Monthly Threat Actor Group Intelligence Report, January 2023 (ENG)
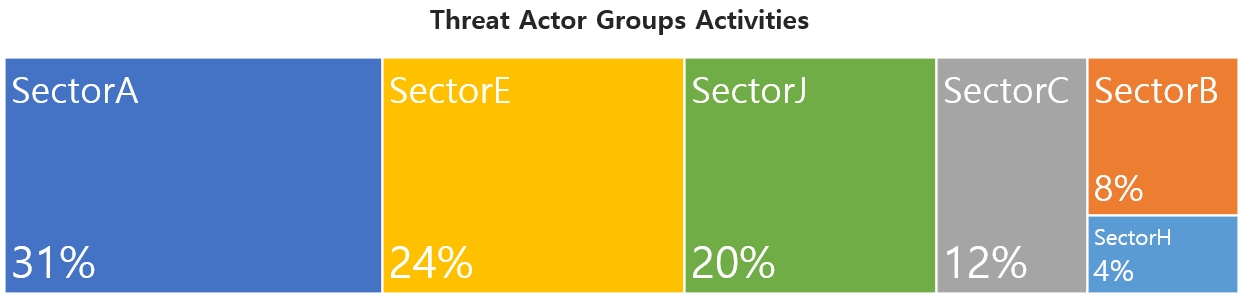
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 December 2022 to 20 January 2023. In January, activities by a total of 19 Threat Actor Groups were identified, in which activities by SectorA was the most prominent by 31%, followed by SectorE and SectorJ groups.
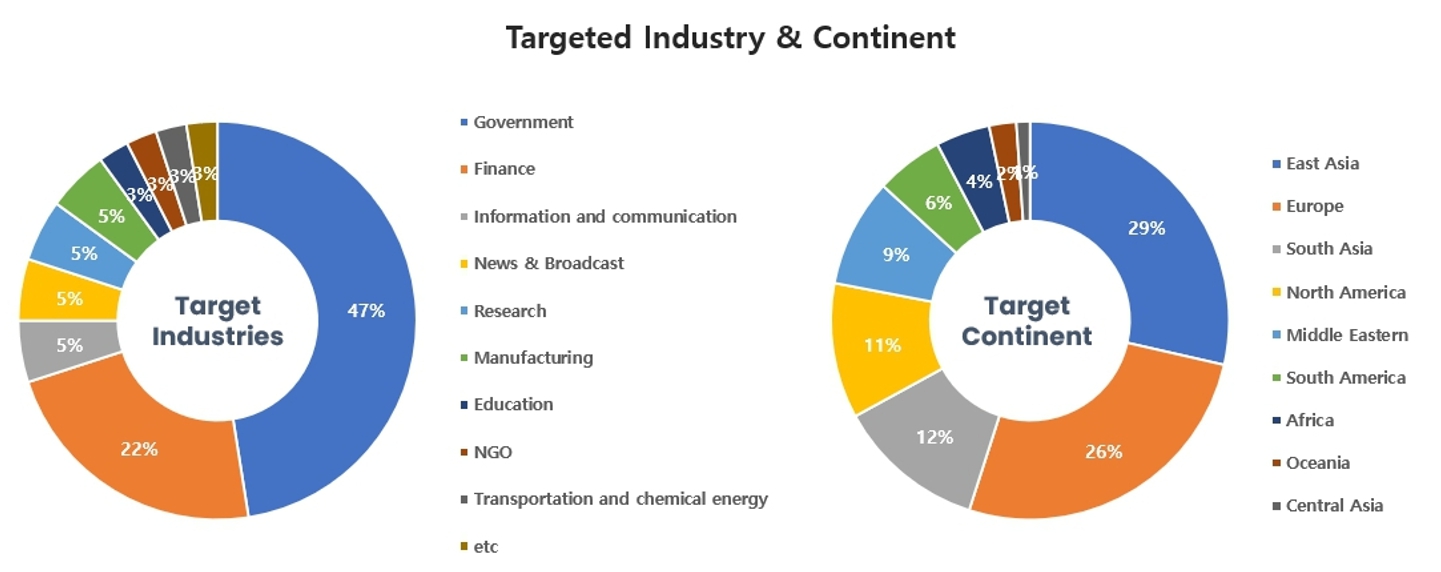
Threat Actors identified in January carried out the highest number of attacks on workers and systems in government agencies and financial sectors. Regionally, East Asia and Europe were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In January 2023, activities by a total of 3 hacking groups were identified, and the groups were SectorA01, SectorA05 and SectorA06 groups.
SectorA01 group was found to be active in Sweden. The group used malwares disguised as the hiring post of a Bitcoin exchange to infect systems and steal system information.
SectorA05 group was found to be active in South Korea. The group targeted on workers in government institutions, media communications, and universities to send out phishing emails, which consisted of a body text leading the targets to change their passwords, and a hyperlink address to a phishing website. The group was seen to have built a phishing website and led the targets to access it in order to steal account credentials.
SectorA06 group was found to be active in Japan, Nigeria, and the United States. The group disseminated VHD (Virtual Hard Disk) and ISO image format malwares to evade detection by MOTW (Mark-of-the-Web), a Microsoft security function that displays the file’s origins. Afterwards, the group was analyzed to be attempting to collect system information and take over system controls.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In January 2023, activities by a total of 2 hacking groups were identified, and the groups were SectorB22 and SectorB38.
