by Ian Mercado
Powload gained notoriety as a catalyst for other malware, a prominent example being Emotet, a banking trojan known for its modular capabilities. Powload has since remained a cybercrime staple due to its ability to combine simple infection methods with constantly evolving features — including capabilities intended for evading security technology.
By sifting through six months’ worth of data (Jan-Jun 2019) covering over 50,000 samples from the Trend Micro


infrastructure, we managed to gain insight into how Powload has incorporated new techniques to increase its effectiveness, especially in its ability to hide from detection. Here’s what we’ve learned.
Powload in the wild
A typical Powload attack uses social engineering techniques to get the user to click on an email attachment — for example, disguising the email as an invoice document supposedly from a supplier. The Powload samples incidents we’ve observed often use attachments that contain a macro coded with Visual Basic for Attachments (VBA), which, when clicked, activates a hidden PowerShell process to download and execute the malware payload. Most Powload variants will often incorporate obfuscation techniques to avoid hash-based detections.
While PowerShell scripts remain the most common method for downloading and executing the malware, the methods for tricking users into clicking the attachments and for hiding traces of the malware from security software are not always the same. We observed some basic techniques that range from using macro-enabled documents as social engineering lures to using hacking tools for obfuscation.
Social engineering techniques
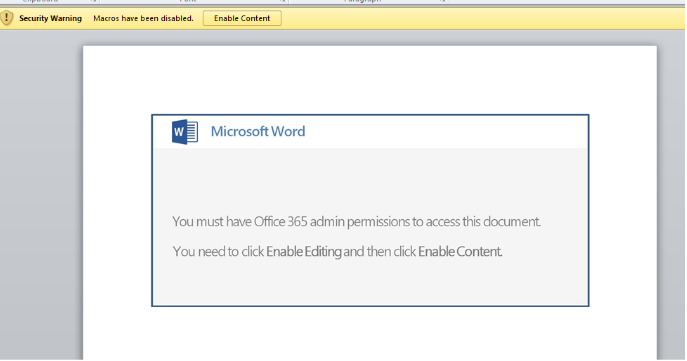
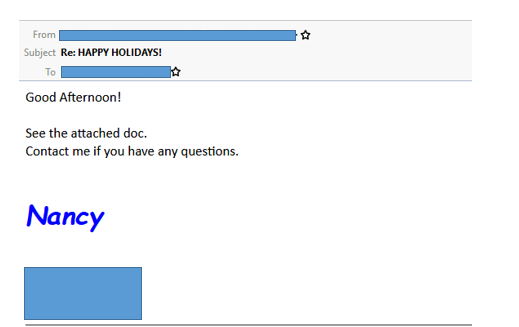
The use of macro-enabled documents as malicious attachments has become increasingly common among malware families, and Powload is no exception – in fact, it is by far the most common method of social engineering used in the attacks. Users who open the document will be prompted with the “Enable Content” button, which, when clicked, causes the malicious macro to be executed.
Figure 1. Example of a macro-enabled document used in Powload attacks. Clicking the “enable content” button will cause the macro to be executed.
Most of the samples we analyzed used files that are compatible with Microsoft Word 97-2003 (denoted by a document with a .doc extension). By setting up the document to disable features that are incompatible with Word 97-2003, attackers can target victims who use older versions of the software.
![]()
Evasion techniques
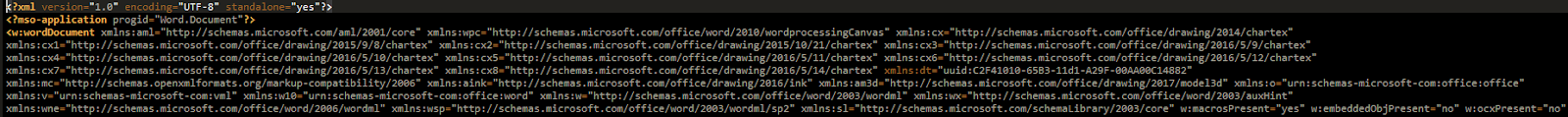
Use of XML-based documents to evade detection. The XML (eXtensible Markup Language) file format is interpreted as a normal document file by Microsoft Word. Some attackers are using it as a malicious attachment to evade structural Microsoft Word Document detections.
Figure 3. Word document MSO-Application that is interpreted as a normal document file
Abuse of the Forms module to hide malicious macro strings. One interesting technique we observed during the past couple of months is the use of unreadable text/ASCII to hide macro strings which are stored in the attribute properties of the Forms module. This is done to avoid structural format detections since no malicious strings will be present in the macro code, with only indirect references to the attribute properties being shown.
Figure 4. Unreadable string stored in the Forms module
Use of password-protected macro modules. Microsoft Office applications contain a privacy protection feature for safeguarding macro source codes. The encoded password uses the variable DPB, which can be viewed by using a hex editor. However, this feature can pose as a double-edged sword when cybercriminals abuse the feature by allowing only users who have the password from accessing the source code, preventing researchers from analyzing if the document is malicious in nature.
Note: According to Microsoft’s documentation, VBA project files that don’t use a password have the following hex values for the DPB variable:“DPB=”0E0CD1ECDFF4E7F5E7F5E7”.
