Introduction
Back in March we spotted and monitored a new emerging threat which we dubbed as GoBrut botnet. In our previous blog post, we analyzed a Windows version of this bot, arguing about the usage of the GoLang programming language, a modern language able to reach extremely high level of code portability, potentially enabling the attackers to write code once and compile it for every OSes. That’s exactly what happened. We discovered a new version of the bot compiled for Linux hosts.
This is not the first Linux compatible GoBrut sample discovered in the wild, in fact, other security firms reported in April 2019 the version 2.24 of the bot has been compiled for Linux systems. Our recent discovery, instead, regards an even newer version of the bot, version 3.06. Even in this case it was compiled for Linux environments.
For this reason, Cybaze-Yoroi ZLAB decided to dig into this new version of the Linux GoBrut bot.
Technical Analysis
![]()
Figure 1: Displayed malware version
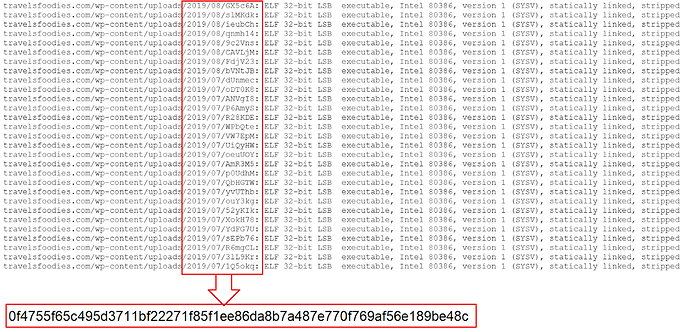
During our intelligence monitoring operations, we encountered a compromised website containing a conspicuous number of suspicious files, in particular ELF binaries. The files were actually copies of the same unique sample.
| Hash | 0f4755f65c495d3711bf22271f85f1ee86da8b7a487e770f769af56e189be48c |
| Threat | GoBrut |
| Brief Description | GoBrut Linux version 3.06 |
| Ssdeep | 98304:EE1b80T1Mv8SzjLZ/YJG9MMa2megmG5OFZj8KIX:n980JpSzBsMa2ac8K |
Table 1: Information about the GoBrut version 3.06
So, we proceeded to compare this latest sample with the previously known ones reported in the AlertLogic technical article.
The sample has many similarities with the other known GoBrut ones, similarities observed both during the static and the dynamic analysis session. For instance the control flow and the communication protocol are the same, the checking and the retrieval of the jobs have no major changes. In detail:
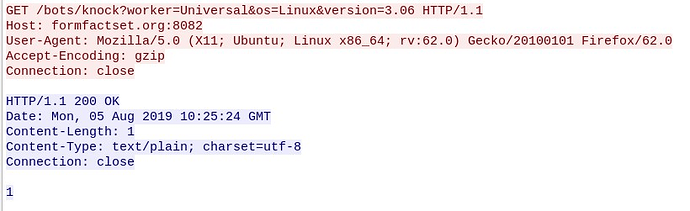
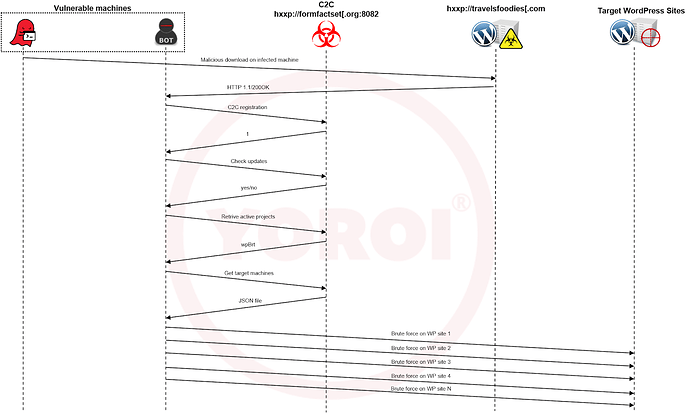
- Register itself to the command and control:
Also, the sample registers itself to the C2 through the path “bots/knock” indicating its kind of worker, the host OS and the version of the malware. The C2 responds with “1” as acknowledgement.
