Distributed Denial of Service (DDoS) attacks are more varied than the mega-sized DDoS attacks that you hear about on the evening news. Unfortunately, DDoS attacks are quite common and affect ISPs, Hosters, and Enterprises daily. DDoS attacks range from nearly a Terabyte per second (Tbps) to as small as a handful of packets. While you might be wondering why the broad range of attack sizes and doubt the effectiveness of a few packets, let’s look back and review what is a DDoS attack. DDoS attacks are attacks that deny the availability of a service, such as Internet connectivity, a network device from performing its function, or even an application from functioning normally. These attacks can target a service anywhere, from a hosted website to an organization’s data center, to a cloud service provider’s service, to an Internet Service Provider’s infrastructure (ISP).
All DDoS attacks, or DDoS attack vectors, belong to one of three DDoS attack types (with Attack Category breakout percentage for Enterprises, Governments, and Educational institutions as reported by Arbor Networks’ Worldwide Infrastructure Security Report (WISR), 12 edition) which are:
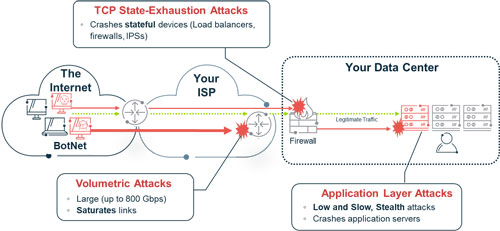
- Volumetric Attacks (60%) – target network bandwidth or network connections, such as a company’s Internet connection to their ISP and saturate that link or port with garbage network traffic. While some of these have been as big as 800 Gbps, they only need to as large as the aggregate bandwidth of the network connection being targeted to be effective. Examples of attacks include botnet or source spoofed IPs, such as in a reflection/amplification attack, where large bits per second (bps) and high packets per second (pps) rates of traffic are generated to consume the available bandwidth for the targeted connection, router, switch, or server. Often these attacks exceed the target’s size and cause collateral damage enroute, as the distributed attack traffic is closing in on the target.
- TCP State-Exhaustion Attacks (19%) – target the stateful nature of TCP protocols, by either consuming all TCP listener sockets or all available memory for stored states. Commonly targeted devices include firewalls, IPSs, load balancers and servers, which are all vulnerable to these attacks. Nearly half of all companies had firewalls or IPSs failed or contributed to an outage during an attack, according to Arbor’s WISR report. Examples of attack types include SYN, FIN, and RST floods, which are much smaller than volumetric but are enough to consume the device’s available sockets or memory.
- Application Layer Attacks (also known as Layer 7 attacks) (25%) – target vulnerabilities in applications, including limitations, scale, functionality, or bugs. These attacks can be the hardest to detect since they are low and slow, which makes them stealthy. These attacks launched from a single machine sending a very small number of packets at a slow rate over time. Examples of attacks include HTTP GET / POST, SIP Invite floods, ApacheKiller, Slowloris, SlowPOST, RUDY, refref, has collision, and many more.
While each of these types of attacks can be devastating in their own right, the truly disturbing DDoS attacks are those that orchestrate multiple vectors together for a more brutally effective attack. 40% of Enterprises, Governments, and Educational institutions saw multi-vector DDoS attacks in the past year, similar to 2015, as noted in Arbor’s WISR report. Attacks, or some portions of attacks, being mitigated upstream may explain why the 11% increase in multi-vector attacks observed by service providers, up to 67% is not seen by their customers downstream.
So the next time you find yourself thinking about threats to your network, infrastructure, devices, servers, applications, cloud services, or anything network with value to your organization – ask yourself “what would happen if it was not available to its users?” If the answer is not nice, then first review the tools that you may have in your organization that could be used to detect one of these types of attacks and how would you mitigate each. Pre-planning goes a long way in the defense of your organization.
Visit our site to learn more about what you can do to protect your organization against DDoS attacks.
The post Not All DDoS Attacks Are Huge Volumetric DDoS Flood Attacks AND Affect more than Layers 3 and 4 appeared first on Arbor Insights - Our people, products and ideas.
Article Link: https://www.arbornetworks.com/blog/insight/not-ddos-attacks-huge-volumetric-ddos-flood-attacks-affect-layers-3-4/