The ASEC analysis team has recently confirmed that Makop ransomware disguised as a resume is being distributed to Korean users. Makop ransomware is malware that has continuously changed and been distributed since last year. It has been introduced in the previous ASEC blogs and it still takes the form of NSIS (Nullsoft Scriptable Install System). It appears that it disguised as a resume to target recruitment managers amidst the recruitment season of the companies. Given that this ransomware was distributed during the recruitment season of the first half of the year, it appears that it aimed to be distributed amidst the recruitment season of the second half of the year again.
The malicious e-mails and filenames that are being distributed are shown below. A compressed malicious file is attached to the e-mail, and the e-mail subject and the filename of the attachment include the applicant’s name. Furthermore, considering that there are files that use passwords among the distributed files, it appears that files with unzip passwords are being distributed as well.
-
Distributed filenames
\LeeMinYoung(PW-210913)\resume\resume(I will always do my best if you hire me).exe
\ParkMinJi(PW-210913)\resume2\resume(I will always do my best if you hire me).exe
\LeeSunYoung Application Form\resume1\resume(I will always do my best if you hire me).exe
\ChangSungKyu\resume3\resume4\resume(I will always do my best if you hire me).exe
The attachment file is compressed (.zip) and upon decompressing it, a file (.alz) compressed with a certain program is found. Another compressed file exists within the compressed file, which is assumed that the malicious file was compressed twice to bypass detection.
Ultimately, two files are found within the attachment file as shown below. The executable (exe) disguised as a Word icon is Makop ransomware that performs this malicious behavior.
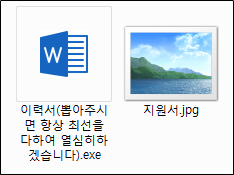 Decompressed attachment file
Decompressed attachment fileWhen the ransomware file is run, it deletes the volume shadow copy and after terminating the related running process to encrypt running document files, it proceeds with the encryption using the commands shown below.
-
Command to delete volume shadow
vssadmin delete shadows /all /quiet
wbadmin delete catalog -quiet
wmic shadowcopy delete
-
Terminated processes
msftesql.exe sqlagent.exe sqlbrowser.exe sqlservr.exe sqlwriter.exe oracle.exe ocssd.exe dbsnmp.exe synctime.exe agntsrvc.exe mydesktopqos.exe isqlplussvc.exe xfssvccon.exe mydesktopservice.exe ocautoupds.exe encsvc.exe firefoxconfig.exe tbirdconfig.exe ocomm.exe mysqld.exe mysqld-nt.exe mysqld-opt.exe dbeng50.exe sqbcoreservice.exe excel.exe infopath.exe msaccess.exe mspub.exe onenote.exe outlook.exe powerpnt.exe steam.exe thebat.exe thebat64.exe thunderbird.exe visio.exe winword.exe wordpad.exe
Filenames and extensions excluded from the encryption are as follows:
-
Excluded extension
makop CARLOS shootlock shootlock2 1recoesufV8sv6g 1recocr8M4YJskJ7 btc KJHslgjkjdfg origami tomas RAGA zbw fireee XXX element HELP zes lockbit captcha gunga fair SOS Boss moloch vassago usagoo pecunia exe dll mammon gamigin marbas harmagedon hinduism sinister baseus
-
Excluded filenames
boot.ini bootfont.bin ntldr ntdetect.com io.sys readme-warning.txt desktop.ini
For the encrypted, the extension of .[random 8 characters].[[email protected]].baseus is added.
 Encrypted files
Encrypted filesIn the encrypted folders, ransom note of the filename of readme-warning.txt is created, and a folder of C:\YOUR_FILES_ARE_ENCRYPTED is also created to create the same ransom note.
As Makop ransomware disguised as resume is still consistently being distributed, users need to take extra caution. Users should also refrain from opening files from unknown sources and take caution in opening executables that use a document file icon.
AhnLab’s anti-malware product, V3, detects and blocks the malware using the alias below.
[File Detection]
- Ransomware/Win.MAKOP.C4631800
[Behavior Detection]
- Malware/MDP.Behavior.M3635

[IOC Info]
- 3d044acc234d0c4532e6a7eb694b8608
- 996872f7782f5507e757c88f2b14bc13
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
The post Makop Ransomware Disguised as Resume Being Distributed in Korea appeared first on ASEC BLOG.
Article Link: Makop Ransomware Disguised as Resume Being Distributed in Korea - ASEC BLOG