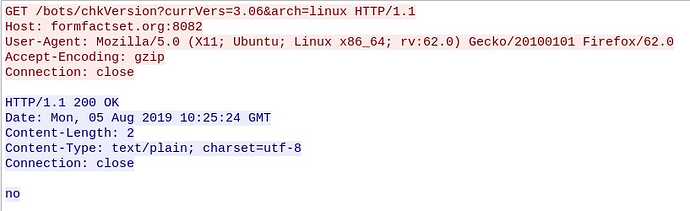
- Check malware updates:
Figure 5: Check for updates
The malware indicates to the C2 its version and the target architecture and the C2 responds indicating whether some updates are available with a simple “yes/no” response.
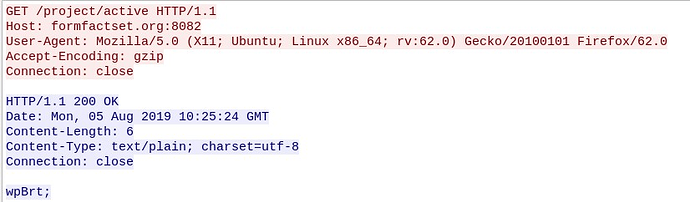
- Retrieve the “Active projects”, which simply means that the malware asks to the C2 which are the services to try the bruteforce:
During the time of analysis, the only active project configured by the botnet operators was the “wpBrt” one, a “WordPress Brute Forcing” attack campaign configured to attack over 270 thousand of with third parties websites with dictionary attacks.
- Get the Json file of the target websites:
Like all the previous versions, also this one retrieves the target list in JSON format and starts trying to access them. At this point, we can summarize the observed behaviour of the GoBrut bot with the following diagram:
A Dangerous Upgrade
As previously mentioned, the behavior of the bot remained similar to the older versions. However, this new version has been made more powerful due to the addition of new features. It has been equipped with new brute forcing modules, in particular with:
- StealthWorker/WorkerQnap module, able to target Qnap NAS service login page.
- StealthWorker/Worker_WooChk module, aiming to support attacks to the “WOO Commerce” CMS.
- StealthWorker/Worker_wpMagOcart module, designed to force the MageCart ecommerce logins.
- StealthWorker/Worker_WpInstall_finder, a recon tool able to find the installation directory of within WordPress sites.
- StealthWorker/WorkerBackup_finder, another utility designed to search for exposed backup folders.
- StealthWorker/WorkerHtpasswd module: trying to retrieve info from the misconfigured htpasswd files.
The full set of modules can be found in the section “List of Workers” .
Target Distribution
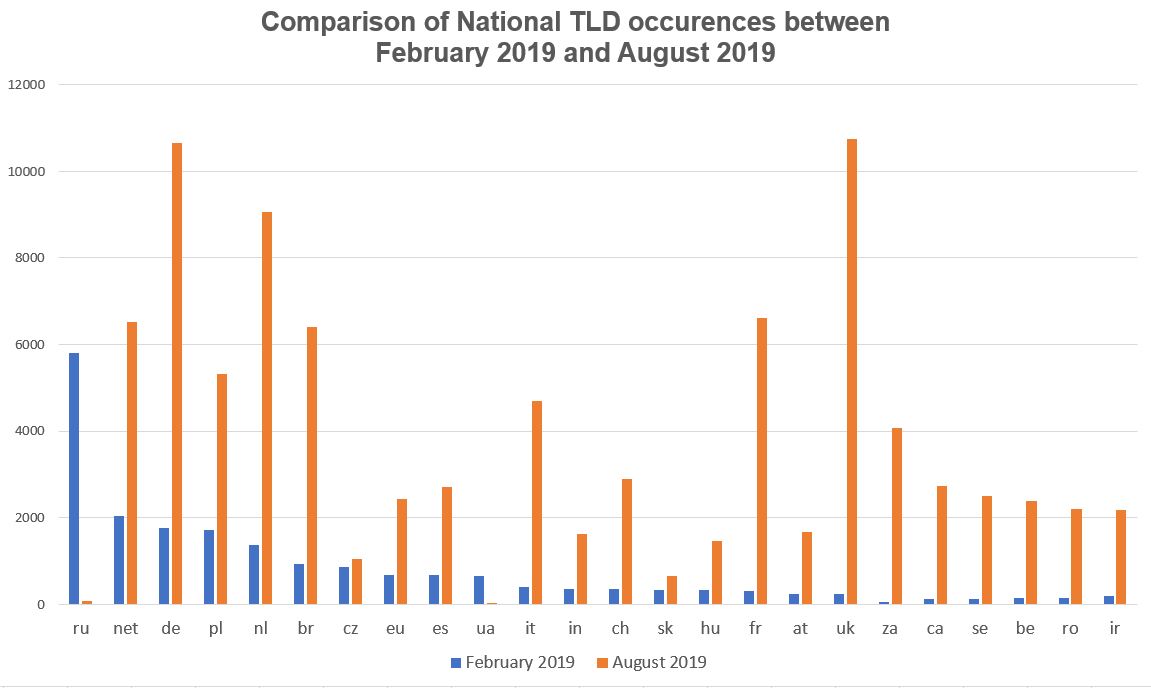
Like our previous analysis, we collected the list of targets of the current botnet campaign and, at the time of writing, we identified more than 270k third parties destinations under attack.
