Summary:
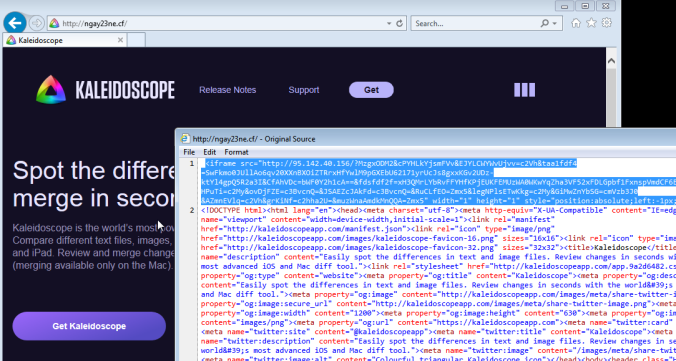
Through malvertising I came across an “Ngay” website which used an iframe to redirect to Rig EK. The payload was Smoke Loader which then dropped a XMR Miner.
I’ve been using App.Any.Run sandbox a lot lately. Although I found the RigEK redirection using traditional methods and the payloads did work on my lab, I put the payload into Any.Run anyway as it portrays the IOC’s very well.
I’ve also been playing with pastebin posts so check that out though it is mainly focused on maldoc malware. https://pastebin.com/u/Zerophage
Background Information:
- An article regarding the integration of Flash exploit CVE-2018-4878
https://malware.dontneedcoffee.com/2018/03/CVE-2018-4878.html - CVE-2018-4878 information https://nvd.nist.gov/vuln/detail/CVE-2018-4878
Downloads
(in password protected zip)
- 22-May-2018-Rig-Smoke-PCAP-> PCAP for traffic
- 22-May-2018-Rig-Smoke-CSV-> IOCs in CSV
- Pastebin – https://pastebin.com/NMLpGFSk
- 22-May-2018-Smoke-XMR-> Smoke Loader and XMR Miner
-
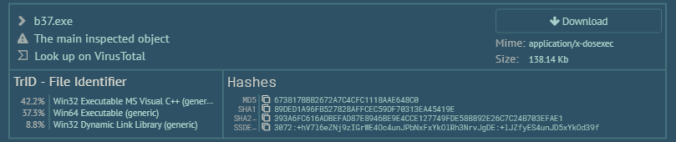
Smoke Loader- “b37.exe”sha256 – 393a6fc616adbefad87e8946be9e4cce127749fde58b892e26c7c24b703efae1 sha1 – 89ded1a96fb527828affcec59df70313ea45419emd5 – 673817bbb2672a7c4cfc1118aae648c0
- Any.Run of the payload -> https://app.any.run/tasks/b7e731ff-bb63-4c35-9d05-9563b0cf3bbc
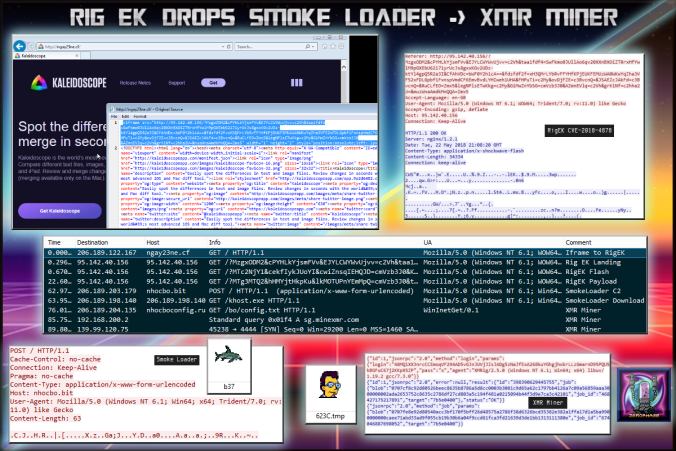
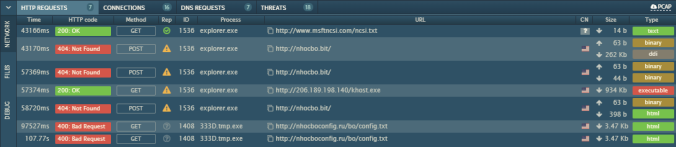
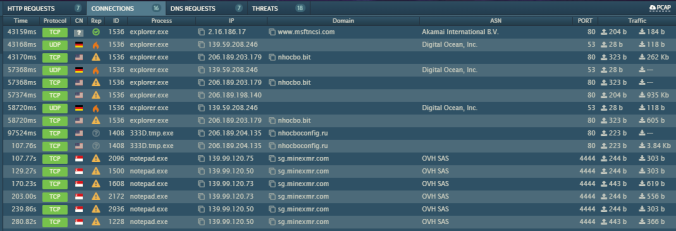
Details of infection chain:
(click to enlarge!)
Full Details:
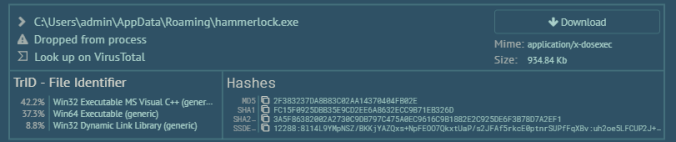
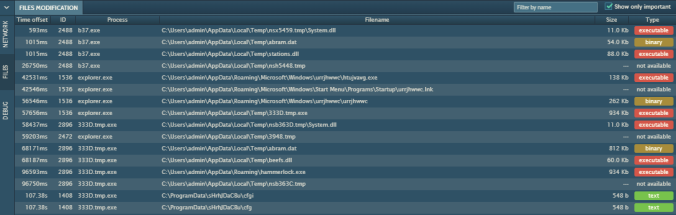
And here are the file modifications. You can see persistence in Startup. The miner is copied into Roaming as “hammerlock.exe”
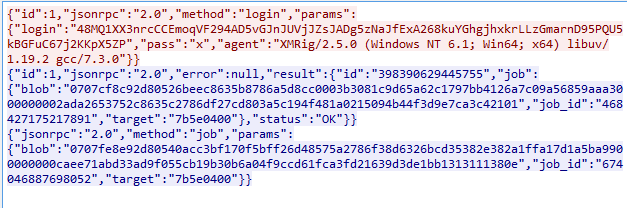
Below we can see the XMR miner communication:
![]()
Article Link: https://zerophagemalware.com/2018/05/22/rig-ek-via-ngay-drops-smokeloader-xmr-miner/