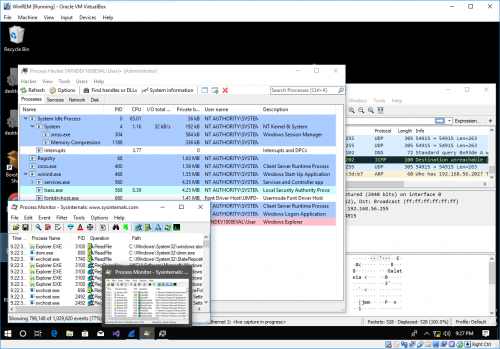
If you're not into Wireshark, procmon and Windows Sysinternals you might be in the wrong place :)
Malware analysis allows the analyst to see what actions are taken and allows us to use those actions to build a profile that can be used to detect and block further infections and find related infections. We run the malware in labs to determine how they act, we give them different inputs to see how the behavior changes, we run them through debuggers to disable safeties and checks that it might have against analysis, and we may even use a disassembler to more fully understand the paths that the malware may take. Using these techniques, the malware analyst builds a list of indicators that can be used to detect and block the malware that they are examining, build information about who may be targeting their network, and even what the malware may be gathering. I’m going to narrow my focus to behavior analysis and give some examples of what can be done with threat hunting and this technique.
Behavioral Analysis for Malware
Behavioral analysis is the step of running the malware under controlled conditions where you can observe the actions that the malware takes. By running the malware in a completely isolated environment we can tell what the malware would do if it was unable to communicate. With behavioral analysis, you take everything a step at a time. When it is completely isolated does it try to scan for a network? If yes, then go ahead, add it to one, and see what happens. After that does it start looking for? Give it to it. The main goal of this type of analysis is to see what the malware does in a step-by-step process, allowing you to map its different actions and have a better overall picture of the malware before you start examining it in debuggers or through disassembly. I would say that this is one of the more fun parts of the analysis process.
Basic Lab Environment for Malware Analysis
Your basic lab environment should contain:
- VMware/Virtualbox with the following computers:
- Windows with Wireshark, Process Monitor, and procDOT installed.
- REMnux (has everything preinstalled that you will need)
Make sure that your VMs are set to host only networking and that your windows machine has your REMnux box as the default gateway by setting a static IP address. This ensures that the first hop will be to REMnux and will allow the traffic control that we would want.
Tools for Malware Behavioral Analysis
There are several tools that you want to use to gather the most information that you can:
Wireshark: This tool isused to gather network traffic on a given interface. The follow option will allow you to view pages and traffic, and it even allows you to recreate and save files that were transferred while the packet capture was running. https://www.wireshark.org/
Process Monitor: (procmon) This tool is used to record the full activity of a computer for the time that it is monitoring. This is extremely useful for detailing actions taken by processes. https://docs.microsoft.com/en-us/sysinternals/downloads/procmon
ProcDOT: This tool takes a CSV from Process Monitor and can show you what a specific process did as a flowchart. This makes it much easier to interpret what happened, and in what order. http://procdot.com/
FakeDNS: This tool is an included script in REMnux that replies to all DNS requests with its own information and outputs the requested domain to the terminal. This is useful for determining what domains are being requested by each computer that is connected to it.
accept-all-ips: This tool is also an included script in REMnux. This redirects all IP traffic to the REMnux host. Very dangerous if activated on a live environment, but very useful to force traffic to your analysis machine.
INetSim: This is a software suite that simulates many common services/protocols on the web. This suite will even provide malware samples with benign executable if something asks for it. https://www.inetsim.org/
Running the Malware through Behavioral Analysis
When you run the malware make sure to start procmon and Wireshark on the Windows host always just before you launch the malware. That allows you to make sure that you catch all the malware activity. Once you are done with the malware you will be able to save the procmon results and open them in procdDOT. This will give you a nice view of exactly what the malware did. Make sure to check Wireshark as well for any unknown traffic as well. Once you can see what it does with nothing you can reset your windows machine and start again. Yes, it does get repetitive resetting with each go, but you always want to start with a clean environment. After you have determined what the malware was looking for, set up your REMnux system or clean environment to give it what it wants. You really want to repeat this until you either cannot determine what it needs, or it stops asking for new things. At this point you should have a nice list of IP addresses, domains, files, etc. that the malware is looking for, or reaching out to.
Make sure to tune your systems to alert for these indicators that are found. You would not want to end up with a similar infection because you forgot to look for the information you just found. There are other types of analysis to do with the malware sample you have, but for this let’s concentrate on the next step and look at what our list of indicators can help us with.
Let’s Go Threat Hunting Using Our Malware Analysis
Once you have determined what the malware is looking for, you have a great place to start looking for other threats. Find other places on the network that may have a similar build (even if it happens to be all your workstations) and hunt. Checking system logs, either by querying the logs directly or through your SIEM, for similar activity can be can used to find threats as well. If you notice that the malware is using a non-standard user agent when making a network connection, looking through your proxy logs for that agent and similar agents can be a great way to find similar threats. The same could be said on ports and domains. Most of the time if a tool works users will stick with it. The same can be said of the bad actors who are deploying malware. If I use WordPress as an example, not to say it isn’t the most secure platform, when a hack occurs there is usually a file that is added to one of the include folders, and malware may point to that file directly. It is a good idea then to check for similar paths in domains that your firewall and proxy shows traffic to. This can often reveal different threats in your environment. Be thorough in this type of searching. Just because you have the indicators and activity blocked and triggering alerts now, doesn’t mean that another system was not compromised before you put those checks and blocks in place.
Ensure that you have access to the logs from the computer where malware was found. If you have access to get the information on network flow even better. Using these and what you know of the malware after the reversing process you should be able to make the determination if the malware allowed other malicious activity to enter the network. If it did, the logs and network flow should give you a clue as to what else was allowed in and if it used the computer for any lateral movement.
Malware analysis and threat hunting are two concepts and techniques used to ensure that our networks remain secure. When we use tie these concepts together we can more effectively determine the scope of the threat. Behavioral analysis is just one step of the malware analysis process that can be helpful. There are more types of malware analysis and reverse engineering that give information that behavioral analysis does not pick up and you can use to further your threat hunting.
Article Link: http://feeds.feedblitz.com/~/568081054/0/alienvault-blogs~Malware-Analysis-for-Threat-Hunting