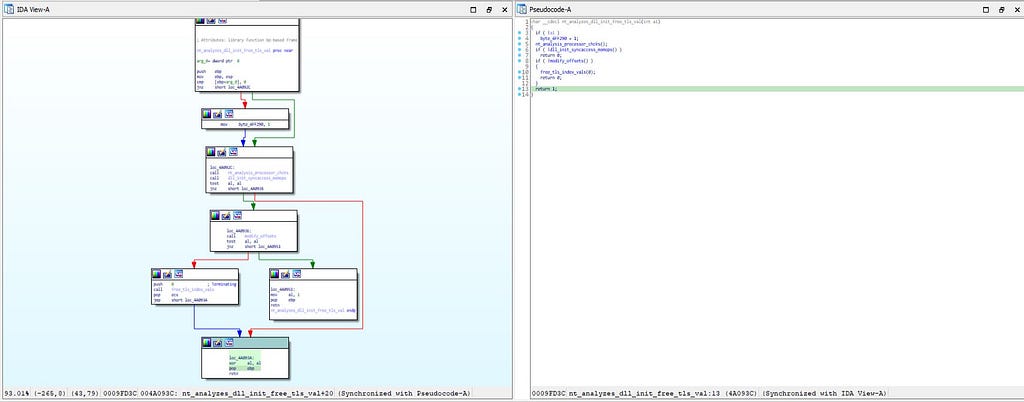 Call graph & reversed code of nt_analyzes_dll_init_free_tls_val function
Call graph & reversed code of nt_analyzes_dll_init_free_tls_val functionAnd just after few if statements are being executed for freeing up memory on infected system and other is being used for returning true value.
nt_analysis_nt_debugging function:
In this module, authors of “Bluelight” developers have make use of “IsDebuggerPresent()” function which is responsible to look for if the debugger is running on infected system on which “Bluelight” malware is being running what it does is that if debugger is being running on system then the malware won’t allow it’s debugging on infected system. And as a whole is known as anti-debugging technique.
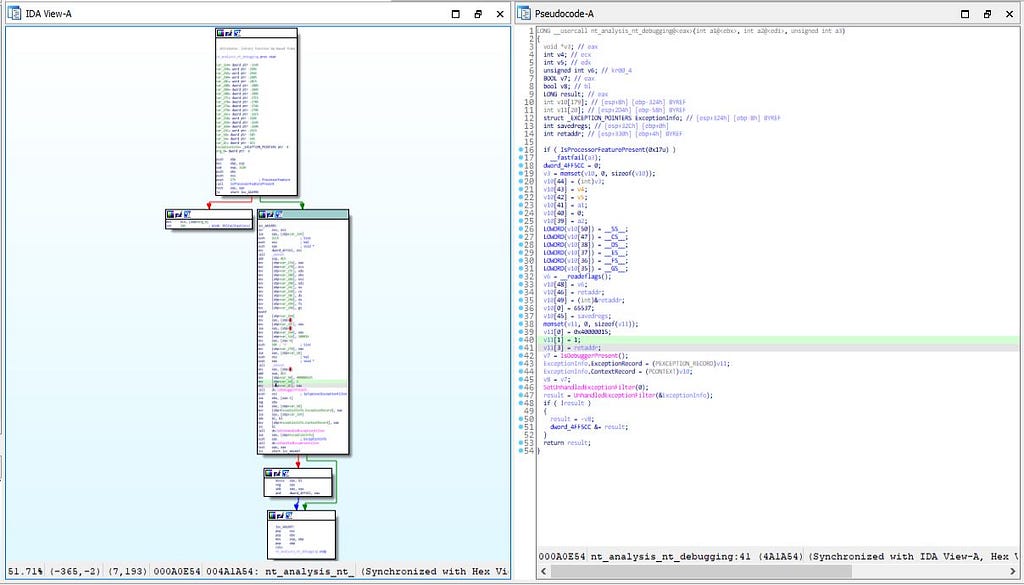 Call graph & reversed code of nt_analysis_nt_debugging function
Call graph & reversed code of nt_analysis_nt_debugging functionimg_sec_and_shutdown function:
In this function, the image section operations is being happening along with the one if statement looking for the shutdown operations.
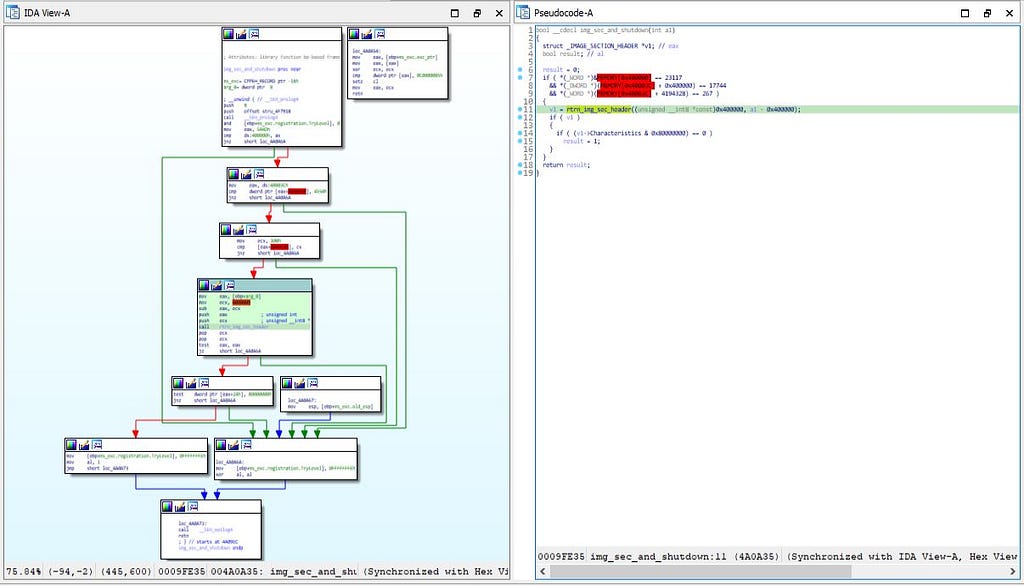 Call graph & reversed code of img_sec_and_shutdown function.
