the decoy document 74aa6fff407dee851f224329489232a8e7f2d6046aaff3c9cebfff81b7d5db22 uses a version of royal road to drop a new bakdoor developped on MFC C++.
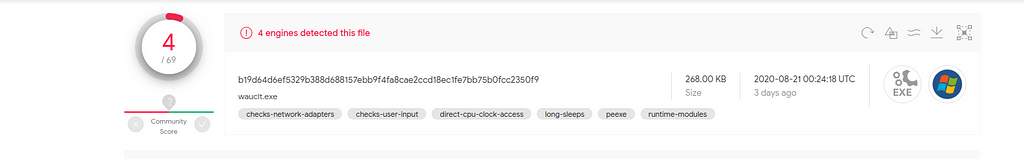
b19d64d6ef5329b388d688157ebb9f4fa8cae2ccd18ec1fe7bb75b0fcc2350f9
The dectection rate on virustotal is very low:
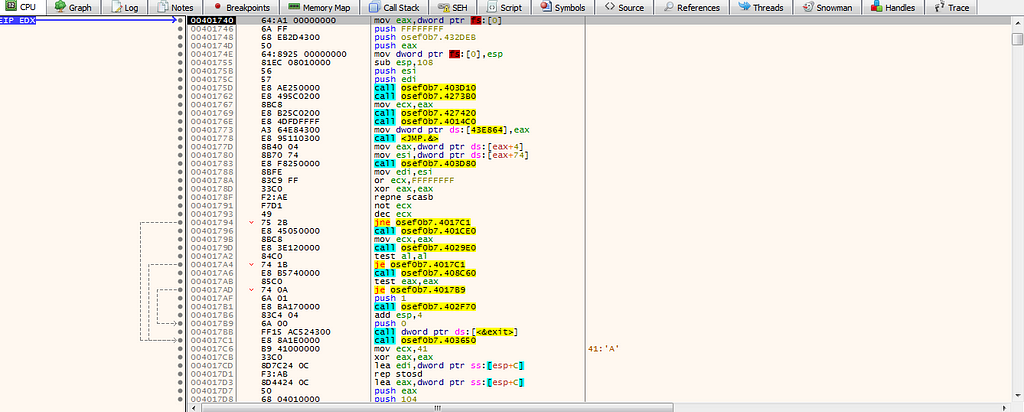
