Dot "MZP" Ransomware @ AnyRun | VirusTotal | HybridAnalysis
--> sha256 bebf5c12e35029e21c9cca1da53eb43e893f9521435a246ea991bcced2fabe67
This sample was first discovered by AmigoA and AkhmendTaia on the 31st of December 2019. AV Detections and Ransomnote contents didn't seem to match any previously present strain. The Note is delivered via a .txt File with a strange numeric victim ID and only one contact email address. The extension appended to encrypted Files seems to be a random 8 character lowercase string.
New #MZP #Ransomwarehttps://t.co/YCY8NXzJZw
— Amigo-A (@Amigo_A_) December 31, 2019
It seems nothing special, but early AV-detections is uninformative.
Thanks to @AkhmedTaia pic.twitter.com/qS1YapH8jW
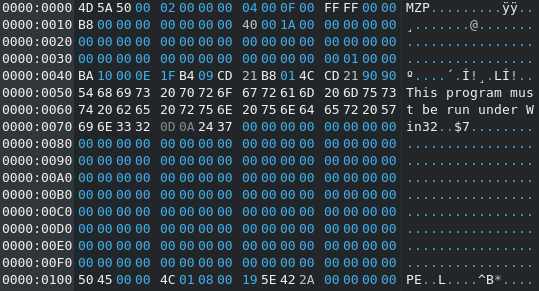
Because of the "MZP" (4D 5A 50) Magic at the beginning of the executable file they dubbed the Malware "MZP" Ransomware. As I explained before with the MZRevenge/MaMo Ransomware the "P" after the MZ Magic String indicates that the binary was built with Borland Delphi and P stands for Pascal (the programming language).
In my Opinion the Name "MZP Ransomware" is to generic to be useful for future reference, so I'd like to propose the name "Dot Ransomware" because of the File Icon found with the Malware Samples. It shows the character "Dot" from the Warner Bros Cartoon Series "Animaniacs" popular in the mid-1990s.
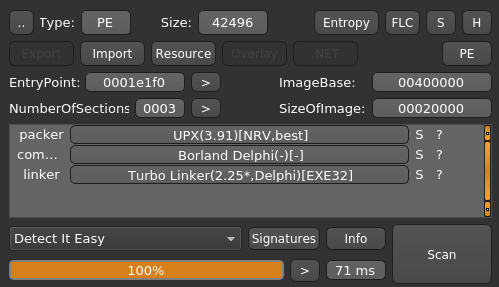
Two things to note about the Output of "Detect it easy" for this sample:
-
It confirms that the Ransomware was built with Borland Delphi (Version 4).
-
This sample seems to be packed with UPX 3.91. Running
upx -d 01.exeyields us the unpacked Version. The Hashsums can be found in the IOC Section down below
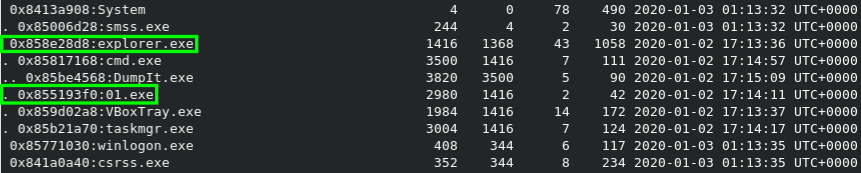
Let's try something new :D Up until now I pretty much neglected memory dump analysis as a whole, but since I attended the Workshop on Volatility at 36c3 I noticed what I'm missing out on. With volatility -f IE9WIN7-20200102-171509.dmp --profile=Win7SP1x86_24000 pstree we can dump the process tree at the time of the capture. We can see that 01.exe is running as a subprocess of explorer.exe.