Call graph & reversed code of img_sec_and_shutdown function.Where all other functions in this module “main_fun_caller” function are either used for thread, file or anti analysis purpose.
main function:
In this function, firstly the number of milliseconds is stored in the “no_of_millsec” by making use of “GetTickCount()” function and printed using the function “no_of_millsec()”. “calr_sync_proc” function is being used for the syncing the processes with the value of “ no_of_millsec”.
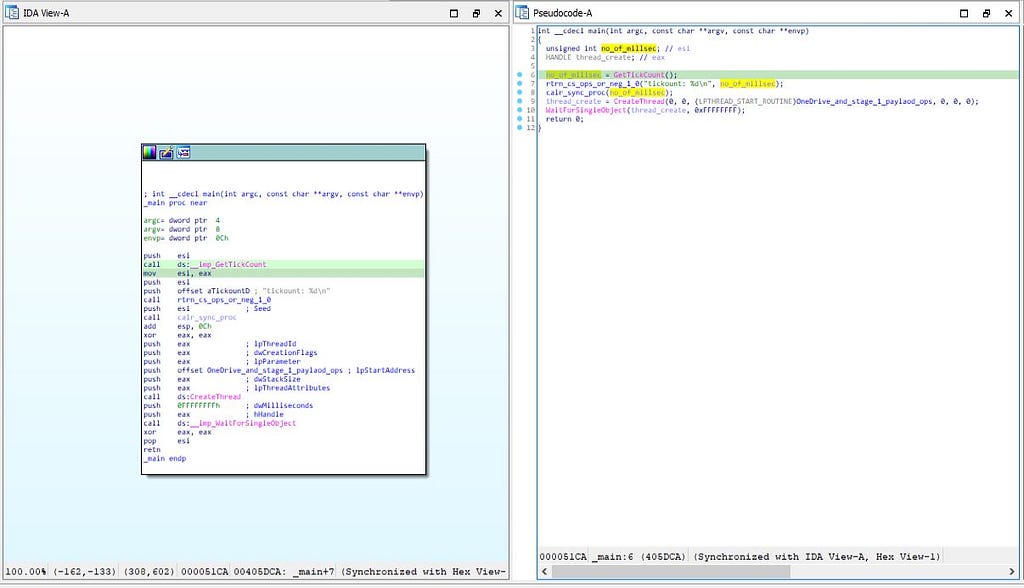 Call graph & reversed code of main function
Call graph & reversed code of main functionSoon further moving in this module there is the variable named as “threat_create” which is being developed to store the created thread using CreateThread() function which is here being deployed for the execution of the function “OneDrive_and_stage_1_paylaod_ops()” as thread and wait is being executed till the “thread_create” object signaled passing “thread_create” as the first parameter in the WaitForSingleObject() function and if all statements executions succeeds then the true value is being returned by the main function.
OneDrive_and_stage_1_paylaod_ops function:
After performing some string operations in this module, there is “Oauth_API_and_OneDrive_API_access” function which is the being called for “Oauth_API” & “OneDrive_API” access to perform C2 ( command and control server) operations.
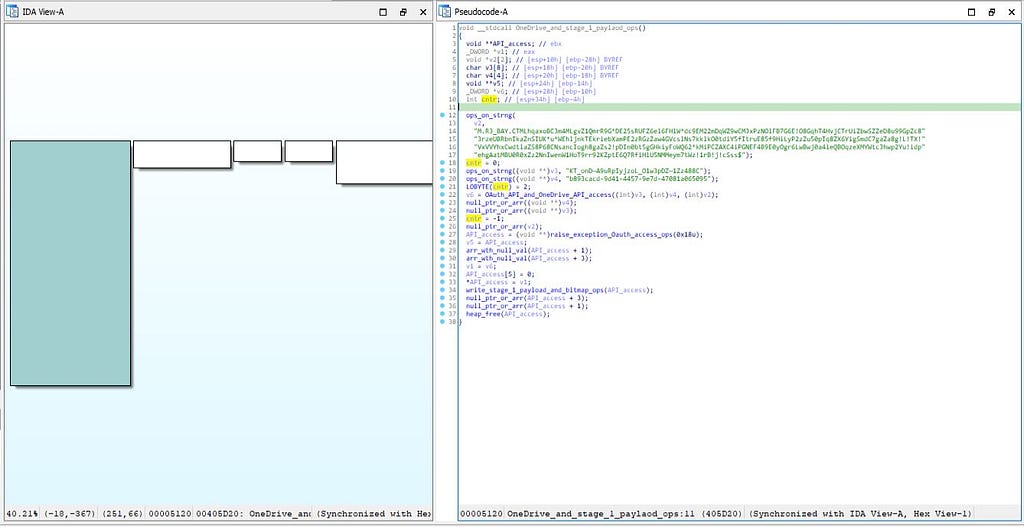 Call graph & reversed code of OneDrive_and_stage_1_paylaod_ops function
Call graph & reversed code of OneDrive_and_stage_1_paylaod_ops functionOauth_API_and_OneDrive_API_access function:
In this module, as the execution of this module happens, exception are raised & Oauth access operations are being performed with “raise_exception_Oauth_access_ops” & its being stored in v6 and after it the “rtrn_handle_Mutex_obj__and_Oauth_obj” function execution is being
