Introduction
Since the release of the Mirai source code in October of 2016, there have been hundreds of variants. While publishing my own research, I noticed that Palo Alto Networks was also examining similar samples, and published their findings. Earlier this month, not too long after Palo Alto Networks published their report, discovered a newer version of Echobot that uses 26 different exploits for its infection vectors. In some cases I needed to reach out to MITRE in order to have them assign new CVEs as a result.
I frequently check my honeypot traps looking to examine new and interesting binaries. I look for two things: new exploitation vectors and new attack types.
For new exploitation vectors, I ask the following questions:
- What exploitation methods are bot creators using to infect systems and devices?
- Are they adding new unknown zero days?
- Or are they targeting new system vulnerabilities in web application frameworks or enterprise software systems?
- With regard to attack types, I'm looking to see if there are new amplification or reflection methods being added to the attack capabilities.
- Have they found a new network protocol to abuse?
Echobot Exploits
I recently came across an updated version of the Echobot binary that had some interesting additions. The first binary I found was compiled for ARM and still had the debugging information intact, which made it a little easier to analyze. While examining that binary, I discovered the system hosting the binaries and downloaded an x86 version that also still had the debugging symbols intact.
I counted 26 different exploits that were being used in the spread of this botnet. Most were well-known command execution vulnerabilities in various networked devices.
I'll examine which exploits are being used and how botnet authors are using exploits outside of the IoT botnet genre. When Mirai was first released it targeted weak default credentials commonly found in IoT devices. Then variants of Mirai began targeting vulnerabilities in those devices.
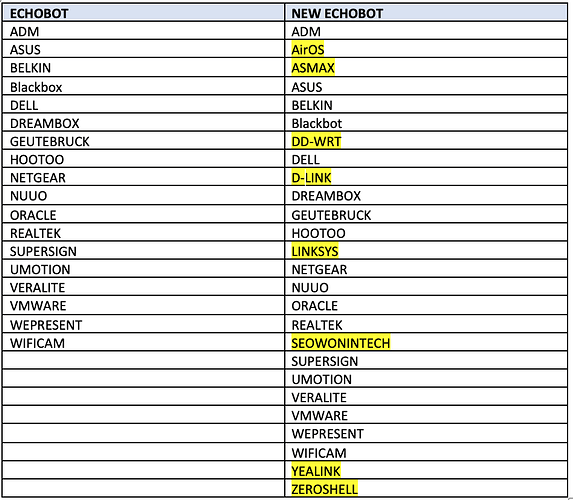
Below is a table comparing the two versions of Echobot and their accompanying exploits.
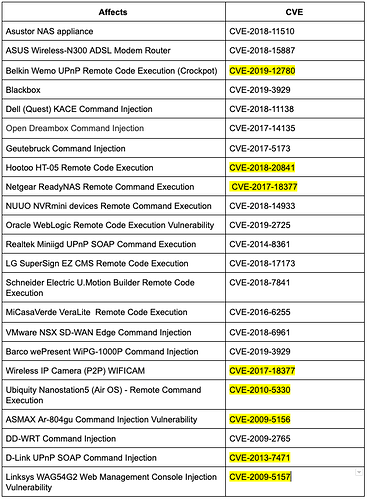
Some vulnerabilities that were being exploited in the wild had public advisories but no CVE numbers assigned. This made it difficult in some cases to discern which vulnerabilities were being exploited. The table below lists each exploit and its CVE assignment, highlighted CVE numbers have been newly assigned by Mitre at my request.
What I found the most interesting, and not so surprising, is the inclusion of cross-application vulnerabilities. For example, rather than sticking to devices with embedded OSs like routers, cameras, and DVRs, IoT botnets are now using vulnerabilities in enterprise web (Oracle WebLogic) and networking software (VMware SD-WAN) to infect targets and propagate malware.
Also of note is the inclusion of 10+ year old exploits for network devices that I believe may never have been patched by the vendors. This alludes to the botnet developers deliberately targeting unpatched legacy vulnerabilities.
Using strings to compare both binaries reveals the same commonly shared attack code typically derived from the Mirai botnet. The only changes seem to be the exploits used for the infection vector. The XOR value also remains the same as 0x54.
The loader system 31.13.195.251 is a virtual server hosted in Bulgaria on Neterra's cloud network.
