AhnLab Security Emergency response Center (ASEC) discovered cases of the Nevada ransomware being distributed during the team’s internal monitoring. Nevada is a malware written using Rust as its basis and its tendency of adding the “.NEVADA” extension to the files it infects is its defining trait. After encrypting directories, it generates ransom notes with the filename “README.txt” in each directory. These notes contain a Tor browser link for ransom payments.
 Figure 1. Encrypted file examples (left), Nevada ransom note (right)
Figure 1. Encrypted file examples (left), Nevada ransom note (right)1. Main Features of Nevada Ransomware
As shown in the figure below, this ransomware supports command-based options to have more control over the execution method. If the ransomware is executed without specifying any options, it will go through every drive and only perform encryption. However, encryption can be performed on specific files and directories by designating them using the “file” and “dir” options. Additionally, other features can be used, such as self-deletion, the additional load of drives targeted for encryption, and safe mode operation by using the other options. The table below is a brief description of the command-line based features supported by this ransomware.
 Figure 2. Nevada ransomware execution options
Figure 2. Nevada ransomware execution options| Option | Feature |
| -file | Perform encryption on the designated file |
| -dir | Perform encryption on designated directory. All subdirectories are also encrypted (Directories with the “Nevada” extension are excluded from encryption) |
| -sd | Self-deletion |
| -sc | Volume shadow deletion (Must be run as administrator) |
| -lhd | Load hidden drives |
| -nd | Encrypt shared network folders |
| -sm | Perform ransomware operation after rebooting in safe mode (Must be run as administrator) Deactivates Windows Defender service |
| -help | Explanation of ransomware options |
1. Self-deletion (-sd)
As shown below, the Nevada ransomware supports a feature that allows it to delete itself after it performs the encryption routine.
 Figure 3. Self-deletion option of Nevada ransomware
Figure 3. Self-deletion option of Nevada ransomware| “cmd.exe” /c ping 127.0.0.1 -n 3 > Nul & Del /f /q C:\path\to\malware\ransom.exe |
2. Volume Shadow Deletion (-sc)
A key feature of the Nevada ransomware has been discovered where it uses DeviceIoControl as a way to interfere with system recovery (T1490). The following figure shows the method used to delete the volume shadow copies within the ransomware. This method appears to be the same as the one posted on Twitter and GitHub (poc) around March of 2021.
 Figure 4. Resizing volume shadow using DeviceIoControl()
Figure 4. Resizing volume shadow using DeviceIoControl()This code gets direct access to device drivers through Device IO Control calls to “resize the volume shadow copy storage to an extremely small size.” Although various other existing malware often uses vssadmin, wbadmin, bcedit, and wmic command calls to interfere with system recovery, this ransomware uses a less common method where Device IO Control calls is used directly.
3. Load Hidden Drives (-lhd)
The Nevada ransomware goes through every volume using each defined drive string shown in the figure below. It also has a feature that allows it to load hidden partitions for encryption.
 Figure 5. Hidden partitions loaded and encrypted
Figure 5. Hidden partitions loaded and encrypted4. Encrypt Shared Network Folders (-nd)
Aside from the above feature of loading and encrypting hidden drives, Nevada is also capable of accessing shared network resources within a system and performing encryption, as shown in the figure below.
 Figure 6. Encryption of shared network folders
Figure 6. Encryption of shared network folders5. Run in Safe Mode (-sm)
This malware is capable of rebooting the system and operating in safe mode. For this purpose, it is also capable of registering the ransomware program as a service that can be executed while in safe mode. An additional feature was also confirmed where the ransomware would remove WinDefender from the auto-run service list after rebooting into safe mode.
 Figure 7. Service creation and auto-run registry registration to operate after booting into safe mode
Figure 7. Service creation and auto-run registry registration to operate after booting into safe mode Figure 8. WinDefender disabled after booting into safe mode
Figure 8. WinDefender disabled after booting into safe mode| Action | Registry Key | Value |
| Create | HKLM\SYSTEM\CurrentControlSet\Control\ServicesPipeTimeout | 0x5265c00 |
| Create | HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\nevada | “Service” |
| Delete | HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\WinDefend | – |
2. Nevada Encryption Targets and Exception Conditions
1. Locale Excluded from Infection
In the case of this Nevada ransomware sample, it does not infect systems that are in specific nations of the Commonwealth of Independent States (CIS). It instead terminates itself. These countries have been confirmed to be related to the former Soviet Union. It appears that a bit flag is set for these countries within the code to exclude them from the process.
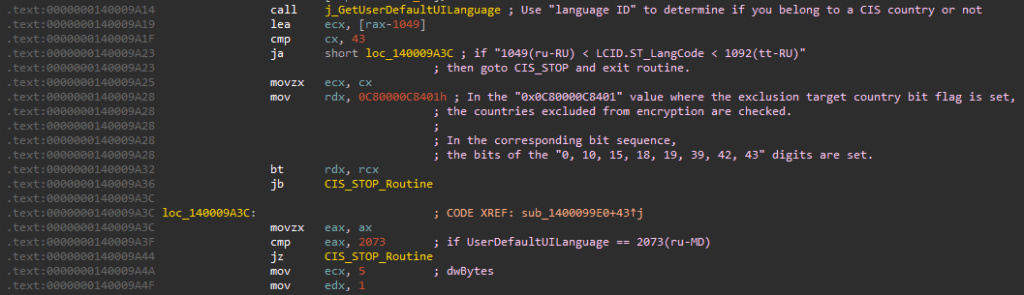 Figure 9. Nevada ransomware’s language code checking routine
Figure 9. Nevada ransomware’s language code checking routine| 0x0419(ru-RU), 0x0423(be-BY), 0x0428(tg-Cyrl-TJ) ,0x042B(hy-AM), 0x042C(az-Latn-AZ), 0x0440(ky-KG), 0x0443(uz-Latn-UZ), 0x0444(tt-RU), 0x0819(ru-MD) |
2. Filenames and Folders Excluded from Encryption
This ransomware includes a routine that checks the filenames and folder names that are excluded from encryption as shown in the figure below. The files and folders that are ultimately excluded from encryption are listed in Table 4.
 Figure 10. Filenames and folders excluded from infection check routine
Figure 10. Filenames and folders excluded from infection check routine| Folders excluded from infection | windows, program files, program files (x86), appdata, programdata, system volume information, NEVADA, |
| Extensions excluded from infection | exe, ini, dll, url, lnk, scr |
| Substrings excluded from infection | ntuser |
3. Conclusion
To prevent ransomware infection, users must be cautious of running files from unknown sources and make sure to scan suspicious files with an anti-malware program while also keeping the program updated to the latest version.
V3 detects this malware in the following way.
[File Detection]
- Ransomware/Win.Nevada.C5391542 (2023.03.06.03)
[Behavior Detection]
- Ransom/MDP.Decoy.M1171
- Ransom/MDP.Event.M1785
[IOC]
- b673d92b77489d12779dc1fb5e8f6fdd (MD5)
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
The post Nevada Ransomware Being Distributed in Korea appeared first on ASEC BLOG.
Article Link: Nevada Ransomware Being Distributed in Korea - ASEC BLOG