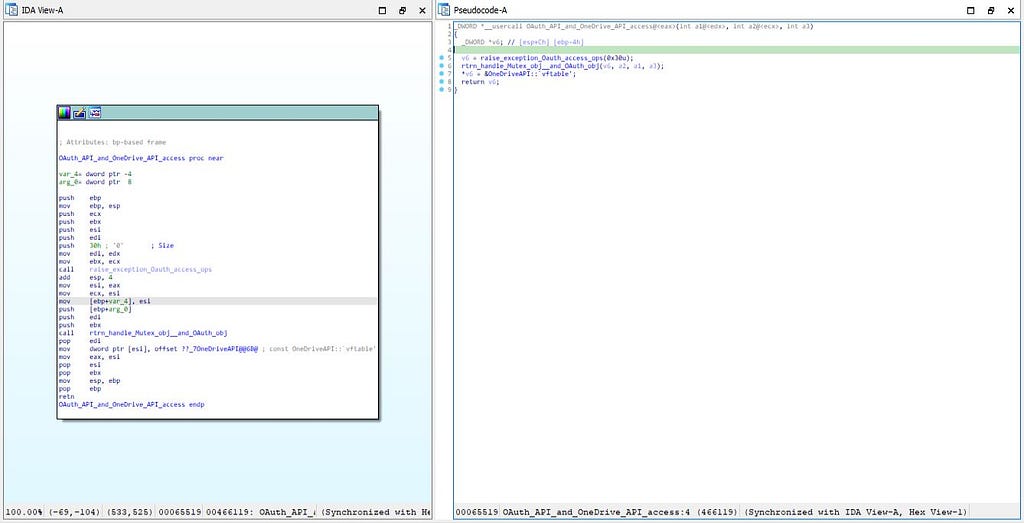 Call graph & reversed code of Oauth_API_and_OneDrive_API_access
Call graph & reversed code of Oauth_API_and_OneDrive_API_accessperformed that works for returning handle to the Mutex & OAuth object and followed by it is the address of “OneDriveAPI” having the access of virtual function table for some kind of functionality at runtime & it’s being in the pointer to v6 means it’s having value of the value present at the address of v6 and this value is returned by this module for creating appfolder in OneDrive that we will see further in this blog. Before freeing the heap , another call is being made to “write_stage_1_payload_and_bitmap_ops” function.
write_stage_1_payload_and_bitmap_ops function:
In this function, result variable contains the 0 or 1 value got from the “rtrn_0_or_1” function.
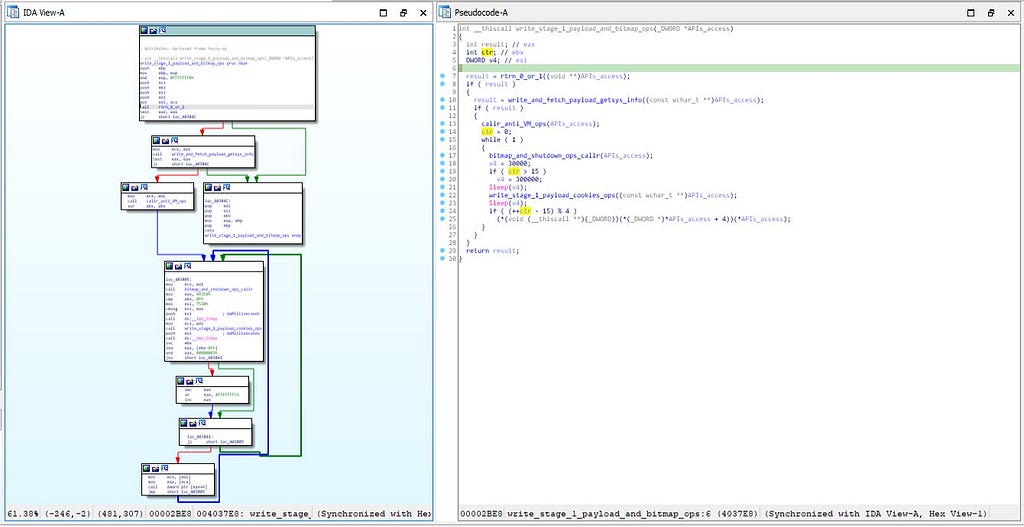 Call graph & reversed code of write_stage_1_payload_and_bitmap_ops function
Call graph & reversed code of write_stage_1_payload_and_bitmap_ops functionIn this function, result variable contains the 0 or 1 value got from the “rtrn_0_or_1” function. As moving in this module “if” statement is being run and then in the first statement in it “result” is being used store “write_and_fetch_payload_getsys_info”.
write_and_fetch_payload_getsys_info function:
This module is being developed for making call to the “get_payload_and_gather_sys_info” function which is being used for get payload (plugins) from C&C server then taking further look in this module we can see that call is being made to “write_ops” module which recon. data from infected system by “Bluelight” malware stores in the “logo/title.jpg” sub-directory that is further discussed in this blog.