The backdoor is packed with a home made packer. The real entrypoint is call by a thread with the function AfxWinMain at FUN_00432cc8 and the entry of this thread is at 401740.
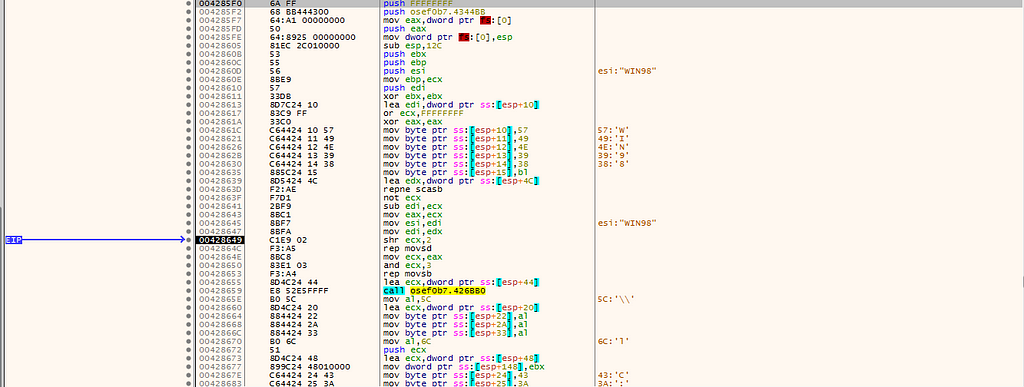
in 004285F0, the backdoor checks the windows version:
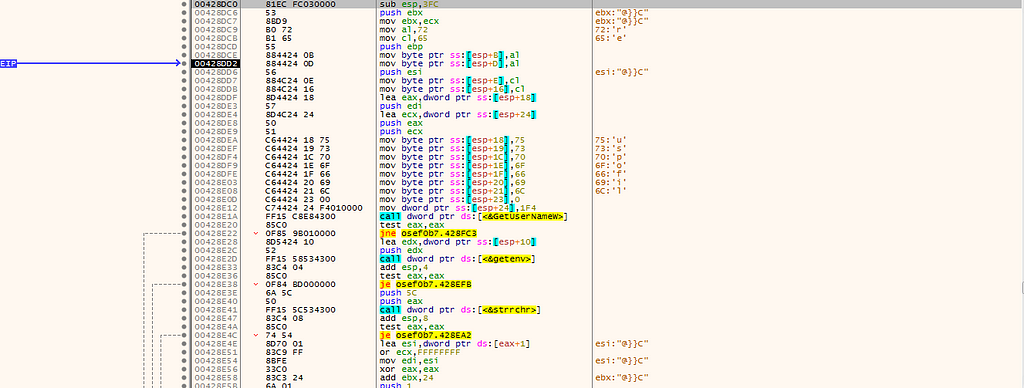
in 00428DC0, it checks the environnement user:
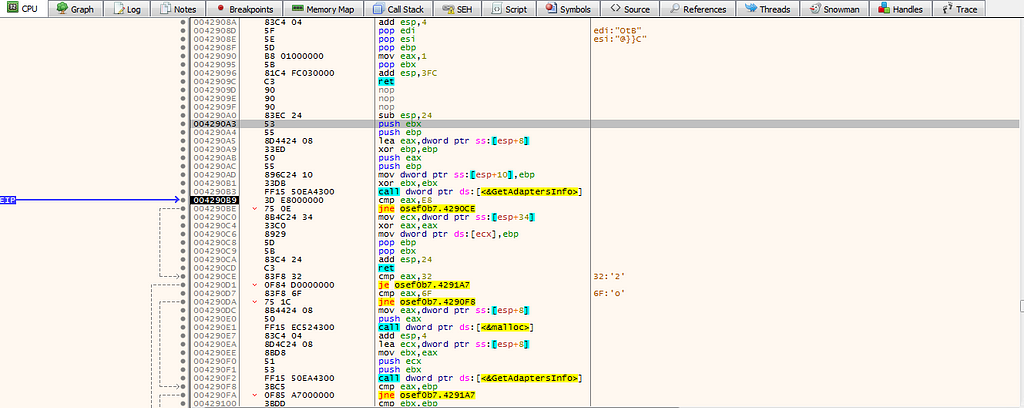