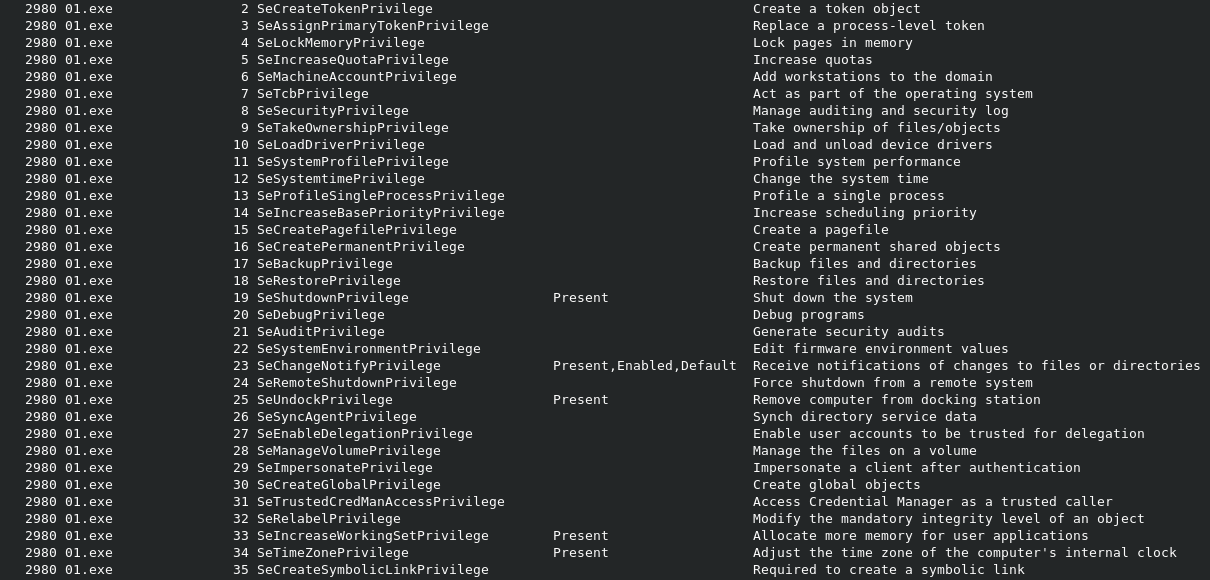
With the privs plugin Volatility can show which process privileges are present, enabled, and/or enabled by default. Below you can see a screencapture of the output for the Ransomware. The Plugins cmdscan and consoles sadly did not return any output for 01.exe.
Let's check out what IDR (Interactive Delphi Reconstructor) can tell us about the binary. First off: Strings.
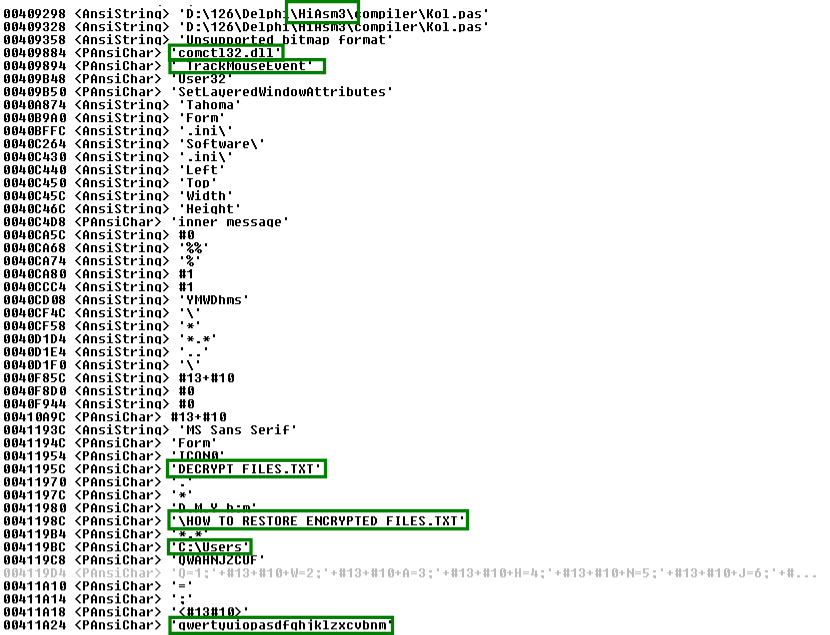
The first String related to the Compiler tells us that the criminals likely used HiASM (an old russian IDE for Delphi Development) to build the Malware. The DLL mentioned below comctl32.dll is often targeted for UAC Bypasses. It also seems to track Mouse events to some extent this could either be used as an evasion mechanism or entropy collection (the first option is a lot more plausible). "HOW TO RESTORE ENCRYPTED FILES.txt" is the filename of the dropped ransomnote, although I'm not sure about the use of "DECRYPT FILES.txt" since this file was not present on any infected system (Speculation: Does is select one out of multiple Filenames to make tracking more difficult?). Lastly we have a filepath and a string that looks like the criminal dragged his face across the keyboard once.
Alright, let's move along. Because Delphi is notoriously weird and difficult to disassemble/decompile it is time to try a new tool again. Today I will be using Ghidra with Dhrake developed by Jesko Hüttenhain. You can find the Git repository below and if you would like to know more about the inner workings of the two scripts you should definitely read his article about them here.