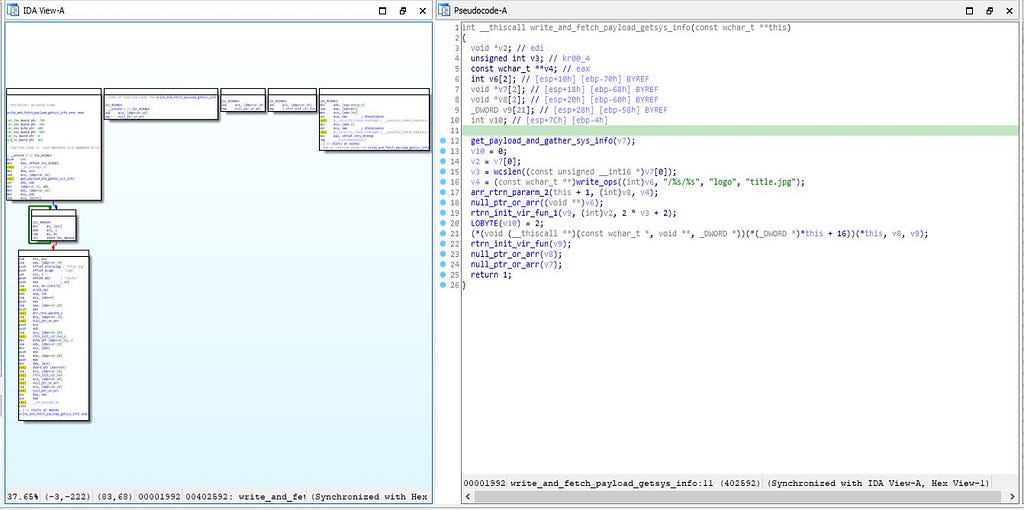 Call graph & reversed code of write_and_fetch_payload_getsys_info function
Call graph & reversed code of write_and_fetch_payload_getsys_info functionget_payload_and_gather_sys_info function:
This function is responsible for gathering system information along with the fetching payload (plugins) from Command and Control Server ( C&C ). After some operations on string call is being made to “get_payload_via_WinINet_app” function.
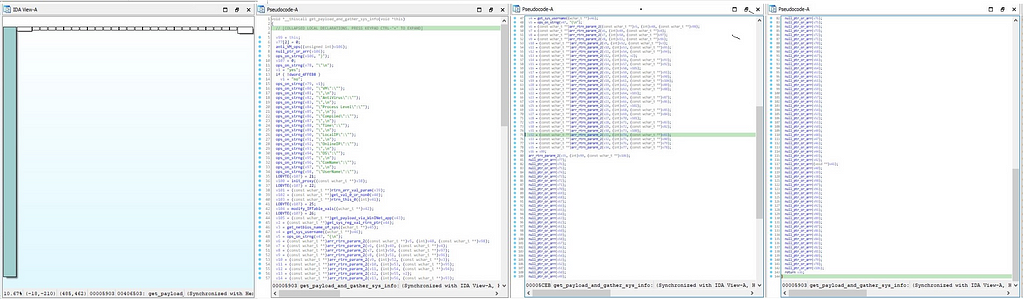 Call graph & reversed code of get_payload_and_gather_sys_info function
Call graph & reversed code of get_payload_and_gather_sys_info functionget_payload_via_WinINet_app function:
Using the WinINet application in this function, payload (plugins) from C2 (C&C) server is being fetched other than that in this module call is being made to “mem_ops_and_anti_analysis_ops” function which is the module that perform the memory operations after fetched plugins from C2.
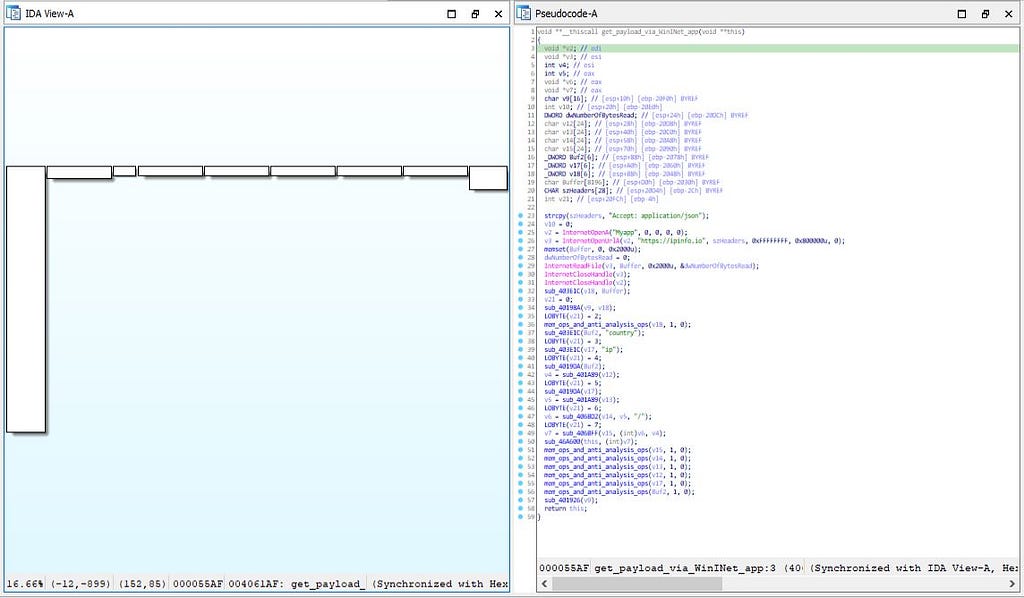 Call graph & reversed code of get_payload_via_WinINet_app function
Call graph & reversed code of get_payload_via_WinINet_app function& now jumping back in the “write_stage_1_payload_and_bitmap_ops” module from where we left . “if” statement is being executed with the result as parameter and first statement executed inside this nested “if” is the call to “callr_anti_VM_ops” function which is used for the perform anti-VM operations.
Soon after that, while loop is being executed having “ctr” as counter initiated with the 0 and having conditional check as 1. In the loop, in the starting the “bitmap_and_shutdown_ops_callr” function is being executed which works for making call to shutdown operations. After it the “if” statement is being run every-time whenever the parameter having condition greater than the numeric value 15. Soon after execution Sleep function with “v4” as parameter call is being made to “write_stage_1_payload_cookies_ops” function.
write_stage_1_payload_cookies_ops function:
Now it’s time to look into the techniques developed by APT37 malware developers for communication and storing stolen data from infected system in the cloud OneDrive appfolder discussed earlier as you can observe “background” directory is being created. & after execution of “mem_ops_and_anti_analysis_ops”.