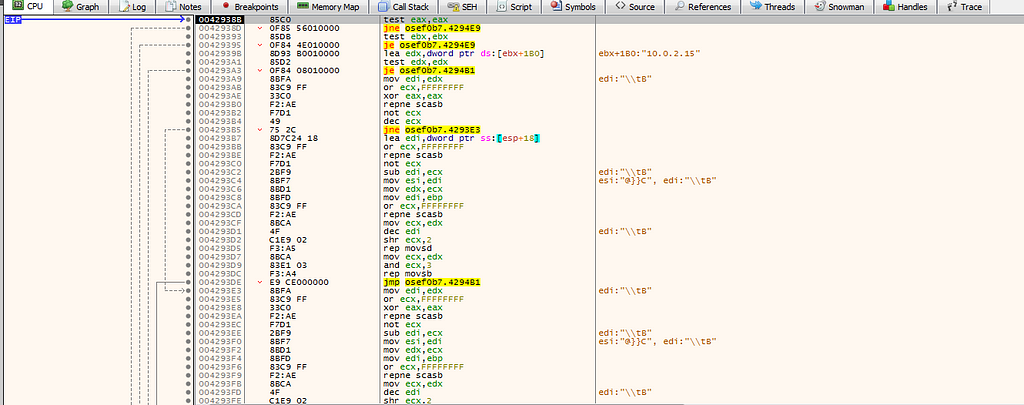
in 004291C0, it check the IP internal and mac address in the sub function: 004290A3
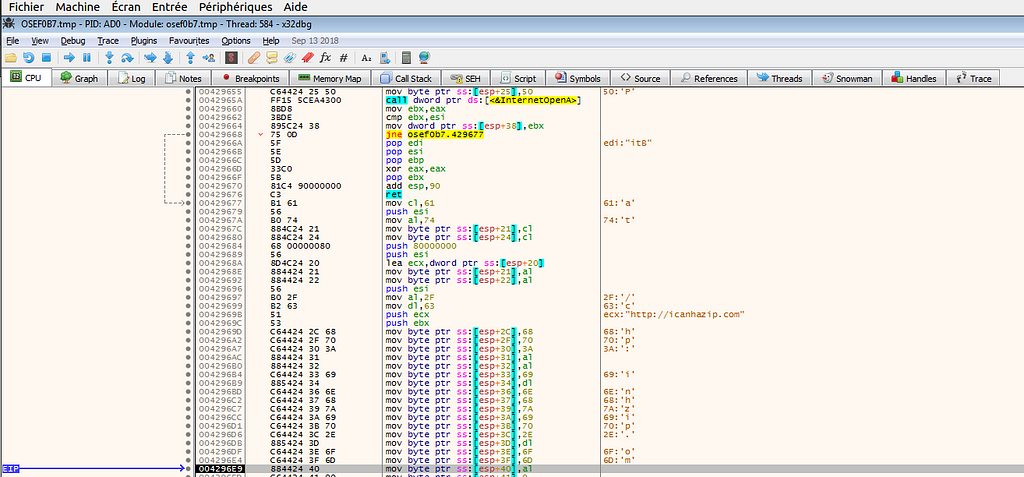
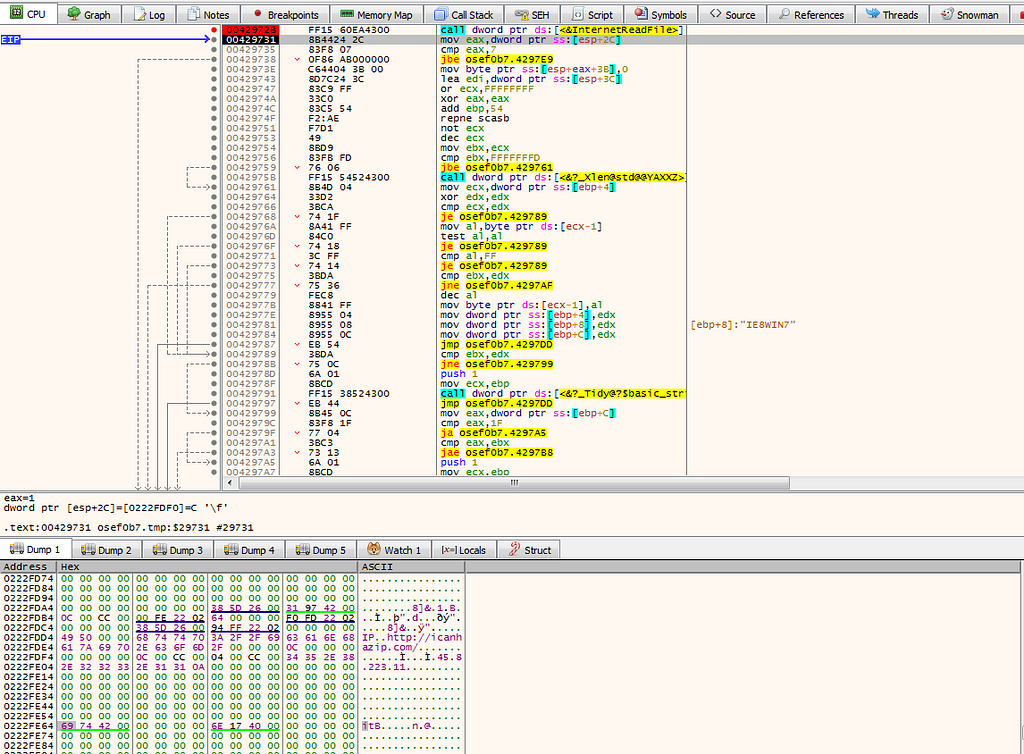
In 00429620, it find the IP external using the service icanhazip.com using InternetOpenUrlA
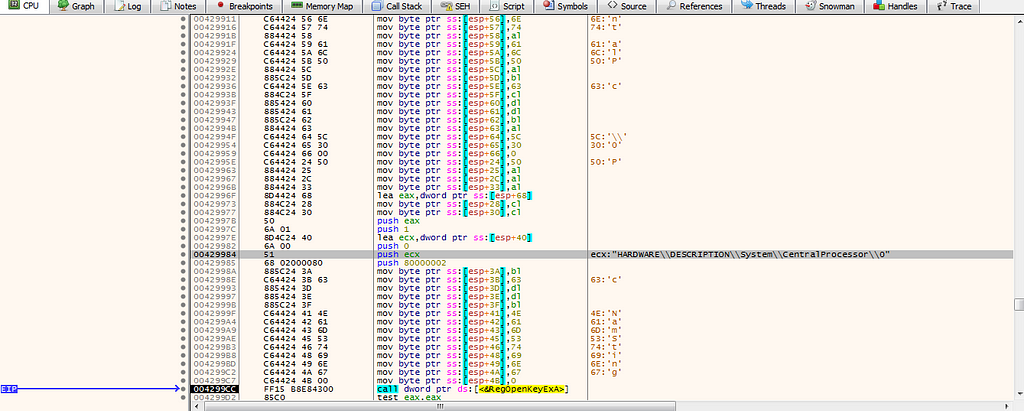
