WebMin - 1.910
Webmin is a web-based interface for system administration for Unix. Using any modern web browser, you can setup user accounts, Apache, DNS, file sharing and much more. Webmin removes the need to manually edit Unix configuration files like /etc/passwd, and lets you manage a system from the console or remotely. See the standard modules page for a list of all the functions built into Webmin.
Vulnerability
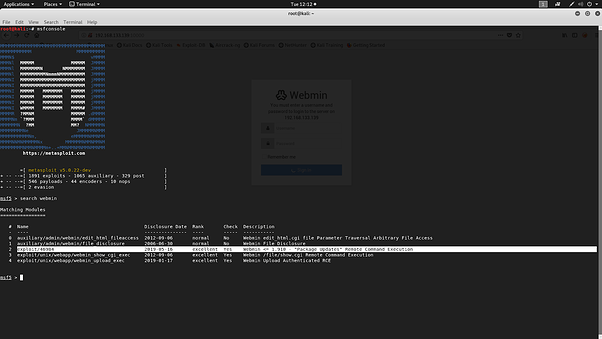
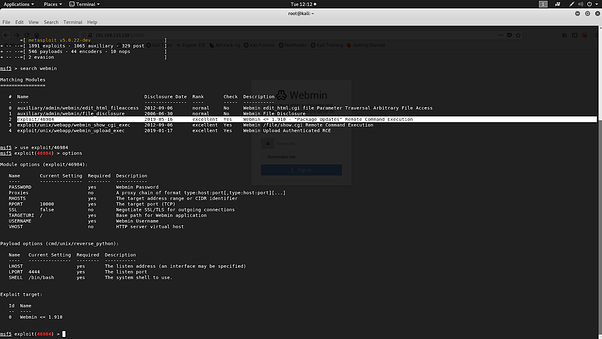
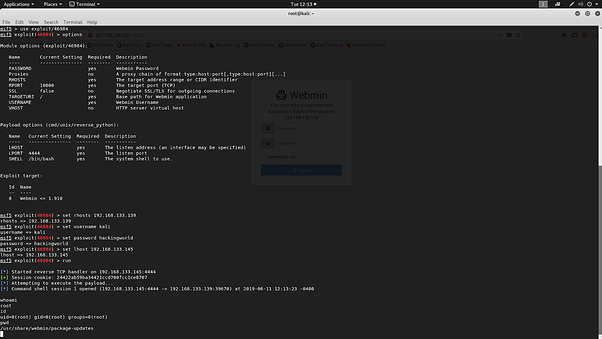
Their is a vulnerability exist in the Package Update module in the Webmin - 1.910 through which an authenticated user with the access to the module is vulnerable to be able to remote code execution. Webmin is uses port 10000 for its web interface and uses the system default user for the authentication and if the user is root user of the machine can give full system access to the attacker and attacker might be able to pivot in the internal network if needed.
Webmin is a web-based interface for system administration for Unix. Using any modern web browser, you can setup user accounts, Apache, DNS, file sharing and much more. Webmin removes the need to manually edit Unix configuration files like /etc/passwd, and lets you manage a system from the console or remotely. See the standard modules page for a list of all the functions built into Webmin.
Vulnerability
Their is a vulnerability exist in the Package Update module in the Webmin - 1.910 through which an authenticated user with the access to the module is vulnerable to be able to remote code execution. Webmin is uses port 10000 for its web interface and uses the system default user for the authentication and if the user is root user of the machine can give full system access to the attacker and attacker might be able to pivot in the internal network if needed.
Proof of Concept
Prevention
As for the prevention of the vulnerability, update you webmin app for the latest one which has its vulnerability patched. If the development company doesn’t release any patches, then, you can use ssl only and turn off the http service.
As for the prevention of the vulnerability, update you webmin app for the latest one which has its vulnerability patched. If the development company doesn’t release any patches, then, you can use ssl only and turn off the http service.
LibreNMS
LibreNMS is an autodiscovering PHP/MySQL/SNMP based network monitoring which includes support for a wide range of network hardware and operating systems including Cisco, Linux, FreeBSD, Juniper, Brocade, Foundry, HP and many more.
LibreNMS is an autodiscovering PHP/MySQL/SNMP based network monitoring which includes support for a wide range of network hardware and operating systems including Cisco, Linux, FreeBSD, Juniper, Brocade, Foundry, HP and many more.
We intend LibreNMS to be a viable project and community that:
encourages contribution,
- focuses on the needs of its users, and
- offers a welcoming, friendly environment for everyone.
The Debian Social Contract will be the basis of our priority system, and mutual respect is the basis of our behaviour towards others. For more about the culture we’re trying to build, please read the Freenode philosophy, including guidelines for running an IRC channel and being a community catalyst.
Vulnerability
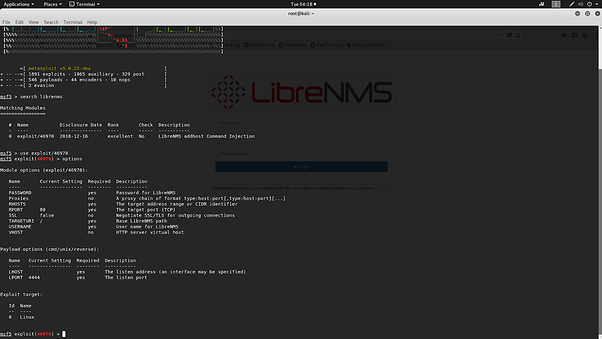
LibreNMS 1.46 allows remote attackers to execute arbitrary OS commands by using the $_POST[‘community’] parameter to html/pages/addhost.inc.php during creation of a new device, and then making a /ajax_output.php?id=capture&format=text&type=snmpwalk&hostname=localhost request that triggers html/includes/output/capture.inc.php command mishandling.
LibreNMS 1.46 allows remote attackers to execute arbitrary OS commands by using the $_POST[‘community’] parameter to html/pages/addhost.inc.php during creation of a new device, and then making a /ajax_output.php?id=capture&format=text&type=snmpwalk&hostname=localhost request that triggers html/includes/output/capture.inc.php command mishandling.
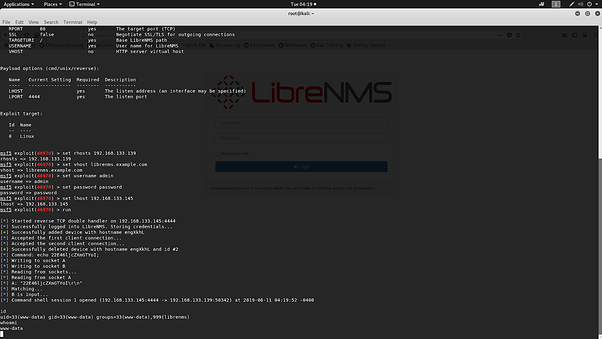
We set rhosts as target machine ip ‘192.168.133.139’, vhost as our domain ‘librenms.example.com’, lhost as our attacker machine ip for listening ‘192.168.133.145’, username and password as the login credentials for the librenms web interface. When we run the module, we get the reverse shell back of the victim’s machine or server.
Prevention
Update the LibreNMS interface with latest updates and check for the permissions given to the interface.
References
Article Link: https://blog.lucideus.com/2019/07/librenms-146-webmin-1910-package.html