Static and Dynamic Analysis.

Analysis of “PDF Reader Upgrade” App

Static Analysis:-
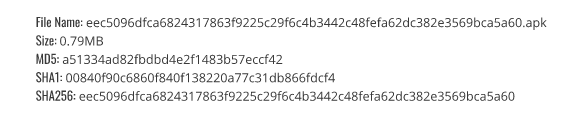
Hash’s:
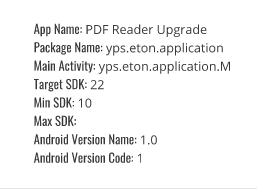
Information About App:

 info. of App.
info. of App.Certificate Info:
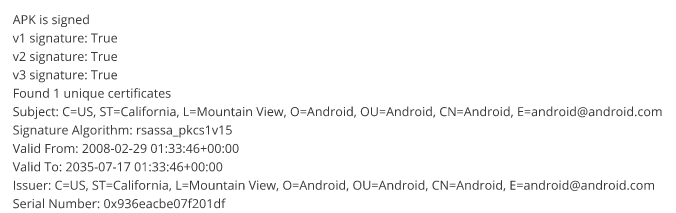 Certificate is signed with the v1 signature schema which makes it vulnerable to Janus vulnerability.
Certificate is signed with the v1 signature schema which makes it vulnerable to Janus vulnerability.App Permissions:
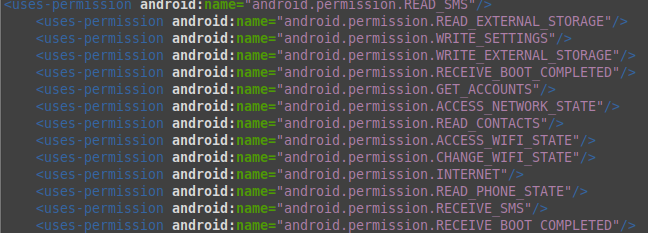 In image we can see app has access to many malicious permissions.
In image we can see app has access to many malicious permissions.Obfuscation and Anti-VM Code:
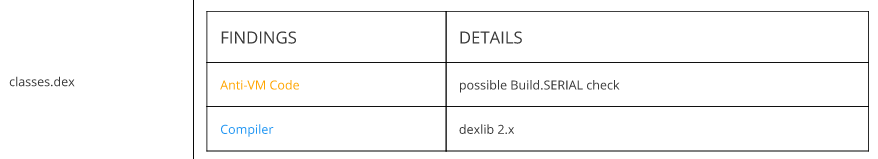
Code Analysis:
App logs into the sensitive information of user which should never be logged.It also has ability to read and write into the external storage.
Activites
Services:
Android API used:

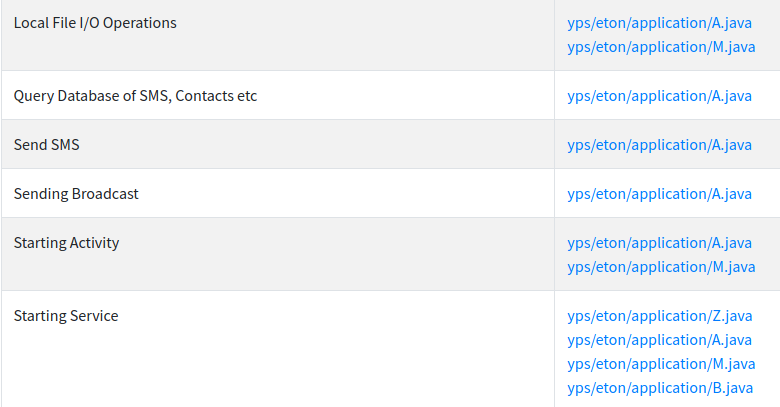
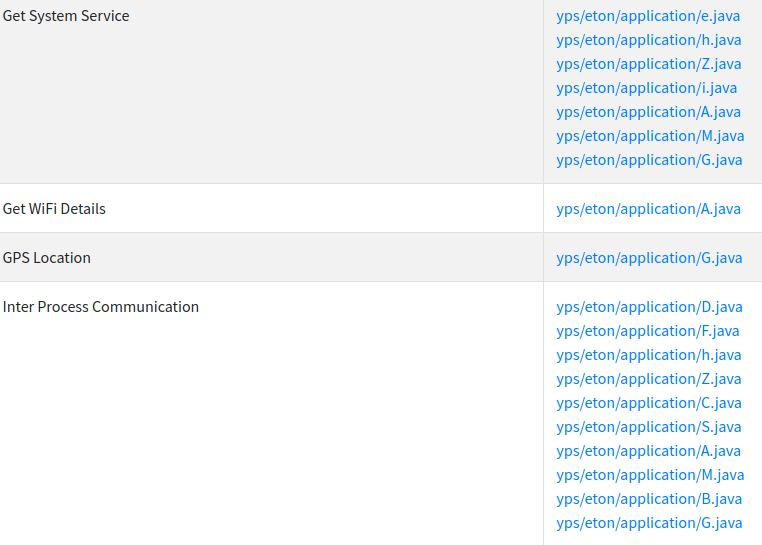
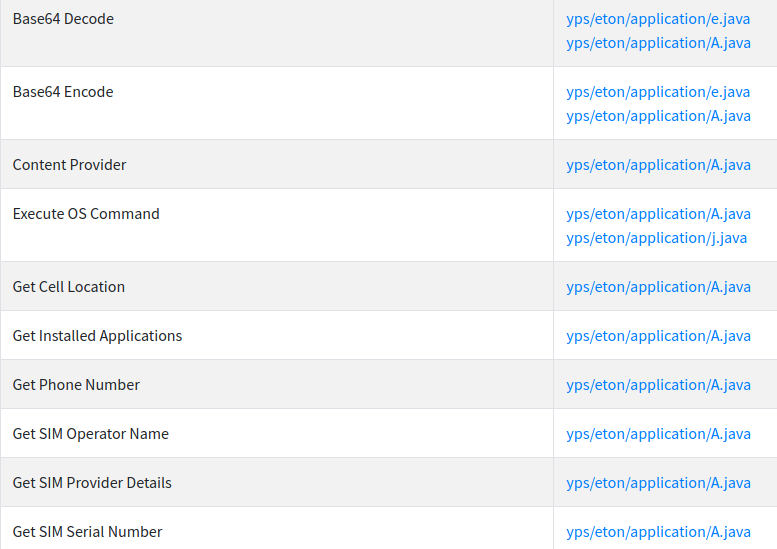 These are API’s used by this malicious app.
These are API’s used by this malicious app.Dynamic Analysis:-
Running app dynamically on emulator [ android VM ] . App for sometime the App crashes.
 screenshot of running app dynamically in emulator.
screenshot of running app dynamically in emulator.Domains:
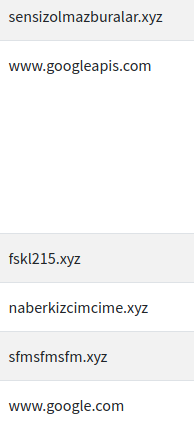
Urls:

