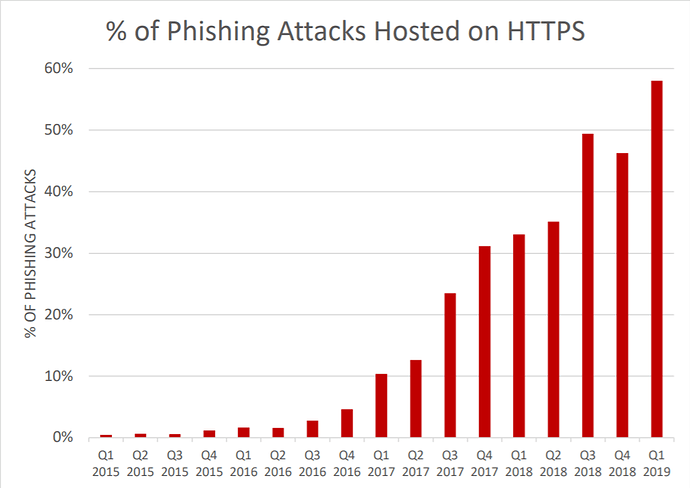
As Google Chrome and other web browsers further embrace HTTPS in a visual way, it’s becoming a requirement that threat actors use it, too. By the end of Q1 2019, more than half of all phishing sites have employed the use of HTTPS, now up to 58%. This is a major milestone and shows that threat actors actions often mirror that of the majority of users.
“In Q1 2019, 58 percent of phishing sites were using SSL certificates, a significant increase from the prior quarter where 46% were using certificates,” said John LaCour, Founder and CTO of PhishLabs. “There are two reasons we see more. Attackers can easily create free DV (Domain Validated) certificates, and more web sites are using SSL in general. More web sites are using SSL because of browsers warning users when SSL is not used, and most phishing is hosted on hacked, legitimate sites.”
At the end of last year, our team identified that nearly half of all phishing sites were employing HTTPS or a SSL certification. Specifically, HTTPS was found on 49% by the end of Q3. It later dipped in Q4, which was the first drop since our initial analysis in Q1 of 2015. As John noted, there are several reasons behind the use of HTTPS on phishing sites, and the specific use of Secure (lock) versus Not Secure can be a bit confusing. HTTPS simply means that a site is using encrypted communication when sending information between you and it. When a threat actor uses it, say for example using a fake login screen for Twitter, that site is still going to steal your login credentials, but at least it does so securely.

Although threat actors can certainly go after one another, the HTTPS feature on a phishing site is simply another social engineering or required feature.
On the feature side, HTTPS prevents the likes of Google Chrome from throwing up a big red flag stating that the user should turn around. On social engineering, a site needs to mirror an actual site in every way feasible, or simply reduce the number of red flags a regular user may notice before handing over their credentials.
The use of HTTPS and the amount in play comes down to the threat actor’s preference. When we see an increase in HTTPS on phishing sites it’s due in part to how active threat actors are and who their targets are. The same can be said about why some threat actors will use compromised websites and spoofed websites, rather than a free website.
The next quarterly update will be available after July, but it’s reasonable to expect that HTTPS will only increase in use by threat actors going forward.
Article Link: The Leader in Digital Risk Protection | Intelligence & Mitigation