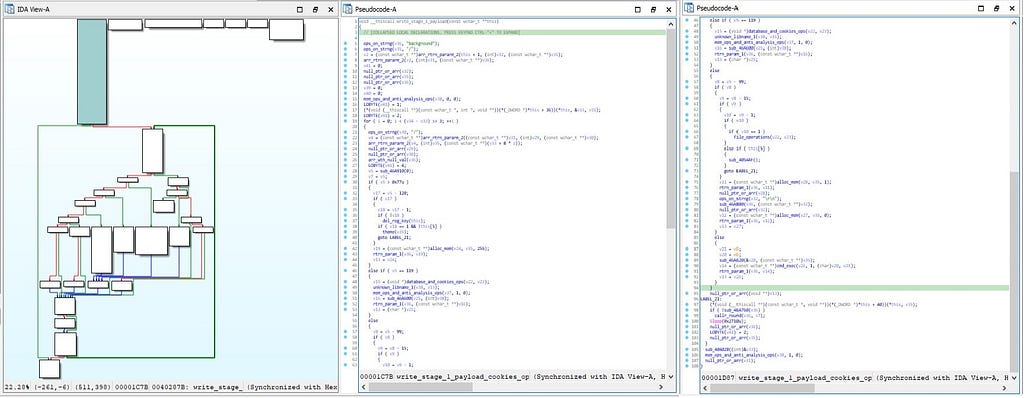 Call graph & reversed code of write_stage_1_payload_cookies_ops function
Call graph & reversed code of write_stage_1_payload_cookies_ops functionDuring the execution of for loop, inside there is the nested if present in for loop & in it after the “del_reg_key” is being executed “theme” directory is being created in appfolder in OneDrive.
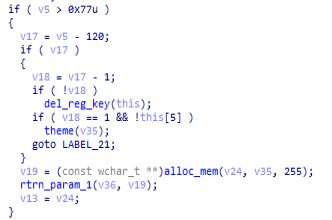
del_reg_key function:
In this module deletion of registry key value is being happening present in the “HKEY_CURRENT_USER”.
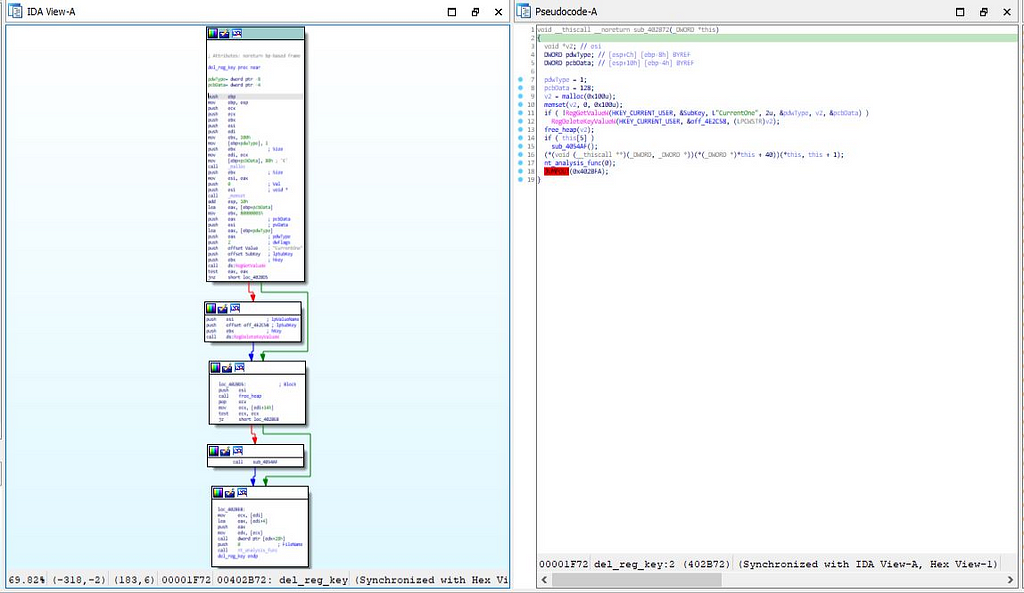 Call graph & reversed code of del_reg_key function
Call graph & reversed code of del_reg_key functiontheme function:
In this module using OneDrive API Access directory is being created in appfolder.