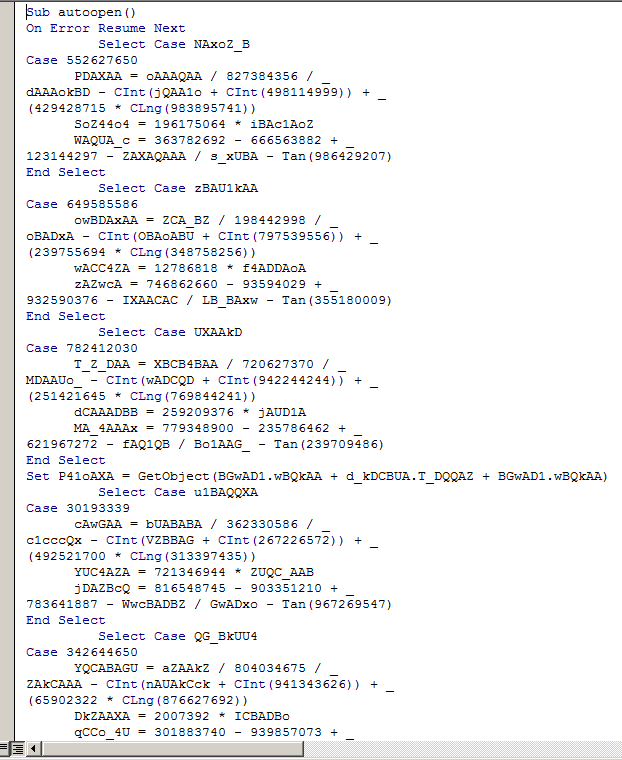
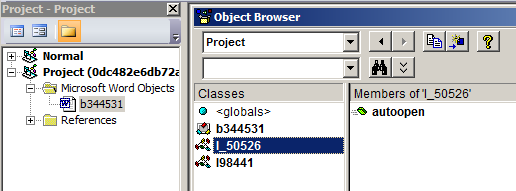
Possible use of hidden VBA project modules. We also found signs of the possible use of a hacking tool named EVILCLIPPY — named after the now defunct Word assistant — which contains a function that allows it to hide the modules of a VBA project. This makes it more difficult for security researchers to reverse engineer a sample. Although there is no hard evidence that EVILCLIPPY was used, many samples had hidden modules, making it likely this or another similar software was used for the attack.
Keeping up with Powload’s continuous evolution
During the whole period in which we observed Powload’s activities, the techniques used were constantly changing — from minor modifications like changing the titles and styles of the malicious emails to building up a wide array of obfuscation techniques over time. Not all the techniques were used at the same time either. For example, the use of hidden VBA project modules was not present during the first months of the year but was added in the past few months — an indication that it is possibly a new strategy that was only recently implemented by the cybercriminals behind the attacks.
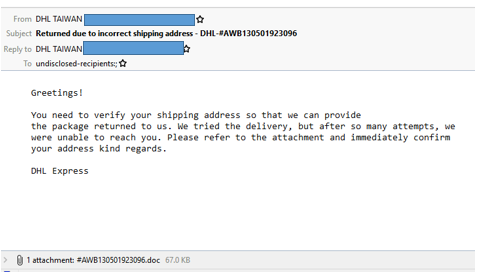
Figures 6 and 7. Emails samples that delivered Powload attachments. The first email has a more professional tone, while the second one is more informal.
Based on what we know and have observed about Powload, it is likely that we will see further improvements to the already constantly evolving malware. Given its role as a downloader for other malware families, we can expect it to remain prominent in the cybercrime scene.
Social engineering remains Powload’s main method of tricking users into downloading it into their machines. That’s why strategies designed to deal with the trojan necessarily includes strategies for combating social engineering as well. To help defend against threats like Powload that use email-based attacks, we recommend that users follow these best practices:
- Check for errors in the email text. Organizations take great pains to make their business correspondence look as professional as possible. If an email contains many grammatical or typographical errors, it might be a sign of an email-based attack.
- Consider the context of the message. It doesn’t make sense for a business that deals in financial matters to receive an invoice for construction supplies. Always verify if the message makes sense for current business dealings.
- Ensure the authenticity of the sender.Check the email address of the sender to see if it matches the ones used by the organization.
- Avoid clicking unfamiliar links or downloading unverified attachments.Many cybercriminals now try to make their emails as convincing as possible to trick even the most careful recipients. Therefore, exercise prudence and avoid clicking links or downloading attachments unless absolutely certain that they are legitimate.
The following Trend Micro solutions can help protect organizations by blocking malicious documents and scripts and preventing access to suspicious domains: Trend Micro
Security

Business Security.
MITRE ATT&CK Techniques
| Tactic | Technique | ID | Description |
| Initial Access | Spear-phishing Attachment | T1193 | Spear-phishing attack that uses malware attached to an email |
| Execution
|
PowerShell | T1086 | Used as the main executor for the embedded malicious code |
| User Execution | T1204 | Attempts to get users to click on the malicious attachment | |
| Defense Evasion
|
Hidden Window | T1143 | Used to execute Powload’s behavior in the background |
| Binary Padding | T1009 | Used to change the file hash to avoid hash-based blacklists |
The post Powload Loads Up on Evasion Techniques appeared first on .
![]()
Article Link: http://feeds.trendmicro.com/~r/Anti-MalwareBlog/~3/XakqNf7Zl1E/