In addition to the “.com”, “.org” and “.info” domains, we notice that most TLDs refer to the EMEA region and, this time, almost no Russian TLD is present. This could mean, with low confidence, the botnet operators may not want to run attacks against the Russian cyberspace, perhaps due to the possible Russian origin of its current clients.
Also, we found over 4600 Italian TLDs appeared in the target list of this GoBrut campaign. Most of them are Small-Medium Companies running WordPress based websites, but there are also Law Firms and No-Profit Associations. As described in our Collection #1 Analysis Whitepaper (ITA), these kind of entities can also be targeted by criminals to exploit their relationship and reputation in order to reach more valuable targeted such as Enterprises, Corporates or VIPs.
Conclusion
The active development of this botnet is another indicator of the increasing popularity of GoLang even for the malware writers. This trend has also been noticed by PaloAlto Unit42 in a technical article published back in January 2019, where they observed an important increase in the number of GoLang powered malware since 2016.
Moreover, the analysis of this StealthWorker/GoBrut version shows the increasing effort of the attackers in expanding their operations, supporting more technologies and adding other recon modules.
We also observed that the targets of this last campaign are hundred of thousand WordPress powered websites, and part of them are related to Italian economic fabric, confirming the increased dangerousness of the botnet along with the presence of ongoing malicious campaigns.
Indicators of Compromise
Hashes
- 0f4755f65c495d3711bf22271f85f1ee86da8b7a487e770f769af56e189be48c
C2:
- formfactset[.org[:8082
Yara Rules
import "elf"
rule GOBRUT_ELF_August_2019{
meta:
description = "Yara Rule for GOBRUT ELF version"
author = "Cybaze Zlab_Yoroi"
last_updated = "2019-08-07"
tlp = "white"
category = "informational"
strings:
$h = {7F 45 4C 46}
$a1 = "StealthWorker"
$a2 = /Worker(\w+)_brut/
$a3 = "github.com/go-pg"
condition:
all of them and elf.type == elf.ET_EXEC and elf.machine == elf.EM_386
}List of Workers
StealthWorker_WorkerPMA_check_DetectCMS
StealthWorker_WorkerPMA_check_Worker
StealthWorker_WorkerWP_check_userEnumerate
StealthWorker_WorkerWP_check_Worker
StealthWorker_WorkerWP_brut_checkBrutOk
StealthWorker_WorkerWP_brut__ptr_WP_Login
StealthWorker_WorkerWP_brut__ptr_WP_Login
StealthWorker_WorkerWP_brut_Worker
StealthWorker_WorkerWP_brut__ptr_WP_HttpClient
StealthWorker_WorkerWHM_check_DetectCMS
StealthWorker_WorkerWHM_check_Worker
StealthWorker_WorkerMagento_check_Worker
StealthWorker_WorkerMagento_check_saveGood
StealthWorker_WorkerJoomla_check_Worker
StealthWorker_WorkerJoomla_check_saveGood
StealthWorker_WorkerDrupal_check_Worker
StealthWorker_WorkerDrupal_check_saveGood
StealthWorker_WorkerCpanel_check_DetectCMS
StealthWorker_WorkerCpanel_check_Worker