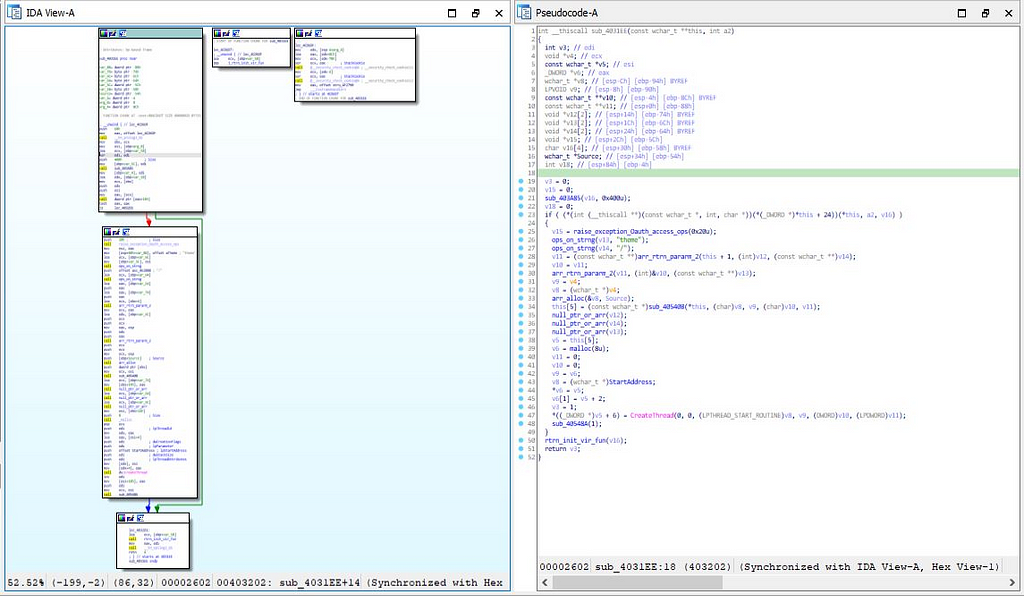 Call graph & reversed code of theme function
Call graph & reversed code of theme functionJust after the completion of “if” statement
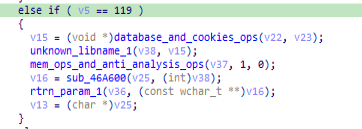
database_and_cookies_ops function :
In this module, harvested passwords & cookies from different browsers like:
:- Win7 IE,
:- Win10 IE,
:- Edge,
:- Chrome,
:- Naver Whale
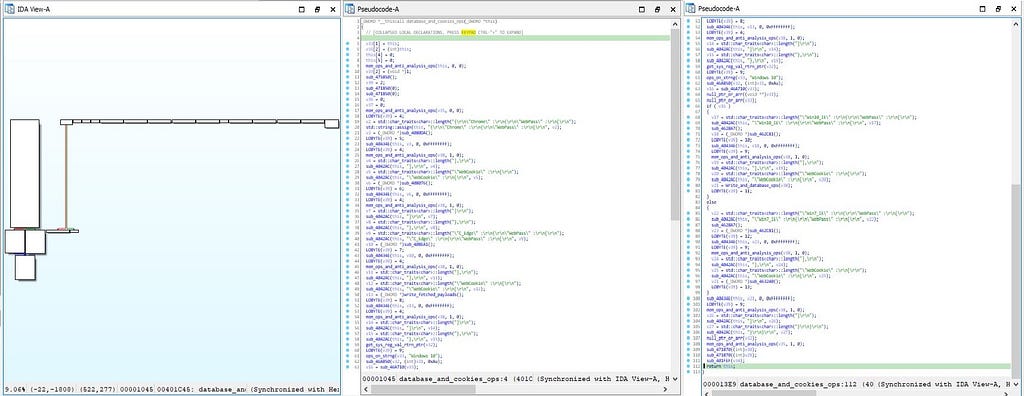 Call graph & reversed code of database_and_cookies_ops
Call graph & reversed code of database_and_cookies_ops& this is the subroutine ( module ) present in “Bluelight” malware for harvesting cookies & passwords from chrome browser which is having code for all other browsers for harvesting passwords and cookies.
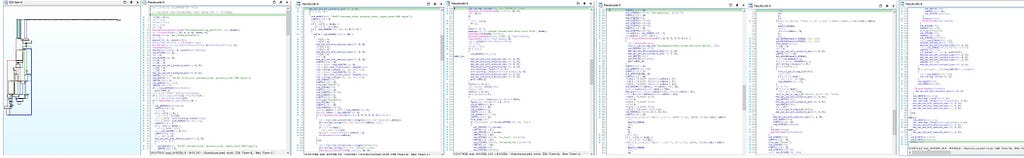 Call graph & reversed code of passwords and cookies harvesting function.
Call graph & reversed code of passwords and cookies harvesting function.then after that call to “Write_and_database_ops” function is being made.
Write_and_database_ops function:
In the function APT37 developers had used a technique to store the cookies and database and logs using “Storage Engine File”.
Function used in this module are:
JetSetSystemParameterA()
JetCreateInstanceA()
JetInit,
JetAttachDatabaseW() etc, etc.
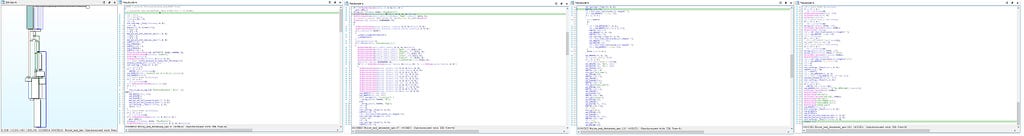 Call graph & reversed code of Write_and_database_ops function
Call graph & reversed code of Write_and_database_ops functionJumping back to “write_stage_1_payload_and_bitmap_ops” function and getting out of it & moving into “OneDrive_and_stage_1_paylaod_ops” function, in the end of this module heap is being freed.
Now let’s look into how “Bluelight” malware communicate with and make all requests to command and control server (C&C/C2).
For communicating with the communicate with C2 server “Bluelight” malware make of data section of “Bluelight” malware. In the data section calls to several functions is being made.
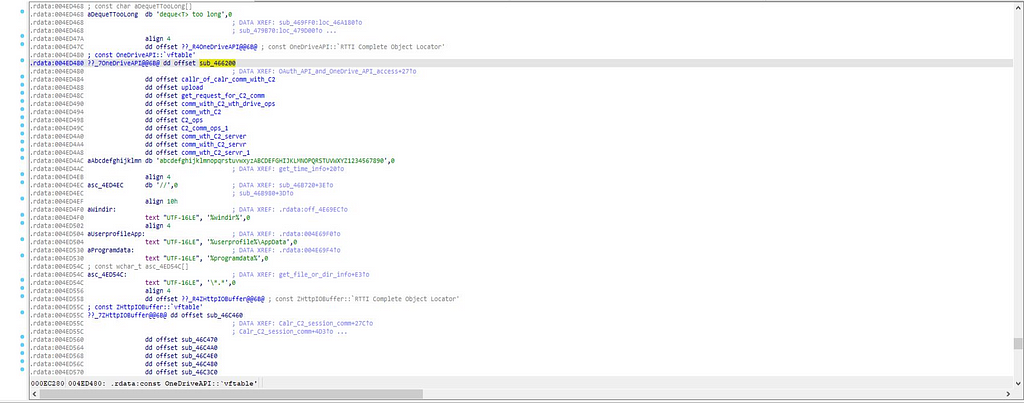 IDA View of .rdata ( data ) section of Bluelight malware.