A short tl;dr: Dhrake is short for "Delphi hand rake" and tries to fix missing symbols and borked function signatures by matching to the symbols extracted through IDR beforehand. This will not only clean up the decompilation results in Ghidra but also automatically create structs and virtual method tables for you instead of doing it by hand (as if reversing Delphi wasn't already painfull enough). It's pretty cool, give it a try!
The first step to success (lol who am I kidding) is firing up Ghdira and loading the sample. Tell it to auto-analyze the file.
Next we need to extract the .IDC Symbol file with the Help of IDR. For this it is sufficient to clone the Git Repo and paste the Knowledge Base files from the Dropbox linked at the end of the Readme into it. After that is done just run IDR.exe, import the binary and choose IDC Generator under Tools.
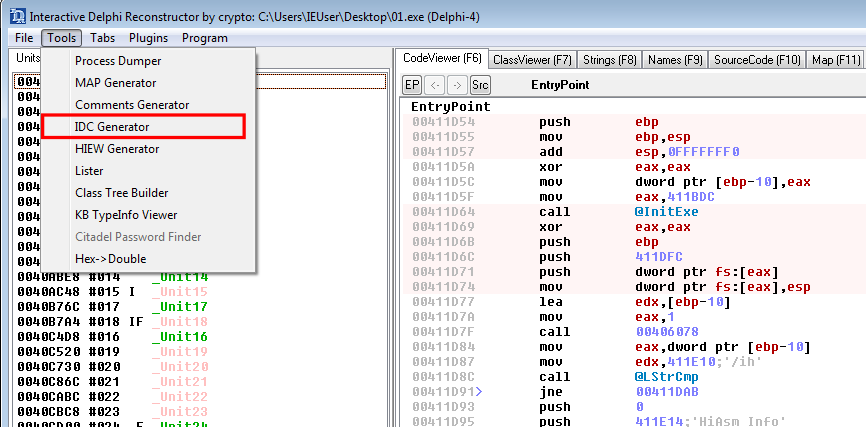
After copying the two Dhrake scripts into your ghidra_scripts folder (e.g. ~/ghidra_scripts) you can refresh the list in the Script Manager once and switch to the Delphi Category. Run DhrakeInit and select the IDC file you created earlier.
Filtering for "VMT" in the Symbol Tree gives you all the Symbols relevant to Dhrake. Just click the Name in the Listing view once and run DhrakeParseClass (set the checkbox "In Tool" and press F8 to run). The Script will now automatically create the corresponding class and vtable struct.

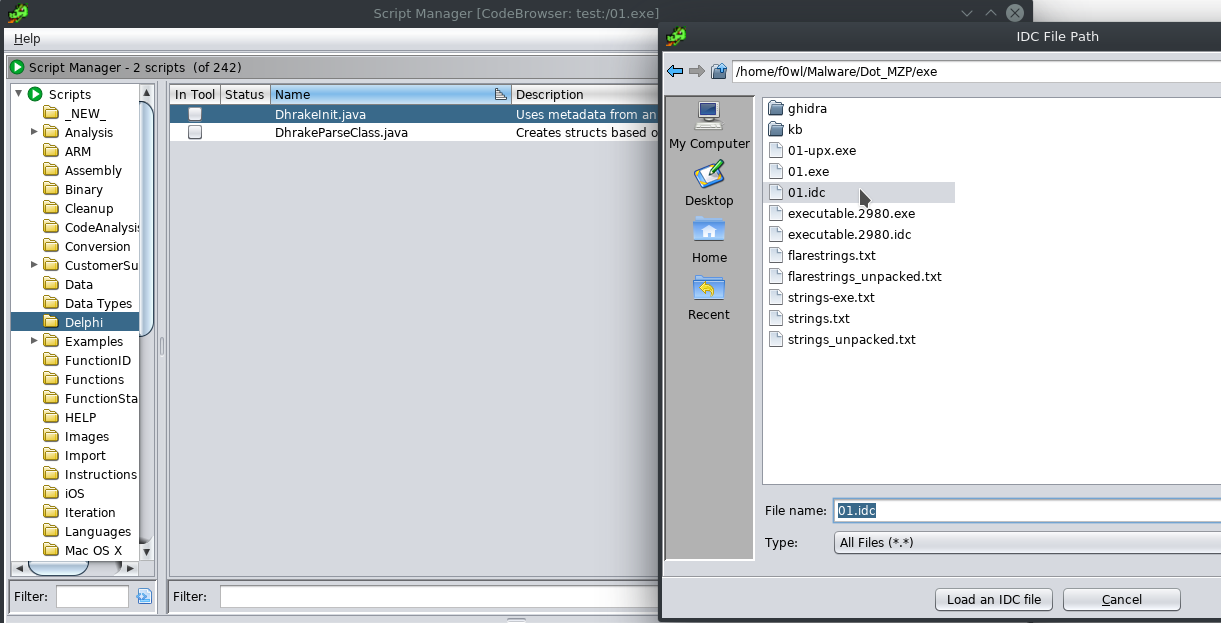
So I guess we should continue with the analysis now :D As 90% of ransomware strains do "Dot" will read the Keyboard Layout as well. GetKeyboardLayout(0) returning 7 would be equivalent to a Japanese Keyboard Layout (wtf?). Passing 1 to GetKeyboardType will return the Subtype which is OEM specific, but will tell you how many function keys there are. Weird. Here's the Documentation.