in 00429810, it check the kind of the processor in reading the key: ”HARDWARE\\DESCRIPTION\\System\\CentralProcessor\\0"
in 0042A190, it checks the privilege of the process.
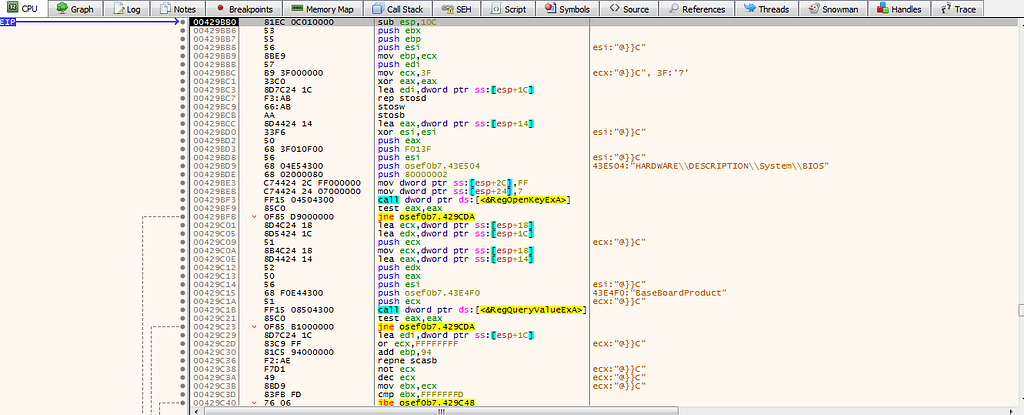
in 00429BB0, it checks the Bios version of the MotherBoard
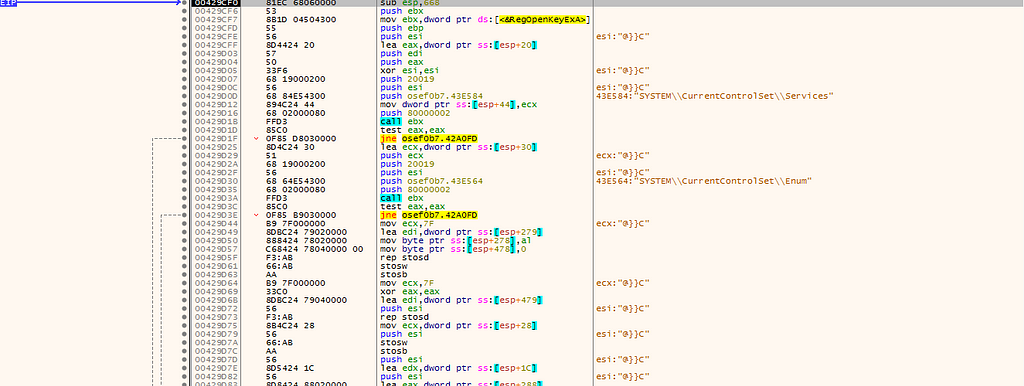
In 00429CF0, it checks the services installed on the computer.