$ whois 31.13.195.251
INETNUM Object, RIPE Internet Number Registry
inetnum: 31.13.195.0 - 31.13.195.255
netname: NETERRA-VPSBG-NET
descr: VPS.BG IP PA Space
country: BG
admin-c: HP4040-RIPE
tech-c: HP4040-RIPE
status: ASSIGNED PA
remarks: For abuse please use [email protected]
mnt-by: MNT-NETERRA
created: 2018-10-04T14:59:30Z
last-modified: 2018-11-06T11:30:22Z
source: RIPE
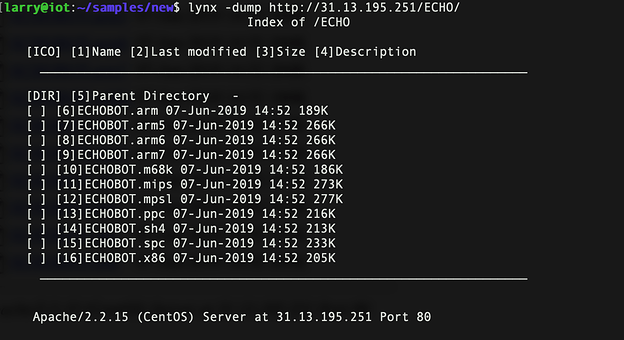
The system is hosting binaries via FTP and HTTP protocol. The binaries were recently updated as the file timestamps are from 6/7/2019.
Starting Nmap 7.60 ( https://nmap.org ) at 2019-06-09 12:26 UTC
Nmap scan report for 31.13.195.251
Host is up (0.14s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
17/tcp open qotd?
21/tcp open ftp vsftpd 2.2.2
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rwxr-xr-x 1 0 0 193688 Jun 07 18:52 ECHOBOT.arm
| -rwxr-xr-x 1 0 0 272683 Jun 07 18:52 ECHOBOT.arm5
| -rwxr-xr-x 1 0 0 272683 Jun 07 18:52 ECHOBOT.arm6
| -rwxr-xr-x 1 0 0 272683 Jun 07 18:52 ECHOBOT.arm7
| -rwxr-xr-x 1 0 0 190920 Jun 07 18:52 ECHOBOT.m68k
| -rwxr-xr-x 1 0 0 279285 Jun 07 18:52 ECHOBOT.mips
| -rwxr-xr-x 1 0 0 283925 Jun 07 18:52 ECHOBOT.mpsl
| -rwxr-xr-x 1 0 0 221169 Jun 07 18:52 ECHOBOT.ppc
| -rwxr-xr-x 1 0 0 218406 Jun 07 18:52 ECHOBOT.sh4
| -rwxr-xr-x 1 0 0 238523 Jun 07 18:52 ECHOBOT.spc
| -rwxr-xr-x 1 0 0 209614 Jun 07 18:52 ECHOBOT.x86
| -rw-r--r-- 1 0 0 1880 Jun 07 18:56 ECHOBOT1.sh
|_drwxr-xr-x 2 0 0 4096 Mar 22 2017 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 50.116.41.112
| Logged in as ftp
| TYPE: ASCII
| Session bandwidth limit in byte/s is 2048000
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 2.2.2 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 5.3 (protocol 2.0)
| ssh-hostkey:
| 1024 fc:9c:c6:64:56:bc:72:03:d3:2a:e0:88:37:ab:d8:ec (DSA)
|_ 2048 ce:7c:8a:f5:50:4d:fe:73:cd:04:b9:76:ce:8f:42:4b (RSA)
80/tcp open http Apache httpd 2.2.15 ((CentOS))
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.2.15 (CentOS)
|_http-title: Apache HTTP Server Test Page powered by CentOS
777/tcp open multiling-http?
3306/tcp open mysql MySQL (unauthorized)
16992/tcp filtered amt-soap-http
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 3.10
Network Distance: 15 hops
Service Info: OS: Unix
The domains akumaiotsolutions.pw and akuma.pw are still being used for command and control. At the time of this writing they're not resolving to an IP address. Historical DNS data has shown A records pointing to servers in Italy (80.211.224.232, 80.211.168.74) and the US (198.54.117.200)
Conclusion
Botnet developers are always looking for ways to spread malware. They are not just relying on exploiting new vulnerabilities that target IoT devices, but vulnerabilities in enterprise systems as well. Some of the new exploits they've added are older and have remained unpatched by the vendor. It seems the updates to Echobot are targeting systems that have possibly remained in service, but whose vulnerabilities were forgotten.
This is an interesting tactic as these systems if found have remained vulnerable for years and will probably remain vulnerable for many more. Also, there are not just new exploitation vectors to examine but attack vectors as well. New weaknesses in popular protocols and services that can be leveraged to amplify and reflect attacks will be discovered. These same types of flaws will undoubtedly also be discovered in new and evolving protocols that have yet to become widely used. This is because all computing systems will always be under development. All we can do is learn from our mistakes and do our best to prevent them from happening in the future.
Article Link: https://blogs.akamai.com/sitr/2019/06/latest-echobot-26-infection-vectors.html