Dot also queries the current cursor position on the screen and passes it on to another function. Haven't investigated further yet.

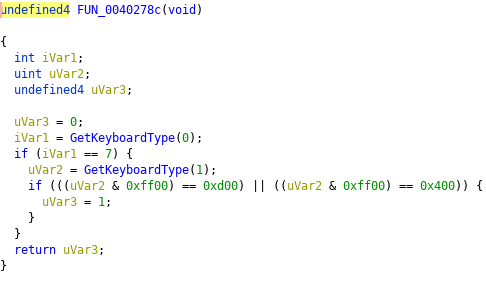
Here we are again: weird DLLs that may or may not be a UAC Bypass. UACme mentions two Methods (#21 and #22) employing comctl32.dll. Unsure what to make of this at the moment.
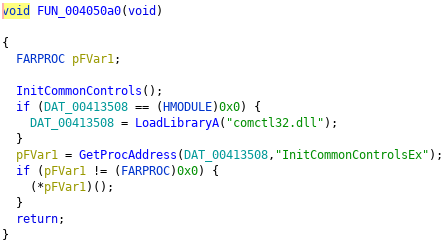
In one of the Szenarios I ran Regshot to see whether the Ransomware adds/modifies/deletes Registry Keys, but there weren't any changes that I can attribute to it. The Screenshot you can see below shows a routine created by Delphi that I don't deem malicious.
This is another work in progress article as I've come down with the "Congress Flu", so check back in a few days for an update. Probably the most important thing this "report" is still missing is a look at the crypto implementation. A look at the Imports reveals that it is not using the Windows Crypto API but rather a weird Delphi one. We'll see.
MITRE ATT&CK
T1107 --> File Deletion --> Defense Evasion
T1045 --> Software Packing --> Defense Evasion
T1012 --> Query Registry --> Discovery
T1076 --> Remote Desktop Protocol --> Lateral Movement
IOCs
Dot Samples
01.exe --> SHA256: bebf5c12e35029e21c9cca1da53eb43e893f9521435a246ea991bcced2fabe67
SSDEEP: 768:Qa8bmv7hNAMbgYT6hQdPLC7TasOKS/3U7fzd4tA9yenQ779Zo2lPnoCLnS9QtRbY:Ebmvs71+DKoKS/kjzdfrQty2lPnoqS9X
01.exe –> SHA256: aa85b2ec79bc646671d7280ba27f4ce97e8fabe93ab7c97d0fd18d05bab6df29
SSDEEP: 98304:mt+HWV4nwA+8PgzCRfjMlFBiZhfcrQSav//dH768QyO4YXoftvFUmgaJml9iUybR:NddPgzC+lFkZhER6/t+Hyr4A9FUmVJm+
unpacked:
01.exe –> SHA256: 814e061d2e58720a43bcb3fe0478a8088053f0a407e25ff84fb98850d128f81c
SSDEEP: 1536:CCq2EikJZdZ529nEaqQOyergddb6apjAwzHx4D:7IZYxEHJrIdFjAwzHx4
Registry Changes
Inconclusive as Regshot didn't show anything suspicious, only Delphi related Keys at most
E-Mail Addresses
recover_24_7@protonmail[.]com
Ransomnote
If you want to return your .[REDACTED: random 8-letter lowercase extension] files, contact us and we will send you a decryptor and a unique decryption key. recover_24_7@protonmail[.]comAll your files have been encrypted!
Your personal identifier:===========================================================================================
[REDACTED: 606-digit numeric ID]
===========================================================================================
Article Link: "Nice decorating. Let me guess, Satan?" - Dot / MZP Ransomware