In an incident response investigation, CrowdStrike analysts use multiple data points to parse the facts of who, what, when and how. As part of that fact-finding mission, analysts investigating Windows systems leverage the Microsoft Protection Log (MPLog), a forensic artifact on Windows operating systems that offers a wealth of data to support forensic investigations. MPLog has proven to be beneficial in identifying process execution and file access on systems.
To aid investigators everywhere, this blog post provides an overview of the MPLog files, offers examples of the data contained within and walks through a case study of RClone, a data exfiltration tool used by eCrime actors during ransomware attacks.
What Is the MPLog?
The Microsoft Protection Log, or MPLog, is a plain-text log file generated by Windows Defender or Microsoft Security Essentials for troubleshooting purposes. This log can contain historical evidence of the following:
- Process execution
- Threats detected
- Scan results and actions taken
- Signature update versions
- File existence
Where to Find the MPLogs
MPLog files are stored under the directory C:\ProgramData\Microsoft\Windows Defender\Support. In this directory you will find the file MPLog-*. The screenshot in Figure 1 provides an example of sample content.
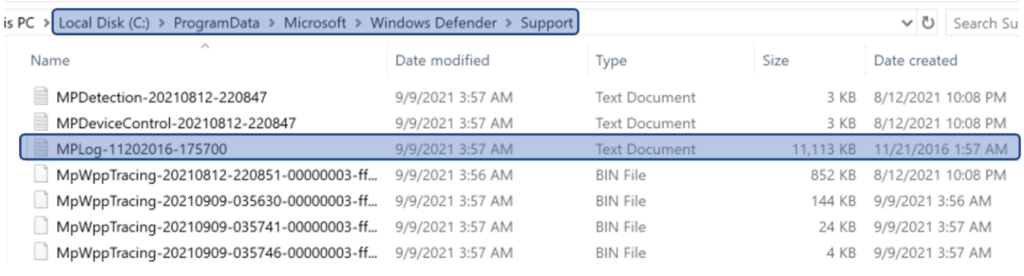
Figure 1. Example MPLog location
Interpreting MPLog Data
There are several different event types present in this log file. Some examples are listed below.
Note: Log formatting for each event has changed over time, so depending on when the event was written, you may have more or fewer fields than explained below.
Estimated Impact Events
Estimated impact events are generated to log the estimated performance impact information of running software as part of Windows Defender. These events can show evidence of execution, file access and count of file access. Microsoft documentation on these events can be found here.
Example: 2020-06-14T20:11:42.880Z ProcessImageName: explorer.exe, TotalTime: 30, Count: 11, MaxTime: 15, MaxTimeFile: \Device\HarddiskVolume1\Users\Public\Desktop\PuTTY (64-bit).lnk->[CMDEmbedded], EstimatedImpact: 9%
| Field Name | Description | Data |
| N/A | Event time generated in UTC | 2020-06-14T20:11:42.880Z |
| ProcessImageName | Process image name | explorer.exe |
| TotalTime | The cumulative duration in milliseconds spent in scans of files accessed by this process | 30 |
| Count | The number of scanned files accessed by this process | 11 |
| MaxTime | The duration in milliseconds in the longest single scan of a file accessed by this process | 15 |
| MaxTimeFile | The path of the file accessed by this process for which the longest scan of MaxTime duration was recorded | \Device\HarddiskVolume1\Users\Public\Desktop\PuTTY (64-bit).lnk |
| EstimatedImpact | The percentage of time spent in scans for files accessed by this process out of the period in which this process experienced scan activity | 9% |
Table 1: Estimated Impact Events
SDN Events
As part of Windows Defender’s cloud protection service, SDN events can show evidence of file existence on disk along with sha1 and sha2 hashes for the identified file. The following is an example of an SDN event:

| Field Name | Description | Data |
| N/A | File full path and name | C:\ProgramData\badfile.exe |
| Sha1 | SHA1 hash of file | 876d0908145c822c06060413ecacc1baca97892c |
| Sha2 | SHA256 hash of file | 121b6ad75b3ead2a09e8bf6959423f6ce91239e0c062060aa948bb379f906534 |
Table 2. SDN events
Detection Events
These events can show evidence of file execution, process information and the Windows Defender street name for detection.