Emails:
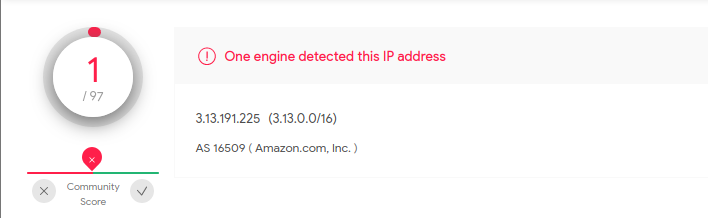
C2 server:-
3[.]13[.]191[.]225
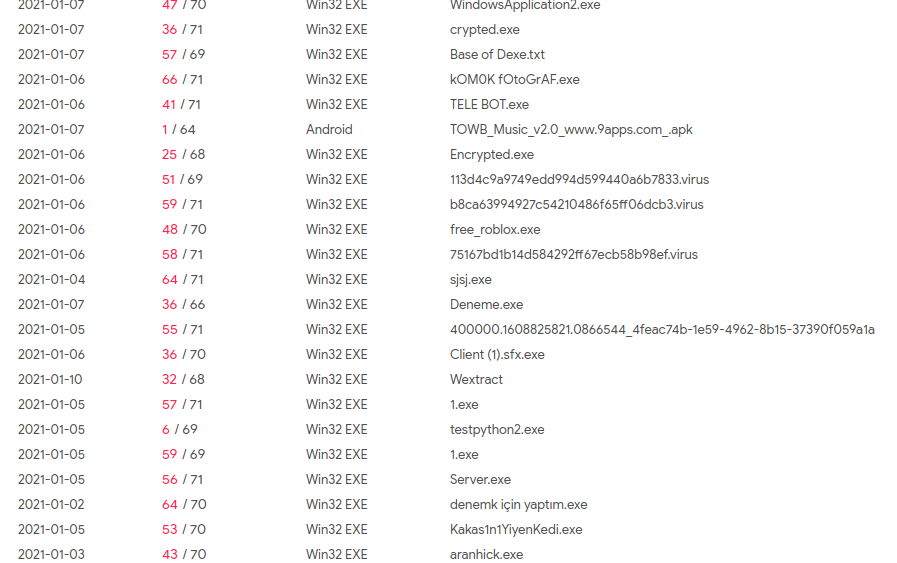
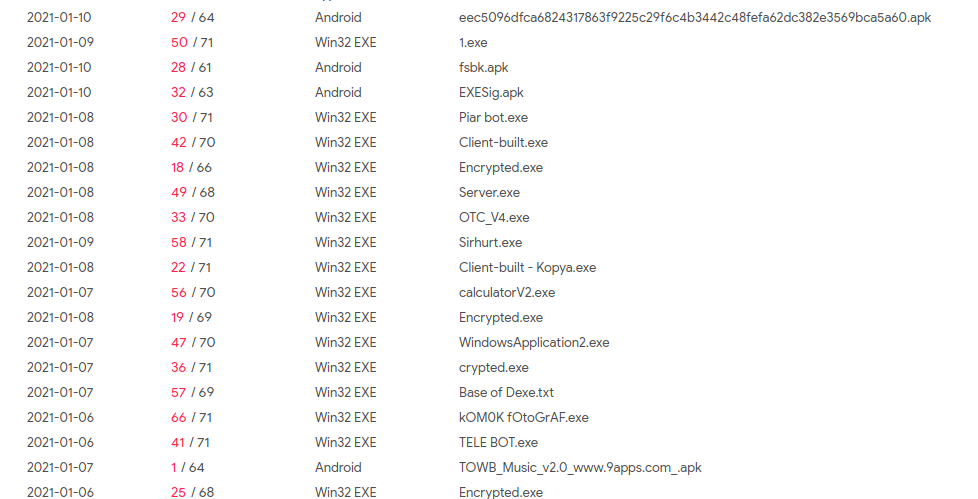
Communicating Files with C2:-
Conclusion
Spynote malware is been active recently on Google Play Store with the signed valid signatures which makes its harder to detect and millions of such apps are being available with such similar configurations.
That’s all for today.
Article Link: https://medium.com/@0xthreatintel/spynote-malware-internals-25acc21ce10d?source=rss-a15183055fd6------2