IDA View of .rdata ( data ) section of Bluelight malware.First function which is being called is “callr_of_calr_comm_with_C2” in .rdata section after offset “sub_466200”. In this function call to “calr_C2_session_comm” is being made.
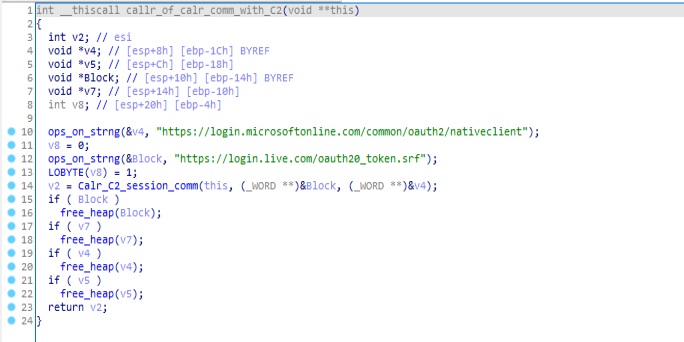 Pseudo-code of callr_of_calr_comm_with_C2 function.
Pseudo-code of callr_of_calr_comm_with_C2 function.And in which call to a POST request is being made to communicate with C2 server using “comm_with_C2” module called in the .rdata section after the call is being made to “comm_with_C2_wth_drive_ops” function. In this module call to “C2_comm_session” is being made.
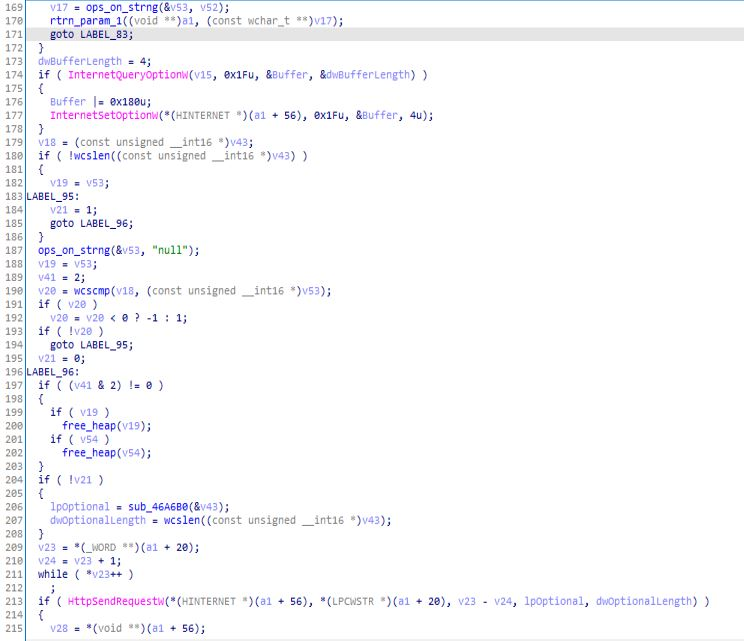
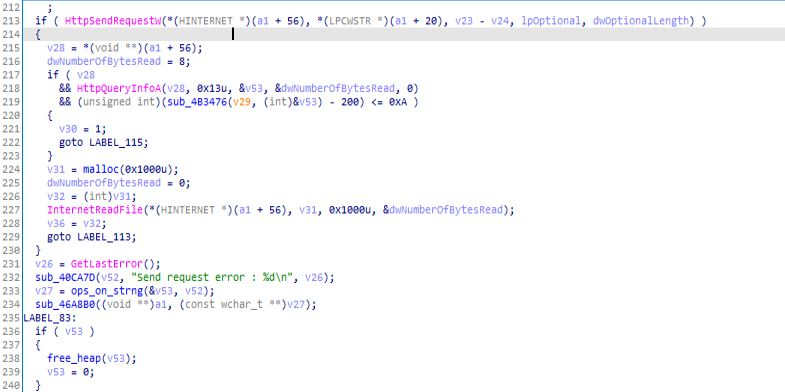 Pseudo-code of comm_with_C2 function.
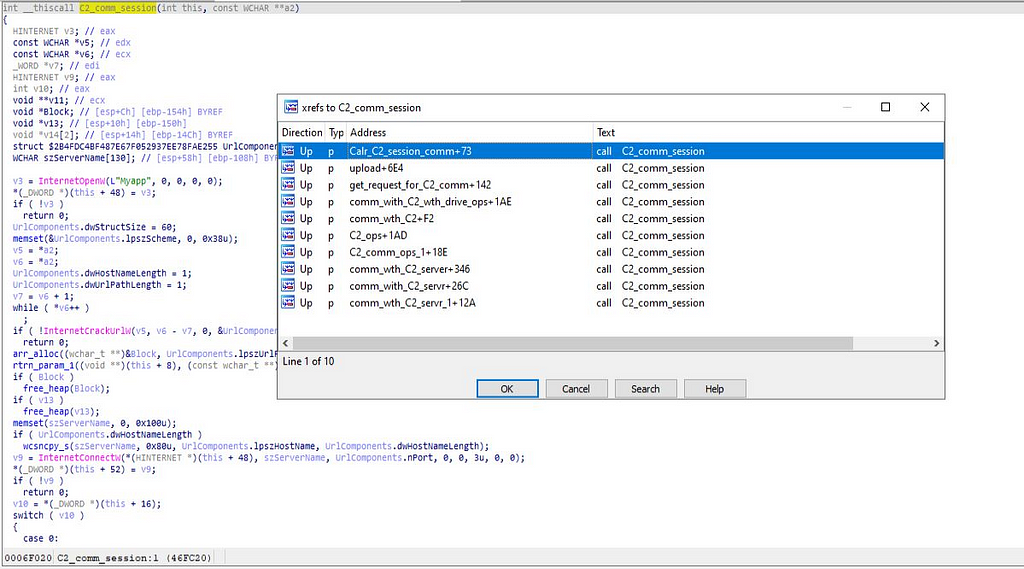
Pseudo-code of comm_with_C2 function.C2_comm_session function:
As we observe that this function is being accessed in all the function called .rdata section as mentioned earlier in this blog.
