Threat actors are exploiting fear and uncertainty to spread Covid-19 themed malicious Android package kits (APKs) onto users’ mobile devices. APKs pose a significant risk to end users because of the sensitive personal information and credentials stored on mobile devices.
We analyzed a popular APK to see if it shares binary code with other Android malware. This particular sample copies significant portions of code from previous Cerberus, Anubis and Ginp variants, which appears to be an ongoing trend among malicious Android applications.
Update as of April 20
We have been monitoring a high number of malicious APK samples reported on Twitter. For example, this tweet from MalwareHunterTeam indicating a fake APK alleging to be sponsored by the Turkish Ministry of Health:
"evdekal.apk": 2dd91a4d60bedd071f98e0fc71438ea6aca61b5827193d3d376a16400ed98a01
From: https://ortakoporotör[.]com/evdekal.apk
Turkish Coronavirus related campaign, site says "sponsored by the Ministry of Health"…
cc @LukasStefanko @virqdroid pic.twitter.com/P0qnrKsv5l— MalwareHunterTeam (@malwrhunterteam) April 21, 2020
Or this example of “Covid.apk” –
"covid.apk": ca57aea7f82c4cab9e16b5b5b1380246babf7e1fe38f0cb0b1d9fe1052b28600
MS detects as "Coravin"…
cc @LukasStefanko @virqdroid pic.twitter.com/O81xy8bc15— MalwareHunterTeam (@malwrhunterteam) April 11, 2020
Here is another example –
Low detected "base.apk": f4ed2a6f5d144cfe88b17d2e0f15a63ce28eef3fac1f4d0b427436c0acec0f2f
cc @LukasStefanko @virqdroid pic.twitter.com/HSNFIwrP6F— MalwareHunterTeam (@malwrhunterteam) April 18, 2020
Many of these samples had low detections upon initial upload to VirusTotal, including this fake media player application which had only four detections –
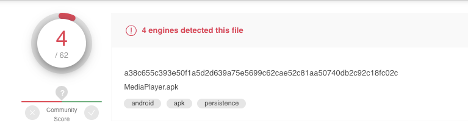
We analyzed the APK using our genetic analysis platform, Intezer Analyze, which classified the threat to Cerberus:
This application is clearly malicious, as seen under the “Dalvik Code Reuse” section, because it shares the majority of its code with previous Cerberus, Anubis and Ginp variants. All three are types of Android malware.
The main connection here is to Cerberus, a banking trojan that attempts to steal the victim’s banking credentials. Cerberus recently underwent an upgrade and is now being shipped with full RAT functionality. The malware can provide its operator with full access to the storage of the infected device. Because this particular application shares 124 genes (or 31.23%) of its code with Cerberus, we can understand that it is a new variant.
MediaPlayer.apk also displays a strong genetic connection to Anubis, an Android malware which source code leaked in 2019, and is being used by adversaries to develop future Android threats.
We see shared code with Ginp, which is another APK malware and which shares code with Anubis, as seen from the analysis report. The connection between Ginp and Anubis has been documented in the past and is easy to spot in Intezer Analyze.
Intezer Analyze supports genetic analysis for Android applications
As threat actors continue to exploit fear and uncertainty to spread malware via Covid-19 themed apps, try uploading them to the free community edition to detect malicious APKs and better understand the origins of these threats.
This is a beta feature so please help us improve by sharing your feedback. If you receive an analysis that you think can be improved, let us know by clicking on the report analysis button in the upper right corner of Intezer Analyze.
The post Malicious APKs share code during Covid-19 pandemic appeared first on Intezer.
Article Link: https://intezer.com/android/malicious-apks-share-code-during-covid-19-pandemic/