SectorB22 group was found to be active in Taiwan, Germany, Czech Republic and Estonia. The group targeted on government institution workers to send out malware-incorporated compressed files disguised under various topics such as European Commission draft report and Austria working visa. In the final stage, the malware carried out the function of monitoring the infected system and collecting information.
SectorB38 group was found to be active in Vietnam and Latvia. The group disseminated MS Word document malwares utilizing the Template Injection technique. In the final stage, DLL malware was used to collect information from the infected system and transfer them to the C2 server.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In January 2023, activities by a total of 1 group was identified, and the group was SectorC08.
SectorC08 group was found to be active in Ukraine, Russia, Latvia, Lithuania, Poland, England, Egypt, France, and the United States. The group used malware disguised as administrative documents related to military services, and attempted to steal information through UltraVNC, a remote access tool, at later stages.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorE Group Activities
In January 2023, activities by a total of 3 hacking groups were identified, and the groups were SectorE02, SectorE03, SectorE05.
SectorE02 group was found to be active in India, Bangladesh, France, Iran, Albania, the United States, Sri Lanka, Pakistan, and Estonia. The group distributed MS Word and Excel malwares disguised as monthly action plan, cybersecurity policies, and list of invitation ideas. Following this, additional malware was used to collect system information such as file data, process details, and screenshots, and transferred them to the C2 server.
SectorE03 group was found to be active in China, England, the United States, Pakistan, Russia, Ukraine, France, South Korea, India, Canada, Italy, Kyrgyzstan, Belgium, Belarus, Columbia, Japan, Germany, Iraq, Nigeria, and Lithuania. The group targeted on government sector workers to send out emails attached with malwares, and the VHD (Virtual Hard Disk) in the attached file was used to evade detection by MOTW (Mark-of-the-web). In the final stage, the malware collects information from the infected system and attempts to take over system controls.
SectorE05 group was found to be active in Taiwan, Pakistan, Australia, China and Iran. The group targeted on workers of government institutions and IT industries to deliver emails attached with malwares. The malware maintains persistency in the infected system to collect computer name and username for sending them to the C2 server.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
5. Characteristics of SectorH Group Activities
In January 2023, activities by a total of 2 groups were identified, and the groups were SectorH01 and SectorH03.
SectorH01 group was found to be active in Columbia and China. The group used MS Word document malware disguised as legal notice to install FSociety, a pentesting framework, and njRAT, a remote access tool, in the target’s system to carry out information stealing activities.
SectorH03 group was found to be active in India. The group disseminated Android remote access tools disguised as YouTube, a video streaming platform, to carry out information stealing activities.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, India, so it is analyzed that they will continue activities to collect advanced information regarding Indian government agencies’ military and politics to their need.
6. Characteristics of cybercrime group activities
In January 2023, activities by a total of 8 hacking groups were identified, and the groups were SectorJ04, SectorJ06, SectorJ09, SectorJ14, SectorJ64, SectorJ72, SectorJ73, and SectorJ84.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ04 group was found to be active in India, China, the United States, the Netherlands, Canada, Singapore, Brazil, Germany, Finland, Morocco, Israel, Spain, France, Turkey, Cameroon, Belgium, England, South Korea, and Tunisia. The group used a phishing website impersonating the website of a video call software, and used malware disguised as the legitimate software to attempt information stealing.
SectorJ06 group was found to be active in Germany and South Korea. The group used HIVE ransomware to encrypt data and exploited various tools such as Cobalt Strike to steal data.
SectorJ09 group continued to use their hacking strategy of inserting obfuscated skimming scripts in websites to collect username, address, email, phone number and credit card details from the payment page.
SectorJ14 was found to be active in Japan, England, France, South Korea, Germany, the United States, Taiwan, and Turkey. The group targeted on a specific Wi-Fi router for DNS Hijacking purposes, and distributed malware disguised as Chrome browser that steal Android smartphone information to users accessing the damaged router.
SectorJ64 group was found to be active in Mexico, Taiwan, China. The group targeted on servers consisting of vulnerable security settings or prone to vulnerabilities due to using older versions by scanning for servers that are accessible through internet, and attempted Cryptojacking after a successful penetration.
SectorJ72 group was found to be active in Canada, Columbia, Italy, Belgium, Poland, Spain, Turkey, Ukraine, South Korea, Germany, the United States, England, the Philippines, Taiwan, and Algeria. The group led targets to access a URL that hosted malwares through malicious advertisements, and used downloader malwares disguised as pornographic videos.
SectorJ73 group used PolyVice ransomware that contained Vice Society strings in the file for financial profit, which created a ransom note after file encryption to deliver contact points for ransom negotiations.
SectorJ84 group was found to be active in Spain, Austria, Bulgaria, Italy, Hong Kong, Germany, the United States, India, Turkey, Belarus, Romania and England. The group led targets to download compressed malwares through a phishing link that was included in a phishing email disguised as invoices. The malware executed at the final stage stole various information such as credentials across multiple browsers and cryptocurrency wallet related data.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact [email protected]
Article Link: Monthly Threat Actor Group Intelligence Report, January 2023 (ENG) – Red Alert