Summary:
This is a quick blog about a Rig EK detection I found on Friday. I had tweeted it out as I could not figure out the payload but I also did not have time to blog it. The community all chipped in and discovered it was a new version of Smoke Loader.
Background Information:
- An article regarding the integration of Flash exploit CVE-2018-4878
https://malware.dontneedcoffee.com/2018/03/CVE-2018-4878.html - CVE-2018-4878 information https://nvd.nist.gov/vuln/detail/CVE-2018-4878
Downloads
(in password protected zip)
- 13-April-2018-Rig-Smoke-> PCAP for traffic
- 13-April-2018-Rig-Smoke-CSV-> IOCs in CSV
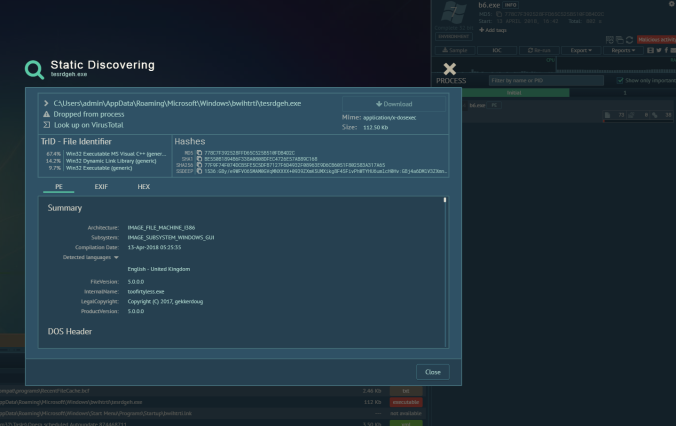
- 13-April-2018-Smoke-Loader -> Smoke Loader
- Smoke Loader hash – 77f9f74f074dcb5fe5c5dfb7127f6d4932f08963e9d6cb6051f802583a317a65
- Any.Run of the payload: https://app.any.run/tasks/60f95e10-7ec8-4592-82cf-273f682541f1
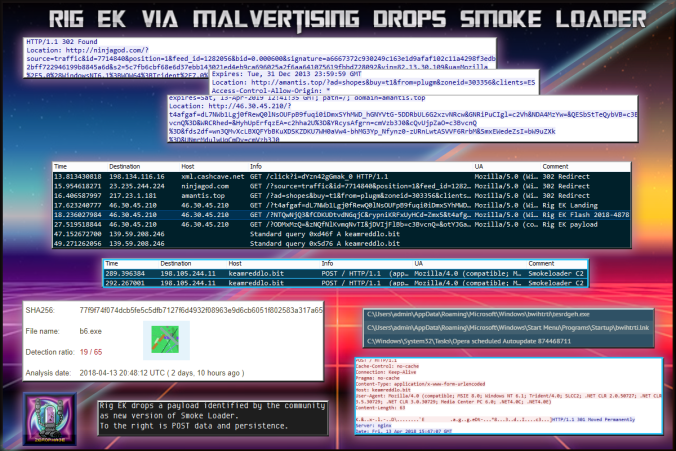
Details of infection chain:
(click to enlarge!)
Full Details:
As you may know, Rig EK is now using the Flash exploit 2018-4878. You can view my previous post to see a few more details about this. Essentially they appear to have just replaced the old flash file with the new one without any major changes.
| SHA256: | 77f9f74f074dcb5fe5c5dfb7127f6d4932f08963e9d6cb6051f802583a317a65 |
| File name: | b6.exe |
| Detection ratio: | 19 / 65 |
| Analysis date: | 2018-04-13 20:48:12 UTC ( 2 days, 10 hours ago ) |
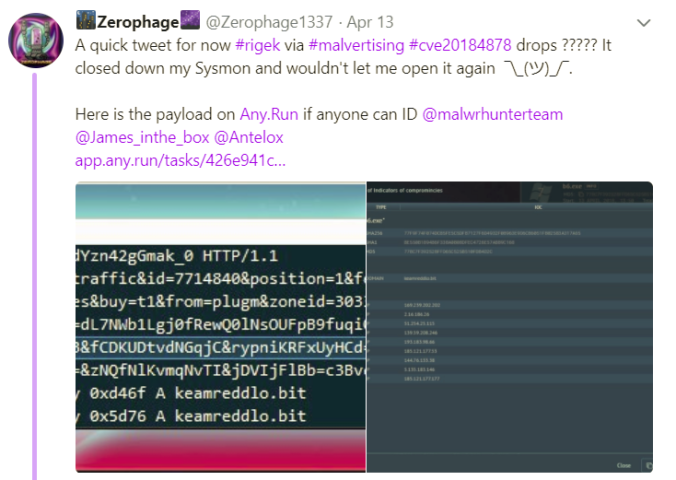
Essentially a number of Twitter users replied to this tweet with some very interesting information about the payload.
![]()
Article Link: https://zerophagemalware.com/2018/04/16/rig-ek-via-malvertising-drops-smoke-loader/