HASH MD5: 88e085572a182ca102676676ec0ef802
File Type: Win32 executable
Signature: Microsoft Visual C# v7.0 / Basic .NET
Link to Download Sample: Any.Run
Type: Remote Access Trojan
njRAT is a remote access Trojan. It is one of the most widely accessible RATs. I came across this while going through
Any.Run trends and thought to download sample for analysis.
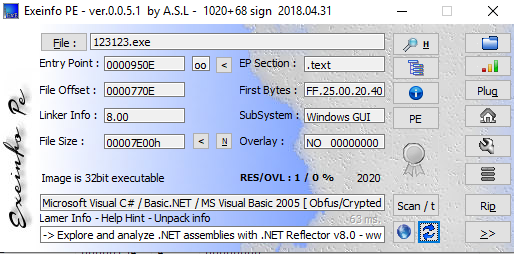 PE file information
PE file informationI have disassembled executable file using dnSpy. It makes easy to analyse the code. Stub shows entry point where I can
put breakpoint to start the debugging to analyse the behavior
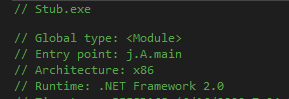 .net version v2.0.50727
.net version v2.0.50727I start debugging and put break point at entry point.
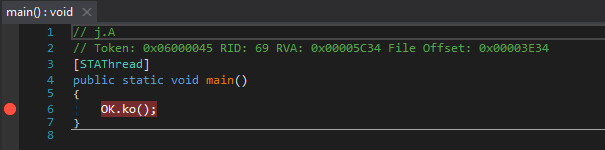 Entry Point
Entry PointKo() function first check the list predefined process running on victim’s machine if they are, the malware executable
will stop execution. In this case, wireshark was running in background. It stops calling assembly and execution process.


To avoid call to CsAntiProcess which look for the running process, I change the value of anti_CH bool variable value to
false manually. (Value of variable can change from Locals windows)
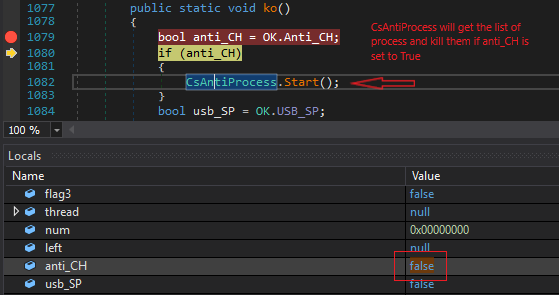
CsAntiProcess handler look for the process and if its there , it stops execution.
 Class CsAntiProcess
Class CsAntiProcessThe list of process mentioned
| SN | Process List | Process Name |
| 1 | procexp | Process Explorer (Sys Internal Tool) |
| 2 | SbieCtrl | SbieCtrl.exe (Sandboxie) |
| 3 | SpyTheSpy | Spyware monitoring tool |
| 4 | wireshak | WireShark |
| 5 | apateDNS | ApteDNS tool |
| 6 | IPBlocker | IPBlocker |
| 7 | Tiger-Firewall | – |
| 8 | smsniff | – |
| 9 | exeinfoPE | Exeinfo PE Tool |
| 10 | NetSnifferCS | – |
| 11 | SandBoxie Control | – |
| 12 | processhacker | Process Hacker |
| 13 | dnSpy | .Net disassembler (I am using it for debugging here) |
| 14 | CodeReflector | – |
| 15 | ILSpy | .Net disassembler |
| 16 | VGAuthService | VMware Guest Authentication Service |
| 17 | VBoxService | Virtual Box Service |
NOTE: To bypass process check, I also changed the names of process e.g. Wireshark.exe to wk.exe and procexp.exe to prex.exe which helped to by pass process check when I executed malware without debugging in dnSpy because process names are hard coded.
On proceed with the debugging, it drops an executable file svchost.exe on the system at location
C:\Users\<user profile>\AppData\Roaming\svchost.exe
 code that drops executable file.
code that drops executable file. EXE is a string variable initialized as svchost.exe. It could be named svchost.exe (Windows Service Host) to create
confusion and it make difficult to differentiate its malicious without analyzing its location and properties.

It also drops Tools.exe at location C:\

 File dropped at location C:\
File dropped at location C:\File also drop at location
C:\USers\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\e84128b2e0547d1dd1f8090d86c80c48
and add to registry HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Name: e84128b2e0547d1dd1f8090d86c80c48
Value data: “C:\Users\IEUser\AppData\Roaming\svchost.exe” ..
Adding this registry value, the executable will execute everytime when user logon to the system.


Dropping file in this case is copying itself to the three different location. As all three files have different names but same hash and code.
In code, IP address along with the port 7777 and executable names are initialized.

C2 Server IP Address details:
- VT Score: 1/79
- Status: Malicious
 VirusTotal Score for C2 server IP address – Link
VirusTotal Score for C2 server IP address – Linksvchost.exe has sent TCP segment with SYN control bits to C2 server but there is no response from the server. Though
the IP address exists and IP location is Russia.
I used netstat to check the tcp connection.
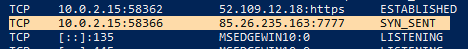 Netstat command >> netstat -a
Netstat command >> netstat -a 1) Command >> netstat -a -b 2) Process name svchost.exe sent TCP segment
1) Command >> netstat -a -b 2) Process name svchost.exe sent TCP segment Summary:
- On execution, malicious executable file check running process on the system.
- If any of the process running (listed in table above), malware stops execution.
- It copies itself to three different locations:
- C:\Tools.exe
- C:\Users\<user profile>\AppData\Roaming\svchost.exe
- C:\USers\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\e84128b2e0547d1dd1f8090d86c80c48.exe
- Creates registry entry so e84128b2e0547d1dd1f8090d86c80c48.exe will execute every time user logon to the system.
- Command and Control server IP address is 85.26. 235.163 port 7777
- svchost.exe tried to connect to C2 server, server didn’t respond.
- Accessing C2 server IP address on port 7777 in browser, gets 200 OK response with empty response header.
Thank you.
Comments and suggestions are welcome.
Article Link: njRAT Malware Analysis – Malware Analysis