Yet another Security Analytics product focused on the network. On the surface that sounds like a not-so-relevant product category. Don’t we already have a plethora of network security products starting with Firewalls, IDS/IPS, Full Packet Capture and Replay, and Web Gateway? And the list goes on.
Yet another Security Analytics product focused on the network. On the surface that sounds like a not-so-relevant product category. Don’t we already have a plethora of network security products starting with Firewalls, IDS/IPS, Full Packet Capture and Replay, and Web Gateway? And the list goes on.
But at the same time just pick up a copy of the Wall Street Journal – what do you find? Fortune 500 companies in the news as the result of having suffered data breaches with sensitive data compromised. In almost all cases malicious attackers breached the company’s network and got a hold of sensitive information that was securely stored deep within the data center.
Clearly, despite all of the technologies available today, attacks are still successful. Current tools aren’t doing enough. Before you dismiss this as a problem of the privileged (i.e. Fortune 500-type of companies), what you may have noticed is that having networks breached is far more prevalent in smaller and mid-size companies. It’s just that they are not the companies that get reported in the news all the time.
Why a New Category of Network Security is Desperately Needed
So now that we have your attention, let’s dig a bit deeper into what the security problem really is.
Attackers have to compromise a machine or user on a company’s network and then operate within the network to get to the crown jewels. To prevent this, companies have implemented security controls based on the age-old idea of fortification – deploy perimeter controls like Firewalls and IDS and I will prevent all the bad stuff from entering my network. What is referred to as North-South traffic.
But these perimeter defenses are helpless when your devices (i.e. end user machines) walk outside the perimeter and show up on coffee shop networks. When they rejoin your network, the threat simply walks right in, bypassing all perimeter controls. What we are missing is the ability to detect threats already operating within a network. Can you find the malicious attacker that has been able to compromise a machine on your network and is now free to operate within your network?
The knee-jerk response to the security problem described above is as follows: “Fine! Granted this is a problem that needs to be addressed. I’ll simply deploy my perimeter security controls like IDS within my network.” But the solution is not that straight-forward. The challenge is that once the attacker is inside the network the tools and techniques to move laterally and compromise other machines are very different than those used to try to breach perimeter defenses. They range from every day IT tools and techniques like webshells running remote commands and remote desktop (RDP) to deploying sophisticated tools like Metasploit that have built-in modules and automation to bypass complex security hurdles. These IT tools are commonly used for normal business activities, such as IT administrator using RDP to connect to a user’s machine to troubleshoot normal IT issues, so, not something that would typically set off the alarms.
Analyzing Network Traffic is Beyond Manual Monitoring
Hopefully, we have established that security controls designed to inspect network protocols and identify malicious attacks on the perimeter are important but not as effective for detecting attackers operating within the network. At this point, you may be contemplating the massive volume of activity taking place across your company’s network on any given day – the East-West traffic – and how you might possibly monitor it to detect the malicious activity. Clearly, it’s beyond manual monitoring and needs technology-based help.
This is where the era of Artificial Intelligence (AI) begins. AI and technologies like Big Data Analytics offer efficient storage and compute at petabyte-scale. These technologies have been effectively used to build a new category of network security product – Network Traffic Analysis (NTA). The objective is to solve the challenge of detecting attackers operating within the network.
NTA solutions are designed to capture, store, and inspect all internal network traffic (i.e. machine A connecting to machine B within your network), and external network traffic (i.e. machine A communicating with server C on the Internet outside the boundary of your network). Applying sophisticated machine learning algorithms, AI-based NTA solutions can learn typical behavior patterns on any network and can then spot anomalies on the network. When attackers operate within the network, their network interactions will be anomalous, or unusual, compared to employees conducting normal, legitimate daily business. The end result is the ability to accurately spot attackers that have penetrated the network and their activities make it clear that they are now operating within a network.
Real World Data Breach Scenario – How would Network Traffic Analytics help?
