Our home city Barcelona hosted BSides last week, where the information security community across Europe gathered discuss the current security landscape. Members of our Labs team were invited to present research into FormBook, one of the most notorious info-stealers or form-grabbers in recent years.
The fight against cybercrime is a collaborative effort, and events like BSides enable researchers from teams of all sizes to get together to share and exchange knowledge. The following post develops the content of Borja Rodriguez and Victor Acin’s presentation: Selling FormBook.
Understanding FormBook
FormBook is malware which emerged around 2016, developed in C/ASM. Its main objective is to steal personal information from its victims, performing tasks as a formgrabber (stealing forms sent by browsers), keylogger (exfiltrating the keys registered by the victims), and stealer (exfiltrating credentials extracted from browsers and messaging clients). It is supported by more than 80 applications. Sold in underground forums including HackForums, its creator ng-Coder offers subscription plans as though it were a service. A period subscription offers customers a sample and panel hosted online. As a result of this model and a periodic update cadence, its samples became increasingly widespread over the course of 2018.
Distribution and Campaigns
During the investigation, Blueliv found the execution of several email campaigns for the distribution of FormBook during the first quarter of 2019. To infect its victims, an RTF document was attached to the emails, taking advantage of the vulnerabilities CVE-2017-11882, Microsoft Office Memory Corruption Vulnerability and CVE-2012-0158, Microsoft Windows Common Controls ActiveX Control Remote Code Execution Vulnerability.
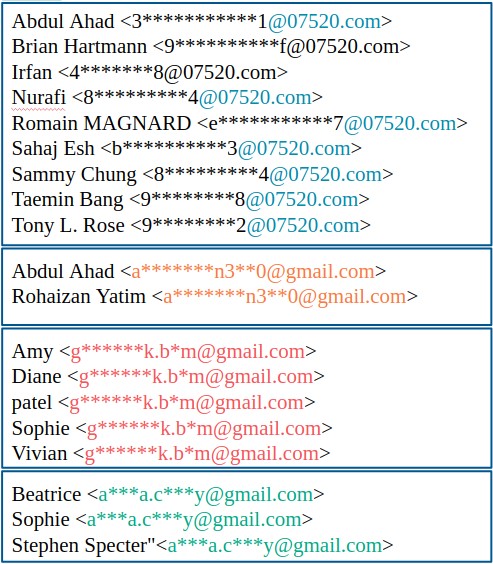
These vulnerabilities allow an attacker to execute arbitrary code remotely (RCE) thanks to a buffer overflow failure in the Microsoft Office Suite. Analyzing the emails, four campaigns were found to be executed from different email accounts, as displayed in the image below. These campaigns were specifically designed to target companies, using emails that try to establish business relationships.
Here we can see the emails and names used as sender in 4 differentiated campaigns.
Malware
The FormBook binary is sold unpacked. This typically translates to finding the sample with a variety of packers (written in different languages in the wild, such as VBS, .NET, C / C ++ and Delphi) when used by serious cybercriminals, making it difficult to unpack automagically, and unpacked, when used by script kiddies.
Another interesting characteristic of FormBook is the extensive use of “anti” measures. The author has included many known, but not-so-common, anti-detection/sandbox/analysis and obfuscation techniques, such as encrypting most of the data used for operation, using dynamic function calling, loading his own copy of NTDLL, checking running processes, checking loaded DLLs and checking for known sandbox paths/usernames, amongst others.
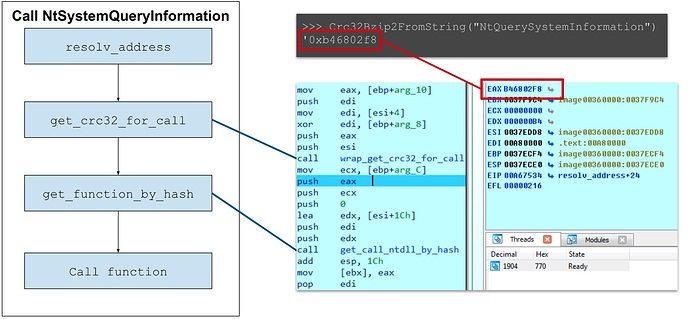
The following image illustrates an example of dynamic function calling, in which FormBook is attempting to invoke NtSystemQueryInformation.
The malware makes dynamic function calls using the hash of the function it wants to invoke.