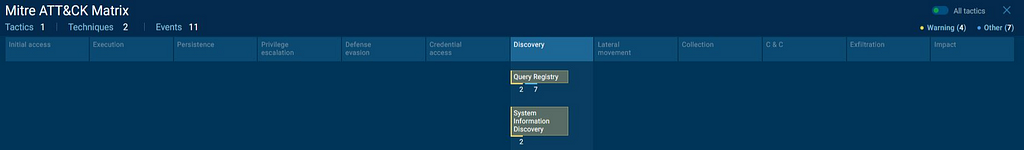
Mapping Mitre Attack Techniques
Query Registry :- T1012 ,
System Information Discovery :- T1082 .
 mapping on Any.Run
mapping on Any.Run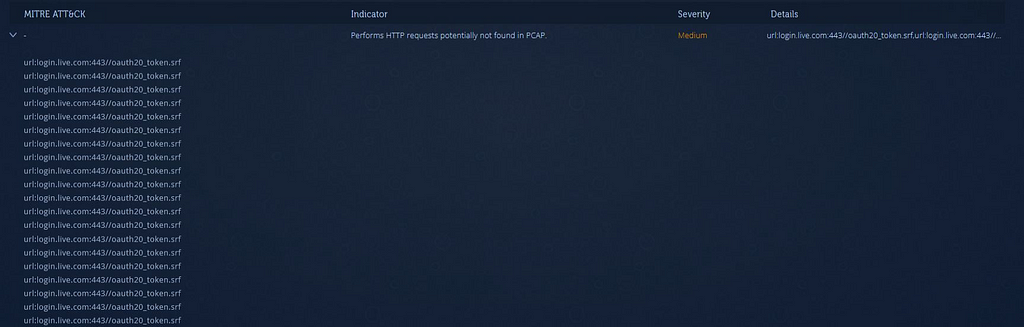 mapping on Analyze Intezer
mapping on Analyze IntezerTracking Network Communication
C2: 20[.]190[.]160[.]136
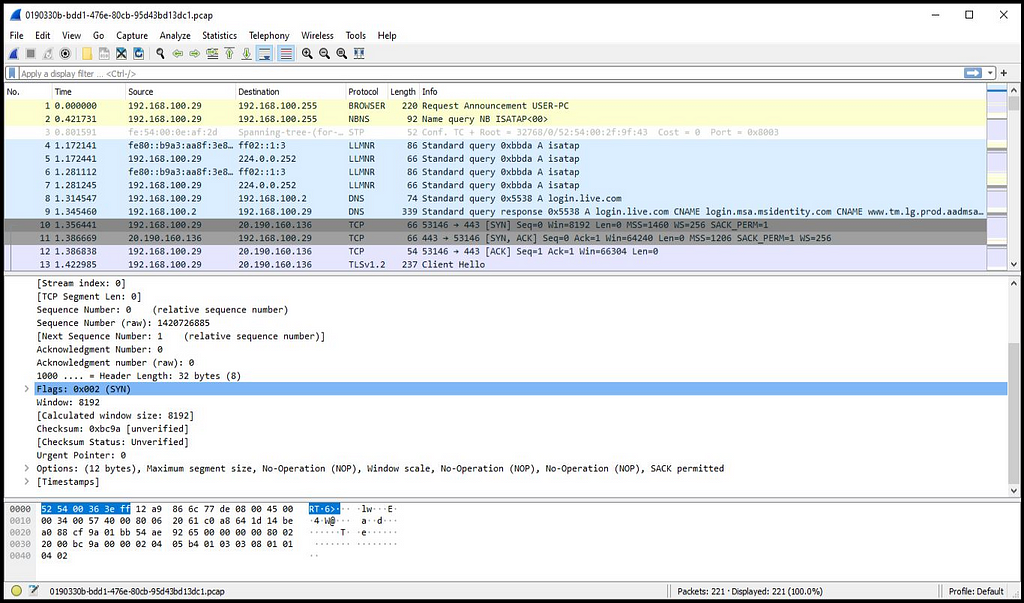 Wireshark View of pcap generated using Any.Run
Wireshark View of pcap generated using Any.RunIOCs & Sandbox Detentions
md5:0b649bc5dbbf21801c21aaa5e5f79fc6
sha: c644e8d446bb6bbcd4696d6a19d009b522258c9e
sha256: 7c40019c1d4cef2ffdd1dd8f388aaba537440b1bffee41789c900122d075a86d
ip4 IP: 20[.]190[.]160[.]136
https://www.virustotal.com/gui/file/7c40019c1d4cef2ffdd1dd8f388aaba537440b1bffee41789c900122d075a86d
https://analyze.intezer.com/analyses/000eb65e-1724-4133-b05a-e3d8cf68f113
https://app.any.run/tasks/0190330b-bdd1-476e-80cb-95d43bd13dc1#
References
- APT37
- APT37 (Reaper): The Overlooked North Korean Actor
- North Korean APT InkySquid Infects Victims Using Browser Exploits
Sample from Report: https://bazaar.abuse.ch/sample/7c40019c1d4cef2ffdd1dd8f388aaba537440b1bffee41789c900122d075a86d/
 Peace
PeaceThanks for reading and giving your precious time for my research.
Love South Korea.
Article Link: https://0xthreatintel.medium.com/static-analysis-of-bluelight-malware-7bb0a399a54e?source=rss-74fc42f1684f------2