If you have read the Verizon Data Breach Report Digest (highly recommend it if you have not read it), this scenario on “Backdoor Access – The Alley Cat” should be familiar. To refresh your memory, a construction company finds competitors in overseas market have designs and innovative engineering drawings for skyscrapers that are very similar to those on which the construction company had spent substantial R&D $$. Suspecting a data breach, a review of their network and endpoint posture reveals a significant network breach that occurred several months ago.
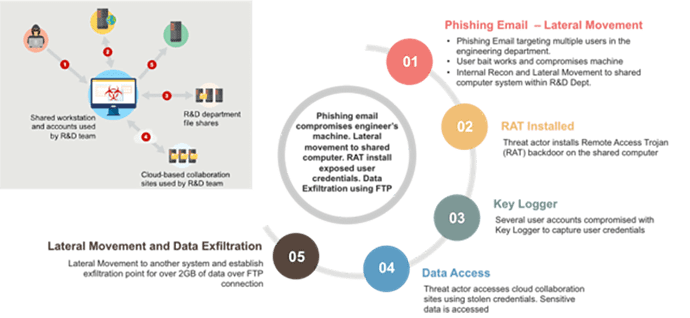
Not surprisingly, this was actually a straightforward attack by cybercriminals that went after intellectual property and sold it on the underground market (see Figure 1 and details below).
Figure 1: The stages of the “Backdoor Access – The Alley Cat” attack. Source: Verizon Data Breach Report.
- Phishing email was sent to several engineers in the R&D department. Once a user fell prey to the bait, his machine was compromised and used to laterally move within the network to other systems in the R&D department.
- Threat actors discovered a shared computer in a conference room used for presentations and installed a Remote Access Trojan (RAT) as a backdoor on the shared computer.
- The RAT was used to establish a presence in the network and eventually a keylogger was installed on the shared computer, compromising user credentials.
- The threat actors then accessed a cloud collaboration site using the stolen credentials to access engineering drawings and design plans.
- Finally, the threat actors once again moved laterally to another machine to establish an exfiltration point and managed to steal the information over an FTP connection.
Let’s break down the scenario and evaluate how Network Traffic Analysis would have detected these malicious attacks and alerted the security team at every stage of the attack:
| Stage in the Attack | What NTA Technology Would Detect |
| 1. Phishing email resulted in a compromised host and lateral movement | NTA products detect and prevent attacks from entering the organization. In this case, NTA would have identified the email campaign with a malicious phishing URL sent to multiple users within the same department. NTA products can also watch the network to see if any employee visits the URL and link phishing email with actual network activity. |
| 2. RAT installed on a shared computer in the conference room. | NTA products can detect anomalous lateral movement. Additionally, the context that the machine was compromised due to download from a phishing URL sets up the alert as a high priority. |
| 3. Keylogger downloaded onto a shared computer, resulting in compromised credentials. | Network Analytics products often integrate or include malware protection in the form of sophisticated sandbox solutions. NTA products would have identified connections to an external website and the download of the RAT. |
| 4. Threat actors used credentials to access cloud collaboration site. | Anomalous data downloads on the shared computer from cloud collaboration sites would have triggered a security alert. |
| 5. Threat actors moved laterally to identify exfiltration point and then used FTP connection to steal information. | Finally, data exfiltration using less common protocols such as FTP from a machine that typically does not transfer huge volumes of data would have triggered anomaly detection and alerted the security team. |
Summary
The organization in the breach case study was a victim but arguably now they are better off – their security posture has changed significantly. Millions of organization gamble with their existential risk by not sufficiently focusing on security. While it may be a cliche – but it’s true – most organizations just don’t know that their network has been breached until something dramatic happens to them. I hope they don’t become another case study of how they got breached. Rather we should have case studies on how organizations take network security seriously and have thwarted cyberattacks.
Stay tuned for my next blog in this series on network security in which I will elaborate on AI, machine learning, and big data as revolutionary, not evolutionary technologies.
The post Network Traffic Analytics – Do We Need One More Network Security Category? appeared first on Lastline.
Article Link: https://www.lastline.com/blog/network-traffic-analytics-do-we-need-one-more-network-security-category/