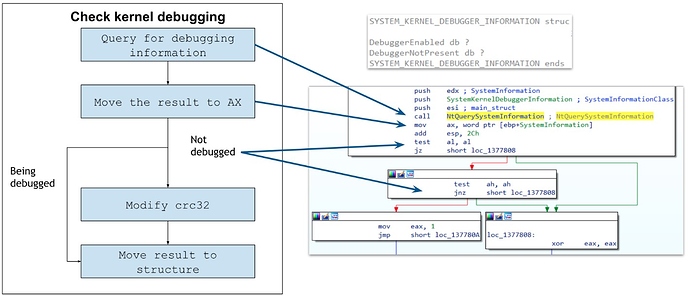
When performing its anti-checks, FormBook modifies the crc32 of some of the calls it will need once it has finished unpacking to crash the sample in the event that an analyst attempts to bypass them. The next image shows how it checks for a kernel debugger using NtQuerySystemInformation.
FormBook checks for kernel debugging using NtQuerySystemInformation with the flag SystemKernelDebuggerInformation.
After passing all checks and migrating to a new process, FormBook gains persistence and infects any running processes supported by its formgrabbing capabilities. FormBook then hooks different APIs for the different applications it targets; some are common APIs (HttpSendRequestA, HttpSendRequestW, WSASend), others very targeted (PR_Write in nss3.dll, which is used by Mozilla products for Windows).
Threat Actor and Sales
The sales of FormBook since its first appearance in 2016 has evolved parallel to versions of the malware itself. ng-Coder, its creator, made his first appearance in Hackforums in October 2015, interested in Assembly, C/C++ and pentesting topics, participating in threads and earning renown selling shellcodes. In February 2016 the sales of version 0.1 of FormBook began, advertised as computer spying software requiring the legal consent of the user. This first version, priced at $120 for the binary and the panel, worked only as a form-grabber for Internet Explorer, Firefox and Chrome.
Post selling FormBook v0.1 in HF
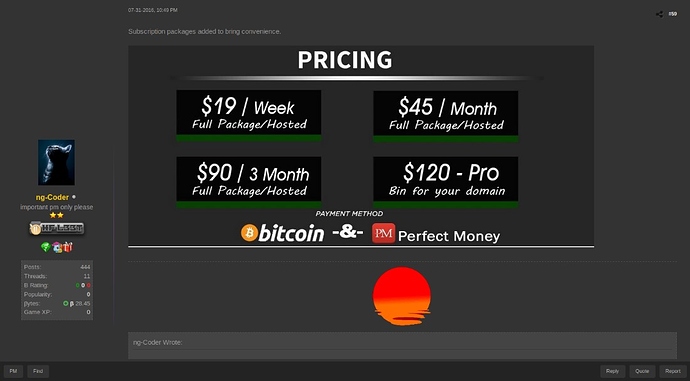
At the beginning of March 2016, a thread was created in Hackforum to sell a version adding new software support and a password recovery feature for browsers and email clients. Two months later, ng-Coder started selling subscription packages – malware-as-a-service – with periodic payment requests in exchange for the binary and an installed and hosted panel.
Pricing of v0.2 with subscription packages
In April 2017 version 0.3 was released, adding many of the features that have made FormBook one of the most prolific pieces of malware in recent years. These include the encryption of the communication with the C2, the FB-Connect functionality allowing the panel to use the bot as a file browser, and the end of 1pc policy, meaning BINs with different account numbers can now co-exist and run on the same computer.
Advertising FormBook v0.3
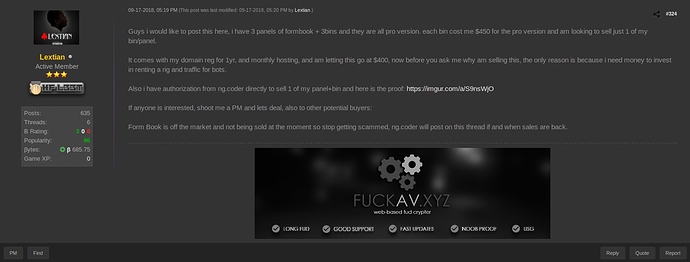
Due to the use of FormBook in email campaigns, ng-Coder stopped selling FormBook openly in the forum. After the sales ceased, some users were scammed by ng-Coder impostors being contacted via Skype. FormBook has begun to be sold in markets and user have appeared claiming to have a cracked version of FormBook builder in other forums. Meanwhile, in Hackforums it appears that users are reselling their subscription packages with the approval of ng-Coder.
User on HF selling subscription packages
Overall FormBook appears to have been coded by an experienced programmer, using clean code, a well-thought execution flow and extensive support for many applications. It uses previously known techniques, but many of these remain fairly uncommon. It also makes use of weak encryption mechanisms and is not packed by default. The malware is still being maintained, but new sales have ceased, suggesting that the subscription model it currently employs is generating enough revenue to be profitable.
The presentation and post were delivered by the Blueliv Labs team.
The post Selling FormBook appeared first on Blueliv.
Article Link: https://www.blueliv.com/blog-news/research/selling-formbook/