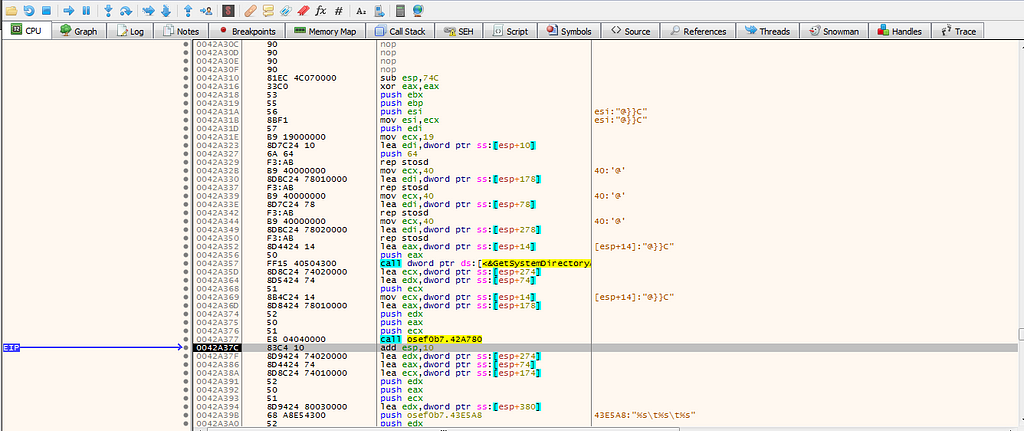
in 0042A310, it checks the harddrives in the subfunction 0042A780.
The results are stored in the stack:
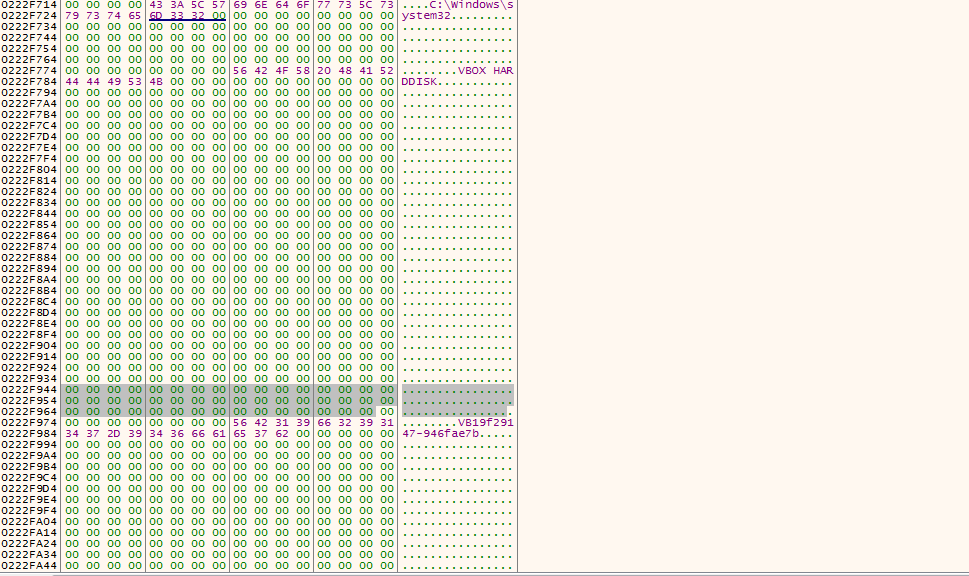
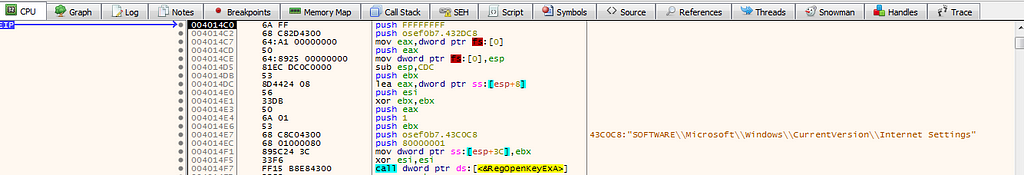
In 004014C0, it check the Internet Settings on the computer:
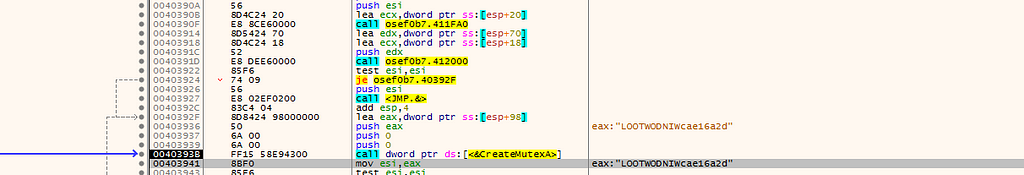
a mutex is created: “LOOTWODNIWcae16a2d”
the malware communicates with the domain: jkncj.com
Threat Intelligence
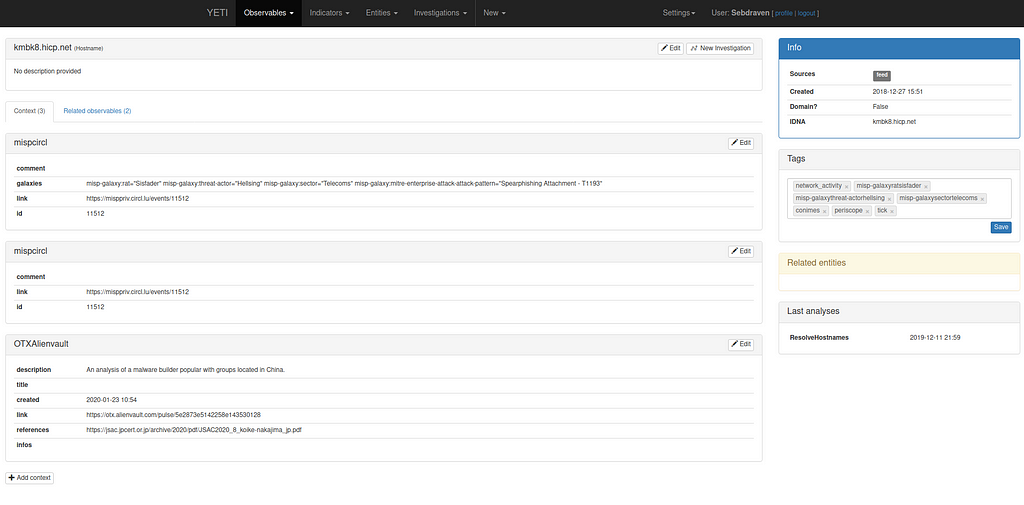
This domain resolves on 91.218.113.17. This IP has resolved on kmbk8.hicp.net
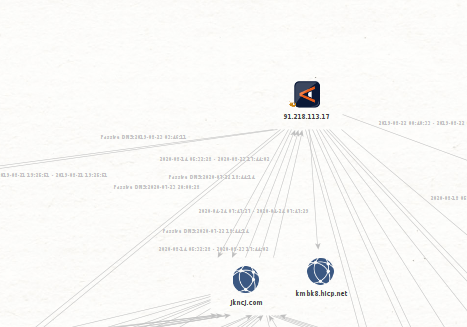
This domain is used during operation by Goblin Panda:
https://jsac.jpcert.or.jp/archive/2020/pdf/JSAC2020_8_koike-nakajima_jp.pdf
IOCs:
RTF Royal Road: 74aa6fff407dee851f224329489232a8e7f2d6046aaff3c9cebfff81b7d5db22
backdoor MFC: C:\Users\admin\AppData\Local\Temp\OSEF0B7.tmp b19d64d6ef5329b388d688157ebb9f4fa8cae2ccd18ec1fe7bb75b0fcc2350f9
jkncj.com
91.218.113.17