Examples:
- 2021-07-22T15:38:04.557Z DETECTION_ADD Ransom:Win32/Conti.ZA file:C:\ProgramData\badfile.exe
- 2021-07-22T15:38:04.557Z DETECTION_ADD Ransom:Win32/Conti.ZA process:pid:100128,ProcessStart:132696072639875080
| Field Name | Description | Data |
| N/A | Event time generated in UTC | 2021-07-22T15:38:04.557Z |
| N/A | AV street name | Win32/Conti.ZA |
| PID | Process ID | 100128 |
| ProcessStart | Process start time (WebKit/Chrome Timestamp) | 132696072639875080 |
| File | File full path and name | C:\ProgramData\badfile.exe |
Table 3. Detection events
EMS Detection Events
As part of Windows Defender’s memory scanning engine, EMS detection events can show evidence of process injection.
Examples:
- Engine:EMS scan for process: explorer pid: 6108, sigseq: 0x0, sendMemoryScanReport: 0, source: 1
- Engine:EMS detection: HackTool:Win64/CobaltStrike.A!!CobaltStrike.A64, sigseq=0x0000C0C53E1F0B73, pid=6108
| Field Name | Description | Data |
| N/A | Process name | explorer.exe |
| N/A | AV street name | HackTool:Win64/CobaltStrike.A!!CobaltStrike.A64 |
| PID | Process ID | 6108 |
Table 4. EMS detection events
Rclone Case Study
In a recent ransomware incident, CrowdStrike leveraged MPLog data to gain more insight into the use of the file transfer utility Rclone, used by the threat actor for data exfiltration. MPLog data was used to identify which files the threat actor was targeting and the potential number of files exfiltrated.
Like many ransomware incidents today, CrowdStrike identified evidence of potential data exfiltration prior to execution of the ransomware. This was evident from the presence of the Rclone utility and evidence of execution found on an encrypted system. Unfortunately, there was no telemetry from the system to say what the exact Rclone command parameters were. For those unfamiliar with Rclone, a typical command is as follows:
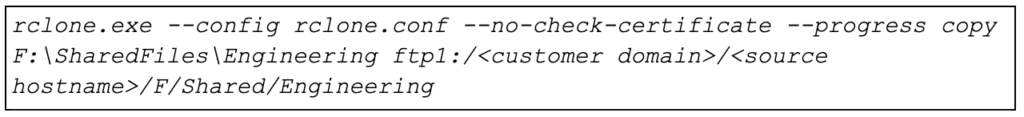
As seen in the sample command, the data targeted for exfiltration can be identified in the path information. Using a simple string search for the term “rclone.exe” CrowdStrike discovered the following hits in the MPLog file:
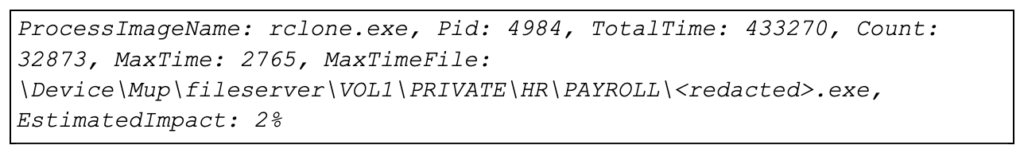
Combined with what we know about the Estimated Impact Events from Microsoft’s documentation, we can make several statements from this data:
- rclone.exe executed with PID 5244
- rclone.exe accessed 32,873 files
- Windows Defender scanned 32,873 files that rclone.exe accessed
- rclone.exe accessed the file
\Device\Mup\fileserver\VOL1\PRIVATE\HR\PAYROLL\<redacted>.exe- This is a file that Windows Defender took the longest time to scan that rclone.exe accessed
Conclusion
Additional research is needed to fully understand the details and additional potential investigative value of the MPLog, but initial analysis and research show that this data can be valuable for assisting in forensic investigations to identify process execution and file access on systems. Especially in cases where anti-forensic measures are taken or other artifacts on disk become impacted, MPLog can help investigators pick up the pieces and tell the full story.
Additional Resources
- For more information on CrowdStrike’s Incident Response, Compromise Assessment or Threat Hunting offerings, visit the CrowdStrike Services page or please reach out to us at: [email protected].
- Start your full-featured free trial of CrowdStrike Falcon Prevent
 and see how true next-gen AV performs against today’s most sophisticated threats.
and see how true next-gen AV performs against today’s most sophisticated threats.
Article Link: How to Use MPLogs for Forensic Investigations | CrowdStrike