StealthWorker_WorkerCpanel_check_saveGood
StealthWorker_WorkerFTP_check_ScanPort
StealthWorker_WorkerFTP_check_Worker
StealthWorker_WorkerFTP_check_saveGood
StealthWorker_WorkerPMA_brut__ptr_Instance_HttpClient
StealthWorker_WorkerPMA_brut__ptr_Instance_TryLogin
StealthWorker_WorkerPMA_brut__ptr_Instance_TryLogin
StealthWorker_WorkerPMA_brut_Instance_CheckSuccessFull
StealthWorker_WorkerPMA_brut_Worker
StealthWorker_WorkerPMA_brut__ptr_Instance_CheckSuccessFull
StealthWorker_WorkerCpanel_brut_Brut
StealthWorker_WorkerCpanel_brut_Worker
StealthWorker_WorkerWHM_brut_Brut
StealthWorker_WorkerMagento_brut_basicAuth
StealthWorker_WorkerMagento_brut_BrutRSS
StealthWorker_WorkerMagento_brut_BrutPanel
StealthWorker_WorkerMagento_brut_BrutDownloader
StealthWorker_WorkerMagento_brut_Worker
StealthWorker_WorkerJoomla_brut_Worker
StealthWorker_WorkerDrupal_brut__ptr_WP_Login
StealthWorker_WorkerDrupal_brut_Worker
StealthWorker_WorkerSSH_brut_Exe_cmd
StealthWorker_WorkerSSH_brut_check_honeypot
StealthWorker_WorkerSSH_brut_Brut
StealthWorker_WorkerSSH_brut_Worker
StealthWorker_WorkerSSH_brut_SaveGood
StealthWorker_WorkerSSH_brut_Exe_cmd_func1
StealthWorker_WorkerFTP_brut_Brut
StealthWorker_WorkerFTP_brut_SaveGood
StealthWorker_WorkerFTP_brut_CheckFalsePositive
StealthWorker_WorkerFTP_brut_Worker
StealthWorker_WorkerFTP_brut_Worker_func1
StealthWorker_WorkerMysql_brut_Brut
StealthWorker_WorkerMysql_brut_Worker
StealthWorker_WorkerPostgres_brut_Brut
StealthWorker_WorkerPostgres_brut_Worker
StealthWorker_WorkerPostgres_brut_SaveGood
StealthWorker_WorkerBackup_finder_HttpCheck
StealthWorker_WorkerBackup_finder_Worker
StealthWorker_WorkerBitrix_brut__ptr_WP_Login
StealthWorker_WorkerBitrix_brut_SaveGood
StealthWorker_WorkerBitrix_brut_Worker
StealthWorker_WorkerBitrix_brut__ptr_WP_HttpClient
StealthWorker_WorkerBitrix_check_Worker
StealthWorker_WorkerOpencart_check_Worker
StealthWorker_WorkerOpencart_brut_Worker
StealthWorker_WorkerOpencart_brut_newfileUploadRequest
StealthWorker_WorkerOpencart_brut__ptr_WP_HttpClient
StealthWorker_WorkerHtpasswd_check_Worker
StealthWorker_WorkerHtpasswd_brut_SaveGood
StealthWorker_WorkerHtpasswd_brut_Worker
StealthWorker_WorkerAdminFinder_GetPage
StealthWorker_WorkerAdminFinder_SaveGood
StealthWorker_WorkerAdminFinder_Worker
StealthWorker_Worker_WpInstall_finder_Worker
StealthWorker_Worker_WpInstall_finder_saveGood
StealthWorker_Worker_wpMagOcart_Worker
StealthWorker_Worker_WooChk_userEnumerate
StealthWorker_Worker_WooChk_Worker
StealthWorker_Worker_WooChk_saveGood
StealthWorker_WorkerQnap_check_Worker
StealthWorker_WorkerQnap_check_saveGood
StealthWorker_WorkerQnap_brut_SaveGood
StealthWorker_WorkerQnap_brut_Worker
StealthWorker_WorkerQnap_brut_newfileUploadRequest
StealthWorker_WorkerQnap_brut_HttpClientThis blog post was authored by Luigi Martire, Davide Testa and Luca Mella of Cybaze-Yoroi Z-LAB
Article Link: https://blog.yoroi.company/research/new-gobrut-version-in-the-wild/